Security audit on the server. Search by security magazine. Power powershell
A security log audit helped my colleague monitor virtually any actions of employees who have at least some access to servers or ActiveDirectory.
In the topic there will be a lot of code, which I hope will be useful to you.
The first step was to determine the list of events that needed to be monitored. To reduce the amount of text, I created a procedure that, by the event ID, gives its description:
Then it was necessary to describe the events that are tracked by the access mask:
')
Now we know what we want to follow. The next step in developing an audit script is to get the security log in XML format, because if there are many events, then line-by-line processing takes quite a lot of time.
To get events from the log you can use one of the commands, each of which has its own advantages and disadvantages:
Benefits:
- quick access to the event properties;
- no preprocessing is required to access event properties.
Disadvantages:
- access only from the system security log, which is stored along the path: Windows / System32 / winevt / security.evtx;
- long processing of the contents of the tag. Processing takes place by line separation with the elimination of special characters.
Benefits:
- quick log processing;
- access to any magazine. The main thing is to write the full path.
Disadvantages:
- for processing the received log requires preliminary processing.
The next step after we got access to the log is to pull the required events from the log and make the appropriate decisions on them. In most cases, this is sending an informational message to the mail or logging to a separate file.
Set the parameters by which we will extrude information, possibly using an interface solution. Dialog box with input parameters.
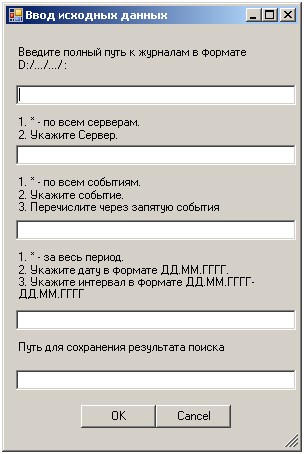
1. The first parameter assumes that the logs are periodically exported to a specific directory, which should be set. If there is one log, then the standard directory for storing logs is set: “C: \ Windows \ System32 \ winevt \ Logs”.
2. The second parameter defines the server by which logs will be searched. If the server is one, then put "*".
3. The third parameter is extremely clear: * - we are looking for events for the entire period, if a date is set, for example, 11/30/2015, then we are looking for that date. The search for the period is carried out by entering the starting and ending dates through a dash (01.11.2015-30.11.2015)
4. Specify the path to save the result of the work, for example, "D: \ log.log" Below is the code that allows you to build an interface for the script:
We get the entered data:
If there is a "-" symbol in the date field, then an interval is entered, if this character is entered incorrectly, your problems We carry out separation by the symbol "-", we determine the beginning and end date of the range.
If in the entered field there is neither "-" nor "*", then a specific date is entered.
1. Search all servers, all events for the entire period:
2. Search all servers, by event filter, for the entire period:
3. Search all servers, all events, for a range:
4. Search all servers, all events, for a specific date:
5. Search across all servers, by event filter, for a certain period:
6. Search across all servers, by event filter, for a specific date:
7. Search on a specific server, search all events for the entire period:
8. Search on a specific server, by event filter, for the entire period:
9. Search on a specific server for all events for the period:
10. Search on a specific server, by event filter, for the period:
11. Search for a specific server, for all events, for a specific date:
12. Search by specific server, by event filter, for a specific date:
At the end of the month (the period is set individually by administrators), the security log is archived on the storage server, with the server name and the date of archiving.
After we have described all the options for searching for events. We need to save the result to a file, the path to which was specified by the user in the last field. If the path is specified, the result is saved to a file. After running the script, the file is automatically launched. If the path to save the result is not specified, the log will be saved in the working directory under the name "log.log".
Thanks for attention.
While writing the script, the article “ PowerShell and Security Audit ” was very useful , thanks to the author.
In the topic there will be a lot of code, which I hope will be useful to you.
