Security Week 48: melancholy with Dell certificates, backdoor in modems, Truecrypt returns
 Every time another failure occurs in the security sphere, two eternal questions materialize from the air: what to do and who is to blame. And the first is more important: more and more often we are dealing with incidents that are just so simple, a patch or something similar cannot be solved. Unfortunately, this applies not only to super-complex attacks. Fortunately, we are usually talking about theoretical threats. Look at the main news of this week:
Every time another failure occurs in the security sphere, two eternal questions materialize from the air: what to do and who is to blame. And the first is more important: more and more often we are dealing with incidents that are just so simple, a patch or something similar cannot be solved. Unfortunately, this applies not only to super-complex attacks. Fortunately, we are usually talking about theoretical threats. Look at the main news of this week:- In Dell laptops found self-signed root certificates;
- In 600 thousand modems of the American company Arris found a backdoor;
- The German state agency took up the audit of TrueCrypt, but it didn’t find anything, but no one trusts the encryption tool abandoned by the developers anyway.
Nothing new. The first two stories - in general, from my beloved category, "never happened and here again." Dozens of software and hardware manufacturers are attacking a special IT Security rake, and it seems that there will never be an end or an edge to this. But there is a solution, and in today's digest I will try to explain in general terms which one. All episodes of the series - here .
Dell's laptops found a self-signed root certificate and private key. And then found another two more.
News Another news . 2000+ comments on Reddit .
')
In February of this year, Lenovo's laptops discovered a pre-installed Superfish program, which showed users some very targeted advertising. Unpleasantly, not surprisingly, but there was one caveat: in order to more effectively show targeted ads even on sites with a secure connection, the HTTPS traffic “broke” traffic with its own root certificate. At first Lenovo didn’t recognize the problem (“this is not a problem”), then they recognized it, apologized and deleted the program.
All is well? Not. Two months later, Dell laptops appear on the market, in which the new manufacturer steps on the same rake: the root certificate of eDellRoot, no longer from third-party software, but from the manufacturer itself, potentially allows for MiTM attacks, monitoring the user, stealing passwords and the like . How did you find? The user who decided for some reason to see the list of installed root certificates (you will agree, quite an atypical occupation) found eDellRoot and wrote about it on Reddit.

It is time for cool epics.
How did you react? And just like Lenovo in February. The first comment from Dell was that there was no problem, this thing is installed for the “more efficient” work of technical support in the event of a client contact, and in general everything is strange. But something went wrong, Microsoft decided to “nail” the certificate using Windows Defender, and Dell apologized and intends to delete the certificate from existing laptops with an update, and no longer install new ones.

