Biometrics: Time Attendance + Fujitsu PalmSecure

Accounting systems for working hours have long ago taken their place in the infrastructure of many enterprises, where management wants to receive timely and objective information about the observance of labor discipline by employees. Fixing the time of arrival and departure is a useful tool for preventing abuse of trust and valuable information for the personnel department. Today we will talk about the time tracking system that uses Fujitsu PalmSecure technology in its work.
Classic time tracking systems imply that the employee has a unique identifier, the presentation of which to the system is confirmation of his passage through the control point. The identifiers can be barcode on the badge, magnetic cards, RFID-cards, tokens. The use of such individual identifiers leads to standard troubles: forgotten at home, lost, handed to a colleague to be noted.
Naturally, such problems suggested using biometric information about an employee as identifiers. The most simple and obvious way out was the use of fingerprints. The number of fingerprint systems is growing rapidly, but there are still obstacles in the way of development: a large number of failures due to a damaged print pattern (cuts, chemical injuries, etc.), a technology that is not sufficiently protected from counterfeit. Enterprises with a large number of employees often encounter situations with a significant number of incorrect fingerprint readings.
')
Later, recognition systems began to be introduced on the retina or iris of the eye (expensive, complex systems), on face geometry (expensive and not the most reliable solution), hand geometry (low reliability).
Currently, fingerprint systems occupy about half of the biometric identification market. However, their is not the highest reliability forced to look for new options for the use of biometric information in the systems of access and accounting of working time.
Fujitsu has used the well-known vein scanning technology commonly used in medical facilities in its developments. The technology was called PalmSecure, because it is based on the method of scanning the veins of the palm of the hand. The resulting image has a greater number of unique areas for identification compared to the same fingerprint scanning technology, reliability is comparable to the technology of identification by the iris, the cost of the final solution, although higher than that of fingerprint systems, is much lower than the rest of the listed ones.
The use of technology PalmSecure provides several advantages when used in the enterprise:
- Hygiene - there is no need for direct contact of the hand with the reader. Scanning is made at a short distance from it.
- High reliability - statistics of failure and incorrect access are at a very high level.
- Hidden identifier (palm) - there is no way to physically steal data for fake.
Of course, there are some restrictions on the use of technology (camera illumination), but for intra-office applications, its use is fully justified.
In the international market, technology has been used for a long time; it has worked well in such applications as:
- Banking identification, ATMs (Japan - 9000 ATMs, Brazil - 12000, Turkey - 1500)
- Medicine (Turkey - insurance system, private hospitals in the USA - registration and identification of patients, Austria - issue of drugs)
- Access control (UK - fitness centers, Germany - data centers)
- Time tracking (India, Malaysia, etc.)
In Russia, solutions based on Fujitsu PalmSecure were first introduced by the company Tendo . The company’s portfolio currently has several solutions that use Fujitsu products: ACS, time tracking, and solutions for easy integration of technology into existing accounting systems.
The principle of operation of the staff time tracking system
When you bring your palm to the device, the staff time tracking program records the time and date of the employee’s arrival / departure, the full name, department, position and work schedule of the employee. After scanning, the information enters the database. As a result, the time tracking program provides automatic registration of the time of arrival / departure of staff, monitoring the presence of staff in the field, providing management with operational information about absent employees.
Identification options
The logic of work of access control systems and accounting of working time is already described in sufficient detail in many sources, therefore, in this article we will focus only on the moments of operation of these systems when using the PalmSecure technology.
So, the systems are installed and configured.
The first step for the system to work in any scenario of work should be to register the vein image of the employee or visitor and save it in the database for further comparison. In the operating mode, the vein reader is constantly turned on and is waiting for the moment when the palm is brought to it. The reader can be placed both separately and as part of a special guide stand, which helps the user to correctly position the hand. In addition to the reading camera, the reader has four presence sensors (at the corners), which help to determine the correct position of the hand relative to the reader by the strength of the incoming reflected signal. This information is transmitted from the reader and can be used to provide hints to the user about the correct orientation of the palm. For quick recognition, the hand must be located parallel to the reading surface, however, a small angle of inclination is allowed. If, according to the reader, the arm is positioned correctly, it takes a picture of the pattern of the veins of the palm. In infrared light, the veins of the palm appear darker than the rest, and thus the reader gets a clear picture of the picture. Further, the reader encrypts the drawing using the AES algorithm and sends it to the System for processing. The drawing is converted by the System into a biometric sample, compressed and encrypted again. The resulting sample is stored in a database.

