New malicious campaign Dridex led to a large number of infections in Europe
Recently, the bank Trojan Dridex was one of the most discussed. This is not surprising, since it has already gained popularity comparable to the well-known banking Trojan Zeus. Dridex is also one of the most serious threats at the moment. Authors are constantly developing their creation to make it more effective.

Dridex, which is also known as Bugat and Cridex, is similar in its workings to bank Zeus-type Trojans, but represents a new stage in the development of this type of malware. To compromise users, attackers use malicious attachments for emails, and this method is used by them both in the case of home users and in the case of corporate users.
This may seem strange, but attackers use the method that was very popular in the late 90s to distribute Dridex: malicious macros in Word and Excel files. This vector of attack is not a thing of the past, but is still used by the authors of Dridex. After the user executes the malicious file, Dridex infects the user's system and includes it in a botnet controlled by intruders. After successfully infecting the system, attackers can steal the user's personal information, such as online banking account information, and send the necessary commands to the bot.
')
Every few weeks, our antivirus lab records the methods by which another cyberband launches a new wave of Trojan distribution for users in various countries. Thanks to our ESET Virus Radar service, we can track those countries that account for the largest number of Trojan infections or those that were targeted by cyber attackers. Each such malicious campaign can cost users of online banking millions of dollars, so for us it is a priority to notify users of the distribution of a new modification of the Trojan as soon as possible.
For some time, we tracked several malicious campaigns using Dridex. Our data show that since August of this year there has been a surge in the activity of intruders using Dridex. High activity persisted in September, October and November.
Dridex distribution statistics on Virus Radar allow us to see that it is one of the most common Trojans in the world today.
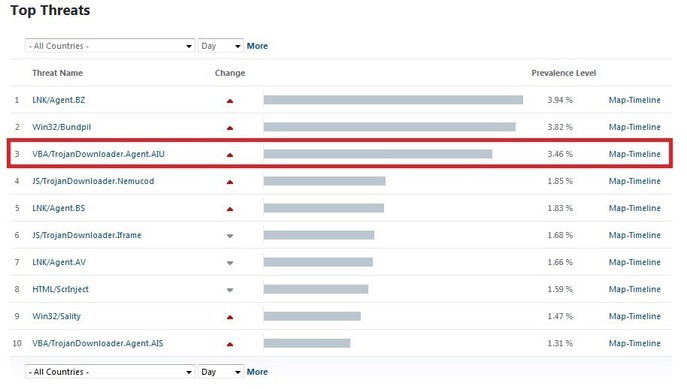
Dridex climbed to the third line very quickly, because a few days ago he was not even on the list. The attackers have achieved the greatest success in infecting users in European countries, especially in Spain and Slovakia, as well as in South Africa.
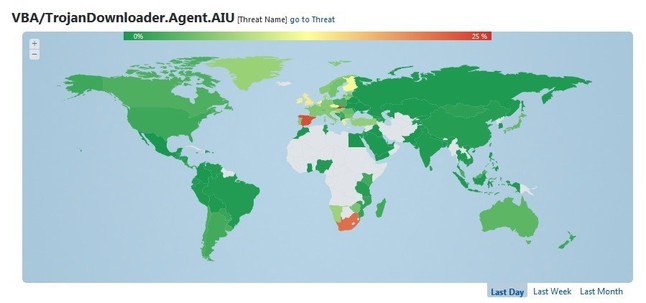
The information above shows us the number of users who tried to open a malicious attachment, but ESET antivirus product detected and blocked it. Since the attackers were successful in various countries of the world, this tells us that the e-mail phishing email with the Trojan was most likely written in English. One may wonder why, for example, users in Spain open e-mail attachments in English, although it is not native to them. It is possible that in this case we can talk about computer literacy of users in various countries of the world. Some users open phishing email attachments just for the sake of curiosity and regardless of who they came from or what data they contain. Fortunately, for some such users, their anti-virus product was able to successfully block the threat before it caused any damage.
The Dridex distribution timeline, shown below, shows that since the moment of a significant increase in its activity, two peaks of activity have been observed: the 13th and 16th of November.

Every new wave of threats like Dridex attracts the attention of law enforcement agencies. Such special and law enforcement services as the NSA, FBI, Europol, GCHQ, and others have repeatedly carried out successful dismantling of botnets and organized raids on cybercriminals who profited from malware.
Our function is also to notify users of a potential threat, which will significantly reduce the risk of infection and loss of funds. We advise users not to click on phishing links or open suspicious email attachments.

Dridex, which is also known as Bugat and Cridex, is similar in its workings to bank Zeus-type Trojans, but represents a new stage in the development of this type of malware. To compromise users, attackers use malicious attachments for emails, and this method is used by them both in the case of home users and in the case of corporate users.
This may seem strange, but attackers use the method that was very popular in the late 90s to distribute Dridex: malicious macros in Word and Excel files. This vector of attack is not a thing of the past, but is still used by the authors of Dridex. After the user executes the malicious file, Dridex infects the user's system and includes it in a botnet controlled by intruders. After successfully infecting the system, attackers can steal the user's personal information, such as online banking account information, and send the necessary commands to the bot.
')
Every few weeks, our antivirus lab records the methods by which another cyberband launches a new wave of Trojan distribution for users in various countries. Thanks to our ESET Virus Radar service, we can track those countries that account for the largest number of Trojan infections or those that were targeted by cyber attackers. Each such malicious campaign can cost users of online banking millions of dollars, so for us it is a priority to notify users of the distribution of a new modification of the Trojan as soon as possible.
For some time, we tracked several malicious campaigns using Dridex. Our data show that since August of this year there has been a surge in the activity of intruders using Dridex. High activity persisted in September, October and November.
Dridex distribution statistics on Virus Radar allow us to see that it is one of the most common Trojans in the world today.

Dridex climbed to the third line very quickly, because a few days ago he was not even on the list. The attackers have achieved the greatest success in infecting users in European countries, especially in Spain and Slovakia, as well as in South Africa.

The information above shows us the number of users who tried to open a malicious attachment, but ESET antivirus product detected and blocked it. Since the attackers were successful in various countries of the world, this tells us that the e-mail phishing email with the Trojan was most likely written in English. One may wonder why, for example, users in Spain open e-mail attachments in English, although it is not native to them. It is possible that in this case we can talk about computer literacy of users in various countries of the world. Some users open phishing email attachments just for the sake of curiosity and regardless of who they came from or what data they contain. Fortunately, for some such users, their anti-virus product was able to successfully block the threat before it caused any damage.
The Dridex distribution timeline, shown below, shows that since the moment of a significant increase in its activity, two peaks of activity have been observed: the 13th and 16th of November.

Every new wave of threats like Dridex attracts the attention of law enforcement agencies. Such special and law enforcement services as the NSA, FBI, Europol, GCHQ, and others have repeatedly carried out successful dismantling of botnets and organized raids on cybercriminals who profited from malware.
Our function is also to notify users of a potential threat, which will significantly reduce the risk of infection and loss of funds. We advise users not to click on phishing links or open suspicious email attachments.
Source: https://habr.com/ru/post/271981/
All Articles