Network equipment at risk? Let's understand ...
Recently, we have been seeing a certain marketing hype around attacks and vulnerabilities in network equipment. Often this is due to quite real events, but most often we are talking about low-level PR-activity of individual researchers or entire companies, which thus assert themselves, parasitizing on not very active coverage of this topic among professionals who are not always able to separate the wheat from the chaff. As a leading manufacturer of network equipment, we decided to raise the veil of secrecy and dot the i in question about the possibility or impossibility of attacks on network equipment, taking as an example the products of Cisco.
SYNful Knock: what is it and what does it eat?
In September 2015, the American company Mandiant, which is part of FireEye, which recently justified a decline in sales of its equipment by the fact that Chinese hackers decreased their activity, published a note on its blog detailed study of the incident with the detected changed firmware of the Cisco IOS operating system on routers in some countries of the world. Mandiant called his note “SYNful Knock - A Cisco router implant”, which led to another demonstration of the superficial understanding of individual researchers of what the network equipment and its security are. In particular, Ilya Medvedovsky, General Director of the Russian company Digital Security, which calls itself “the leading Russian information security consulting company,” commenting on the study of Mandiant, said: “ Cisco itself was forced to admit the fact of the actual detection of the so-called“ implant ”by its customers. "In the style of the NSA, or a hardware rootkit for their network equipment ." However, neither of the implant, and especially the hardware, which was mentioned in the quotation of Mr. Medvedovsky, was not discussed in the Mandiant study. What did Mandiant unearth?
We must immediately say that there is no talk of any kind of vulnerability of network equipment! A successful attacker requires a Cisco router administrator account (and not a switch, as some media outlets wrote) or physical access to equipment. About this, Cisco wrote back in August, a month before the study of Mandiant, by publishing a warning .
')
You will be surprised if someone tells you that someone, having obtained the login and password of the PC administrator, reinstalled the OS on it or installed malware? Most likely no. This is a fairly obvious threat, often implemented in practice. And the recommendation to keep secret the admin password has long belonged to the unfading classics. Why, then, with respect to network equipment, a similar threat is not considered, and the recommendation to store the admin password raises questions? How does a router or switch differ in terms of the principles of ensuring its security from a mobile device or personal computer?
In the case of SYNful Knock, namely, the incident / malicious code identified by Mandiant was named, the attacker was able to install a pre-prepared image of the operating system on the router (could it be called a hardware implant ?!) that contained a number of malicious modules that dealt with various tasks:
To identify the SYNful Knock, several fairly simple mechanisms and recommendations were proposed:
16M 0x40000000: 0x41FFFFFF 0x00000000: 0x01FFFFFF CacheMode = 3, RO, Valid
1M 0x42000000: 0x421FFFFF 0x02000000: 0x021FFFFF CacheMode = 3, RO, Valid
1M 0x42200000: 0x423FFFFF 0x02200000: 0x023FFFFF CacheMode = 3, RO, Valid
1M 0x42400000: 0x425FFFFF 0x02400000: 0x025FFFFF CacheMode = 3, RO, Valid
64K 0x42600000: 0x4261FFFF 0x02600000: 0x0261FFFF CacheMode = 3, RO, Valid
64K 0x42620000: 0x4263FFFF 0x02620000: 0x0263FFFF CacheMode = 3, RO, Valid
The result of this signature is shown below:

According to the currently available information, SYNful Knock did not cause serious damage, and its distribution area (number of affected network devices) was limited and amounted to 163 devices according to Shadowserver (out of ten million devices sold this generation) as of September 20, 2015.
Cisco incident history
However, SYNful Knock was not the first information security incident with Cisco networking products. In total, over the past 4 years, we have identified six incidents involving the infection of our equipment with malicious code. All of them reflect the efforts of seriously minded intruders trying to attack different Cisco platforms in various ways.
But ... Before describing these incidents in a little more detail, I would like to make an important remark, which I already did, describing the incident with the SYNful Knock. In none of the cases mentioned, was there any known or unknown vulnerability in Cisco software. In all cases recorded by us or our customers, either the compromised / stolen network administrator accounts or physical access to the equipment with Cisco IOS were used for the attack.
The table below summarizes all 6 incidents with our equipment recorded in the last 4 years. Color reflects the complexity of the implementation (green - low, red - high). The “static” infection method means that it is a modification of an IOS image stored on the device. "In the process of execution" in turn means that it is a question of changing the code in memory (if the operating system image itself does not change). “Remote detection” means the ability to remotely identify malicious code on network equipment by scanning it itself or its network traffic, as demonstrated above in the section describing SYNful Knock.

