How to design a workplace that employees enjoy and why? BYOD means love
Why implement BYOD
For more than 5 years, the use of personal devices at work, the so-called BYOD (Bring Your own Device - the ability to use personal mobile devices at work), has become an increasingly large-scale and tangible phenomenon on the scale of world IT.

')
Whether we like it or not, our warm lamp calm for our own zoo will be disturbed. The only question is, will we have time to adjust?
As is known, the one who provides services of the best quality wins in the market economy. Oddly enough, this also applies to IT, and I am not talking about IT outsourcing. In the conditions of increasing trend for IT consumerization, the formation of such a phenomenon as User-Centric IT, today it is not enough and unacceptable to provide the user with a workplace only within the office. Studies conducted by J'son & Partners Consulting and Bitrix24 show that by 2020 the number of employees in Russia whose workplace will be fully virtualized and who will be able to work remotely for most of their time will increase to 20%. Naturally, at the same time, these same employees want and should be able to use work applications, systems, documents and desktops as if they were in their office. User comfort should not depend on where he is and what devices he uses.
Ignoring this trend is not in the interests of the business, because the opportunity to work from any place, at any time and from any device (the concept of any place, any time, any device) increases the efficiency of the business itself, and at the same time increases the satisfaction of employees, most contributing to the resolution of the complex task of increasing labor productivity while simultaneously increasing satisfaction with the conditions of this labor itself.
Below we will get acquainted with the main advantages of remote work and the global economic effect currently in Russia according to the results of research by J'son & Partners Consulting and Bitriks24.
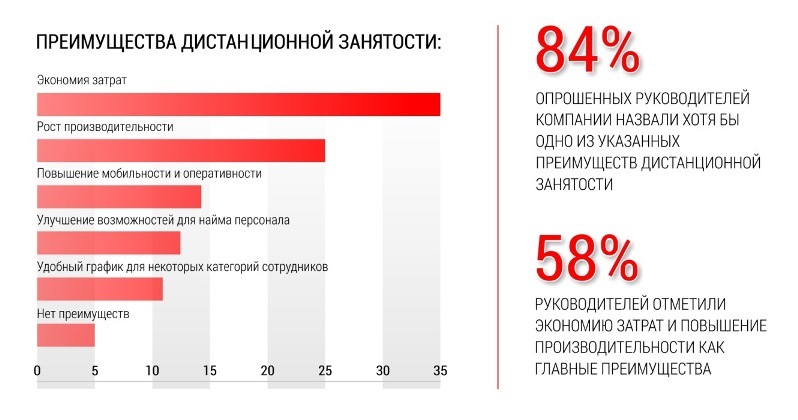

How the voiced benefits translate into a real return on investment - depends, of course, on the particular company, its processes, organizational structure and much more.
But it is also extremely important to build a competent technical solution, which will allow to realize the sounded advantages, as well as reduce the risks from the introduction of BYOD.
BYOD implementation risks
The risks of BYOD are obvious. In general, these are security risks. The possibility of loss of confidentiality of documents leaving the data center, the risks of infecting personal devices not controlled by IT policies, the risks of introducing security threats to the corporate network.
The risks of not implementing BYOD are also quite real and tangible. According to Eric Maiwald, vice president of research for Gartner, the imposition of restrictions on employees in terms of using personal devices at work can result in a real inability to hire qualified personnel in the future. People quickly become accustomed to good, and in the future for qualified specialists the opportunity to work in a way that is convenient for them will become one of the main competitive advantages of employers. Therefore, we take it for granted that we will have to manage mobile devices, and we will write out the main risks in order to think about how to manage them and at the same time extract maximum benefits for the company.

When we offer solutions to the customer, we do not use any one accumulated template, because each customer is unique and unique, both its IT infrastructure and business drivers and the expected effect from the implementation of BYOD.
Place BYOD in an integrated approach to software management
We have already talked about the integrated approach of ICL Services to software management in companies. The diagram below illustrates this approach clearly. So where is the place for BYOD in this picture?
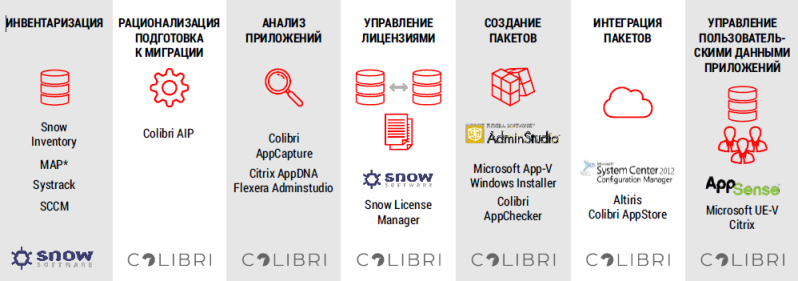
In fact, the BYOD concept fits perfectly into this approach, which once again proves its viability.
