Car safety: what lessons can we learn from recalling cars?
I decided to write an article about car safety after the news that the Chrysler car series was withdrawn due to a software vulnerability. For various reasons, she has been gathering dust in a half-witted state since summer, and now I finally found time between trips to add and publish it. No, they have not guessed, this will not be an article about vulnerabilities in microcontrollers, so much has already been written about this that will be enough for a whole book. I want to look at the problem from the other side.
Of course, you heard about two hackers who took control of a jeep, because everyone wrote about it. I wanted to dig deeper and assume that it was not this one, but other similar problems may not be accidental, but a planned result of the attack. That is, theoretically, an attacker may intentionally introduce vulnerability into products. Although so far this is more reminiscent of the scenario of the new Mr. Robot series, but the scandal associated with another large auto concern, Volkswagen, shows that such an attack could well be turned in reality (ok, if not now, then in the near future).
')
When I started collecting information on this topic, I expected to see a couple of examples, but I discovered dozens of similar cases in the last couple of months only! Here are just the main reviews that happened this summer:
Car reviews form a significant part of all product reviews in general. One of the first such cases occurred back in 1969, when rubber parts of an eight-cylinder engine support from General Motors could fall out and cause the engine to become loose, could roll over and open the throttle, as a result of which the car accelerated quickly. In addition, all this was often accompanied by the refusal of the “dotormazhivatel”, which made it difficult to stop the car. By 1971, 172 cases of malfunctions in the engine support were reported, which led to very serious consequences (63 accidents, 18 wounds).
As you can see, even from this small excursion into history (I recommend also to see the 12 largest automotive reviews ), the most common reasons for reviews are problems with airbags, seat belt faults and various defects in connecting mechanisms, for example, bolts.
After independent activists found out that Volkswagen was inserting a special code into cars that reduced emissions during testing, in just 2 days (September 21-22) the company's market capitalization fell by 25 billion euros (from 77 billion euros to less than 52 billion). Euro). Although there have been examples of much more life-threatening defects in automotive history, this incident has significant economic consequences: in addition to a significant reduction in the company's capitalization, the car concern must pay fines and assume the costs of replacing parts, and no one knows what this scandal will result in the future.
Volkswagen admitted that they installed software that allows them to deceive the inspectors: when special algorithms found that the car was being tested, they lowered emissions. Nice job! Over the past 6 years, models such as the VW Jetta, Golf, Beatle, Passat and Audi A3 have been subjected to software modifications. Thus, the company tried to win a share of the US auto market. Known and the supplier who supplied Volkswagen software and devices for falsifying tests, it turned out to be the world famous company Bosch.
It is clear that the bugs in the software and errors in the production process are the main reasons for product feedback. However, if this can happen by chance and go unnoticed, then it can be assumed that someone, be it a competitor or a group of anonymous hackers acting on ideological grounds, can intentionally create such errors as a result of the attack.
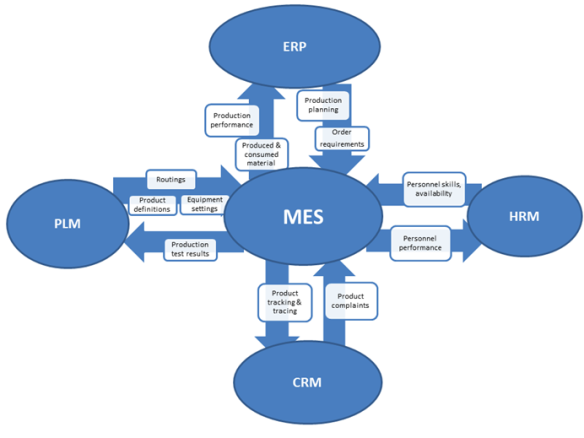
Traditionally, the processes of production, design and design are managed in various corporate business applications. To successfully attack a company, an attacker needs to access these applications and make some minor changes to the CAD during construction, to PLM during configuration of product lifecycle management, or directly during production at MES. The level of integration between MES and PLM, as well as the automation of these systems, allows attackers to easily make changes to these modules. For example, Siemens (one of the largest suppliers of solutions for the automotive industry) says that “the integration of PLM and MES allows you to continuously respond to changing requirements, introducing the latest development and assembly methods through a more connected, more efficient production chain, ensuring full transparency between production and design. "
In addition, production and design are not only connected with each other, but also with corporate networks, which in turn are vulnerable to traditional viruses and attacks. Think these systems are not connected? Read our latest study on the attacks on the oil companies Oil and Gas Cyber Security , which I will discuss in more detail later.