Historically, the first two incidents (options 0 and 1) turned out to be the simplest from the technical point of view. They were aimed at specific customers using the Cisco ISR 2800, 3825 and 3845 routers models already 5 years ago. The attackers simply replaced the IOS image loaded on the device. It is rather easy to deal with similar incidents - you just need to verify the IOS code loaded on the network equipment, which will be discussed later.
Options 2 and 3 turned out to be technically more difficult - the attackers, using a compromised administrator account, were able to modify part of the IOS code in the memory of the Cisco 7600 routers, using some of the hardware debugging capabilities. The main purpose of the implemented code was to capture and redirect IPv4 packets according to the criteria set by the attacker. The second goal of the malicious code was the implementation of NAT to allow intruders to access the internal network from the outside, from the Internet. Verification of the downloadable IOS code in this case does not help anymore, since the operating system on the device is not subject to change - the malicious code works only in memory, during execution. On the other hand, after the device is rebooted, this code, which was modified in memory, stops functioning. In both incidents, it is possible to neutralize the repetition problem by using traditional measures to protect administrative access to equipment and authorize access by privileged users, as well as using the functions of monitoring anomalous behavior in memory, which will also be discussed below.
The 4th variant was similar to the previous two in the way it hit the router (subject to the Cisco 1800, 3800 and 7200 models). However, it was the first and so far the only one in which we found that the malicious code was resistant to rebooting the device and updating its software (by finding the malicious code in the modified ROMMON update code). One of the parts of the malicious code, as well as in previous incidents, was responsible for redirecting traffic of interest to intruders by encapsulating it in ICMP, while the other part of the code was completely new. It was built on a modular architecture and allowed to load, if necessary, new functional parts. When the device was rebooted, these modules had to be loaded again, for which the basic part of the malicious code, “sitting” in the modified ROMMON update, was responsible. You can protect yourself from this variant of the malicious code using the measures described for options from zero to third, or simply by neutralizing the modified ROMMON update by installing a regular update (knowingly, Cisco implemented a digital signature engine for the ROMMON updates and IOS operating system images, but on previous platforms generational checks must be activated manually).
Finally, the last, 5th option, also known as the SYNful Knock, was similar to incidents 0, 1, 2 and 3. Its difference was that it used TCP, rather than ICMP, to communicate with the management servers. For some reason, this is not the most difficult option, received wide press coverage. Although the number of routers infected by it (only the Cisco 1841, 2811 and 3825 models were affected) was about one hundred and fifty devices out of ten million sold during the entire existence of this generation. Is it a lot? Not really. For example, in a geographically distributed network of Cisco 40 thousand routers. For companies with offices in two or three dozen countries, the number of routers is about one or two hundred. So maybe SYNful Knock was found in just one customer, and not in a multitude, as some domestic “experts” wrote? This is quite a reasonable assumption, since only one customer suffered in the same variant No. 3.
A brief educational program before starting a serious conversation
And here it is time to step aside a little to one side and give a brief explanation regarding what Cisco network equipment is today. Let me start with the question: “What Microsoft operating systems do you know?” “Windows”, you will answer and you will be wrong. Even if you do not take into account MS DOS, then even Windows from Microsoft, there are several. There is Windows 3.11, there is Windows 95, there is Windows NT, there is Windows 2000, there is Windows 7, there is Windows 8, there is Windows CE, there is Windows Embedded, there is, finally, Windows 10 (and this is not all Windows). And this is not the same OS - in some places they differ very, very much (and not only in the graphical interface). That's the way Cisco has - we have several operating system networks. There is an IOS, there is a CatOS, there is an AsyncOS, there is a Firepower OS, there is an NX OS. And even IOS is different - IOS, IOS XE, IOS XR. And quite different. The same IOS XR, although it has three letters in common in the name, has little in common with the usual IOS. IOS XR is based on QNX, while IOS XE is based on Linux, and IOS is based on BSDi. By the way, in all the incidents described above, including SYNful Knock, only Cisco IOS attacked so far - no incidents were recorded against IOS XE, IOS XR, NX-OS and our other platforms.
Therefore, when any researcher or company categorically declares that they “hacked iOS”, this is either a sign of incompetence and a misunderstanding that we have many different modifications of our underlying operating system, or a banal desire to embellish and advertise for loud news. But besides different IOS, there are also its various layouts, differing in functionality (IP Base, IP Services, IP Voice, Advanced Security, Service Provider Services, etc.). Well, there are a lot of iOS versions too. For example, if someone writes in his study about the vulnerability of version IOS 15.1, then I have a logical question - which version of 15.1 specifically? 15.1 (1) SY5.27 or 15.1 (1) SY6 or 15.1 (2) SY5.32 or 15.1 (4) M11? This is all different software, although it refers to iOS 15.1. I can argue that Cisco probably uses the unification of separate code fragments that migrate from product to product, from platform to platform, from version to version. Yes, there are such fragments. But in spite of this, no universal malware or vulnerability has yet been discovered for all Cisco software.
Well, when someone says "we hacked Cisco", then it is worth asking gently what exactly was hacked, and whether it really is Cisco. And then, for example, the previously mentioned Russian company Digital Security published the report “Security of subscriber equipment of telecommunication networks” in the fall of 2014, and for some reason, Linksys called Cisco equipment there, putting an equal sign between them. However, the Linksys division was sold to Belkin in the spring of 2013, that is, a year and a half before the publication of the report by domestic “researchers” and had no formal relationship with Cisco. From the actual point of view, having acquired Linksys, Cisco has never integrated it into its business, making it separate and aimed only at home users. Even the development teams and development processes at Cisco and Linksys were different. But it’s probably impossible to blame Digital Security for that. Still, writing about the insecurity of Cisco equipment is much cooler than the same about Linksys, Cisco does not belong to Cisco.
Is it easy to attack network equipment?
Realizing that the Cisco network equipment is a very heterogeneous environment with different types of operating systems, their assemblies and versions, it is worth going back to the original task that I mentioned in the very first paragraph, and ask the global question: "How vulnerable / protected are the network equipment in general? ?
Let's start the year 2000. Then, Cisco released the first version of its security architecture for enterprise Cisco SAFE (Security Architecture for Enterprise) design guide, which described the key design principles and basic axioms that formed the basis of the Cisco secure network architecture.
One of these axioms was "A target for attackers could be any IP device ." Already in the first version of Cisco SAFE, by the way, translated into Russian, it was said about the need for close attention to the security of routers and switches.


