Critical 0-day vulnerability detected in CMS Joomla

On Tuesday, December 14, the Joomla development team released an urgent security update that closes a 0-day vulnerability that opens up the possibility for remote attackers to execute code. Hackers are already actively trying to attack vulnerable sites.
What happened
According to information security company Sucuri, this error has already been exploited by cybercriminals - researchers have found evidence of successful attempts to use it even on December 12. The following lines were present in the log files of the web servers of the compromised sites:
')
2015 Dec 12 16:49:07 clienyhidden.access.log Src IP: 74.3.170.33 / CAN / Alberta 74.3.170.33 – – [12/Dec/2015:16:49:40 -0500] “GET /contact/ HTTP/1.1″ 403 5322 “http://google.com/” “}__test|O:21:\x22JDatabaseDriverMysqli\x22:3: .. {s:2:\x22fc\x22;O:17:\x22JSimplepieFactory\x22:0: .. {}s:21:\x22\x5C0\x5C0\x5C0disconnectHandlers\x22;a:1:{i:0;a:2:{i:0;O:9:\x22SimplePie\x22:5:.. {s:8:\x22sanitize\x22;O:20:\x22JDatabaseDriverMysql\x22:0:{}s:8:\x22feed_url\x22;s:60:.. In the code of the session handler Joomla there is a vulnerability that allows the implementation of the string in the syntax of the serialized session through the HTTP headers User-Agent and X-Forwarded-For. The exploit uses a MySQL feature when handling utf8 characters from the U + 010000 range - U + 10FFFF. When inserting a string at the end of which there is such a character, MySQL will cut the data. This allows you to form and write to the session table a line in which there are custom PHP objects, without violating the syntax. During deserialization of an attacking session, destructors of Joomla classes are called, which leads to the execution of arbitrary code. To ensure that the data is not truncated, in MySQL it is necessary to use utf8mb4 encoding. Go
According to Sucuri researchers, the detected attacks were carried out from the following IP addresses:
- 74.3.170.33 (December 12);
- 146.0.72.83 (December 13);
- 194.28.174.106 (December 13);
On December 14, the number of attempts to exploit has seriously increased - all the “traps” (honeypot) created by the researchers were repeatedly attacked.

Remote code execution using Joomla vulnerability
Members of the Metasploit framework user community on GitHub are real-time writing an exploit to a Joomla vulnerability. According to the latest reports, participants managed to create a working module for exploiting the vulnerability:

Joomla 1.5 was released in January 2008 - this means that the vulnerability has been present in this and later versions of the system for almost eight years. Currently, there is no data on how many sites and web resources have been compromised due to the exploitation of this gap.
How to protect
Vulnerability applies to versions of Joomla 1.5 to 3.4.5 inclusive. All CMS users need to upgrade their system - you can do it here . Users of old unsupported versions 1.5.x and 2.5.x should install patches that are available by reference (instructions for using fixes are in English here ).
As a temporary precaution, Sucuri researchers recommend replacing potentially dangerous data in the HTTP User-Agent header. Below is a sample configuration for an Apache web server:
RewriteCond %{HTTP_USER_AGENT} .*\{.* [NC]RewriteRule .* - [F,L]In addition, experts at Positive Technologies recommend using specialized means of protection against cyber threats - for example, the application layer firewall PT Application Firewall successfully reflects possible attempts to exploit this vulnerability:
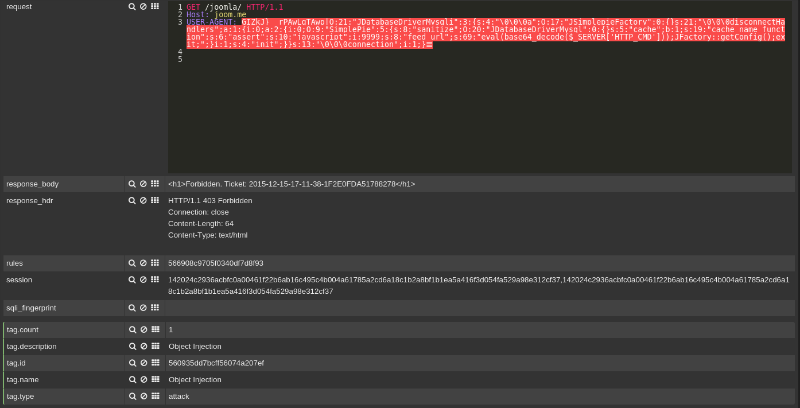
It is not the first time security researchers have found vulnerabilities in Joomla CMS. In October 2015, version 3.4.5 was released, in which serious vulnerabilities were fixed (CVE-2015-7297, CVE-2015-7857, CVE-2015-7858), which opened up opportunities for attackers, including the implementation of SQL- injection.
Recall also that using an open source CMS is not a security guarantee if you have not checked these codes for vulnerabilities. Last year, experts from Positive Technologies, using the PT Application Inspector code analyzer, found many bugs in several popular open source CMS, including Joomla, Shopos, Yii and Jahia, as well as in Wordress plugins. Analysis of one such study, with vulnerabilities of the InstantCMS system, we published at the beginning of the year .
Source: https://habr.com/ru/post/273213/
All Articles