How to get to the president's cottage at five o'clock in the morning
This post is about how the usual break-in turned into torments of conscience and mental agony. Source will not be much more pictures and analysis. So, someone Vasya works as a “bad guy.” The extent of Vasya’s fall is such that the means for living are brought to him by the search and analysis of information, access to which has been compromised due to illiterate maintenance, disorder or savings on maintenance personnel.

This has been the case since the emergence of the group where Vasya spends most of the time, his profile is the analysis of the extracted data and the compilation of some feedback, if requested by the person concerned.
The usual Moscow morning, office basement, coffee, Vasya and his friends are discussing a new order from an old acquaintance. Everything is standard, you need to get info, all you can reach. Addresses, sites, residences of staff, pages in social networks, etc. obtained in advance, and the more information the buyer collects in advance, the faster and better the result will be. The experimental company turned out to be from the northern capital, without a website (these are still fully available in Mother Russia) and supplies some (which will be disassembled below) equipment, the office seems to have collapsed, but is still agonizing, and someone Mr. X wants to get the remnants of the data development. The youngest went on a business trip, for qualifications, in order to listen for wifi traffic for passwords, turnovers, links and other information, you don’t need much.
')
As a result of these studies, secret words were obtained to the post office, then it was revealed from the correspondence that a Dedik who was standing in the experimental subject was leased for storage. The server is sometimes remotely administrated from outside, the old ubunt 12.04 LTS version is spinning on it (this is about saving on equipment and staff). We scanned for vulnerabilities, access via ssh is configured only for specific ip (quite competently), a dozen ports are open, including 21 (FTP), 39, 41 and 95, several holes were found, the server surrendered to CVE-2014-0196 vulnerability , through it they raised the root from the third attempt, twice the server fell, but no one even moved to find out what was wrong. We searched for everything that looked like source code, documentation, etc. We went in, looked around, reaped the harvest, cleaned it, checked it, cleaned it again, left.
Looking through the merged directories, the foldersConfluence, Repositories and Secrets were found with all sorts of garbage and a couple of uninteresting backups, the total amount of data a little more than 70 gigs. The Secrets folder, as well as the backups, contained "soft pink stuffing" from the data, photos, scraps of the text - it feels like having gone through a shredder. We open “Repositories” as the most interesting candidate for the study: there was a bunch of SVN repositories created between 2006 and 2013. Those folders that Vasya unpacked differ in creation dates from the main archive.
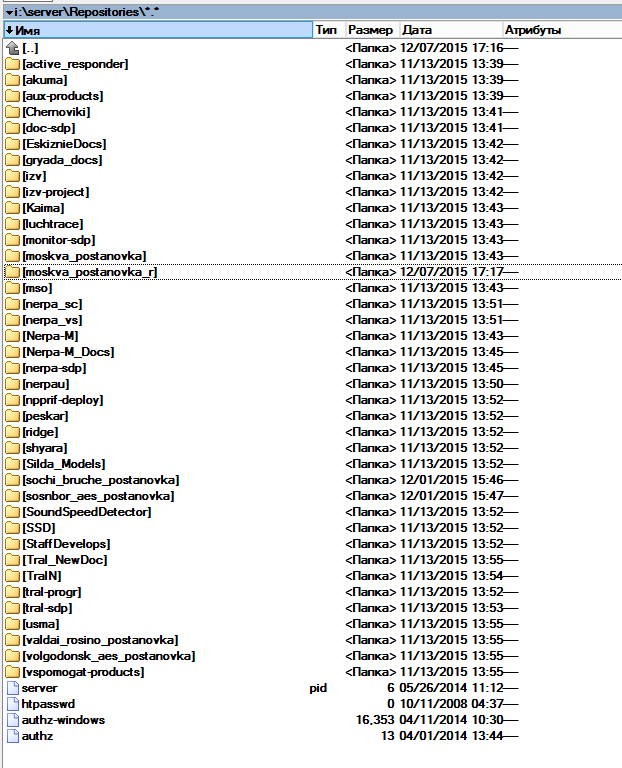
The fishing was a success - here it is “Ide” programmer: a bunch of sorts from a private repository, obtained in “sleepless nights”. Vasya rummaging through folders, simultaneously asking Google for some names, most of the requests the latter responds withadvertising with incoherent muttering, but for some - with very specific events and coordinates:
- moskva_postanovka: well, here it is clear that something was put in the capital;
- sochi_bruche_postanovka: Google doesn't know what sochi_bruche is, but it will answer the question “sochi b ruche”. You can look;
- sosnbor_aes_postanovka: here google gave the answer on such a change as “pine bore aus staging”;
- valdai_rosino_postanovka: again hit the first time - “Valdai Grove staging”;
- volgodonsk_aes_postanovka: well, here and a hedgehog is clear, something was put on the Volgodonsk nuclear power plant, Vasya served there in his youth and was familiar with firsthand knowledge of places.
Apparently, serious guys, it's time to see what kind of fish got into our nets. And yes, Vasya, like an old sishnik, is very jarred by the Russian transliteration in the source code (sarcasm).
We look turnips - mother of God, who writes so? Sortsy mixed with temporary files and objectists, apparently, the developer is (was at the time of 2008) on the first courses of the institute ... stop, student-developer of a large soft? Are you seriously?

