How to split VPN traffic in MacOS

VPN
VPN (English Virtual Private Network - a virtual private network - a generic name for technologies that allow you to provide one or several network connections (logical network) on top of another network (for example, the Internet) WikiPedia
Suppose you are a developer and some of the resources (for example, a database) are located on a corporate network that is accessed via a VPN.
')
If you look at all the available instructions on how to set up VPN on Mac OS, you will see that the authors tell you to checkbox “send all traffic through VPN”, which leads to the fact that (Captain Evidence) all traffic goes through VPN, which in turn imposes all restrictions on the corporate network (a ban on visiting individual resources, closed ports, etc.) or restrictions on the anonymization service (narrow channel, long ping, etc.).
The question arises - is it possible to allow only certain traffic through a VPN, and let the rest of the (main) traffic go through a normal channel without restrictions.
This is done quite simply.
Briefly go through the configuration of the VPN connection.
Click on the "apple" in the upper left corner of the screen and select "System Settings".
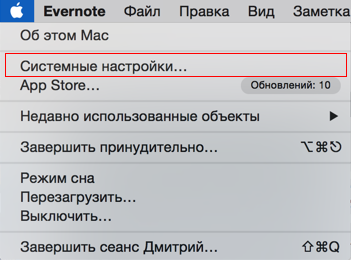
Choose "Network"
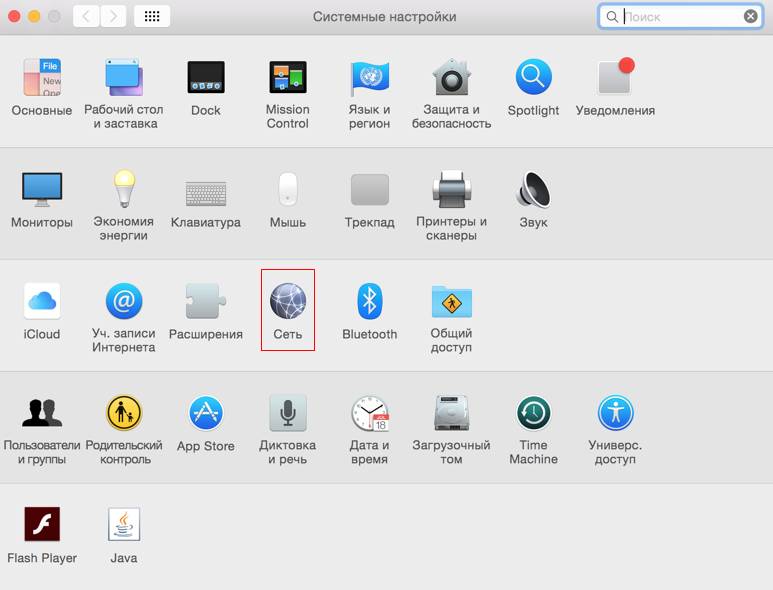
Click on the "plus sign" in the list of network connections.
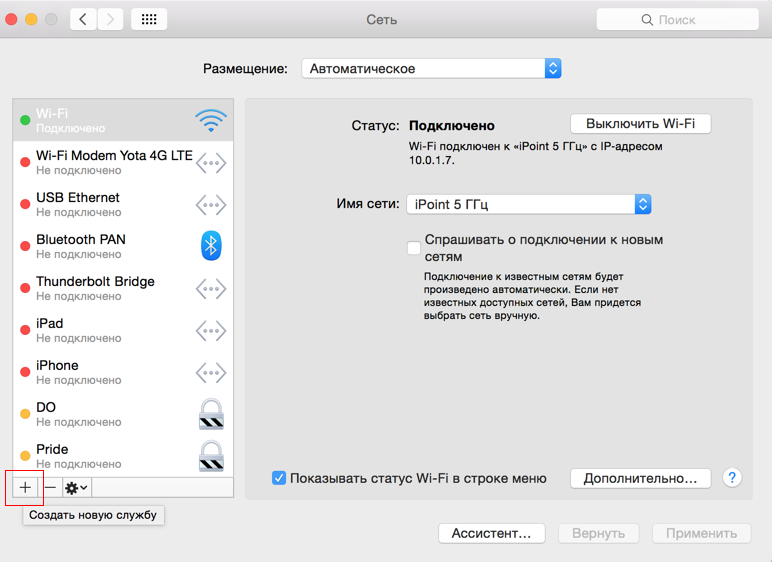
Choose "VPN"
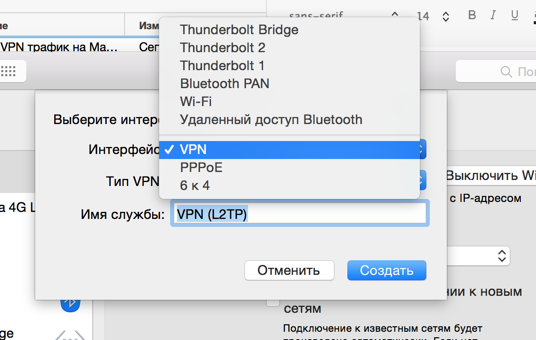
VPN type (in my case, this is L2TP over IPSec)
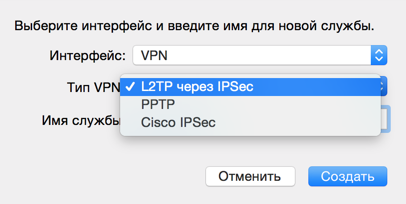
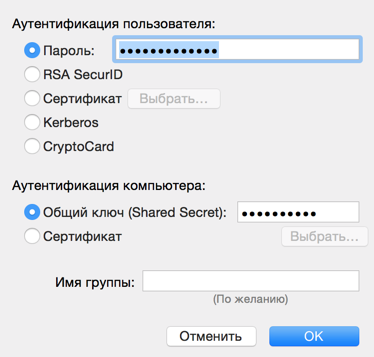
Fill in the connection parameters
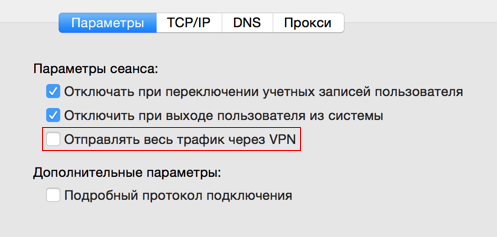
Daws "Send all traffic through VPN" is not set
Now we need to find out the interface through which VPN traffic is going.