Even then, we urged to seriously consider network equipment as a potential target for implementing various unauthorized actions against it - from denial of service attacks and traffic interception to privilege escalation and unauthorized access.
Is it easy to attack a router or switch? Yes, they are not based on the most widely used Windows operating system. But you can't call the principles of their work behind secret. Recall what I wrote above. At the heart of different variants of IOS are BSDi, Linux, QNX. Can they be considered completely invulnerable and free from shortcomings? Alas, it is impossible. Is it then surprising that in network equipment built on the OS database (albeit seriously modified in recent years), sometimes there are certain problems that can lead to real incidents? It's just that the number of such incidents is disproportionately less than blown sensations and just published Cisco PSIRT (and what it is, I'll write below) vulnerability bulletins.
History of “sensations” about shellcodes, rootkits, and other problems in Cisco hardware
Remember the important note about the Cisco hardware incident described above? They were only possible with physical access to the equipment or theft of an administrator account. From a practical point of view, this is important, as there are simply published a lot of stories about researchers who dug out the “any Cisco” method or described the theoretical possibility of creating a rootkit for Cisco equipment, or even demonstrated shellcode for individual, as a rule, irrelevant IOS versions.
But in practice one has to deal with the fact that all these stories have a number of similar signs:
Are these stories interesting from a practical point of view? To researchers, yes. The media, yes. To the manufacturer - no longer, since by the time such publications were published, the manufacturer had long ago issued recommendations on how to protect against such threats, fix software, if necessary, and send out notifications to all of its customers who have signed up to receive them. By the way, anyone can subscribe to them. To consumers, as a rule, not so much, as in the real world, many of the described methods of exploiting public vulnerabilities do not work or are very much limited by operating conditions. This is often forgotten by various enthusiasts who, for the sake of a “fan”, for the sake of PR or just interest, are trying to study equipment that has fallen into their hands that they don’t even know how to properly configure or how to upload the latest version of Cisco IOS to it. It was more relevant and interesting even to the manufacturer.
For example, it publishes a certain explorer with information about the exploitation of the vulnerability in the Tcl interpreter in the IOS version 15.1 operating system on the Catalyst 6500 kernel switch. This vulnerability allows an attacker to obtain privileged user (administrator) rights and execute privileged commands. Having received a working code, a researcher or his company, which has become accustomed to making a name for itself on “exaggerated sensations” and loud statements, did not even bother to contact the manufacturer of network equipment, hastily throws the “roast fact” in the media, which is actively discussed and distributed on the Internet . Many experts, without having experience in network equipment research, trust such statements, because they cannot verify them, and they trust the company's “first in Russia” opinion, believing that the company is unlikely to write a lie (although we have already seen above that researchers do not always understand serious corporate or carrier network equipment as well as Chinese modems or other consumer goods that you can buy for research on any radio market).
But let's face it. The vulnerability in the Tcl interpreter has been known for a long time and even has its CVE identifier. That is, a statement about the found vulnerabilities are frank lies, made only for their own PR. Is this a serious vulnerability and does it allow, as the researchers write, to gain complete control over the network device? Cisco PSIRT refers to its moderate hazard level. Can any intruder take advantage of it? Not. At least because this vulnerability in the specified version of IOS 15.1 at the time of publication of the study was already eliminated (as in others, it is susceptible). Version 15.1 itself (although we don’t know which version of 15.1 we are talking about) is no longer relevant.
I will not write about the need to get into the core of the internal network of the enterprise where the Catalyst 6500 switch is used as the basis for the study, since it may not be so difficult using various social engineering techniques (although under operating conditions, vulnerability would cost mention). But it’s worth saying about the existence of temporary restrictions under which this vulnerability can be used at all. Not at any time, vulnerability can be exploited, which also narrows its scope.
Another example is the “sensational” report by Sebastien Muniz (Sebastien Muniz) at the EUSecWest conference in May of 2008, where a “rootkit” for Cisco equipment was presented . In general, for iOS, rootkits have been talked about for a long time, and Muniz was one of the first to develop its prototype. Everything would be fine, but it was done not by using any vulnerabilities, but by modifying the IOS image loaded onto the network device. Yes, the same option as in the incidents described above that were discovered by Cisco or our customers. And this possibility long before the Municipality was demonstrated by a well-known Cisco equipment researcher named FX (for example, on BlackHat in 2003). And even then a simple neutralization mechanism existed against it, such as verification of the IOS image, which could be carried out both offline (outside the device itself) and on the device itself (using the verify command). In essence, this is not about a vulnerability, which Cisco PSIRT wrote about in its bulletin , but about an interesting feature that can be implemented in practice if you do not follow the well-described recommendations for protecting Cisco network equipment.
In general, this is one of the most popular disadvantages of beginning researchers. Having “found” a vulnerability (which, perhaps, has already been published on the Cisco website for a long time), researchers either consciously or unknowingly forget to specify the source data for which it was found or exploited. But this depends very much on whether it will be possible to repeat this experiment in real life or it will not go beyond the limits of laboratory conditions.
And, finally, the immature researchers part of forget about such a thing as “initial level of security”, meaning that a considerable number of protection mechanisms can be “raised” in the network equipment, further narrowing the capabilities of the attacker. In other words, it turns out that vulnerability has long been known and has been eliminated, while researchers in greenhouse conditions are still trying to exploit it, and then bring their research to the public, presenting it as something unique and long-awaited.From the point of view of real security, vulnerability no longer carries any danger, but PR is PR. Sometimes just for the sake of not being forgotten about the researcher or the company, such studies are clothed in a beautiful wrapper, for which there is nothing.
In other words, from the point of view of a security specialist who works at an enterprise and who is interested in information about the security of its network equipment, it’s worth exploring not only the press releases of the researchers, but also information about the elimination of the hole and about the restrictions on its use, which the manufacturer gives .
Cisco PSIRT
Our Cisco PSIRT Security Product Response Team (Product Security Incident Response Team) regularly publishes information on all issues found in various Cisco solutions on a special website - www.cisco.com/security .
If you go to it, you can see constantly updated information about various vulnerabilities in different products of different versions.It also indicates a lot of related information, for example, about the conditions under which this vulnerability can be implemented, in which software version, where to download the patch for its elimination, links to the base of defects (bugs), etc.
And of course for each vulnerability given information about how to fix it. Do not forget that the security of a solution is determined not by the number of vulnerabilities in it, but by the built process of their elimination.

By the way, about the process of eliminating vulnerabilities. Among researchers, who pursue not only PR, but think about real, and not about declared security, there is the practice of interacting with the manufacturer of the equipment that has this or that problem. There is such a practice and Cisco. According to our policydisclosing information about vulnerabilities, we are ready to cooperate with any researcher or company that has found vulnerabilities in our equipment. The same FX actively interacts with us and does not publish any “sensations” before communicating with PSIRT.
From Russian companies I can name Positive Technologies, which has been fruitfully cooperating with us for a long time, finding in the process of rendering its consulting services and sending us information about vulnerabilities in our various products. Recently, we received about fifteen such notifications from Positive Technologies.varying in hazard level from negligible to high. The company Positive Technologies in this context is an example of a mature approach to the study of software for vulnerability and responsible attitude to software users, which contains vulnerabilities that are disclosed only to the manufacturer. But twice already mentioned domestic Digital Security is not addressed in Cisco PSIRT never about the vulnerabilities it found various problems in our equipment! Moreover, when Cisco PSIRT specialists, on their own initiative, contacted Digital Security about a recent report on ZeroNights about the allegedly discovered vulnerability in Cisco equipment, Digital Security representatives could not answer or provide details of their research.
What does Cisco do?
If we are already talking about Cisco PSIRT, then we can’t help mentioning our other initiatives to ensure the security of our network equipment. But first I want to return to the educational program again.
We should add to the story about types, builds and IOS versions that there is no such general concept as a “Cisco router” (the same applies to switches). When reading reports on any studies, it is always necessary to clarify which particular line and model of network equipment in question, what was the configuration of the equipment, how was the impact. We have ISR, ASR, GSR, CSR, CRS. The most popular line is the ISR (Integrated Services Router) router, which, by surprise, also comes from different generations. Recently, we offer customers the third generation of Cisco ISR routers - ISR 4k (aka ISR 4000). Production of the first generation of Cisco ISR (models 1800, 2800 and 3800), namely, it appeared in all the above incidents, including the SYNful Knock, ended five years ago, in 2010.From which it follows a completely logical and logical conclusion - in the Cisco equipment now being acquired, many of the incidents described earlier are impossible in principle. Why do I make such a conclusion?
Everything is very simple. The first generation of Cisco ISR routers appeared in 2004, when security measures for our own products were episodic and non-systemic. Although already then we had the function of signing the image ( Digital Image Signing ) to protect it from unauthorized changes or substitution, but not everywhere. Now this functionality is present in 560 different Cisco products.