In essence, BYOD is composed of two components: mobile device management (MDM) and desktop infrastructure (VDI).
Software on mobile clients can and should be managed. Doing this allows modern solutions for managing mobile devices, such as MaaS360, Intune, AirWatch, MobileIron, XenMobile and others.
However, before you implement an MDM solution, you need to understand how many such devices and how they are used. To do this, it is necessary to conduct a pre-project survey, one of the most important stages of which will be understanding how many mobile devices are and how they are currently used in the company. It should also be done for terminal servers, if they exist, and indeed for the whole IT economy, because, based on the analysis of workloads, we can come to the conclusion about the need to implement VDI. This is the inventory phase. Next - determine the list of standard software for mobile devices - the stage of rationalization . We analyze applications - we formulate immediate requirements for the preparation of installation packages. These can be packages for terminal servers or requests for so-called Wrapping (preparation of a mobile application for deployment by means of a specific MDM solution for a specific platform) of applications for mobile devices or the creation of an installation package for a mobile application. (The difference from Wrapping here is that changes are made "inside" the application at the file or registry level, in the case of Windows-based OS).
License management - for applications on a terminal server, you need to manage not only licenses for the software itself, but also CAL licenses for connecting to a terminal server, at a minimum. There may also be Citrix licenses required to use Citrix XenApp / XenDesktop solutions. For mobile applications, licenses are usually controlled directly by the vendor.
Next, installation packages are prepared for VDI (MSI or, even better, App-V. Using application-level virtualization will increase the reliability and stability of the virtual desktop), and for mobile applications - wrapping or packaging.
Package integration - can be done with both MDM systems (Intune, etc.) for mobile packages, and VDI solutions (Citrix XenApp for example). At the same time, the packages themselves can, say, be integrated into the “golden” image of the virtual desktop using SCCM, or the App-V Publishing Server (in the case of using App-V Full Infrastructure). This approach makes it easier and more manageable to update operating system images for VDI.
And finally, user data management by applications gives the most noticeable wow effect from BYOD implementation using VDI. After separating the user settings at the level of individual applications on virtual desktops, we ensure that they can be instantly applied on any other desktop, regardless of which device the user connects from! Moreover, with a thoughtful and professional approach, it is even possible to synchronize settings between different operating systems - for example, the user will be able to automatically synchronize application settings between a XenApp terminal server based on, for example, Windows Server 2012 and the dedicated Windows 8 virtual machine!
Pre-project examination
The success of the BYOD implementation project is based primarily on the results of the pre-project survey, which includes inventory and analytics of the use of the client's IT assets (in previous articles we already talked about how we conduct software inventory and analytics and what tools we have developed and used for this) . When conducting a pre-project survey, you must do at least the following:
Solution design. Solution Components
Next, you need to create a high-level description of the infrastructure of workplaces, including mobile devices and virtual desktops, and to work out the details in the draft designs of the individual components.
Of course, the architecture will be individual for the client, because in order to conduct a pre-project survey. It must be based on the right decisions aimed at achieving the objectives. But some of the best practices can still be distinguished.
For example, if a company actively uses System Center products, it will be convenient to customize integration with this solution and manage mobile and BYOD devices using Microsoft Intune . At the same time, if, after analyzing customer requirements, we understand that the VDI infrastructure must be built on a Citrix solution, it will be logical (although not necessary) to use XenMobile to manage mobile devices - because this solution will also allow us to use virtual desktops easily. from mobile devices (although, again, you can do without XenMobile, if you, say, are already using Intune). However, in this case, you may need to repack the Citrix Receiver application using tools appropriate for your MDM solution and the platforms on which the application will be used.
In a word, there are many implementation options, but it is necessary to correctly and clearly define the requirements and what is behind them - what goals does the business pursue when implementing BYOD.
Also, when building a modern workplace, it will be very convenient to use the solutions of the Office 365 line - they are supported on all types of devices (Windows, Android, iOS) and reduce the cost of end-user support, and with the help of Sharepoint Online you can easily and flexibly manage the space for collaborative user work on documents.