Run ifconfig without VPN connected
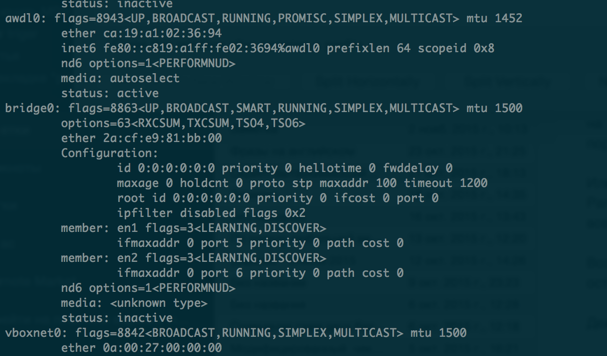
Connecting VPN and running ifconfig again
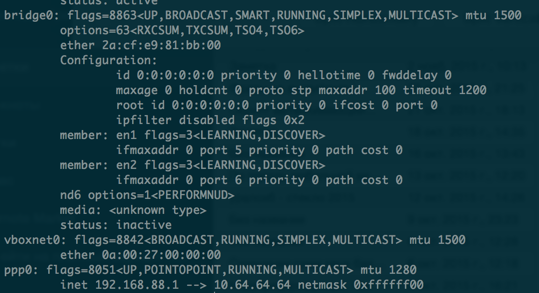
We see that the ppp0 interface appeared
Now, by default, all traffic goes over a normal connection (not a VPN).
Further, I need to connect to my server located at 192.168.0.20 via VPN. For this we need to build a network route. We use the regular unix-command route.
sudo /sbin/route add -host 192.168.0.20 -interface ppp0 Now all traffic goes through my normal connection, and traffic to the corporate server goes through VPN.
For convenience, in the file ~ / .profile create aliases for the command to add routes
alias server-vpn-up='sudo /sbin/route add -host 192.168.0.20 -interface ppp0' Now to raise the connection, you need to connect to the VPN and execute the server-vpn-up command.
The alternative is to create the file / etc / ppp / ip-up, register in it [in my case]
#!/bin/sh /sbin/route add 192.168.0.0/24 -interface $1 and grant execution rights
sudo chmod +x /etc/ppp/ip-up After this, the route will be automatically registered after connecting to the VPN.
What can meet pitfalls.
1. There may be a conflict of IP addresses, if the internal and external networks use the same address space (maybe I use the wrong term, please correct in the comments). Those. You have both VPN and internal home network in 192.168.0 ... In my case, the solution was to reconfigure the home network to 10.0.1 ...
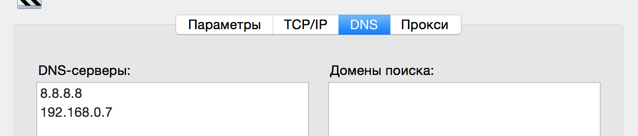
2. When connecting a VPN, the corporate DNS 192.168.0.7 was automatically set. And although all the traffic had to go, it seemed, not through a VPN, all the websites stopped opening. This was decided by adding a Google-DNS DNS 8.8.8.8 and raising it to the very top.
Source: https://habr.com/ru/post/272461/
All Articles