Malicious software Nemucod specializes in distributing the ransomware Teslacrypt
From time to time, various malware distribution campaigns reach a fairly high level of activity in one or several countries over several days. On such days, those users who do not protect their computer properly become especially vulnerable. We observed one of these scenarios last week, when a huge increase in the number of detections of the Nemucod Trojan was recorded.

Nemucod is usually used by hackers as a downloader or downloader to download other malicious programs on the user's computer and then install them. The number of detections was very high both in individual countries and in the world as a whole. This indicates that the malicious campaign was not targeted at a specific country, but was used to infect the maximum number of users in different countries of the world.
')
As is the case with many other malicious campaigns that we recently analyzed, in our case with Nemucod, the attackers used the e-mail message as a vector of attack on users. The message is disguised as an invoice and convinces the user to open the ZIP archive attached to the letter. The email address of the already compromised user is indicated as the sender of the letter, so the more users will be later compromised, the more the attackers will replenish their list of potential senders.
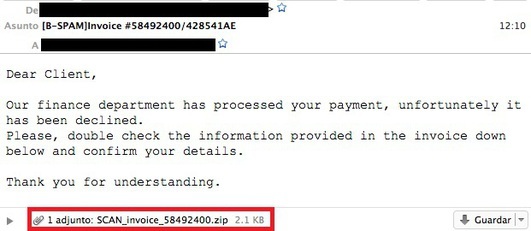
Unlike other malware distribution campaigns, in this case, the archive does not contain an executable file, but a Javascript file. This type of file can be used by attackers to bypass various mail scanners and infect as many users as possible.
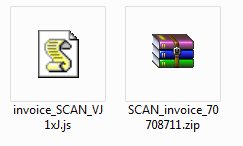
In any case, a malicious Javascript file is as dangerous for a user as an EXE, if executed. Javascript code file contains several features. One of them is that most of the variables used there have arbitrary names. We also found two arrays in the script code, which could be obfuscated IP or web addresses used by attackers to distribute the malware.

In the script code, we found two domains that were used by attackers to distribute the new variants of the ransomware Teslacrypt (detected by ESET AV products as Win32 / Filecoder.EM). One of the domains belongs to a compromised German website, and the other, according to whois, was created recently.
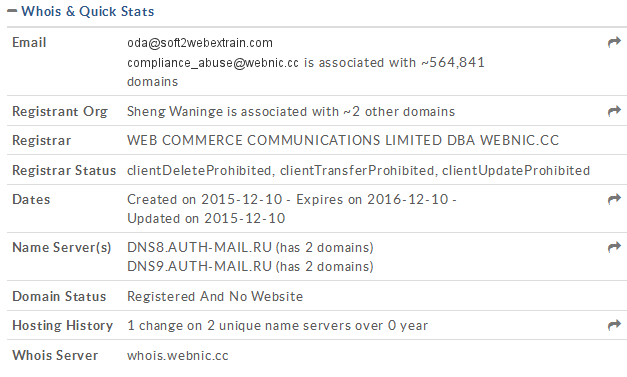
In fact, this resource does not contain any information and contains a warning about this, since the website is under construction. We cannot say with certainty whether the address of the resource was created specifically for spreading the threat, but the date of registration of the domain itself is in this case suspicious.
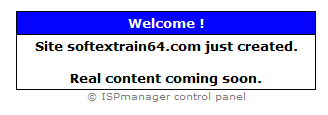
As we have already indicated, one of the downloadable Nemucod in the malware system was a modification of the ransomware Teslacrypt. The name of the malware executable file contained numbers.
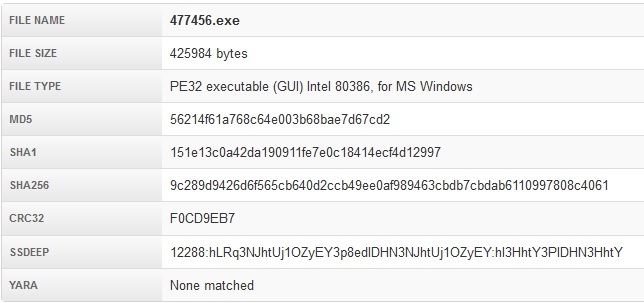
In the case of a victim file being launched, the extortioner begins the process of encrypting certain types of files that are usually used to store images, videos and documents. The malware then initiates the download of the next web page with encryption information to the web browser.