Special attention should be paid to setting up mobile device management policies, in particular, security policies and compliance policies. In many cases, it will be correct, say, to divide and limit the possibility of data exchange between personal applications (those that the user puts himself from the Play Market or the AppStore) and those that are installed from the corporate application portal. Having a corporate application portal available to users will make our workplaces significantly more flexible and easily manageable by users. And this is material savings on the cost of support.
Below is a high-level picture of the possible implementation of the concept of a modern workplace that includes mobile clients.
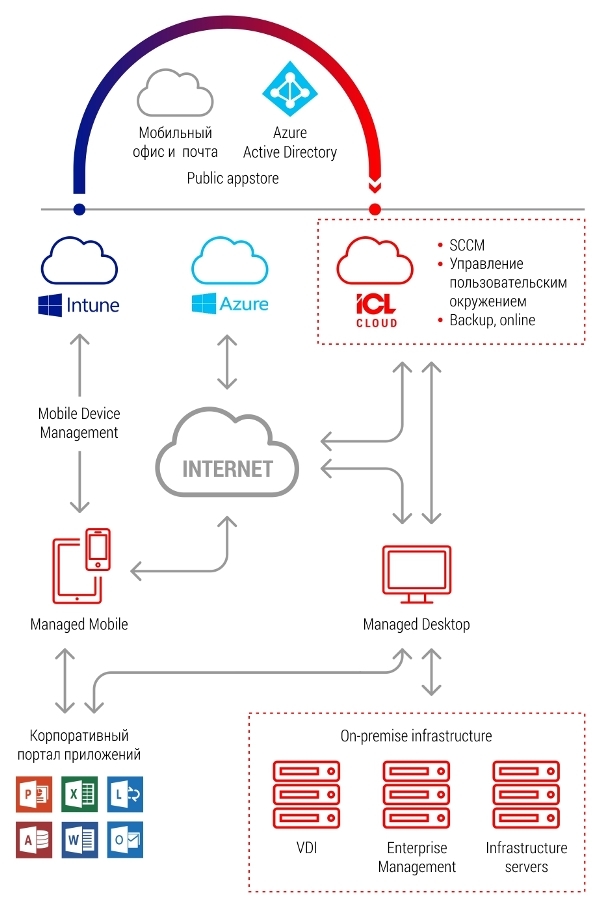
It will greatly enhance the user experience of the Single Sign-On mechanism, which can be implemented using ADFS for Office 365. In the case of using Windows 10 on laptops, technologies such as Windows Hello and Microsoft Passport implement the concept of two-factor authentication and Single Sign-On for applications and websites. Encryption on mobile devices is performed by the forces installed on the OS devices and managed through an MDM solution (XenMobile / Intune / Maas 360 / AirWatch, etc.).
If you need to be able to integrate mobile applications into the enterprise application portal and manage policies at the level of these applications, rather than the entire device, then this usually requires a procedure called Mobile Application Wrapping. It depends on the platform and MDM solution and consists in unpacking the package with the mobile application, modifying the files and registry, packing and signing the “package”.
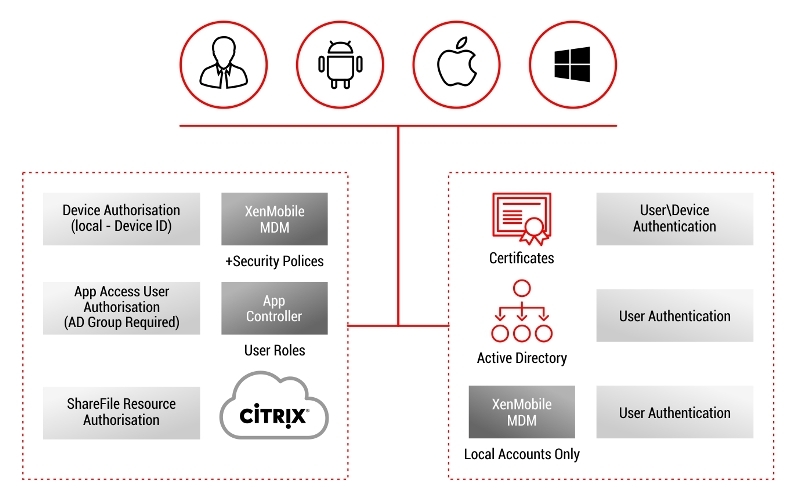
By the example of XenMobile and Netscaler, the figure below shows how the access control for mobile devices to the company's infrastructure is being controlled.
