IBM launched cloud authentication service Identity Mixer

IBM announced the launch of its new cloud service Identity Mixer, which was announced on the International Day of Personal Data Protection on January 28. The service itself is designed to protect the user's personal data during authentication. On November 20, the company announced that Identity Mixer was available for Bluemix developers.
Modern applications and web services today typically require user authentication, that is, identity verification. During the authentication process, a large amount of information related to the user's identity is usually revealed, and the attacker, with due skill, can intercept this information. Services that store user credentials are often hacked, and then attackers get the data of thousands, or even millions of users. And not only names, but also addresses, insurance data, sometimes even credit card numbers and dates of birth.
For example, to access a streaming application, a user may be asked to confirm that he / she has already turned 18 years old. Usually this means an indication of the full date of birth, and in some cases the name, address and other user data are requested. Data is requested and banking applications, online shopping sites, social networks. In this case, the user has to create a personal profile for each such service or application.
')

If the service / application is hacked, then all this information can be obtained by the attacker. Identity Mixer is designed to protect user data with a focus on the data needed to verify identity. Thanks to a set of algorithms based on the cryptographic work of IBM Research specialists, the tool allows developers to create applications whose authentication is "proof with zero disclosure."
Proof with zero disclosure (information) in cryptography (eng. Zero-knowledge proof) is an interactive cryptographic protocol that allows one of the interactive parties (“The verifier” - Testing) to verify the authenticity of any statement (usually mathematical), without This is no other information from the second side (“The prover” - Proving). Moreover, the latter condition is necessary, since it is usually to prove that a party has certain information, in most cases it is trivial if it has the right to simply disclose information. The whole difficulty consists in proving that one of the parties has information without revealing its content. The protocol must take into account that the Prover will be able to convince the Inspector only if the assertion is indeed proven. Otherwise, it will be impossible to do this, or it is extremely unlikely due to computational complexity. The interactivity of the protocol means the direct exchange of information by the parties.
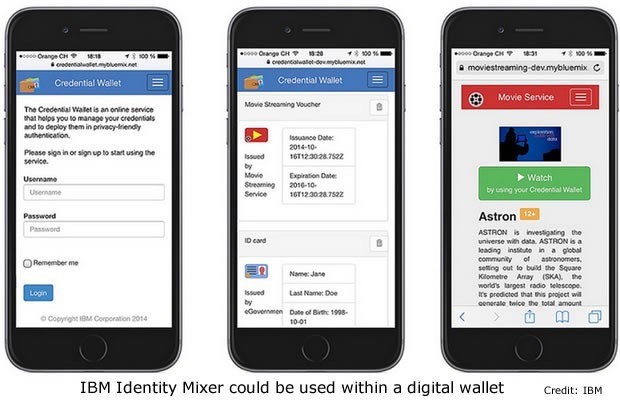
In this case, Identity Mixer authenticates users by requesting the public key. Each user has his own private key, which corresponds to several public keys. Each transaction performed by the user receives its own public key and does not leave any third-party data that may indicate the user's identity. In this case, the user himself can determine which data will be disclosed and to whom.
Thus, if you take all the same streaming service, the user must provide the identifier and subscription data stored in the personal “Data Wallet” (Credential Wallet). To access a movie, for example, users can use an e-wallet to provide all of this data and to easily receive video content.
The result is that the user's personal data is not endangered, and the service does not need to store and protect all third-party data, such as date of birth or name.
Source: https://habr.com/ru/post/272023/
All Articles