Removing temporary files we get the following picture:

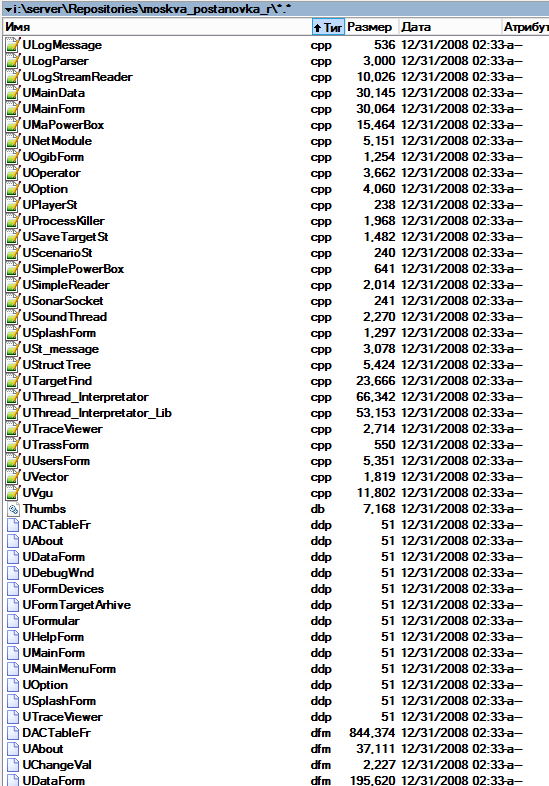
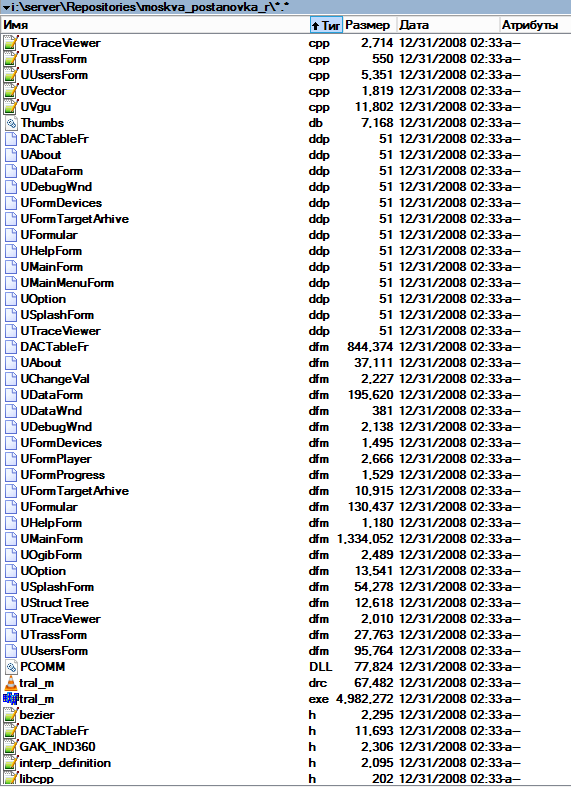