The history of Stuxnet showed that attacks on technological systems are quite real and have already been implemented. Technically, there is not much difference for hackers between attacking ICS / SCADA, or accessing MES, PLM, or CAD systems. In addition, the security of the latter is to some extent even weaker than that of industrial systems. Companies began to introduce SDL and monitor the safety of industrial devices, because the amount of hype on industrial safety exceeds all imaginable limits, and something needs to be done, but now almost no one thinks about the security of MES or PLM systems. And do not forget that these systems are usually associated with other applications (for example, ERP), which are literally teeming with vulnerabilities . In general, accessing MES or PLM is not special.
Let us turn to the possible attack vectors. What happens if someone changes the pressure in the wheel bolts? Of course, in modern cars there are numerous checks that would reveal a similar problem, but the situation when a wheel falls off a car at high speed is not a pleasant one. Wait a minute though? If so many problems in the airbags were not noticed, then a weakly twisted bolt has a right to live. To be honest, this was the first idea that came to my mind, but I discovered that in 1981, due to a problem with a suspension bolt, almost 6 million buicks were withdrawn. 6 million, Kaarl! Imagine how 6 million kosher rappers instantly lost their means of transportation.
If any part of the rear suspension falls off at speed, the likelihood of a dramatic development of events is very high. Knowing this, GM agreed to replace defective parts on a number of models in the early 1980s, when there were reports that the bolts could break or loosen their fasteners. The malfunction of the suspension bolt is somewhat similar to the one proposed by me. A real attacker can create a more devastating and less visible defect, such as an error in ...? Right! In the airbag, which would prevent its disclosure. There are so many problems with these pillows that no one will notice the next one. Of course, not all the pillows, because then it would be easy to detect more on the crash test (although, I look, they are not such crash tests, judging by the number of reviews). As a result, an expensive product recall is probably the most favorable scenario.
If such incidents still seem not too realistic, I remind you that many attacks seemed fantastic. Just a year ago, a remote attack on a car seemed something incredible, and 3 years ago, no one could even imagine a local attack on a car. 6 years ago, almost no one knew what SCADA is, and 8 years ago, SAP security simply did not exist as a class. This can go on indefinitely, so that only a matter of time when such an attack can occur, and perhaps one of the already happened reviews of cars is the result of a competitor's attack. Considering that the scandal with Volkswagen threatens the entire German automotive industry and even the European economy, sabotage attacks can be not just a tool in the competitive struggle, but also cyber weapons, which can be used by those whom I don’t want to point the finger)
It is very likely that the consequences of the scandal caused by the fact that Volkswagen forged test results will go beyond the automotive industry and affect other areas. Similar cases are already known. For example, more recently, independent tests have shown that Samsung TVs use less energy during official tests than during actual use.
The difference between actual performance and test results was discovered by the ComplianTV research group, funded by the European Union. Although the full results have not yet been published, according to the Guardian, the energy consumption indicators are in fact "significantly higher" than the results obtained during the tests.
Thus, it is not a secret that vendors can use (and already use) similar methods to hide dangerous defects of their products. But can you, as a manufacturer who plays an honest game, be sure that no one has implemented such malicious code in your software by attacking critical systems?
Of course, you heard about two hackers who took control of a jeep, because everyone wrote about it. I wanted to dig deeper and assume that it was not this one, but other similar problems may not be accidental, but a planned result of the attack. That is, theoretically, an attacker may intentionally introduce vulnerability into products. Although so far this is more reminiscent of the scenario of the new Mr. Robot series, but the scandal associated with another large auto concern, Volkswagen, shows that such an attack could well be turned in reality (ok, if not now, then in the near future).

