Security Week 51: Zero Day in Joomla, Twitter warns MacKeeper database leak
 In the penultimate episode of our series this year we will discuss the following news:
In the penultimate episode of our series this year we will discuss the following news:- Twitter sends warnings to users that they might be attacked by some kind of special service. There are few recipients, but some of them are somehow connected with the topic of information protection (or political activism in the field of the Internet). This warning was received by Runa Sandvik, who had previously participated in the development and promotion of the Tor project.
- A serious vulnerability has been discovered in CMS Joomla: a two-stage hacking method involves the introduction of a bookmark that allows you to later send and run arbitrary PHP code on a vulnerable system. The vulnerability was actively exploited at least two days before the patch was published.
')
- Data on 13 million users of the MacKeeper utility suite has been made publicly available. No, the developer company was not hacked, there was an incorrect configuration .
Traditional rules: Every week, the editors of the news site Threatpost selects the three most significant news, to which I add an extended and merciless comment. All episodes of the series can be found by tag . Next week - non-standard top security news for the whole of 2015. In the meantime, we can recall what happened in 2014.
MacKeeper almost stole the user base, which was badly laid.
News Reddit talk . Developer Advisory .
A brief retelling of events around MacKeeper that happened this week looks like this:
- Researcher Chris Vickery through a specialized search Shodan found an open customer base of Kromtech, a developer of various utilities for Apple computers.
- The researcher tried to contact the vendor, but he failed.
- The researcher posted the information to the conference makovodov on Reddit, without revealing the details of the leak, and attaching a single screenshot as confirmation. This one :
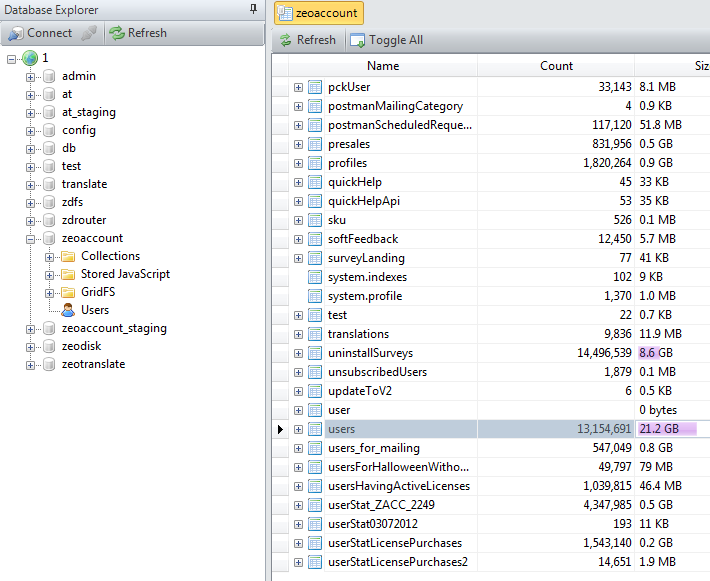
- After that, Chris did manage to contact the company, and the hole was closed.
“But no, the researcher discovered at least 3 more IP addresses, by which the base was still available.
- The hole was finally patched up, after which Chris shared the details of the find.
And the thing was this: the MongoDB database used by Kromtech was accessible from the outside, without any protection, passwords or anything else. Chris Vickery used the specialized search system Shodan, honed to search for similar failures in the configuration. He did not investigate the developers of MacKeeper specifically: he stumbled across their database when searching for the phrase "port: 27017". This is the default port that provides access to MongoDB.
It seems that this time it’s done: the company’s rather operational statement claims that only one case of access from the outside is recorded in the logs, that is, apart from the researcher (which, presumably, the base will not be used), no one else attempted to access user data. However, in such cases it is impossible to be sure for one hundred percent, especially since the passwords in the database were hashed using MD5 without salt, that is, not the most reliable method. We must pay tribute to the company Kromtech: after the incident, they not only initiated the reset of passwords for all users, but also reported on the implementation of a more reliable password hashing algorithm.
And it seems that the incident did not end so badly, but in any case, the very feeling of an awkward moment remains when:

Moreover, MacKeeper, as expected, was not the only case. According to John Motherli, the creator of Shodan, 35,000 MongoDB databases with a total amount of unprotected information of about 680 terabytes are in free access.