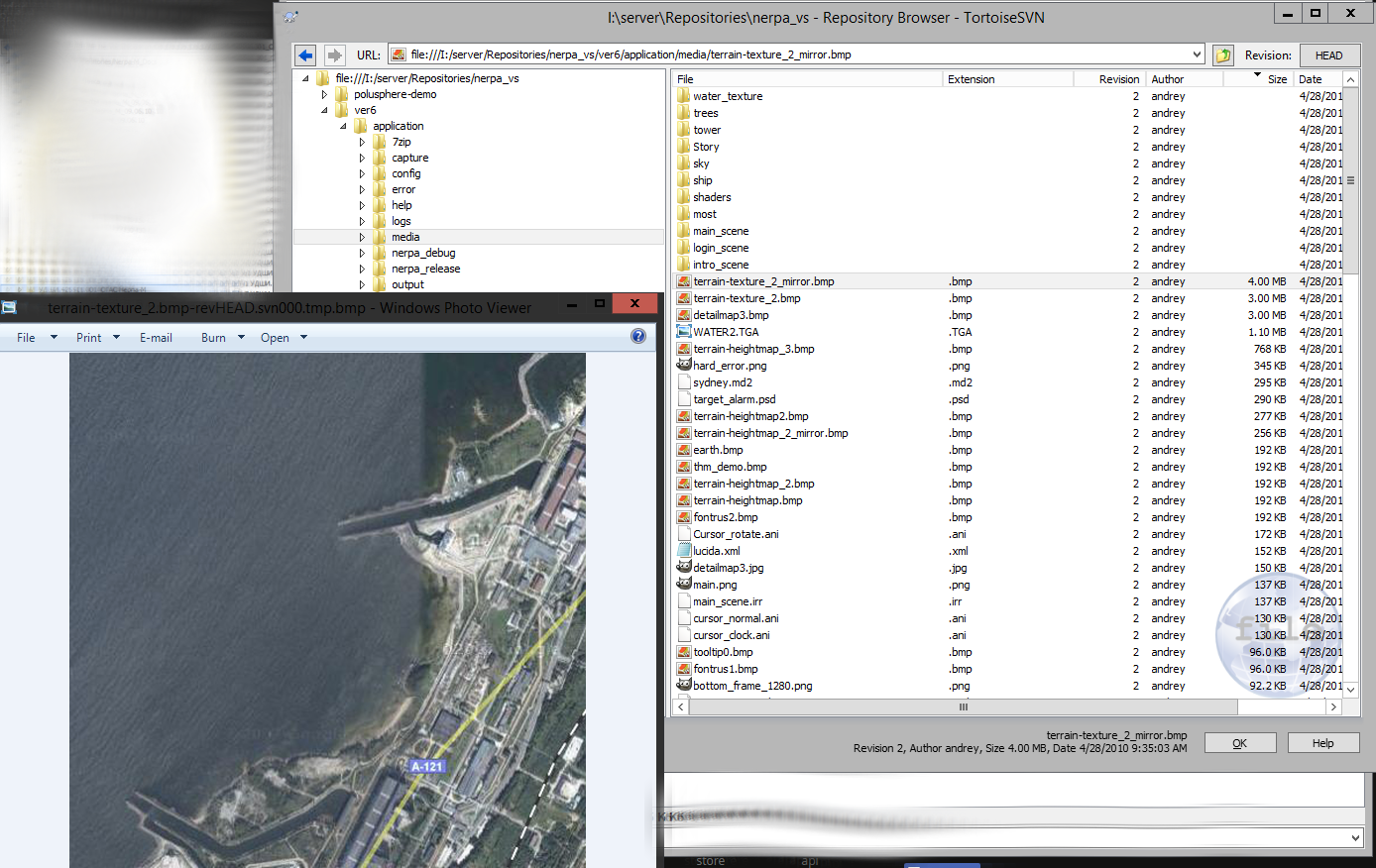
In the Capture folder, the picture strayed on September 30, 2008.