In 2007, we had the first implementation of the ACT hardware module, designed to monitor the integrity of equipment and protection against counterfeit products, which sometimes began to appear on the market, having a Far Eastern origin. In 2008, we introduced a secure development process to Cisco (Cisco Secure Development Lifecycle,CSDL ), and a year later, the second generation of Cisco ISR G2 routers (1900, 2900 and 3900) came into being, with much more functionality to protect itself. And it is at the hardware level. In particular, the ACT module was transformed into the so-called Trust Anchor module (“trust anchor”), which is now implemented in almost 300 Cisco products. The secure, trusted Secure Boot boot feature , which allows you to verify the software integrity of the device, was first implemented in 2010, and today it is an integral part of the development process for most Cisco products.

Similar security changes were made to software. For example, only between the 10th and 12th versions of IOS (and the current version starts already with the number 15) several thousand (!) Intermediate versions of our network operating system were released, not only eliminating certain errors detected during testing and exploitation, but also expanding the protective functionality, taking into account the changing nature of malicious code and actions of intruders. For example, if a verification mechanism and secure boot is enough to protect against static IOS image replacement, then we developed a special monitor to combat malicious code running in memory, which monitors suspicious and abnormal activity in the network device memory. Also to combat in-memory malicious codeWe have eliminated a number of debugging commands that are unnecessary during the normal operation of the device, but give the attackers additional opportunities to implement their black cases. By the way, the study of all these protective functions is mandatory and is part of Cisco Security Ninja, which I already wrote about.
As we developed, we were able not only to enhance the protective potential of our equipment, but also to bring additional capabilities to other processes related to the support of Cisco equipment. These include:
What should I do to protect my infrastructure based on Cisco equipment?
But to answer this question, I will dedicate a separate note in the very near future ...
As a summary
With this small note we have opened a series of publications devoted to how the security of network equipment is arranged and how it can be improved. In the following article, we will look in detail at the steps that any Cisco equipment user can take to prevent the problems mentioned in this material. In the meantime, I would like to summarize it with the following statement: a target can be anything, including a switch with a router. Do not neglect the provision of their protection, a description of the capabilities of which can be found at the manufacturer. Well, I would recommend researchers to be more responsible in publishing information about the vulnerability of network equipment that could be used by attackers to harm users.
Additional Information:
SYNful Knock: what is it and what does it eat?
In September 2015, the American company Mandiant, which is part of FireEye, which recently justified a decline in sales of its equipment by the fact that Chinese hackers decreased their activity, published a note on its blog detailed study of the incident with the detected changed firmware of the Cisco IOS operating system on routers in some countries of the world. Mandiant called his note “SYNful Knock - A Cisco router implant”, which led to another demonstration of the superficial understanding of individual researchers of what the network equipment and its security are. In particular, Ilya Medvedovsky, General Director of the Russian company Digital Security, which calls itself “the leading Russian information security consulting company,” commenting on the study of Mandiant, said: “ Cisco itself was forced to admit the fact of the actual detection of the so-called“ implant ”by its customers. "In the style of the NSA, or a hardware rootkit for their network equipment ." However, neither of the implant, and especially the hardware, which was mentioned in the quotation of Mr. Medvedovsky, was not discussed in the Mandiant study. What did Mandiant unearth?
We must immediately say that there is no talk of any kind of vulnerability of network equipment! A successful attacker requires a Cisco router administrator account (and not a switch, as some media outlets wrote) or physical access to equipment. About this, Cisco wrote back in August, a month before the study of Mandiant, by publishing a warning .
')
You will be surprised if someone tells you that someone, having obtained the login and password of the PC administrator, reinstalled the OS on it or installed malware? Most likely no. This is a fairly obvious threat, often implemented in practice. And the recommendation to keep secret the admin password has long belonged to the unfading classics. Why, then, with respect to network equipment, a similar threat is not considered, and the recommendation to store the admin password raises questions? How does a router or switch differ in terms of the principles of ensuring its security from a mobile device or personal computer?
In the case of SYNful Knock, namely, the incident / malicious code identified by Mandiant was named, the attacker was able to install a pre-prepared image of the operating system on the router (could it be called a hardware implant ?!) that contained a number of malicious modules that dealt with various tasks:
- The redirection of traffic that falls under certain criteria established by the attacker. This was the main "payload" SYNful Knock.
- Providing NAT for external access to the network equipment installed inside.
- Obfuscation, for example, by hiding malicious activity in the process list.
- Encapsulating commands from attackers and responses to them in specially crafted TCP packets sent to the router interface.
To identify the SYNful Knock, several fairly simple mechanisms and recommendations were proposed:
- Analyzing the result of the show platform | include RO, Valid "on the router. The infected router should not produce any results or produce something similar to:
16M 0x40000000: 0x41FFFFFF 0x00000000: 0x01FFFFFF CacheMode = 3, RO, Valid
1M 0x42000000: 0x421FFFFF 0x02000000: 0x021FFFFF CacheMode = 3, RO, Valid
1M 0x42200000: 0x423FFFFF 0x02200000: 0x023FFFFF CacheMode = 3, RO, Valid
1M 0x42400000: 0x425FFFFF 0x02400000: 0x025FFFFF CacheMode = 3, RO, Valid
64K 0x42600000: 0x4261FFFF 0x02600000: 0x0261FFFF CacheMode = 3, RO, Valid
64K 0x42620000: 0x4263FFFF 0x02620000: 0x0263FFFF CacheMode = 3, RO, Valid
- Special scanner SYNfulKnock Scanner, written by the research division of Cisco Talos in the form of a script in Python and distributed absolutely free.
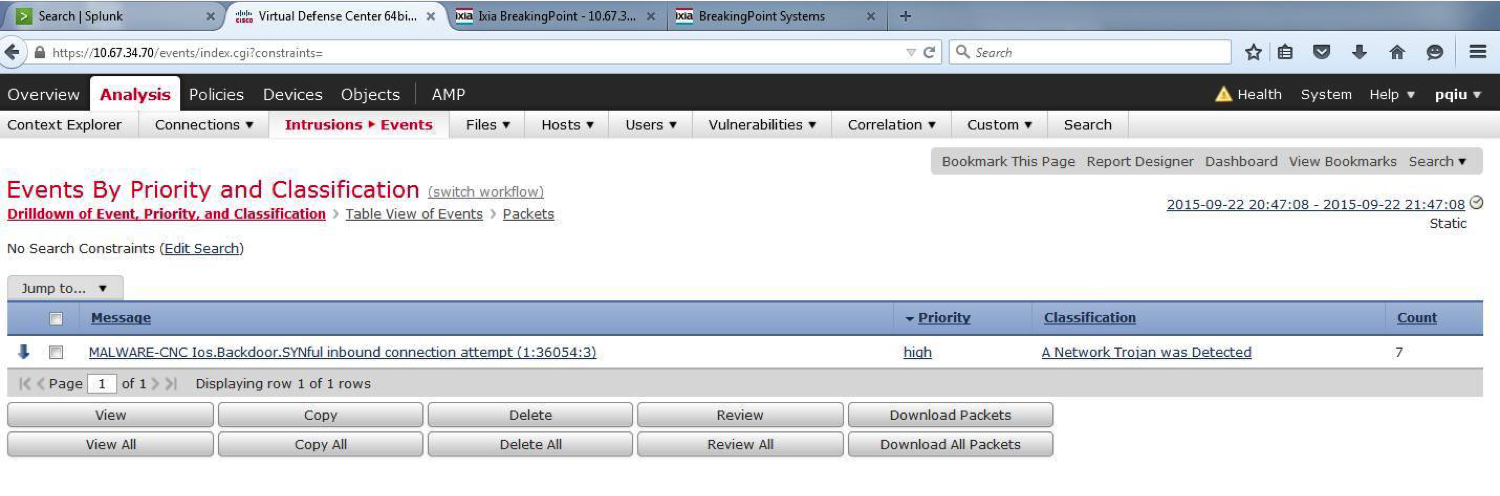
- Signature for Snort attack detection system with SID: 36054 . The Cisco NGIPS intrusion detection system as part of FirePOWER Services on the Cisco ASA, Cisco ISR, Cisco FirePOWER Appliance, Cisco Firepower 9300 and in the virtual version has a similar signature.