The extortioner generates a text file in each directory that contains the encrypted files. It contains the same instructions for restoring access to files as on the mentioned web page, albeit with some inaccuracies. For example, the text on a webpage indicates that the extortioner uses the RSA-2048 encryption algorithm, while the text document indicates the use of RSA-4096.

This behavior of the malware can be explained by using the pattern of behavior of other families of ransomware, such as Cryptowall. In any case, despite the encryption algorithm used, in most cases, the encrypted files cannot be completely restored to their original state, so the victim loses access to his data.
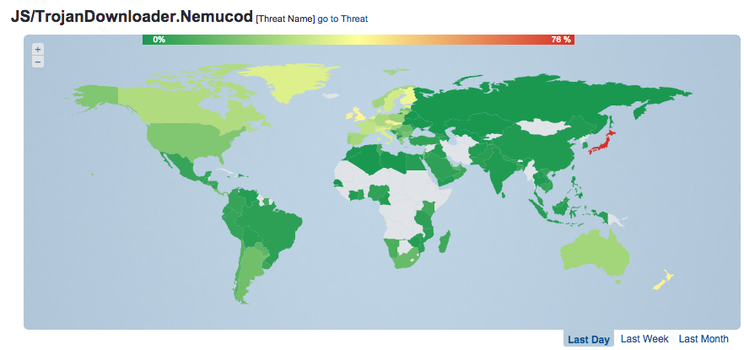
The campaign to spread malware is interesting because the frequency of its detection on users' computers was very high. We observed peak values of its activity at a level of more than 10% on a global scale, but this value was even greater for some countries. In some European countries, a detection rate of more than 20% was recorded, for example, 23% in Spain and 30% in Italy.
In other regions, such as North America and South America, a lower detection rate was recorded, but still more than usual (about 14% in Argentina or 15% in the United States and Canada).
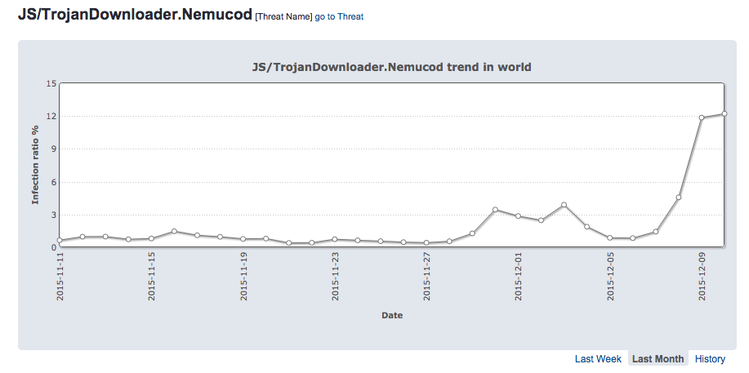
The highest level of threat spread was recorded in Japan. In more than two days, the number of Nemucod detections has reached more than 75% of the total number of all malicious programs detected in this country. While the question remains open why the number of detections for this country turned out to be so high, we did not observe such a surge of Nemucod activity for a very long time.
Conclusion
This malicious campaign did not affect such a significant number of users as previous ones, but a high level of malware detection for several days shows us that such high results of malicious activity can be achieved by sending out a large number of phishing e-mail messages.
The fact that the number of affected users was not as large as in the case of previous campaigns to spread extortionists, despite the increased number of detections, is good news. This means that users use special protection measures that are capable of detecting new threats, and this may also mean the fact that users do not launch for execution the files that came as attachments in suspicious e-mail messages.
However, we can still improve our security measures to counteract the actions of the extortionists. One such measure is to keep up-to-date backup copies of all important data. Further, this copy can be used to restore them.