It looks like a picture from Google maps. The distinctive features of this place are the location near the water, and the unusual shape of the embankment. Further search on the gold-headed map led to the following result:

A dock was also found in the repository, explaining why the program was made and what the product actually was, Vasya received.



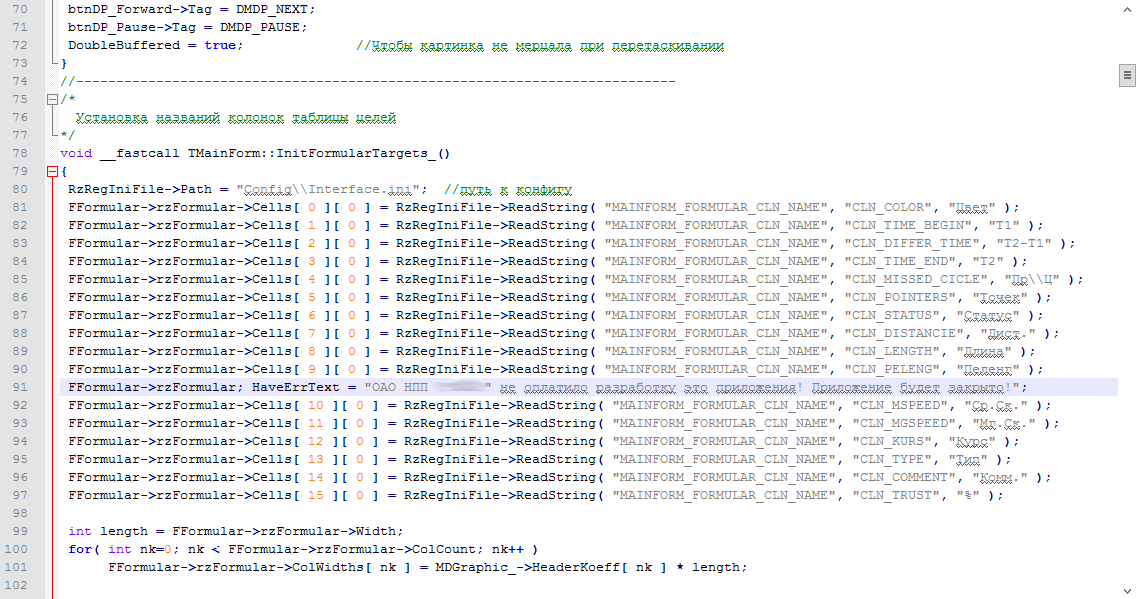
Having figured out the exemplary purpose of the program, Vasya began to study the source code more closely in search of something unusual. After all, everyone knows that developers who are not burdened with corporate etiquette can insert something to entertain themselves. What search criteria were asked? First of all, comments like: “WTF, TODO, f * ck and other funny words” were sought. And the attempts were rewarded on the third day of Zen contemplation: the following pieces of code were found:
1. Protection against bosses (UMainForm.cpp file):
If either the one with the special name in the Windows folder is not found, the program will issue the following warning: “OAO NPP“ XXX ”did not pay for the development of this application! The application will be closed! ”
Funny warning, apparently calculated on the chief-fool.
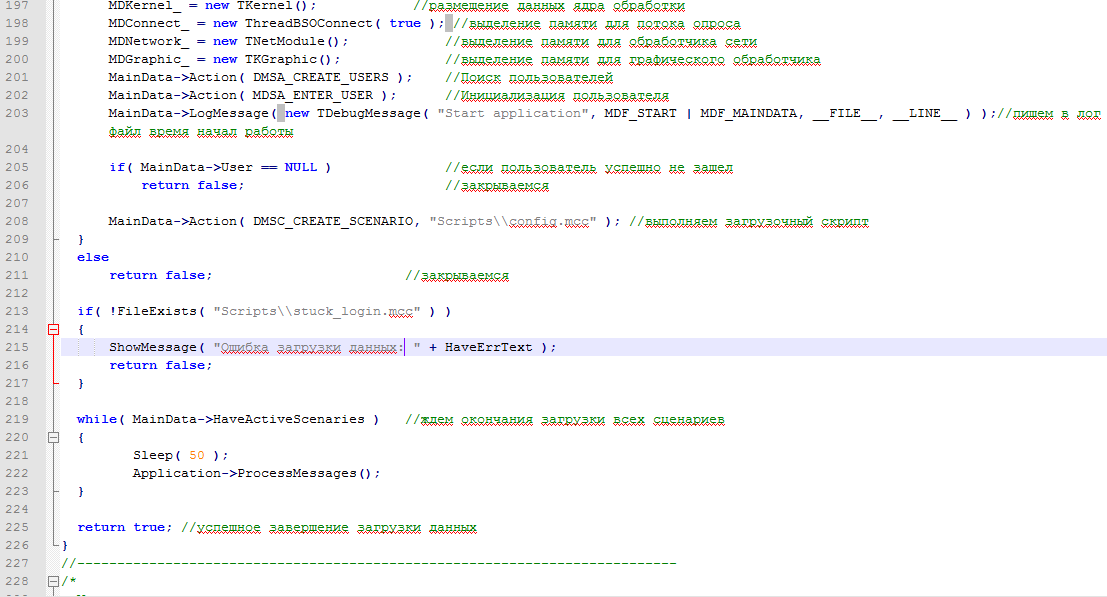
2. Border on the lock (file UBChannel.cpp).
This section of the code in the period from 5.00 to 5.30 in the morning, apparently, sends further to the program with random instead of real data received from the equipment.