The first step was to determine the list of events that needed to be monitored. To reduce the amount of text, I created a procedure that, by the event ID, gives its description:
Function DefineReason ($Id){ switch ($Id){ 4741{ Return " "} 4742{ Return " " } 4743{ Return " "} 4727{ Return " "} 4728{ Return " "} 4729{ Return " "} 4730{ Return " "} 4731{ Return " "} 4732{ Return " "} 4733{ Return " "} 4734{ Return " "} 4735{ Return " "} 4737{ Return " "} 4743{ Return " "} 4754{ Return " " } 4755{ Return " "} 4756{ Return " "} 4757{ Return " "} 4758{ Return " "} 4764{ Return " "} 4720{ Return " "} 4722{ Return " "} 4724{ Return " "} 4725{ Return " "} 4726{ Return " "} 4738{ Return " "} 4740{ Return " "} 4767{ Return " "} 4780{ Return " , "} 4781{ Return " "} 4794{ Return " "} 5376{ Return " : "} 5377{ Return " : "} 4825{ Return "e , RDP"} 1102{ Return " Security"} } } Then it was necessary to describe the events that are tracked by the access mask:
')
# Function DefineReasonByAccessMask ($AccessMask){ switch($AccessMask){ "0xc0000064" { Return " " } "0xc000006A" { Return " , "} "0xc0000234" { Return " " } "0xc0000072" { Return " "} "0xc0000006F" { Return " "} "0xc00000070" { Return " "} "0xc00000193" { Return " "} "0xc00000071" { Return " "} "0xc00000224" { Return " "} "0xc000015b" { Return " "} "0xc000006d" { Return " "} } } Now we know what we want to follow. The next step in developing an audit script is to get the security log in XML format, because if there are many events, then line-by-line processing takes quite a lot of time.
To get events from the log you can use one of the commands, each of which has its own advantages and disadvantages:
1. Get-LogEvent security
Benefits:
- quick access to the event properties;
- no preprocessing is required to access event properties.
Disadvantages:
- access only from the system security log, which is stored along the path: Windows / System32 / winevt / security.evtx;
- long processing of the contents of the tag. Processing takes place by line separation with the elimination of special characters.
2. Get-WinEvent –path “D: /”
Benefits:
- quick log processing;
- access to any magazine. The main thing is to write the full path.
Disadvantages:
- for processing the received log requires preliminary processing.
Try { $Events = Get-WinEvent -FilterHashTable $MyFilter } Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events) { Try{ $EventXML = [xml]$Raw_Event.ToXML() } Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) The next step after we got access to the log is to pull the required events from the log and make the appropriate decisions on them. In most cases, this is sending an informational message to the mail or logging to a separate file.
Set the parameters by which we will extrude information, possibly using an interface solution. Dialog box with input parameters.

1. The first parameter assumes that the logs are periodically exported to a specific directory, which should be set. If there is one log, then the standard directory for storing logs is set: “C: \ Windows \ System32 \ winevt \ Logs”.
2. The second parameter defines the server by which logs will be searched. If the server is one, then put "*".
3. The third parameter is extremely clear: * - we are looking for events for the entire period, if a date is set, for example, 11/30/2015, then we are looking for that date. The search for the period is carried out by entering the starting and ending dates through a dash (01.11.2015-30.11.2015)
4. Specify the path to save the result of the work, for example, "D: \ log.log" Below is the code that allows you to build an interface for the script:
$objForm = New-Object System.Windows.Forms.Form $objForm.Text = " " $objForm.Size = New-Object System.Drawing.Size(300,450) $objForm.StartPosition = "CenterScreen" # Events path $objLabel1 = New-Object System.Windows.Forms.Label $objLabel1.Location = New-Object System.Drawing.Size(10,20) $objLabel1.Size = New-Object System.Drawing.Size(280,40) $objLabel1.Text = " `nD:/.../.../ :" $objForm.Controls.Add($objLabel1) $objTextBox1 = New-Object System.Windows.Forms.TextBox $objTextBox1.Location = New-Object System.Drawing.Size(10,60) $objTextBox1.Size = New-Object System.Drawing.Size(280,20) $objForm.Controls.Add($objTextBox1) #Find Server mode $objLabel2 = New-Object System.Windows.Forms.Label $objLabel2.Location = New-Object System.Drawing.Size(10,90) $objLabel2.Size = New-Object System.Drawing.Size(280,30) $objLabel2.Text = "1. * - .`n2. ." $objForm.Controls.Add($objLabel2) $objTextBox2 = New-Object System.Windows.Forms.TextBox $objTextBox2.Location = New-Object System.Drawing.Size(10,120) $objTextBox2.Size = New-Object System.Drawing.Size(280,30) $objForm.Controls.Add($objTextBox2) #Type Events Mode $objLabel3 = New-Object System.Windows.Forms.Label $objLabel3.Location = New-Object System.Drawing.Size(10,150) $objLabel3.Size = New-Object System.Drawing.Size(280,45) $objLabel3.Text = "1. * - .`n2. .`n3. " $objForm.Controls.Add($objLabel3) $objTextBox3 = New-Object System.Windows.Forms.TextBox $objTextBox3.Location = New-Object System.Drawing.Size(10,195) $objTextBox3.Size = New-Object System.Drawing.Size(280,30) $objForm.Controls.Add($objTextBox3) #Date Events mode $objLabel4 = New-Object System.Windows.Forms.Label $objLabel4.Location = New-Object System.Drawing.Size(10,225) $objLabel4.Size = New-Object System.Drawing.Size(280,60) $objLabel4.Text = "1. * - .`n2. ...`n3. ..-.." $objForm.Controls.Add($objLabel4) $objTextBox4 = New-Object System.Windows.Forms.TextBox $objTextBox4.Location = New-Object System.Drawing.Size(10,285) $objTextBox4.Size = New-Object System.Drawing.Size(280,30) $objForm.Controls.Add($objTextBox4) #Save Result $objLabel5 = New-Object System.Windows.Forms.Label $objLabel5.Location = New-Object System.Drawing.Size(10,315) $objLabel5.Size = New-Object System.Drawing.Size(280,30) $objLabel5.Text = " " $objForm.Controls.Add($objLabel5) $objTextBox5 = New-Object System.Windows.Forms.TextBox $objTextBox5.Location = New-Object System.Drawing.Size(10,345) $objTextBox5.Size = New-Object System.Drawing.Size(280,30) $objForm.Controls.Add($objTextBox5) # . . $OKButton = New-Object System.Windows.Forms.Button $OKButton.Location = New-Object System.Drawing.Size(75,380) $OKButton.Size = New-Object System.Drawing.Size(75,23) $OKButton.Text = "OK" $OKButton.Add_Click({$objForm.Close()}) $objForm.Controls.Add($OKButton) $OKButton.DialogResult=[System.Windows.Forms.DialogResult]::OK $CancelButton = New-Object System.Windows.Forms.Button $CancelButton.Location = New-Object System.Drawing.Size(150,380) $CancelButton.Size = New-Object System.Drawing.Size(75,23) $CancelButton.Text = "Cancel" $CancelButton.Add_Click({$objForm.Close()}) $objForm.Controls.Add($CancelButton) $objForm.Topmost = $True $objForm.Add_Shown({$objForm.Activate()}) $dialogResult = $objForm.ShowDialog() # We get the entered data:
# if ($dialogResult -eq "OK"){ $Log_Path = $objTextBox1.Text $FindServerMode = $objTextBox2.Text $TypeEventsMode = $objTextBox3.Text $DateEventsmode = $objTextBox4.Text $SaveResult = $objTextBox5.Text } If there is a "-" symbol in the date field, then an interval is entered, if this character is entered incorrectly, your problems We carry out separation by the symbol "-", we determine the beginning and end date of the range.
if ($DateEventsmode -match "-"){ $x = $DateEventsmode.split("-") $StartDate = $x[0] $EndDate = $x[1] $StartDate = [DateTime]::parse($StartDate) $StartDate $EndDate = [DateTime]::parse($EndDate) $EndDate } If in the entered field there is neither "-" nor "*", then a specific date is entered.