We can configure specific requirements for the connecting mobile device, and in case of non-compliance with these requirements, the device will not be connected.
Access control to co-created documents can be implemented using Microsoft SharepoInt Online in the cloud or, for example, Citrix ShareFile "on the ground".
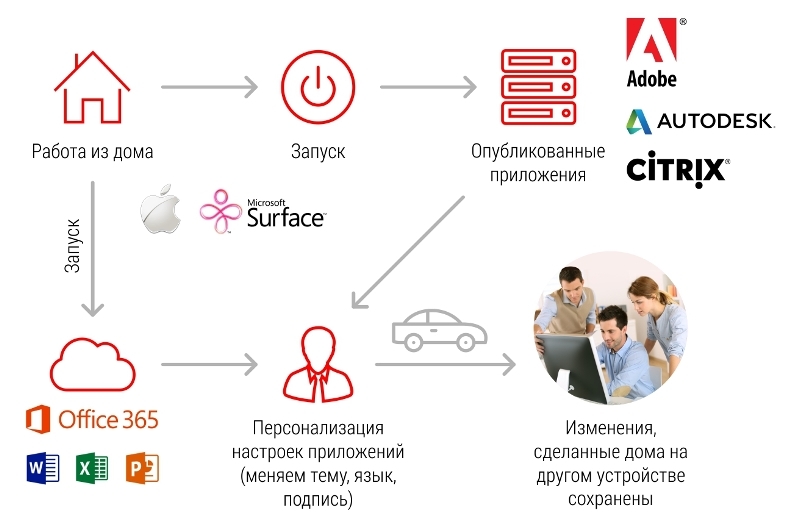
Using Citrix or Microsoft personal virtual disks, or, even better, managing solutions for user environments such as AppSense / MS UE-V significantly increases the user experience - all personalized changes will be available from any device anytime and anywhere without additional actions by the user, and the workplace becomes as mobile as possible. To work with a virtual desktop, for example, a Citrix user will be exactly the same - be it a laptop, mobile device or desktop computer. It is possible to configure policies so that the data does not leave the limits of your data center.
By integrating the described components with an existing enterprise management solution to automate the preparation of virtual desktop images and software deployment using SCCM, we can further optimize our workplace infrastructure.
So that the workplace is guaranteed to be mobile, modern and remain at the same time as controlled as possible, we would recommend using all the most delicious ingredients of our dish:
And, although at first glance, such an infrastructure seems to be complex, in fact it is as flexible, modern and user-centric as possible. And it will certainly increase your competitiveness both in the labor market and in the market for your business, by reducing the cost of supporting many components (this includes, in particular, the cloud components of the solution and personalization of the user environment) and maximum protection of your IT infrastructure without losing its mobility.
By ignatyev
For more than 5 years, the use of personal devices at work, the so-called BYOD (Bring Your own Device - the ability to use personal mobile devices at work), has become an increasingly large-scale and tangible phenomenon on the scale of world IT.

')
Whether we like it or not, our warm lamp calm for our own zoo will be disturbed. The only question is, will we have time to adjust?
As is known, the one who provides services of the best quality wins in the market economy. Oddly enough, this also applies to IT, and I am not talking about IT outsourcing. In the conditions of increasing trend for IT consumerization, the formation of such a phenomenon as User-Centric IT, today it is not enough and unacceptable to provide the user with a workplace only within the office. Studies conducted by J'son & Partners Consulting and Bitrix24 show that by 2020 the number of employees in Russia whose workplace will be fully virtualized and who will be able to work remotely for most of their time will increase to 20%. Naturally, at the same time, these same employees want and should be able to use work applications, systems, documents and desktops as if they were in their office. User comfort should not depend on where he is and what devices he uses.
Ignoring this trend is not in the interests of the business, because the opportunity to work from any place, at any time and from any device (the concept of any place, any time, any device) increases the efficiency of the business itself, and at the same time increases the satisfaction of employees, most contributing to the resolution of the complex task of increasing labor productivity while simultaneously increasing satisfaction with the conditions of this labor itself.
Below we will get acquainted with the main advantages of remote work and the global economic effect currently in Russia according to the results of research by J'son & Partners Consulting and Bitriks24.


How the voiced benefits translate into a real return on investment - depends, of course, on the particular company, its processes, organizational structure and much more.
But it is also extremely important to build a competent technical solution, which will allow to realize the sounded advantages, as well as reduce the risks from the introduction of BYOD.