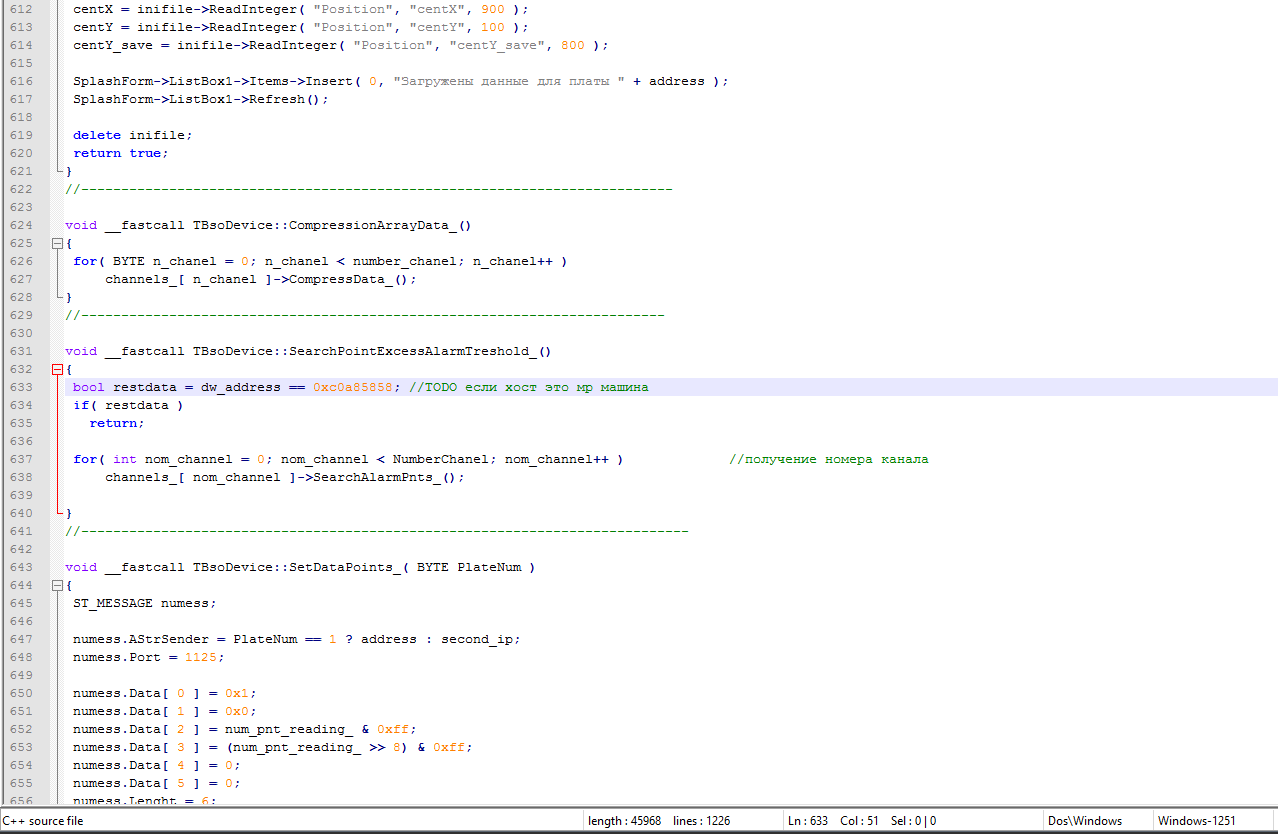
3. Black hole (UBsoDevice.cpp file).
A third suspicious site has been identified here. If the network address of the machine is set to 192.168.88.88, then the incoming information is not sent further (tab / test machine?).
A Google search yields the following results for the queries of “GUPO, Tral M, Gals, Nerpa M, NPP XXX”.
The software described in the repository serves this equipment: one , two , you can read more here .
The next page indirectly confirms the correctness of the compromised information - three , in the repository there are also folders with the names "nerpa-m, nerpau, nerpa-sdp, nerpa_vs, nerpa_sc ". Vasya did not study them, so we will not dwell on them, but the programming style is similar. It also indicates on the site that the service life of these products is at least 10 years, i.e. if the programs were delivered in 2008, then they still work and, perhaps, the same leaky ones (either these are program bookmarks, or test lines were not commented out before production).
Having a little rummaged in repositories, it was possible to find out the following habitats of this masterpiece by the programmer of thought.
1. Valdai (presumably a rest house in Roshchino, near a government facility;
2. Kalinin NPP;
3. Leningrad NPP;
4. Sochi (presumably the rest house "Bocharov Ruchey", near a government facility, allegedly a government dacha);
5. Moscow (presumably the House of the Moscow Region Government);
6. Volgondos NPP.
Presumably a general list of device installation locations:

After scoring the number of desired buns, the interested person somehow disappeared from the field of vision, leaving Vasya in deep thoughts about the meaning of being in the modern world and the prices for the operating system that grow without measure. At the general council, it was decided to point out unlucky admins to security flaws, indicating the methods of their possible remediation. Also, a letter was sent to the head of OAO NPP XXX with a description of the vulnerabilities found. As usual, a two-week interval was given before the publication of the written article, but Vasya’s reply came somewhat discouraged, with some remarks (the audience is still cultural):
“Listen to me [az] deeply to me deeply [b] th as you received or sleep [n] dil this information. You have no idea what kind of r [ya] but he has run into and if anyone else finds out about this, the whole country will look for you, and I personally [will punish you]. ”Punctuation is left unchanged.
At the general council, it was decided to publish some of the information in the form of this article, while not merging the Sortsy into the Internet, although supporters show the world "this" almost won.
Vasya, of course, deleted the sorts, and forgot everything he saw and dug out. It’s a shame only if the software for the army and sensitive objects is written by [students] low-professional programmers, having managed to cram a couple of bookmarks, and then the inadequate and rude people who hired them sell it for considerable sums to the state. According to information from specialized forums, the cost of such equipment for the army and other departments is several million wooden. I hope that the manufacturer has eliminated the existing vulnerabilities, but who guarantees that there are no others, not such obvious ones?
PS: At the time of this writing, a server without any problems is scanned with old holes. Rip.
UBChannel.cpp - pastebin.com/xnA9p80F
UKernel.cpp - pastebin.com/7AZpqkRX
UMainForm.cpp - pastebin.com/PJgdKGcY