There would be fewer potential problems with eDellRoot if the affected machines would not have a private key either. As it turned out, in some models of Dell, you can find two more of the same pair, although they are less common, and the validity of one of the newly discovered certificates has already expired. That is, it turns out that such an extremely unsafe practice is generally accepted, common and (until now) was not qualified by vendors as something bad.
Let me remind you of another story on a topic that our experts excavated at the beginning of last year. Absolute Computrace software not only had a “restore” function after a complete system reinstallation, it also used extremely insecure methods of interaction with the server infrastructure, and perhaps was activated from those laptop owners who never asked the developer of the “anti-theft” system to do so. So, this is a good example of how difficult it is to investigate such potential security threats. Here in 2009 some aspects of the work of Computrace are explored by one company. Here the experts of “Laboratories” decide to develop the topic and find even more problems. To do this: (1) analyze the interaction of the BIOS and the installed software (2) analyze the program code and interaction with the server (3) select several diverse laptops, compare software versions and modules, evaluate the configuration on each. It is desirable that the laptops were new - it was necessary to understand whether the module is activated by default. (4) Prepare a proof of concept showing how you can take control of a laptop remotely.
The conclusion is clear: it all takes several months, if not years. Developer reaction? “Everything is fine with us, there are no problems,” and so on. Examples of Dell and Lenovo show that the first reaction is always the same.
The main mistake that can be made on the background of such events is to begin to divide the software and hardware companies into “good” (in terms of security) and “bad”. This is a great way to replace technology talk with politics, and in the end nothing can be solved. But in general, it is necessary to change the security situation for the better, to everyone
Seriously, the problems of cyber security are so numerous that the security industry in its current form is simply not able to identify and help solve them all. Sooner or later, a responsible attitude to security will become for vendors the same competitive advantage as it is now - concern for the environment or charity. Here is a bright future, to which we all, apparently, sometime come. And when we come - 2015 will surely seem to us to be a dark medieval, and 2001 - and in general Paleolithic.
Wait and see.
In the American Arris modems found a backdoor inside the backdoor
News Blog post researcher.
"Something happened again in the modems." The above-mentioned limitation of resources of the security industry makes the work of researchers similar to a military field hospital: both there and there it is necessary to work quickly, a lot and, most importantly, prioritize . And while everyone is busy restraining the hordes of cybercriminals who attack, as a rule, the obvious, massive and easiest-to-operate holes, there are few forces left to “defend the rear”. And in vain. Researcher Bernardo Rodriguez discovered a cunning vulnerability in Arris cable modems - these are regular hardware pieces that are installed by Internet service providers in tens of thousands when connecting services. In addition to standard vulnerabilities such as XSS and CRSF, he found an undocumented library that allows remote access via telnet or SSH. And then the potential hacker is provided with a whole packet of default passwords, with inevitable full access to the settings.
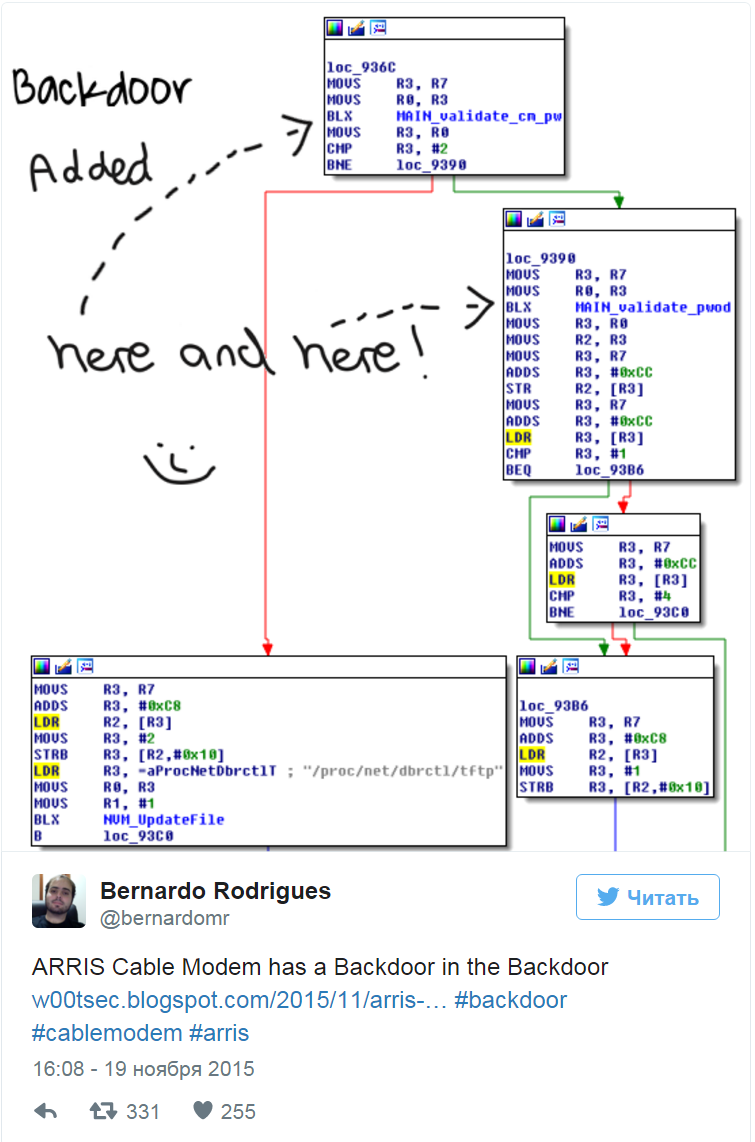
Picture from Rodriguez tweet .
In a post the researcher mentions a reluctance to interact with experts, traditional for modem manufacturers, and an excessively long time to prepare a patch. At the moment there is no patch, but at least the work is on. By the way, if the bright future drawn by me above does happen, many will have to try on the role of such unprepared for the rapid closure of companies' vulnerabilities.
In Germany, once again investigated TrueCrypt and serious holes did not find
News BSI research report .
The German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik or simply BSI) ordered the Fraunhofer Institute to audit the TrueCrypt utility for full or partial encryption of information. The question immediately arises as to why BSI needs this, if TrueCrypt is no longer being developed, and in general was abandoned by developers under very strange and suspicious circumstances. Do government agencies in Germany use for encryption a program developed by someone who is unclear and incomprehensible how? The fact is that certain “elements” of TrueCrypt are used in the Trusted Disk software of Sirrix AG, and this is an officially approved tool for encrypting important data.
In general, there is a reason to look. TrueCrypt is a strange story altogether. The unexpected demarche of the developers, which had previously remained anonymous, caused a reasonable suspicion that there could be a tab somewhere in the encryption system. Checks were carried out repeatedly, in April, a group of comrades OpenCryptoAudit finished its work, and, in short, did not find anything. Recently , two dangerous vulnerabilities were found in the TrueCrypt code, but they also did not affect the encryption process itself. Now, at the request of BSI, the Fraunhofer Institute conducted another study and, in general, did not find anything either.

tl; dr of the Fraunhofer report and BSI
More specifically, the report states that when the system is openly accessible to encrypted data (for example, the system disk is decrypted and the OS is loaded and running), these same data are subject to the usual threats - keyloggers, trojans, and so on. In general, this is such a captain's comment, but the "disabled" encrypted volume is completely safe. Interestingly, we already have three quite authoritative audits of TrueCrypt. Direct studies from the OpenCrypto team and from BSI confirm the absence of bookmarks and holes in the encryption algorithm. Google Project Zero, who discovered those “unrelated” vulnerabilities, gives a third, albeit indirect, confirmation: for some reason I am sure that they were not looking for these vulnerabilities . But there was no confidence in TrueCrypt either: there is hardly anything after the events of May of last year to be able to restore it.
What else happened:
The latest, fourth version of the Cryptowall cryptographer is now distributed using Nuclear's exploit pack. This is the version that encrypts the file names too, I wrote about it earlier .
Found another malware for POS-terminals. It is more complicated and potentially more dangerous than its predecessors. Perhaps more importantly, the attack terminals began to attack much more often .
 Antiquities:
Antiquities:"Plastique-3004, -3012"
Erase the contents of the disks when you run ACAD.EXE. Losing melodies. Slow down the computer (idle cycle on int 8). With every 4000th keystroke, erase 1 sector with a random number on the disk. They contain encrypted texts: “ACAD.EXECOMMAND.COM.COM.EXE”, “Program: Plastique 4.51 (plastic bomb), Copyright 1988, 1989 by ABT Group. Thanks to Mr. Lin (IECS 762 ??), Mr. Cheng (FCU Int-Center) ”. Intercepted int 8, 9, 13h, 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 35.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/271847/
All Articles