Idiots in my internets.
“Zwei Dinge sind unendlich: Das Universum und die menschliche Dummheit. Aber beim Universum bin ich mir nicht ganz sicher. ”* - Albert Einstein
It was evening, and there was a lot of things to do, as usual, but laziness.
A random link came to one site, the address of which I do not cite from obvious ethical considerations. Flash crafts; Its essence is as follows: we stick in the free space, and we are offered to upload our picture to this very place and assign a nickname to it. My fantasy was not enough to imagine how much joy a simple
I wanted to see how it was done, if done at all, protection against automatic input of information; maybe write a trivial bot and take a couple of dozen places with your own pictures.
I uploaded a picture, wrote a nickname ...
However, what I saw in Fiddler turned out to be much more entertaining than any bot.

So what do we see? An ordinary HTTP Post-request, some binary garbage in the content and - believe your eyes? - what is it? - SQL query ?!
')
Yes, citizens, we have seen a lot. We saw buffer overflows on C. We saw SQL injections in bad PHP code. This all will not surprise us. But Albert Germanovich was damn right, and we could not keep up with the thought of certain individuals: average and ordinary people: would it have occurred to you to form a SQL query on the client and transfer it to the server for execution? It is poor, our imagination is poor.
About the fact that there is no sanitization of input, I will not even mention, I think, this is already obvious. So, having entered a text with a quotation mark into the input field, we get another reason for quiet fun: the server is straightforward and open, as befits a decent program, gives MySQL error.
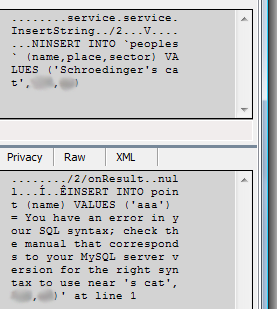
Yes, indeed, the syntax was not all right.
For the sake of fairness, it must be said that simply replacing SQL in the body of a Post-request will not work - the checksum does not converge somewhere in the binary part. Not much useful will come out of the injection through the text entry field: there is a limit on the length of the input text, and several commands, separated by a semicolon, the server part is wisely refused to accept.
This elementary precautionary measure, of course, does not affect the main problem in any way - the execution of the SQL query formed on the client side. With a certain desire to replace the request itself is quite possible, which was done by easy modification of the flash part. I will keep silence about the details for ethical reasons. And if we also knew Flash ...
As a proof of concept, we change the nickname we have just registered user by executing a SQL query
update `peoples` set name = ' new nickname ' where name = ' old nickname '
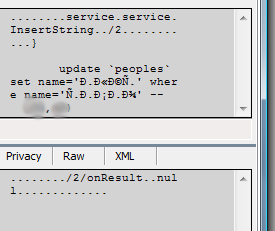
I think it is not necessary to say that someone else's intentions may not be so peaceful at all.
Of course, the site administration has been notified of the vulnerability. At least, I did everything possible, since there are no addresses of either the webmaster or the administrator on the site.
Moral: use the brain, people. You are welcome.
PS In the process of writing this article, many people almost did not suffer, because Habr did not want to upload images while editing the saved version, stubbornly fell out of Javascript error “uncaught exception: Permission denied to get property HTMLDocument.getElementById”
This error occurs when trying to call sts_put_opener () from a child frame. This is due to the fact that the parent iframe is on the subdomain (paul7.habrahabr.ru), and the child one is on the main one, so the POST request was successful, but I did not get any results. I had to link the links using the same true Fiddler. Ugliness, frankly.
PPS Dear CTO! If you read this topic, please do not translate me into testers! It is temporarily lucky for me ... I hope.
* “There are only two endless things: the universe and human stupidity. True, I am not sure about the universe. ”
Source: https://habr.com/ru/post/27196/
All Articles