Google fixed Android vulnerabilities
Google has released a security update for Android Nexus Security Bulletin - December 2015 , which closes 19 vulnerabilities in the OS. Some of them are serious enough and allow attackers to remotely execute code on the device using specially crafted multimedia files, and these files can be delivered to the user via email, a web browser or an MMS message.

Vulnerability CVE-2015-6616 in the system component Mediaserver allows attackers to remotely execute code with elevated privileges on the device by sending an MMS message (Remote Code Execution). Another critical LPE vulnerability in the kernel with the identifier CVE-2015-6619 allows an application to get maximum root privileges in the system and full access to all device resources. This type of vulnerability is used to perform the rooting operation.
')
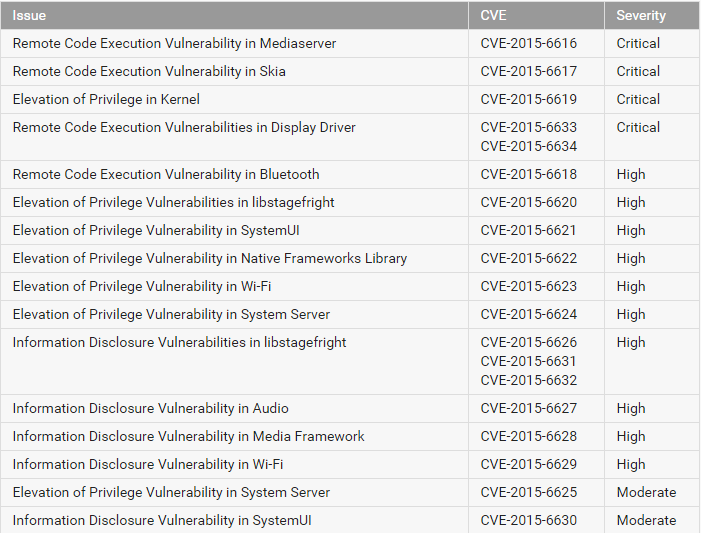
Several vulnerabilities have been closed in the infamous libstagefright library. Previously, Google closed the RCE vulnerabilities in this library, which resulted in remote code execution with maximum permissions on the system. Vulnerabilities in the Display Driver component are also classified as critical as they allow an attacker to remotely execute code using a special multimedia file delivered in various ways, including email, a web browser, MMS messages.
High severity vulnerabilities are Elevation of Privilege (EoP, LPE) and Information Disclosure. In the first case, the attacker uses the usability in the component to obtain elevated privileges in the system, and in the second, in order to obtain inappropriate information bypassing the Android security settings. Virtually all vulnerabilities of this type provide an attacker with access to additional rights, such as Signature or SignatureOrSystem.

be secure.

Vulnerability CVE-2015-6616 in the system component Mediaserver allows attackers to remotely execute code with elevated privileges on the device by sending an MMS message (Remote Code Execution). Another critical LPE vulnerability in the kernel with the identifier CVE-2015-6619 allows an application to get maximum root privileges in the system and full access to all device resources. This type of vulnerability is used to perform the rooting operation.
')

Several vulnerabilities have been closed in the infamous libstagefright library. Previously, Google closed the RCE vulnerabilities in this library, which resulted in remote code execution with maximum permissions on the system. Vulnerabilities in the Display Driver component are also classified as critical as they allow an attacker to remotely execute code using a special multimedia file delivered in various ways, including email, a web browser, MMS messages.
High severity vulnerabilities are Elevation of Privilege (EoP, LPE) and Information Disclosure. In the first case, the attacker uses the usability in the component to obtain elevated privileges in the system, and in the second, in order to obtain inappropriate information bypassing the Android security settings. Virtually all vulnerabilities of this type provide an attacker with access to additional rights, such as Signature or SignatureOrSystem.

be secure.
Source: https://habr.com/ru/post/272601/
All Articles