A little history of car reviews
')
When I started collecting information on this topic, I expected to see a couple of examples, but I discovered dozens of similar cases in the last couple of months only! Here are just the main reviews that happened this summer:
- July 8 - A Japanese parts supplier, Takata, reported that they were recalling 33.8 million vehicles in the United States due to the fact that the airbags could explode, with the result that metal parts could fly into the driver and passengers. Defective airbags led to 7 deaths and more than 100 injuries. Normal such pillows "without" danger.
- July 8 - Ford recalled about 400,000 vehicles in North America to fix software problems.
- July 9 - Honda recalled 4.5 million cars due to the fact that the airbags could explode. Again pillows. Does it seem to me, or do airbags carry more harm than good?
- July 13 - General Motors recalled 155 thousand cars in India. Sorry Rajkumar, you will have to ride a motorbike.
- July 14 - GM recalled 50 thousand cars due to a problem with a seat-belt cable. Are you out of your mind? First cushions, now belts. You still equip the locks with an explosive device, so that if something goes wrong, it will immediately tear everything into pieces.
- July 15 - Nissan recalled 270,000 cars worldwide, because due to a malfunction in the ignition button, the engine could suddenly stall. ABOUT! Almost guessed. Ignition button. Well, well, that at least stall.
- July 15 - Subaru recalled 32,400 cars to fix the problem with airbags. Seriously? Again pillows? Yes, you're kidding.
- July 15 - Toyota recalled 625,000 hybrid cars worldwide due to a crash that could shut off the entire system while driving. So much for the benefits of hybrid cars, just like in the HLS clip of the Leningrad group)
- July 17 - Ferrari recalled 814 sports cars due to a defect in the airbags ... soooo ... As I was taught, 10 deep breaths? Okay ... Airbags in a sports car? Does it make any sense?)
- July 24 - Harley Davidson recalled 185,000 motorcycles due to the fact that the saddle trunk of a motorcycle could fall off, thereby leading to an accident. Naturally! On a normal bike racks do not put.
Car reviews form a significant part of all product reviews in general. One of the first such cases occurred back in 1969, when rubber parts of an eight-cylinder engine support from General Motors could fall out and cause the engine to become loose, could roll over and open the throttle, as a result of which the car accelerated quickly. In addition, all this was often accompanied by the refusal of the “dotormazhivatel”, which made it difficult to stop the car. By 1971, 172 cases of malfunctions in the engine support were reported, which led to very serious consequences (63 accidents, 18 wounds).
As you can see, even from this small excursion into history (I recommend also to see the 12 largest automotive reviews ), the most common reasons for reviews are problems with airbags, seat belt faults and various defects in connecting mechanisms, for example, bolts.
Scandal with Volkswagen
After independent activists found out that Volkswagen was inserting a special code into cars that reduced emissions during testing, in just 2 days (September 21-22) the company's market capitalization fell by 25 billion euros (from 77 billion euros to less than 52 billion). Euro). Although there have been examples of much more life-threatening defects in automotive history, this incident has significant economic consequences: in addition to a significant reduction in the company's capitalization, the car concern must pay fines and assume the costs of replacing parts, and no one knows what this scandal will result in the future.
Volkswagen admitted that they installed software that allows them to deceive the inspectors: when special algorithms found that the car was being tested, they lowered emissions. Nice job! Over the past 6 years, models such as the VW Jetta, Golf, Beatle, Passat and Audi A3 have been subjected to software modifications. Thus, the company tried to win a share of the US auto market. Known and the supplier who supplied Volkswagen software and devices for falsifying tests, it turned out to be the world famous company Bosch.
What we can learn from product reviews
It is clear that the bugs in the software and errors in the production process are the main reasons for product feedback. However, if this can happen by chance and go unnoticed, then it can be assumed that someone, be it a competitor or a group of anonymous hackers acting on ideological grounds, can intentionally create such errors as a result of the attack.