The result of this signature is shown below:

According to the currently available information, SYNful Knock did not cause serious damage, and its distribution area (number of affected network devices) was limited and amounted to 163 devices according to Shadowserver (out of ten million devices sold this generation) as of September 20, 2015.
Cisco incident history
However, SYNful Knock was not the first information security incident with Cisco networking products. In total, over the past 4 years, we have identified six incidents involving the infection of our equipment with malicious code. All of them reflect the efforts of seriously minded intruders trying to attack different Cisco platforms in various ways.
But ... Before describing these incidents in a little more detail, I would like to make an important remark, which I already did, describing the incident with the SYNful Knock. In none of the cases mentioned, was there any known or unknown vulnerability in Cisco software. In all cases recorded by us or our customers, either the compromised / stolen network administrator accounts or physical access to the equipment with Cisco IOS were used for the attack.
The table below summarizes all 6 incidents with our equipment recorded in the last 4 years. Color reflects the complexity of the implementation (green - low, red - high). The “static” infection method means that it is a modification of an IOS image stored on the device. "In the process of execution" in turn means that it is a question of changing the code in memory (if the operating system image itself does not change). “Remote detection” means the ability to remotely identify malicious code on network equipment by scanning it itself or its network traffic, as demonstrated above in the section describing SYNful Knock.