This has been the case since the emergence of the group where Vasya spends most of the time, his profile is the analysis of the extracted data and the compilation of some feedback, if requested by the person concerned.
Moscow day
The usual Moscow morning, office basement, coffee, Vasya and his friends are discussing a new order from an old acquaintance. Everything is standard, you need to get info, all you can reach. Addresses, sites, residences of staff, pages in social networks, etc. obtained in advance, and the more information the buyer collects in advance, the faster and better the result will be. The experimental company turned out to be from the northern capital, without a website (these are still fully available in Mother Russia) and supplies some (which will be disassembled below) equipment, the office seems to have collapsed, but is still agonizing, and someone Mr. X wants to get the remnants of the data development. The youngest went on a business trip, for qualifications, in order to listen for wifi traffic for passwords, turnovers, links and other information, you don’t need much.
')
As a result of these studies, secret words were obtained to the post office, then it was revealed from the correspondence that a Dedik who was standing in the experimental subject was leased for storage. The server is sometimes remotely administrated from outside, the old ubunt 12.04 LTS version is spinning on it (this is about saving on equipment and staff). We scanned for vulnerabilities, access via ssh is configured only for specific ip (quite competently), a dozen ports are open, including 21 (FTP), 39, 41 and 95, several holes were found, the server surrendered to CVE-2014-0196 vulnerability , through it they raised the root from the third attempt, twice the server fell, but no one even moved to find out what was wrong. We searched for everything that looked like source code, documentation, etc. We went in, looked around, reaped the harvest, cleaned it, checked it, cleaned it again, left.
We continue to dig
Looking through the merged directories, the folders

The fishing was a success - here it is “Ide” programmer: a bunch of sorts from a private repository, obtained in “sleepless nights”. Vasya rummaging through folders, simultaneously asking Google for some names, most of the requests the latter responds with
- moskva_postanovka: well, here it is clear that something was put in the capital;
- sochi_bruche_postanovka: Google doesn't know what sochi_bruche is, but it will answer the question “sochi b ruche”. You can look;
- sosnbor_aes_postanovka: here google gave the answer on such a change as “pine bore aus staging”;
- valdai_rosino_postanovka: again hit the first time - “Valdai Grove staging”;
- volgodonsk_aes_postanovka: well, here and a hedgehog is clear, something was put on the Volgodonsk nuclear power plant, Vasya served there in his youth and was familiar with firsthand knowledge of places.
Apparently, serious guys, it's time to see what kind of fish got into our nets. And yes, Vasya, like an old sishnik, is very jarred by the Russian transliteration in the source code (sarcasm).
"Moskva_postanovka_r"
We look turnips - mother of God, who writes so? Sortsy mixed with temporary files and objectists, apparently, the developer is (was at the time of 2008) on the first courses of the institute ... stop, student-developer of a large soft? Are you seriously?