Traditionally, the processes of production, design and design are managed in various corporate business applications. To successfully attack a company, an attacker needs to access these applications and make some minor changes to the CAD during construction, to PLM during configuration of product lifecycle management, or directly during production at MES. The level of integration between MES and PLM, as well as the automation of these systems, allows attackers to easily make changes to these modules. For example, Siemens (one of the largest suppliers of solutions for the automotive industry) says that “the integration of PLM and MES allows you to continuously respond to changing requirements, introducing the latest development and assembly methods through a more connected, more efficient production chain, ensuring full transparency between production and design. "
In addition, production and design are not only connected with each other, but also with corporate networks, which in turn are vulnerable to traditional viruses and attacks. Think these systems are not connected? Read our latest study on the attacks on the oil companies Oil and Gas Cyber Security , which I will discuss in more detail later.
The history of Stuxnet showed that attacks on technological systems are quite real and have already been implemented. Technically, there is not much difference for hackers between attacking ICS / SCADA, or accessing MES, PLM, or CAD systems. In addition, the security of the latter is to some extent even weaker than that of industrial systems. Companies began to introduce SDL and monitor the safety of industrial devices, because the amount of hype on industrial safety exceeds all imaginable limits, and something needs to be done, but now almost no one thinks about the security of MES or PLM systems. And do not forget that these systems are usually associated with other applications (for example, ERP), which are literally teeming with vulnerabilities . In general, accessing MES or PLM is not special.
Let us turn to the possible attack vectors. What happens if someone changes the pressure in the wheel bolts? Of course, in modern cars there are numerous checks that would reveal a similar problem, but the situation when a wheel falls off a car at high speed is not a pleasant one. Wait a minute though? If so many problems in the airbags were not noticed, then a weakly twisted bolt has a right to live. To be honest, this was the first idea that came to my mind, but I discovered that in 1981, due to a problem with a suspension bolt, almost 6 million buicks were withdrawn. 6 million, Kaarl! Imagine how 6 million kosher rappers instantly lost their means of transportation.
If any part of the rear suspension falls off at speed, the likelihood of a dramatic development of events is very high. Knowing this, GM agreed to replace defective parts on a number of models in the early 1980s, when there were reports that the bolts could break or loosen their fasteners. The malfunction of the suspension bolt is somewhat similar to the one proposed by me. A real attacker can create a more devastating and less visible defect, such as an error in ...? Right! In the airbag, which would prevent its disclosure. There are so many problems with these pillows that no one will notice the next one. Of course, not all the pillows, because then it would be easy to detect more on the crash test (although, I look, they are not such crash tests, judging by the number of reviews). As a result, an expensive product recall is probably the most favorable scenario.
If such incidents still seem not too realistic, I remind you that many attacks seemed fantastic. Just a year ago, a remote attack on a car seemed something incredible, and 3 years ago, no one could even imagine a local attack on a car. 6 years ago, almost no one knew what SCADA is, and 8 years ago, SAP security simply did not exist as a class. This can go on indefinitely, so that only a matter of time when such an attack can occur, and perhaps one of the already happened reviews of cars is the result of a competitor's attack. Considering that the scandal with Volkswagen threatens the entire German automotive industry and even the European economy, sabotage attacks can be not just a tool in the competitive struggle, but also cyber weapons, which can be used by those whom I don’t want to point the finger)
Not only automakers at risk
It is very likely that the consequences of the scandal caused by the fact that Volkswagen forged test results will go beyond the automotive industry and affect other areas. Similar cases are already known. For example, more recently, independent tests have shown that Samsung TVs use less energy during official tests than during actual use.
The difference between actual performance and test results was discovered by the ComplianTV research group, funded by the European Union. Although the full results have not yet been published, according to the Guardian, the energy consumption indicators are in fact "significantly higher" than the results obtained during the tests.
Thus, it is not a secret that vendors can use (and already use) similar methods to hide dangerous defects of their products. But can you, as a manufacturer who plays an honest game, be sure that no one has implemented such malicious code in your software by attacking critical systems?
Source: https://habr.com/ru/post/271785/
All Articles