BYOD implementation risks
The risks of BYOD are obvious. In general, these are security risks. The possibility of loss of confidentiality of documents leaving the data center, the risks of infecting personal devices not controlled by IT policies, the risks of introducing security threats to the corporate network.
The risks of not implementing BYOD are also quite real and tangible. According to Eric Maiwald, vice president of research for Gartner, the imposition of restrictions on employees in terms of using personal devices at work can result in a real inability to hire qualified personnel in the future. People quickly become accustomed to good, and in the future for qualified specialists the opportunity to work in a way that is convenient for them will become one of the main competitive advantages of employers. Therefore, we take it for granted that we will have to manage mobile devices, and we will write out the main risks in order to think about how to manage them and at the same time extract maximum benefits for the company.

When we offer solutions to the customer, we do not use any one accumulated template, because each customer is unique and unique, both its IT infrastructure and business drivers and the expected effect from the implementation of BYOD.
Place BYOD in an integrated approach to software management
We have already talked about the integrated approach of ICL Services to software management in companies. The diagram below illustrates this approach clearly. So where is the place for BYOD in this picture?

In fact, the BYOD concept fits perfectly into this approach, which once again proves its viability.
In essence, BYOD is composed of two components: mobile device management (MDM) and desktop infrastructure (VDI).
Software on mobile clients can and should be managed. Doing this allows modern solutions for managing mobile devices, such as MaaS360, Intune, AirWatch, MobileIron, XenMobile and others.
However, before you implement an MDM solution, you need to understand how many such devices and how they are used. To do this, it is necessary to conduct a pre-project survey, one of the most important stages of which will be understanding how many mobile devices are and how they are currently used in the company. It should also be done for terminal servers, if they exist, and indeed for the whole IT economy, because, based on the analysis of workloads, we can come to the conclusion about the need to implement VDI. This is the inventory phase. Next - determine the list of standard software for mobile devices - the stage of rationalization . We analyze applications - we formulate immediate requirements for the preparation of installation packages. These can be packages for terminal servers or requests for so-called Wrapping (preparation of a mobile application for deployment by means of a specific MDM solution for a specific platform) of applications for mobile devices or the creation of an installation package for a mobile application. (The difference from Wrapping here is that changes are made "inside" the application at the file or registry level, in the case of Windows-based OS).
License management - for applications on a terminal server, you need to manage not only licenses for the software itself, but also CAL licenses for connecting to a terminal server, at a minimum. There may also be Citrix licenses required to use Citrix XenApp / XenDesktop solutions. For mobile applications, licenses are usually controlled directly by the vendor.
Next, installation packages are prepared for VDI (MSI or, even better, App-V. Using application-level virtualization will increase the reliability and stability of the virtual desktop), and for mobile applications - wrapping or packaging.
Package integration - can be done with both MDM systems (Intune, etc.) for mobile packages, and VDI solutions (Citrix XenApp for example). At the same time, the packages themselves can, say, be integrated into the “golden” image of the virtual desktop using SCCM, or the App-V Publishing Server (in the case of using App-V Full Infrastructure). This approach makes it easier and more manageable to update operating system images for VDI.
And finally, user data management by applications gives the most noticeable wow effect from BYOD implementation using VDI. After separating the user settings at the level of individual applications on virtual desktops, we ensure that they can be instantly applied on any other desktop, regardless of which device the user connects from! Moreover, with a thoughtful and professional approach, it is even possible to synchronize settings between different operating systems - for example, the user will be able to automatically synchronize application settings between a XenApp terminal server based on, for example, Windows Server 2012 and the dedicated Windows 8 virtual machine!
Pre-project examination
The success of the BYOD implementation project is based primarily on the results of the pre-project survey, which includes inventory and analytics of the use of the client's IT assets (in previous articles we already talked about how we conduct software inventory and analytics and what tools we have developed and used for this) . When conducting a pre-project survey, you must do at least the following:
- Create an understanding of the client company, business drivers dictate the need for changes, the expected effects and limitations.
- Assess the client environment: what are the workloads of users, identify problem and ideal customers for the implementation of BYOD and MDM (Mobile Device Management).
- Determine the types and principles of dividing users into groups.
- Define general security requirements when working on a mobile device and in the infrastructure of virtual desktops.
- Identify application groups and application security requirements.
- Identify device groups that can be supported by MDM and VDI.
- Make a complete inventory.
- Detect mobile devices already in use in the environment and their number
- Streamline existing software park.
