FireEye Specialists Discover New Bootkit
Specialists of the company FireEye have published data on the bootkit called BOOTRASH, which is used by a cyber group called FIN1. FIN1 resorts to the use of various malware under the general name Nemesis to compromise banks and payment terminals. FireEye indicates that the cyber group uses a system infection mechanism at the sector level of the hard disk, compromising the known structure of the Volume Boot Record (VBR), in which the file system data structures and loader code are located.

The so-called Nemesis attacker platform includes a set of various files and tools, including a keylogger, tools for transferring files, capturing screenshots, and managing running processes. All of these tools are used by cybercriminals to steal financial information from banks and payment terminals.
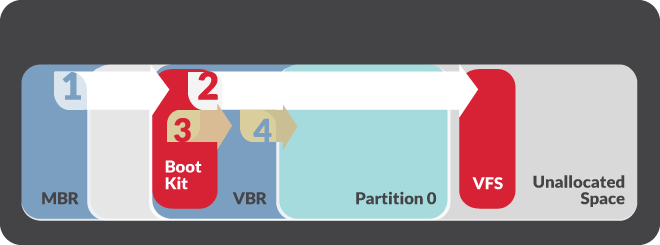
Fig. The OS boot process in the compromised BOOTRASH system ( hijack the system boot process ). A portion of the malicious code for the early boot phase is located in its own malware file system called the Virtual File System (VFS), which is located behind the volume data.
')
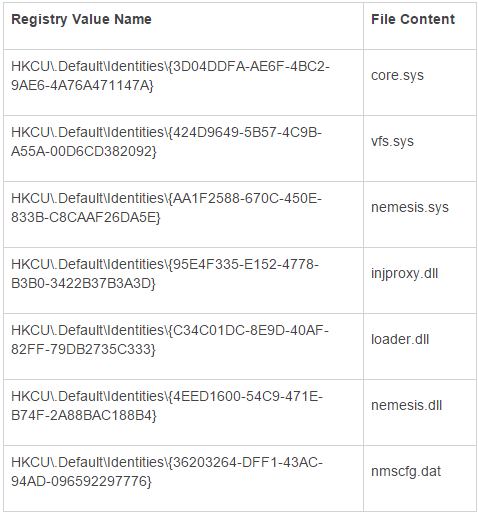
To store Nemesis files, BOOTRASH uses the free space between disk partitions to organize its file system. Otherwise, the behavior of BOOTRASH is not much different from the usual bootkits, which we wrote about earlier . The bootkit file system contains important files for its operation, such as vbr.bin, vbs.bin, and bootldr.sys. Other executable and data files can be stored both in VFS and as binary data in the registry section HKCU \ .Default \ Identities. The following table lists such components.
Storing malware files in hard disk sectors and organizing your own file system is a good method of hiding your presence both for the user's eyes and for AV scanners and security products that specialize in analyzing file systems. However, the majority of such products today are able to scan both MBR and VBR for the presence of malicious code, restoring the necessary bootstrap code or bootloader code in these critical sectors. Having lost its code in these important sectors, the bootkit is deprived of the possibility of performing further operations, including activation of the payload, which is bad news for intruders.
The dropper BOOTRASH has the following MD5 identifier: 372f1e4d2d5108bbffc750bb0909fc49.

The so-called Nemesis attacker platform includes a set of various files and tools, including a keylogger, tools for transferring files, capturing screenshots, and managing running processes. All of these tools are used by cybercriminals to steal financial information from banks and payment terminals.

Fig. The OS boot process in the compromised BOOTRASH system ( hijack the system boot process ). A portion of the malicious code for the early boot phase is located in its own malware file system called the Virtual File System (VFS), which is located behind the volume data.
')
To store Nemesis files, BOOTRASH uses the free space between disk partitions to organize its file system. Otherwise, the behavior of BOOTRASH is not much different from the usual bootkits, which we wrote about earlier . The bootkit file system contains important files for its operation, such as vbr.bin, vbs.bin, and bootldr.sys. Other executable and data files can be stored both in VFS and as binary data in the registry section HKCU \ .Default \ Identities. The following table lists such components.

Storing malware files in hard disk sectors and organizing your own file system is a good method of hiding your presence both for the user's eyes and for AV scanners and security products that specialize in analyzing file systems. However, the majority of such products today are able to scan both MBR and VBR for the presence of malicious code, restoring the necessary bootstrap code or bootloader code in these critical sectors. Having lost its code in these important sectors, the bootkit is deprived of the possibility of performing further operations, including activation of the payload, which is bad news for intruders.
The dropper BOOTRASH has the following MD5 identifier: 372f1e4d2d5108bbffc750bb0909fc49.
Source: https://habr.com/ru/post/272641/
All Articles