Nemucod is usually used by hackers as a downloader or downloader to download other malicious programs on the user's computer and then install them. The number of detections was very high both in individual countries and in the world as a whole. This indicates that the malicious campaign was not targeted at a specific country, but was used to infect the maximum number of users in different countries of the world.
')
As is the case with many other malicious campaigns that we recently analyzed, in our case with Nemucod, the attackers used the e-mail message as a vector of attack on users. The message is disguised as an invoice and convinces the user to open the ZIP archive attached to the letter. The email address of the already compromised user is indicated as the sender of the letter, so the more users will be later compromised, the more the attackers will replenish their list of potential senders.

Unlike other malware distribution campaigns, in this case, the archive does not contain an executable file, but a Javascript file. This type of file can be used by attackers to bypass various mail scanners and infect as many users as possible.

In any case, a malicious Javascript file is as dangerous for a user as an EXE, if executed. Javascript code file contains several features. One of them is that most of the variables used there have arbitrary names. We also found two arrays in the script code, which could be obfuscated IP or web addresses used by attackers to distribute the malware.

In the script code, we found two domains that were used by attackers to distribute the new variants of the ransomware Teslacrypt (detected by ESET AV products as Win32 / Filecoder.EM). One of the domains belongs to a compromised German website, and the other, according to whois, was created recently.

In fact, this resource does not contain any information and contains a warning about this, since the website is under construction. We cannot say with certainty whether the address of the resource was created specifically for spreading the threat, but the date of registration of the domain itself is in this case suspicious.

As we have already indicated, one of the downloadable Nemucod in the malware system was a modification of the ransomware Teslacrypt. The name of the malware executable file contained numbers.

In the case of a victim file being launched, the extortioner begins the process of encrypting certain types of files that are usually used to store images, videos and documents. The malware then initiates the download of the next web page with encryption information to the web browser.

The extortioner generates a text file in each directory that contains the encrypted files. It contains the same instructions for restoring access to files as on the mentioned web page, albeit with some inaccuracies. For example, the text on a webpage indicates that the extortioner uses the RSA-2048 encryption algorithm, while the text document indicates the use of RSA-4096.

This behavior of the malware can be explained by using the pattern of behavior of other families of ransomware, such as Cryptowall. In any case, despite the encryption algorithm used, in most cases, the encrypted files cannot be completely restored to their original state, so the victim loses access to his data.
The campaign to spread malware is interesting because the frequency of its detection on users' computers was very high. We observed peak values of its activity at a level of more than 10% on a global scale, but this value was even greater for some countries. In some European countries, a detection rate of more than 20% was recorded, for example, 23% in Spain and 30% in Italy.
In other regions, such as North America and South America, a lower detection rate was recorded, but still more than usual (about 14% in Argentina or 15% in the United States and Canada).

The highest level of threat spread was recorded in Japan. In more than two days, the number of Nemucod detections has reached more than 75% of the total number of all malicious programs detected in this country. While the question remains open why the number of detections for this country turned out to be so high, we did not observe such a surge of Nemucod activity for a very long time.

Conclusion
This malicious campaign did not affect such a significant number of users as previous ones, but a high level of malware detection for several days shows us that such high results of malicious activity can be achieved by sending out a large number of phishing e-mail messages.
The fact that the number of affected users was not as large as in the case of previous campaigns to spread extortionists, despite the increased number of detections, is good news. This means that users use special protection measures that are capable of detecting new threats, and this may also mean the fact that users do not launch for execution the files that came as attachments in suspicious e-mail messages.
However, we can still improve our security measures to counteract the actions of the extortionists. One such measure is to keep up-to-date backup copies of all important data. Further, this copy can be used to restore them.
Source: https://habr.com/ru/post/273383/
All Articles