Historically, the first two incidents (options 0 and 1) turned out to be the simplest from the technical point of view. They were aimed at specific customers using the Cisco ISR 2800, 3825 and 3845 routers models already 5 years ago. The attackers simply replaced the IOS image loaded on the device. It is rather easy to deal with similar incidents - you just need to verify the IOS code loaded on the network equipment, which will be discussed later.
Options 2 and 3 turned out to be technically more difficult - the attackers, using a compromised administrator account, were able to modify part of the IOS code in the memory of the Cisco 7600 routers, using some of the hardware debugging capabilities. The main purpose of the implemented code was to capture and redirect IPv4 packets according to the criteria set by the attacker. The second goal of the malicious code was the implementation of NAT to allow intruders to access the internal network from the outside, from the Internet. Verification of the downloadable IOS code in this case does not help anymore, since the operating system on the device is not subject to change - the malicious code works only in memory, during execution. On the other hand, after the device is rebooted, this code, which was modified in memory, stops functioning. In both incidents, it is possible to neutralize the repetition problem by using traditional measures to protect administrative access to equipment and authorize access by privileged users, as well as using the functions of monitoring anomalous behavior in memory, which will also be discussed below.
The 4th variant was similar to the previous two in the way it hit the router (subject to the Cisco 1800, 3800 and 7200 models). However, it was the first and so far the only one in which we found that the malicious code was resistant to rebooting the device and updating its software (by finding the malicious code in the modified ROMMON update code). One of the parts of the malicious code, as well as in previous incidents, was responsible for redirecting traffic of interest to intruders by encapsulating it in ICMP, while the other part of the code was completely new. It was built on a modular architecture and allowed to load, if necessary, new functional parts. When the device was rebooted, these modules had to be loaded again, for which the basic part of the malicious code, “sitting” in the modified ROMMON update, was responsible. You can protect yourself from this variant of the malicious code using the measures described for options from zero to third, or simply by neutralizing the modified ROMMON update by installing a regular update (knowingly, Cisco implemented a digital signature engine for the ROMMON updates and IOS operating system images, but on previous platforms generational checks must be activated manually).
Finally, the last, 5th option, also known as the SYNful Knock, was similar to incidents 0, 1, 2 and 3. Its difference was that it used TCP, rather than ICMP, to communicate with the management servers. For some reason, this is not the most difficult option, received wide press coverage. Although the number of routers infected by it (only the Cisco 1841, 2811 and 3825 models were affected) was about one hundred and fifty devices out of ten million sold during the entire existence of this generation. Is it a lot? Not really. For example, in a geographically distributed network of Cisco 40 thousand routers. For companies with offices in two or three dozen countries, the number of routers is about one or two hundred. So maybe SYNful Knock was found in just one customer, and not in a multitude, as some domestic “experts” wrote? This is quite a reasonable assumption, since only one customer suffered in the same variant No. 3.
A brief educational program before starting a serious conversation
And here it is time to step aside a little to one side and give a brief explanation regarding what Cisco network equipment is today. Let me start with the question: “What Microsoft operating systems do you know?” “Windows”, you will answer and you will be wrong. Even if you do not take into account MS DOS, then even Windows from Microsoft, there are several. There is Windows 3.11, there is Windows 95, there is Windows NT, there is Windows 2000, there is Windows 7, there is Windows 8, there is Windows CE, there is Windows Embedded, there is, finally, Windows 10 (and this is not all Windows). And this is not the same OS - in some places they differ very, very much (and not only in the graphical interface). That's the way Cisco has - we have several operating system networks. There is an IOS, there is a CatOS, there is an AsyncOS, there is a Firepower OS, there is an NX OS. And even IOS is different - IOS, IOS XE, IOS XR. And quite different. The same IOS XR, although it has three letters in common in the name, has little in common with the usual IOS. IOS XR is based on QNX, while IOS XE is based on Linux, and IOS is based on BSDi. By the way, in all the incidents described above, including SYNful Knock, only Cisco IOS attacked so far - no incidents were recorded against IOS XE, IOS XR, NX-OS and our other platforms.
Therefore, when any researcher or company categorically declares that they “hacked iOS”, this is either a sign of incompetence and a misunderstanding that we have many different modifications of our underlying operating system, or a banal desire to embellish and advertise for loud news. But besides different IOS, there are also its various layouts, differing in functionality (IP Base, IP Services, IP Voice, Advanced Security, Service Provider Services, etc.). Well, there are a lot of iOS versions too. For example, if someone writes in his study about the vulnerability of version IOS 15.1, then I have a logical question - which version of 15.1 specifically? 15.1 (1) SY5.27 or 15.1 (1) SY6 or 15.1 (2) SY5.32 or 15.1 (4) M11? This is all different software, although it refers to iOS 15.1. I can argue that Cisco probably uses the unification of separate code fragments that migrate from product to product, from platform to platform, from version to version. Yes, there are such fragments. But in spite of this, no universal malware or vulnerability has yet been discovered for all Cisco software.
Well, when someone says "we hacked Cisco", then it is worth asking gently what exactly was hacked, and whether it really is Cisco. And then, for example, the previously mentioned Russian company Digital Security published the report “Security of subscriber equipment of telecommunication networks” in the fall of 2014, and for some reason, Linksys called Cisco equipment there, putting an equal sign between them. However, the Linksys division was sold to Belkin in the spring of 2013, that is, a year and a half before the publication of the report by domestic “researchers” and had no formal relationship with Cisco. From the actual point of view, having acquired Linksys, Cisco has never integrated it into its business, making it separate and aimed only at home users. Even the development teams and development processes at Cisco and Linksys were different. But it’s probably impossible to blame Digital Security for that. Still, writing about the insecurity of Cisco equipment is much cooler than the same about Linksys, Cisco does not belong to Cisco.
Is it easy to attack network equipment?
Realizing that the Cisco network equipment is a very heterogeneous environment with different types of operating systems, their assemblies and versions, it is worth going back to the original task that I mentioned in the very first paragraph, and ask the global question: "How vulnerable / protected are the network equipment in general? ?
Let's start the year 2000. Then, Cisco released the first version of its security architecture for enterprise Cisco SAFE (Security Architecture for Enterprise) design guide, which described the key design principles and basic axioms that formed the basis of the Cisco secure network architecture.

One of these axioms was "A target for attackers could be any IP device ." Already in the first version of Cisco SAFE, by the way, translated into Russian, it was said about the need for close attention to the security of routers and switches.


