Children and parents on the web: the story of hacking services VTech

Data leakage of users of various services due to hacking of the latter is far from uncommon, unfortunately. One has only to recall the sensational hacking of the Ashley Medison betrayal service, when the data of millions of users leaked to the Web. A huge number of users were just bots, but this does not change anything - each of us is vulnerable.
Even data of users who monitor their accounts, come up with complex passwords, try to provide negative scenarios, flows away to the Network. But leaks still happen. Moreover, an interesting nuance is that if the data security of adults is monitored by everyone and everywhere, then the problem of protecting the data of children on the web is somehow not very popular. And there are even more problems here, because children are not well acquainted with the basics of information security. And if so, the hackers find other ways to get the data of the kids. An example is the recent hacking of VTech services (a manufacturer of children's electronic toys), as a result of which millions of small user accounts have leaked onto the Web.
We are talking about 4.8 million entries, including names, e-mail, dates of birth, etc. True, most of the accounts here belonged to the parents, but about 200 thousand are accounts of the children. Moreover, hackers gained access not only to accounting, but also to hundreds of thousands of photos and other materials. One of the first users who discovered the hack was Lorenzo Bicchierai , who often writes for Motherboard. This user has decided to contact an information security specialist.
')
The first step that was taken was that some of the accounts from the entire data set were checked. Inquiries were sent to some email addresses (explaining the situation), and some users responded. The result - yes, definitely, the Vtech service was hacked.
By the way, the service notifying users in case of hacking has been running for a long time. Check and subscribe to notifications here .
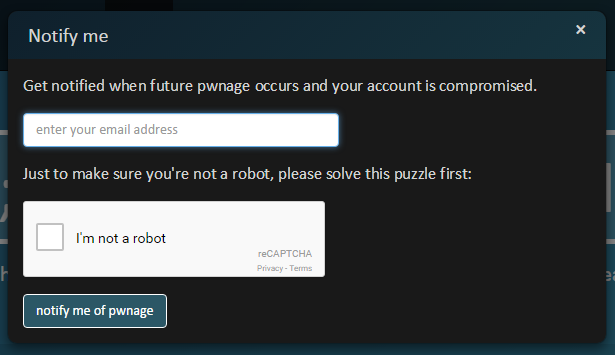
It looks like the service interface
And this means that anyone can identify adults and children, and understand who the parents of children whose data has been “merged” into the Web. Moreover, the data allow us to find out the place of residence of most people registered on Vtech.
Interestingly, the administration of the service was not aware of hacking until it was written by Lorenzo. Only after this work began to eliminate the effects of hacking. In addition, it was possible to contact the hacker who conducted the entire operation. As it turned out, he did it “just for fun”. The data he simply did not need.

Here in this form all data was obtained.
The main data was contained in the file top — parent.csv, where there were almost 5 million lines. User data is as follows:
id
encrypted_password
first_name
last_name
password_hint
secret_question
secret_answer
email_promotion
active
first_login
last_login
login_count
free_order_count
pay_order_count
client_ip
client_location
registration_url
country
address
city
state
zip
updated_datetime
Passwords are presented in this form:

But such data was required when registering the parent of the child:
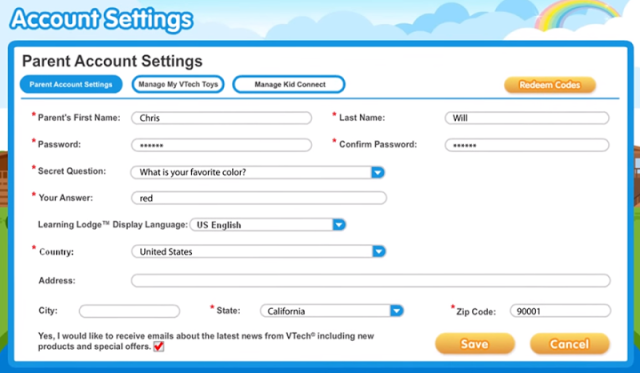
The company Vtech itself produces many dozens of models of devices for children and their parents, including, for example, a video nurse. Vtech also has an online store where parents can download e-books, apps and games for their children's devices.
The hacker who hacked into the Vtech network reported that SQL injection was used. The burglar will get access to web servers and databases of the company with close access.
After analyzing the incident, it turned out that hacking was only a matter of time. For example, passwords were hashed using MD5, an algorithm that is not very difficult to crack, to say the least. Moreover, the password reminder questions were saved as plain text. So there were no problems with getting or resetting the password at all. The same information, with due desire, could also be used to attempt to gain control over the user’s account on other services — Gmail or a bank account, as an example.
Worst of all, the accounts of many children were associated with the accounts of the parents, plus the address of residence. Nowadays, such an attitude to the storage of information of children is simply unforgivable.
How to identify parents? Yes, very simple:
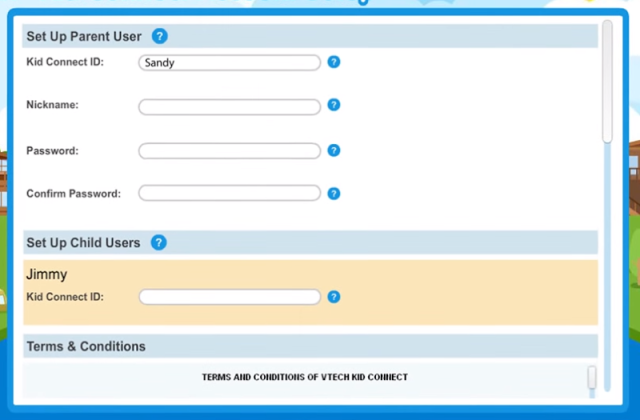
Data on parents are displayed here in this form:
id
username
domain
ll_child_id
ll_parent_id
parent_id
country_lang
create_datetime
expired_datetime
Sample entries:
215836, 'foo% 40bar.com', 'kc-im2.vtechda.com', 0, 2700413, 2700413, 'USeng', '2013-12-25 13:55:21', NULL
and child's record:
215841, 'LittleJohnny', 'kc-im2.vtechda.com', 3974296, 0, 2700413, 'USeng', '2013-12-25 13:55:23', NULL
Well, plus to everything, additional data:
id
created_datetime
updated_datetime
parent_id
login_name
password
first_name
dob
product_code
is_avatar_created
account_level
gender
expiry_date
registration_url
Where are they from? From other sites that are linked to Vtech. Namely:
www.planetvtech.com
www.lumibeauxreves.com
www.planetvtech.fr
www.vsmilelink.com
www.planetvtech.de
www.planetvtech.co.uk
www.planetvtech.es
www.proyectorvtech.es
www.sleepybearlullabytime.com
de.vsmilelink.com
fr.vsmilelink.com
uk.vsmilelink.com
es.vsmilelink.com
And everything looks pretty nice:
Here is the registration form:

Add a child account? No problem:

It is worth noting that the security problems voiced above (for example, the ability to bind a child and a parent in a matter of seconds) is not so easy to fix. They are, so to speak, fundamental, Vtech will have to redo everything, if not re-develop their web services and authentication system.
After it became known about the burglary, parents began to resent asking why the company knew the address and all the other data only so that customers could download a couple of electronic books.
And it is all the more strange that Vtech does not use safety standards that have long been mandatory. For example, SSL is not used anywhere, and data (passwords, logins) are transmitted in clear text. In general, it is even strange that no one paid attention to the service earlier.
Key Security Issues Vtech
Let's look again at the mistakes that the company has committed, whose annual turnover is about 2 billion US dollars.
1. No ssl. Data transmission goes through open channels, and there is quite a lot of data. This is information about parents, password, login, information about the child.
2. Passwords are stored in a slightly protected form, let's say. But secret questions are not protected at all, this is a plain text. Yes, and the passwords of children are also stored in clear form. These are children, why should their data be protected, right?

3. The lack of protection against SQL injection. Here, in general, everything is not simple, but very simple.
4. Universal use of Flash. Even the creator, the Adobe company, is calling for abandoning this technology. And a company of this level, like Vtech, could have done this for a long time using safe technologies.
Take care of yourself and your children!
Source: https://habr.com/ru/post/273423/
All Articles