if ($DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*"){ $StartDate1 = [DateTime]::parse($DateEventsmode) } 1. Search all servers, all events for the entire period:
if ($FindServerMode -eq "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 1" $ALL_LOGS = Get-ChildItem -Path $Log_Path -recurse| Where {$_.Extension -eq ".evtx"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName} $i=0 Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" $i++ } } } 2. Search all servers, by event filter, for the entire period:
if ($FindServerMode -eq "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 2" $ALL_LOGS = Get-ChildItem -Path $Log_Path | Where {$_.Extension -eq ".evtx"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } 3. Search all servers, all events, for a range:
if ($FindServerMode -eq "*" -and $DateEventsmode -match "-" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 3" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $Event.TimeCreated if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 4. Search all servers, all events, for a specific date:
if ($FindServerMode -eq "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 5" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 5. Search across all servers, by event filter, for a certain period:
if ($FindServerMode -eq "*" -and $DateEventsmode -match "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 4" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne ""} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 6. Search across all servers, by event filter, for a specific date:
if ($FindServerMode -eq "*" -and $TypeEventsMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $Log_Path -ne "") { Write-host " 6" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 7. Search on a specific server, search all events for the entire period:
if ($FindServerMode -ne "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 7" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } 8. Search on a specific server, by event filter, for the entire period:
if ($FindServerMode -ne "*" -and $DateEventsmode -eq "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 8" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $LogFile+= "EventID: " + $Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } 9. Search on a specific server for all events for the period:
if ($FindServerMode -ne "*"-and $DateEventsmode -match "-" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 9" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode -and $StartDate -ne "null" -and $EndDate -ne "null"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 10. Search on a specific server, by event filter, for the period:
if ($FindServerMode -ne "*" -and $DateEventsmode -match "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -ne "*" -and $Log_Path -ne ""){ Write-host " 10" $ALL_LOGS = Get-ChildItem -Path $Log_Path | Where {$_.Extension -eq ".evtx" -and $_.FullName -match $FindServerMode -and $StartDate -ne "null" -and $EndDate -ne "null"} | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated -gt $StartDate -and $Event.TimeCreated -lt $EndDate){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 11. Search for a specific server, for all events, for a specific date:
if ($FindServerMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $TypeEventsMode -eq "*" -and $Log_Path -ne ""){ Write-host " 11" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.EventData.Data) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } 12. Search by specific server, by event filter, for a specific date:
if ($FindServerMode -ne "*" -and $TypeEventsMode -ne "*" -and $DateEventsmode -notmatch "-" -and $DateEventsmode -ne "*" -and $Log_Path -ne ""){ Write-host " 12" $ALL_LOGS = Get-ChildItem -Path $Log_Path -Recurse| Where {$_.Extension -eq ".evtx" -and $StartDate1 -ne "null" } | Sort LastWriteTime $ALL_LOGS foreach ($Log in $ALL_LOGS){ $LogFile = "Audit EventLog Security" +"`n" ($Log).FullName $Log.LastWriteTime $StartDate $EndDate $MyFilter = @{Path=($Log).FullName;ID=$TypeEventsMode} Try {$Events = Get-WinEvent -FilterHashTable $MyFilter} Catch {"No events were found in $Log"; Continue} ForEach ($Raw_Event in $Events){ Try{$EventXML = [xml]$Raw_Event.ToXML()} Catch {Write-Host "Unable to convert an event to XML"} $Event = @{} ForEach ($object in $EventXML.Event.Message) { $Event.Add($object.name,$object.'#text') } $Event.Add("ID",$Raw_Event.ID) $Event.Add("TimeCreated",$Raw_Event.TimeCreated) $Event if ($Event.TimeCreated.Day -eq $StartDate1.Day -and $Event.TimeCreated.Month -eq $StartDate1.Month -and $Event.TimeCreated.Year -eq $StartDate1.Year){ $LogFile+= "EventID: " + $Raw_Event.ID +"`n" $LogFile+= "Target User Name: " + $Event.TargetUserName +"`n" $LogFile+= "Target Domain Name: " + $Event.TargetDomainName +"`n" $LogFile+= "Status: " + $Event.Status +"`n" $LogFile+= "TimeGenerated: " + $Event.TimeCreated +"`n" $LogFile+= "Workstation Name: " + $Event.WorkstationName +"`n" $LogFile+= "IpAddress: " + $Event.IpAddress +"`n" $LogFile+= "Computer: " + [xml]$Raw_Event.ToXML().Event.System.Computer +"`n" $Reason = DefineReason -Id $Raw_Event.ID $AccessM = DefineReasonByAccessMask -AccessMask $Event.Status $LogFile+= "Reason(RU): " + $Reason + " "+ $AccessM +"`n" $LogFile+= "Reason(SYS): " + $Event.Message +"`n" $LogFile+= "----------------------------------------------------------------`n" } } } } At the end of the month (the period is set individually by administrators), the security log is archived on the storage server, with the server name and the date of archiving.
After we have described all the options for searching for events. We need to save the result to a file, the path to which was specified by the user in the last field. If the path is specified, the result is saved to a file. After running the script, the file is automatically launched. If the path to save the result is not specified, the log will be saved in the working directory under the name "log.log".
if ($SaveResult -ne ""){ $LogFile | Out-File $SaveResult -Encoding utf8 Invoke-Item $SaveResult $Event2= @{} $Event = @{} $Log_Path="" } else{ $LogFile | Out-File ".\log.log" -Encoding utf8 Write-Host $LogFile $Event2= @{} $Event = @{} $Log_Path="" } Thanks for attention.
While writing the script, the article “ PowerShell and Security Audit ” was very useful , thanks to the author.
Source: https://habr.com/ru/post/271963/
All Articles