Removing temporary files we get the following picture:



In the Capture folder, the picture strayed on September 30, 2008.

It looks like a picture from Google maps. The distinctive features of this place are the location near the water, and the unusual shape of the embankment. Further search on the gold-headed map led to the following result:

"Dig further"
A dock was also found in the repository, explaining why the program was made and what the product actually was, Vasya received.



"Easter eggs"
Having figured out the exemplary purpose of the program, Vasya began to study the source code more closely in search of something unusual. After all, everyone knows that developers who are not burdened with corporate etiquette can insert something to entertain themselves. What search criteria were asked? First of all, comments like: “WTF, TODO, f * ck and other funny words” were sought. And the attempts were rewarded on the third day of Zen contemplation: the following pieces of code were found:
1. Protection against bosses (UMainForm.cpp file):
If either the one with the special name in the Windows folder is not found, the program will issue the following warning: “OAO NPP“ XXX ”did not pay for the development of this application! The application will be closed! ”
Funny warning, apparently calculated on the chief-fool.


2. Border on the lock (file UBChannel.cpp).
This section of the code in the period from 5.00 to 5.30 in the morning, apparently, sends further to the program with random instead of real data received from the equipment.

3. Black hole (UBsoDevice.cpp file).
A third suspicious site has been identified here. If the network address of the machine is set to 192.168.88.88, then the incoming information is not sent further (tab / test machine?).

What is worth (presumably)
A Google search yields the following results for the queries of “GUPO, Tral M, Gals, Nerpa M, NPP XXX”.
The software described in the repository serves this equipment: one , two , you can read more here .
The next page indirectly confirms the correctness of the compromised information - three , in the repository there are also folders with the names "
Where it is (presumably)
Having a little rummaged in repositories, it was possible to find out the following habitats of this masterpiece by the programmer of thought.
1. Valdai (presumably a rest house in Roshchino, near a government facility;
2. Kalinin NPP;
3. Leningrad NPP;

4. Sochi (presumably the rest house "Bocharov Ruchey", near a government facility, allegedly a government dacha);
5. Moscow (presumably the House of the Moscow Region Government);
6. Volgondos NPP.
Presumably a general list of device installation locations:

The truth of life
After scoring the number of desired buns, the interested person somehow disappeared from the field of vision, leaving Vasya in deep thoughts about the meaning of being in the modern world and the prices for the operating system that grow without measure. At the general council, it was decided to point out unlucky admins to security flaws, indicating the methods of their possible remediation. Also, a letter was sent to the head of OAO NPP XXX with a description of the vulnerabilities found. As usual, a two-week interval was given before the publication of the written article, but Vasya’s reply came somewhat discouraged, with some remarks (the audience is still cultural):
“Listen to me [az] deeply to me deeply [b] th as you received or sleep [n] dil this information. You have no idea what kind of r [ya] but he has run into and if anyone else finds out about this, the whole country will look for you, and I personally [will punish you]. ”Punctuation is left unchanged.
Epilogue
At the general council, it was decided to publish some of the information in the form of this article, while not merging the Sortsy into the Internet, although supporters show the world "this" almost won.
Vasya, of course, deleted the sorts, and forgot everything he saw and dug out. It’s a shame only if the software for the army and sensitive objects is written by [students] low-professional programmers, having managed to cram a couple of bookmarks, and then the inadequate and rude people who hired them sell it for considerable sums to the state. According to information from specialized forums, the cost of such equipment for the army and other departments is several million wooden. I hope that the manufacturer has eliminated the existing vulnerabilities, but who guarantees that there are no others, not such obvious ones?
PS: At the time of this writing, a server without any problems is scanned with old holes. Rip.
Sources
UBChannel.cpp - pastebin.com/xnA9p80F
UKernel.cpp - pastebin.com/7AZpqkRX
UMainForm.cpp - pastebin.com/PJgdKGcY
Source: https://habr.com/ru/post/273249/
All Articles