Even then, we urged to seriously consider network equipment as a potential target for implementing various unauthorized actions against it - from denial of service attacks and traffic interception to privilege escalation and unauthorized access.
Is it easy to attack a router or switch? Yes, they are not based on the most widely used Windows operating system. But you can't call the principles of their work behind secret. Recall what I wrote above. At the heart of different variants of IOS are BSDi, Linux, QNX. Can they be considered completely invulnerable and free from shortcomings? Alas, it is impossible. Is it then surprising that in network equipment built on the OS database (albeit seriously modified in recent years), sometimes there are certain problems that can lead to real incidents? It's just that the number of such incidents is disproportionately less than blown sensations and just published Cisco PSIRT (and what it is, I'll write below) vulnerability bulletins.
History of “sensations” about shellcodes, rootkits, and other problems in Cisco hardware
Remember the important note about the Cisco hardware incident described above? They were only possible with physical access to the equipment or theft of an administrator account. From a practical point of view, this is important, as there are simply published a lot of stories about researchers who dug out the “any Cisco” method or described the theoretical possibility of creating a rootkit for Cisco equipment, or even demonstrated shellcode for individual, as a rule, irrelevant IOS versions.
But in practice one has to deal with the fact that all these stories have a number of similar signs:
- They are based on public information about vulnerabilities already published on the Cisco website.
- They usually apply to irrelevant versions of Cisco network operating systems.
- They mainly concern only Cisco IOS, and not IOS XE, IOS XR or NX-OS.
- They are based on research in the laboratory, far from real life and real settings.
- They do not take into account the software and hardware protection mechanisms available in Cisco equipment.
Are these stories interesting from a practical point of view? To researchers, yes. The media, yes. To the manufacturer - no longer, since by the time such publications were published, the manufacturer had long ago issued recommendations on how to protect against such threats, fix software, if necessary, and send out notifications to all of its customers who have signed up to receive them. By the way, anyone can subscribe to them. To consumers, as a rule, not so much, as in the real world, many of the described methods of exploiting public vulnerabilities do not work or are very much limited by operating conditions. This is often forgotten by various enthusiasts who, for the sake of a “fan”, for the sake of PR or just interest, are trying to study equipment that has fallen into their hands that they don’t even know how to properly configure or how to upload the latest version of Cisco IOS to it. It was more relevant and interesting even to the manufacturer.
For example, it publishes a certain explorer with information about the exploitation of the vulnerability in the Tcl interpreter in the IOS version 15.1 operating system on the Catalyst 6500 kernel switch. This vulnerability allows an attacker to obtain privileged user (administrator) rights and execute privileged commands. Having received a working code, a researcher or his company, which has become accustomed to making a name for itself on “exaggerated sensations” and loud statements, did not even bother to contact the manufacturer of network equipment, hastily throws the “roast fact” in the media, which is actively discussed and distributed on the Internet . Many experts, without having experience in network equipment research, trust such statements, because they cannot verify them, and they trust the company's “first in Russia” opinion, believing that the company is unlikely to write a lie (although we have already seen above that researchers do not always understand serious corporate or carrier network equipment as well as Chinese modems or other consumer goods that you can buy for research on any radio market).
But let's face it. The vulnerability in the Tcl interpreter has been known for a long time and even has its CVE identifier. That is, a statement about the found vulnerabilities are frank lies, made only for their own PR. Is this a serious vulnerability and does it allow, as the researchers write, to gain complete control over the network device? Cisco PSIRT refers to its moderate hazard level. Can any intruder take advantage of it? Not. At least because this vulnerability in the specified version of IOS 15.1 at the time of publication of the study was already eliminated (as in others, it is susceptible). Version 15.1 itself (although we don’t know which version of 15.1 we are talking about) is no longer relevant.
I will not write about the need to get into the core of the internal network of the enterprise where the Catalyst 6500 switch is used as the basis for the study, since it may not be so difficult using various social engineering techniques (although under operating conditions, vulnerability would cost mention). But it’s worth saying about the existence of temporary restrictions under which this vulnerability can be used at all. Not at any time, vulnerability can be exploited, which also narrows its scope.
Another example is the “sensational” report by Sebastien Muniz (Sebastien Muniz) at the EUSecWest conference in May of 2008, where a “rootkit” for Cisco equipment was presented . In general, for iOS, rootkits have been talked about for a long time, and Muniz was one of the first to develop its prototype. Everything would be fine, but it was done not by using any vulnerabilities, but by modifying the IOS image loaded onto the network device. Yes, the same option as in the incidents described above that were discovered by Cisco or our customers. And this possibility long before the Municipality was demonstrated by a well-known Cisco equipment researcher named FX (for example, on BlackHat in 2003). And even then a simple neutralization mechanism existed against it, such as verification of the IOS image, which could be carried out both offline (outside the device itself) and on the device itself (using the verify command). In essence, this is not about a vulnerability, which Cisco PSIRT wrote about in its bulletin , but about an interesting feature that can be implemented in practice if you do not follow the well-described recommendations for protecting Cisco network equipment.
In general, this is one of the most popular disadvantages of beginning researchers. Having “found” a vulnerability (which, perhaps, has already been published on the Cisco website for a long time), researchers either consciously or unknowingly forget to specify the source data for which it was found or exploited. But this depends very much on whether it will be possible to repeat this experiment in real life or it will not go beyond the limits of laboratory conditions.
And, finally, the immature researchers part of forget about such a thing as “initial level of security”, meaning that a considerable number of protection mechanisms can be “raised” in the network equipment, further narrowing the capabilities of the attacker. In other words, it turns out that vulnerability has long been known and has been eliminated, while researchers in greenhouse conditions are still trying to exploit it, and then bring their research to the public, presenting it as something unique and long-awaited.From the point of view of real security, vulnerability no longer carries any danger, but PR is PR. Sometimes just for the sake of not being forgotten about the researcher or the company, such studies are clothed in a beautiful wrapper, for which there is nothing.
In other words, from the point of view of a security specialist who works at an enterprise and who is interested in information about the security of its network equipment, it’s worth exploring not only the press releases of the researchers, but also information about the elimination of the hole and about the restrictions on its use, which the manufacturer gives .
Cisco PSIRT
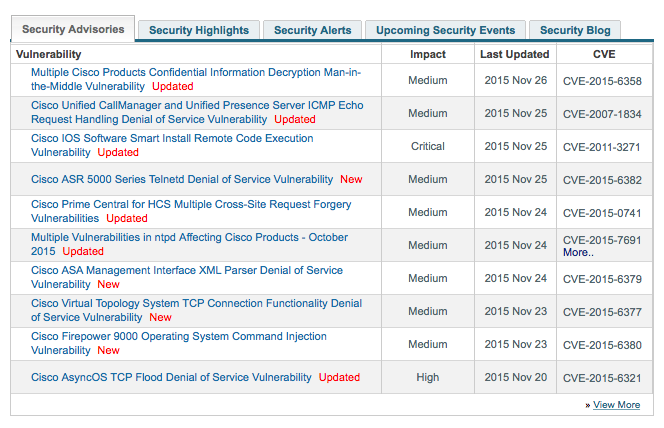
Our Cisco PSIRT Security Product Response Team (Product Security Incident Response Team) regularly publishes information on all issues found in various Cisco solutions on a special website - www.cisco.com/security .

If you go to it, you can see constantly updated information about various vulnerabilities in different products of different versions.It also indicates a lot of related information, for example, about the conditions under which this vulnerability can be implemented, in which software version, where to download the patch for its elimination, links to the base of defects (bugs), etc.

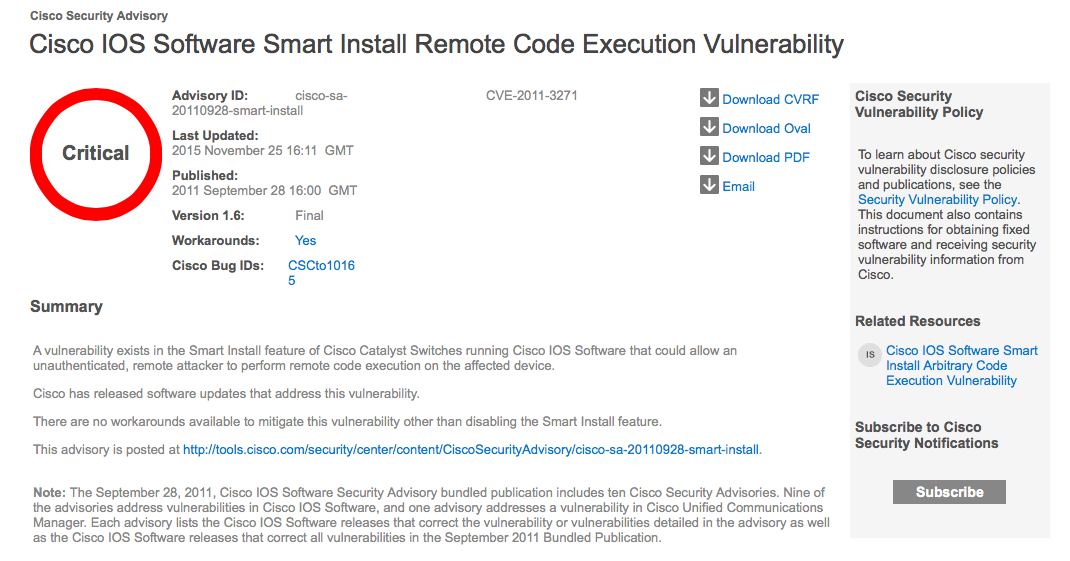
And of course for each vulnerability given information about how to fix it. Do not forget that the security of a solution is determined not by the number of vulnerabilities in it, but by the built process of their elimination.