- Determine the readiness of mobile devices used in the company to implement MDM, including from the licensing point of view (as a guide, you can watch the Microsoft Mobile Device Engagement program - but it’s not at all necessary and not always enough to limit your consideration to Microsoft products when planning MDM and BYOD ).
- Prepare a plan for transforming the infrastructure of user workstations, including mobile and virtual desktops.
Solution design. Solution Components
Next, you need to create a high-level description of the infrastructure of workplaces, including mobile devices and virtual desktops, and to work out the details in the draft designs of the individual components.
Of course, the architecture will be individual for the client, because in order to conduct a pre-project survey. It must be based on the right decisions aimed at achieving the objectives. But some of the best practices can still be distinguished.
For example, if a company actively uses System Center products, it will be convenient to customize integration with this solution and manage mobile and BYOD devices using Microsoft Intune . At the same time, if, after analyzing customer requirements, we understand that the VDI infrastructure must be built on a Citrix solution, it will be logical (although not necessary) to use XenMobile to manage mobile devices - because this solution will also allow us to use virtual desktops easily. from mobile devices (although, again, you can do without XenMobile, if you, say, are already using Intune). However, in this case, you may need to repack the Citrix Receiver application using tools appropriate for your MDM solution and the platforms on which the application will be used.
In a word, there are many implementation options, but it is necessary to correctly and clearly define the requirements and what is behind them - what goals does the business pursue when implementing BYOD.
Also, when building a modern workplace, it will be very convenient to use the solutions of the Office 365 line - they are supported on all types of devices (Windows, Android, iOS) and reduce the cost of end-user support, and with the help of Sharepoint Online you can easily and flexibly manage the space for collaborative user work on documents.
Special attention should be paid to setting up mobile device management policies, in particular, security policies and compliance policies. In many cases, it will be correct, say, to divide and limit the possibility of data exchange between personal applications (those that the user puts himself from the Play Market or the AppStore) and those that are installed from the corporate application portal. Having a corporate application portal available to users will make our workplaces significantly more flexible and easily manageable by users. And this is material savings on the cost of support.
Below is a high-level picture of the possible implementation of the concept of a modern workplace that includes mobile clients.

It will greatly enhance the user experience of the Single Sign-On mechanism, which can be implemented using ADFS for Office 365. In the case of using Windows 10 on laptops, technologies such as Windows Hello and Microsoft Passport implement the concept of two-factor authentication and Single Sign-On for applications and websites. Encryption on mobile devices is performed by the forces installed on the OS devices and managed through an MDM solution (XenMobile / Intune / Maas 360 / AirWatch, etc.).
If you need to be able to integrate mobile applications into the enterprise application portal and manage policies at the level of these applications, rather than the entire device, then this usually requires a procedure called Mobile Application Wrapping. It depends on the platform and MDM solution and consists in unpacking the package with the mobile application, modifying the files and registry, packing and signing the “package”.
By the example of XenMobile and Netscaler, the figure below shows how the access control for mobile devices to the company's infrastructure is being controlled.
We can configure specific requirements for the connecting mobile device, and in case of non-compliance with these requirements, the device will not be connected.
Access control to co-created documents can be implemented using Microsoft SharepoInt Online in the cloud or, for example, Citrix ShareFile "on the ground".

Using Citrix or Microsoft personal virtual disks, or, even better, managing solutions for user environments such as AppSense / MS UE-V significantly increases the user experience - all personalized changes will be available from any device anytime and anywhere without additional actions by the user, and the workplace becomes as mobile as possible. To work with a virtual desktop, for example, a Citrix user will be exactly the same - be it a laptop, mobile device or desktop computer. It is possible to configure policies so that the data does not leave the limits of your data center.

By integrating the described components with an existing enterprise management solution to automate the preparation of virtual desktop images and software deployment using SCCM, we can further optimize our workplace infrastructure.
So that the workplace is guaranteed to be mobile, modern and remain at the same time as controlled as possible, we would recommend using all the most delicious ingredients of our dish:
- cloud services (SaaS - applications),
- MDM solution for managing policies on devices
- enterprise application portal integrated with the corporate environment management system (SCCM / Altiris),
- virtual desktops
- user environment virtualization.
And, although at first glance, such an infrastructure seems to be complex, in fact it is as flexible, modern and user-centric as possible. And it will certainly increase your competitiveness both in the labor market and in the market for your business, by reducing the cost of supporting many components (this includes, in particular, the cloud components of the solution and personalization of the user environment) and maximum protection of your IT infrastructure without losing its mobility.
By ignatyev
Source: https://habr.com/ru/post/273707/
All Articles