Twitter warns users about a possible attack with a thick layer of state support
News
The Nation-state sponsored attack is yet another difficult-to-translate Russian example of the IB-Newspeak. In most cases, it is also incorrect: the intelligence services are not in a hurry to disclose information about their operations, therefore, we can only speculate about their participation in this or that cyber operation. The assumption is made on the basis of the complexity of the attack: if an operation requires so many resources that it is clearly beyond the reach of lone lovers or cybercrime, the conclusion is understandable. On December 12, a small number of Twitter users received a message from the company warning that they were probably the target of the attack, which was allegedly behind the state structure. Here is an example of a warning :
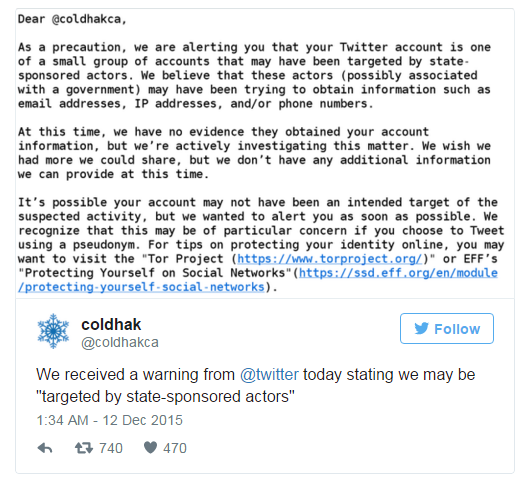
The warning looks as if a lot of man-hours of work of highly paid lawyers were invested in it: the wording is as vague as possible. More or less outlined the interests of the attackers: names, phone numbers, IP-addresses. It is also alleged that most likely this data has not yet been obtained. The rest is recommendations on preserving anonymity, with links to EFF training manuals.
Runa Sandvik, a former Tor developer and security specialist, rightly criticizes Twitter for this very vagueness: if you are trying to keep an eye on someone, it would be nice for this person, at least in general terms, to know exactly how they do it. However, put yourself in the place of Twitter: your infrastructure is either trying to be hacked, or has already been hacked, or you receive strange requests from government agencies of some country. Being bound by strong ropes of international and local legislation, perhaps you have the only option to somehow warn users. Here it is. And one more thing: although Twitter recommends using Tor to disguise its IP address, this is the access option that, according to Runa Sandvik, often leads to blocking by Twitter itself.
Further it is better: if Twitter warns about trying to find out the phone numbers, then why does he so insistently demand to tie his account to the number? In general, it is not easy to be a social network today: on the one hand, your profit depends, among other things, on how actively users share information with you. On the other hand, it is the possession of this data that makes you a target of both cybercrime and someone else.
Zero day vulnerability in Joomla
News Security advisory . Detailed description .
Critical vulnerability in Joomla CMS affects versions up to 3.4.6, including those that are no longer supported 1.5.x and 2.x. The exploitation of this vulnerability allows the execution of an arbitrary code on the system under attack, and, unfortunately, it was discovered not as part of a study, but as a result of the detection of a real attack. Operation of vulnerability takes place in two stages. First, the object is injected using the modified HTTP user agent string. Then through this backdoor you can execute arbitrary PHP code on the machine. The user agent string looks like this (quoted from the blog of Sucuri, which detected the attack, here the string is slightly modified to prevent the ready-made hacking recipe):
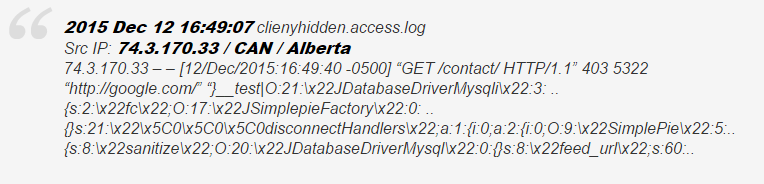
The patch for all versions of Joomla was released on Monday - those who support the current version of CMS, it is enough to upgrade to 3.4.6. Hotfixes have been released for unsupported versions (2.5 and earlier). Unfortunately, cases of attacks on Joomla-based sites were fixed at least two days before the release, so it’s necessary to be updated the sooner the better.
What else happened:
In Brazil , a new banking Trojan was discovered , attacking users mainly through social networks and for some time hosted on the Google cloud platform (already demolished). Brazil in terms of information security is generally a special country. As we recently wrote in a special study , the rampant cybercrime there is such that only those who do not use the Internet at all are at risk of losing data and money (however, even this will not save the theft of a poorly protected state structure database).
Bundle of software vulnerabilities to Cisco routers. Including the company conducts an audit of systems using the Apache Commons Collections library, about the bug in which I wrote earlier.
 Antiquities:
Antiquities:"HH & HH-4091"
Non-dangerous resident virus. Encrypted. Standardly infects .COM files when they are launched. On infection, renames the file to * .A *, writes it to it, and then renames it back. On Mondays, it writes 0 to port A0h. It searches for the “Esik” line on the screen and, if found, after some time turns into the graphic video mode and displays the jumping ball. Intercepts int 1Ch, 21h. It contains the text: "# (- 28 = CIPV] HARD HIT & HEAVY HATE the HUMANS !!! [HH & HH the H.]".
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 69.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/273437/
All Articles