By the way, about the process of eliminating vulnerabilities. Among researchers, who pursue not only PR, but think about real, and not about declared security, there is the practice of interacting with the manufacturer of the equipment that has this or that problem. There is such a practice and Cisco. According to our policydisclosing information about vulnerabilities, we are ready to cooperate with any researcher or company that has found vulnerabilities in our equipment. The same FX actively interacts with us and does not publish any “sensations” before communicating with PSIRT.
From Russian companies I can name Positive Technologies, which has been fruitfully cooperating with us for a long time, finding in the process of rendering its consulting services and sending us information about vulnerabilities in our various products. Recently, we received about fifteen such notifications from Positive Technologies.varying in hazard level from negligible to high. The company Positive Technologies in this context is an example of a mature approach to the study of software for vulnerability and responsible attitude to software users, which contains vulnerabilities that are disclosed only to the manufacturer. But twice already mentioned domestic Digital Security is not addressed in Cisco PSIRT never about the vulnerabilities it found various problems in our equipment! Moreover, when Cisco PSIRT specialists, on their own initiative, contacted Digital Security about a recent report on ZeroNights about the allegedly discovered vulnerability in Cisco equipment, Digital Security representatives could not answer or provide details of their research.
What does Cisco do?
If we are already talking about Cisco PSIRT, then we can’t help mentioning our other initiatives to ensure the security of our network equipment. But first I want to return to the educational program again.
We should add to the story about types, builds and IOS versions that there is no such general concept as a “Cisco router” (the same applies to switches). When reading reports on any studies, it is always necessary to clarify which particular line and model of network equipment in question, what was the configuration of the equipment, how was the impact. We have ISR, ASR, GSR, CSR, CRS. The most popular line is the ISR (Integrated Services Router) router, which, by surprise, also comes from different generations. Recently, we offer customers the third generation of Cisco ISR routers - ISR 4k (aka ISR 4000). Production of the first generation of Cisco ISR (models 1800, 2800 and 3800), namely, it appeared in all the above incidents, including the SYNful Knock, ended five years ago, in 2010.From which it follows a completely logical and logical conclusion - in the Cisco equipment now being acquired, many of the incidents described earlier are impossible in principle. Why do I make such a conclusion?
Everything is very simple. The first generation of Cisco ISR routers appeared in 2004, when security measures for our own products were episodic and non-systemic. Although already then we had the function of signing the image ( Digital Image Signing ) to protect it from unauthorized changes or substitution, but not everywhere. Now this functionality is present in 560 different Cisco products.

In 2007, we had the first implementation of the ACT hardware module, designed to monitor the integrity of equipment and protection against counterfeit products, which sometimes began to appear on the market, having a Far Eastern origin. In 2008, we introduced a secure development process to Cisco (Cisco Secure Development Lifecycle,CSDL ), and a year later, the second generation of Cisco ISR G2 routers (1900, 2900 and 3900) came into being, with much more functionality to protect itself. And it is at the hardware level. In particular, the ACT module was transformed into the so-called Trust Anchor module (“trust anchor”), which is now implemented in almost 300 Cisco products. The secure, trusted Secure Boot boot feature , which allows you to verify the software integrity of the device, was first implemented in 2010, and today it is an integral part of the development process for most Cisco products.

Similar security changes were made to software. For example, only between the 10th and 12th versions of IOS (and the current version starts already with the number 15) several thousand (!) Intermediate versions of our network operating system were released, not only eliminating certain errors detected during testing and exploitation, but also expanding the protective functionality, taking into account the changing nature of malicious code and actions of intruders. For example, if a verification mechanism and secure boot is enough to protect against static IOS image replacement, then we developed a special monitor to combat malicious code running in memory, which monitors suspicious and abnormal activity in the network device memory. Also to combat in-memory malicious codeWe have eliminated a number of debugging commands that are unnecessary during the normal operation of the device, but give the attackers additional opportunities to implement their black cases. By the way, the study of all these protective functions is mandatory and is part of Cisco Security Ninja, which I already wrote about.
As we developed, we were able not only to enhance the protective potential of our equipment, but also to bring additional capabilities to other processes related to the support of Cisco equipment. These include:
- Development of a special tool for investigating incidents on network equipment and checking it for “harmfulness” (available only to our analysts who help customers who suspect something bad about their equipment).
- Develop recommendations for enhancing the protection of network equipment and monitoring its integrity.
- Development of a special tool used by the Cisco TAC technical support team when communicating with customers, and allowing you to analyze the dumps sent by customers to detect the substitution of the network OS image.
- Launch of a special service for verification of software images installed on Cisco equipment.
- And many others.
What should I do to protect my infrastructure based on Cisco equipment?
But to answer this question, I will dedicate a separate note in the very near future ...
As a summary
With this small note we have opened a series of publications devoted to how the security of network equipment is arranged and how it can be improved. In the following article, we will look in detail at the steps that any Cisco equipment user can take to prevent the problems mentioned in this material. In the meantime, I would like to summarize it with the following statement: a target can be anything, including a switch with a router. Do not neglect the provision of their protection, a description of the capabilities of which can be found at the manufacturer. Well, I would recommend researchers to be more responsible in publishing information about the vulnerability of network equipment that could be used by attackers to harm users.
Additional Information:
Source: https://habr.com/ru/post/272093/
All Articles