Critical vulnerability in the Grub2 loader allows to bypass password protection

Security researchers Hector Marco (Hector Marco) and Ismael Ripoll have published information about a 0-day vulnerability they discovered in the popular Grub2 downloader, which is used in most Linux systems. The exploitation of the vulnerability allows you to access the emergency console Grub2 bypassing the password. This, in turn, opens up the possibility for an attacker to launch an attack aimed at elevating privileges to systems and accessing all information.
Vulnerability description
The grub_password_get () and grub_username_get () loader functions are subject to integer overflow. Due to missed verification in the code, pressing Backspace successively 28 times causes overwriting with zero offset memory zeroes. As a result, the stack memory overwrites and a step-by-step overload occurs at different addresses / offsets, which ultimately leads to instructions retw, and as a result, successful operation leads to the launch of the built-in shell.
')
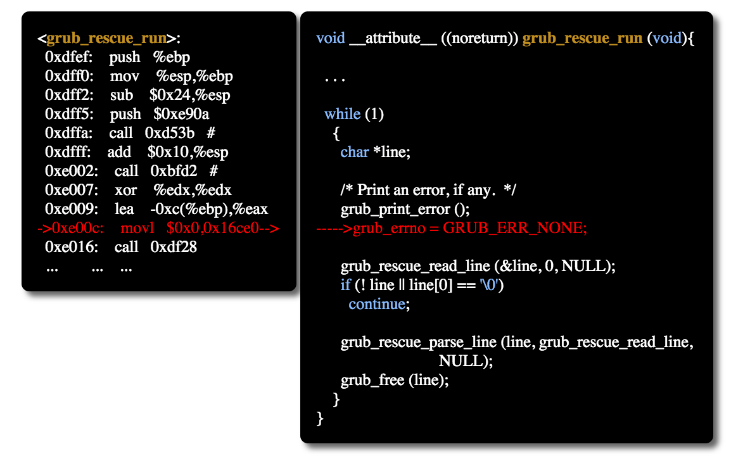
The researchers conducted a proof-of-concept-demo exploiting an error in the grub_username_get () function - after pressing the Backspace key 28 times and once - the Enter key, they got access to the fully functional emergency Grub2 console.
Moreover, Marco and Ripoll managed to get full access to the operating system, even though they did not have a real user password. To do this, they changed the working conditions of the is_authenticated () function, which verifies that the user is authenticated — you can do this with the Grub2 write_word command:
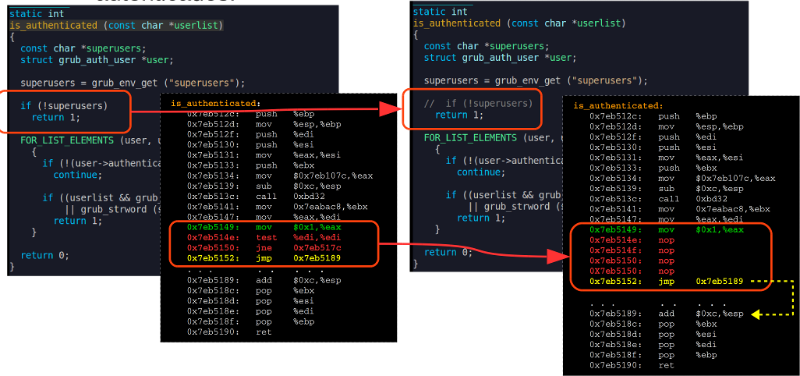
What can cause the operation of the error
According to researchers, the detected vulnerability can be used to carry out APT attacks, the purpose of which could be the theft of critical data. In order to gain access to information, attackers who have access to a computer can use the error in Grub2 to install malicious software on it.
Marco and Ripoll also created a proof-of-concept-demonstration of such an attack. For this, a modified Firefox library libplc4.so was developed, which creates a new process and runs the management console on port 53. Then this library was written to a flash drive and copied to the victim computer, and the original library was replaced.
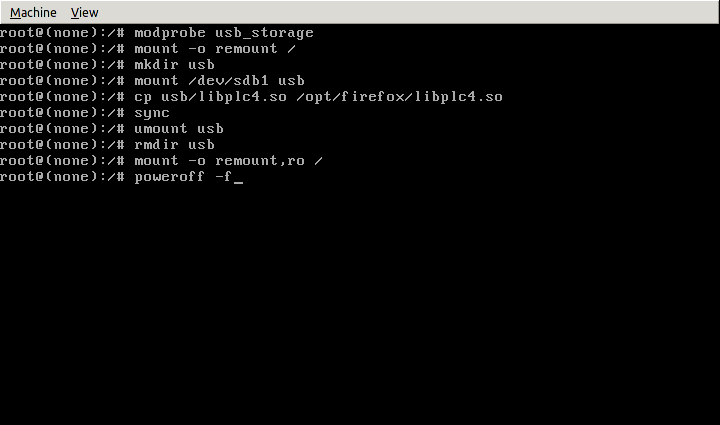
After the user launches Firefox, the management console will be activated, giving the attacker access to the user data:
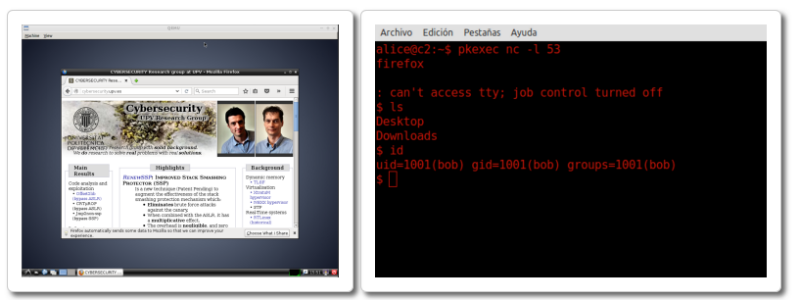
How to protect
Vulnerable bootloader versions from 1.98 to 2.02. In order to check whether a particular system of the described vulnerability is affected, it is necessary at the moment when Grub prompts the user name to press the Backspace key 28 times and then press Enter. If the computer then restarts or the rescue shell starts, the system is vulnerable.
Researchers alerted major developers of Linux-based operating systems, and also developed a patch that fixes the error.
Note that a similar vulnerability was previously found in the Android mobile OS - it allowed you to “get through” the phone’s lock screen using a very long password. In addition, in the summer of 2015, an error was detected in the security system of the gaming store Steam. An attacker could modestly use a Steam user account due to incorrect work of the password recovery function — the system accepted even a null value as the correct code.
Source: https://habr.com/ru/post/273389/
All Articles