Employee recognition scenarios
IDENTIFICATION
Identification - a way to recognize the owner of the submitted biometric information by comparing with all previously registered samples stored in the database.
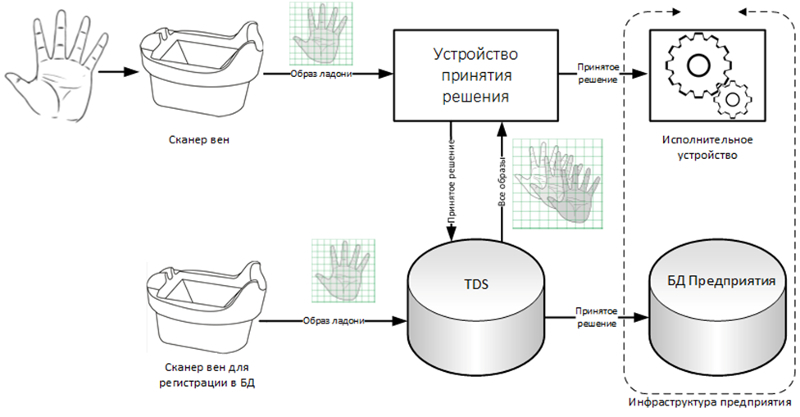
Previously, all the vein pictures of the hands of people who are allowed to perform any actions are recorded (scanned) in the database. Images of vein patterns are stored in the database. At the beginning of work, all images are transferred from the database to some kind of software decision-making device. An employee applies an action to a vein pattern reader to perform an action. The palm image is transmitted from the reader to the software decision-making device, where it is compared with all the registered images. When a match is found, the image is replaced with the corresponding unique identifier, according to which the device makes a decision on the admissibility of the action performed by this person in accordance with the logic prescribed in advance. If the decision is positive, the device sends the appropriate command to the actuator (for example, an electric lock on the door to open it). If necessary, information about the decision can be transferred for processing and storage in the database of the enterprise.
The system provides the ability to store images of both hands of one person. This feature helps to implement additional functionality. For example, a right-hand man scan will initiate a request for a standard pass, while a left-hand scan will force a pass under duress.
Verification
Verification is a way of recognizing a person, in which two identifiers are presented to the system (a palm vein pattern and, for example, a standard access card). The system automatically matches both identifiers and makes the appropriate decision.

Operating procedure:
- A person scans the access card using a reader. A unique identifier is transmitted from the reader to a software decision-making device.
- The device sends a request to the database containing this identifier.
- By identifier in the database is the corresponding image of the palm, which is transmitted back to the decision-making device. Comparison of the palm image and the card identifier is made in advance when registering persons who have access to perform the requested actions.
- A person applies a hand to a vein pattern reader. There is a scanning pattern of the veins of the palm, which in the form of an image of the palm is transmitted to the decision-making device.
- The device compares the palm images received from the reader and from the database and, in accordance with the pre-set logic, makes a decision to perform the requested action. In case of a positive decision, the corresponding command is sent to the actuator.
If necessary, information about the decision can be transferred for processing and storage in the database of the enterprise. This method allows you to significantly increase the speed of decision making with a large number of system users.
COMPARE
This mode is preferred in a situation where the end customer is required to not store identification data in the database. In this case, the system is not subject to the requirements voiced by Federal Law 153-FZ regarding the storage of personal data.
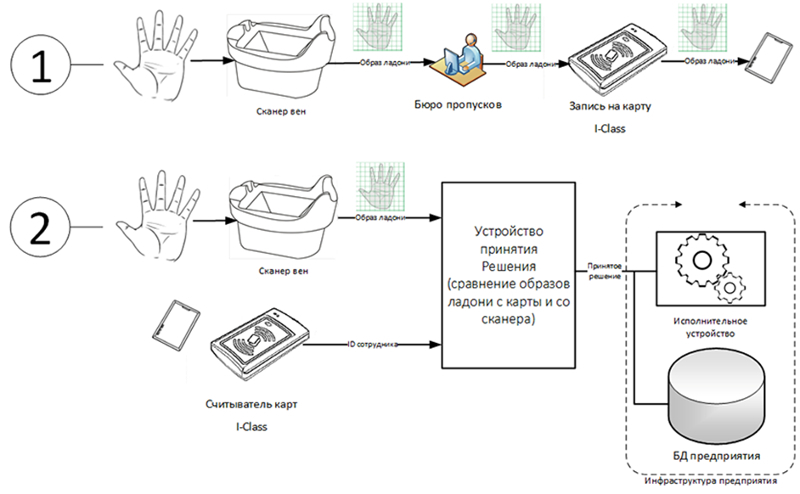
To implement this method, it is necessary to use storage media that have enough internal memory to store a digital image of the palm. The palm image on storage media may take about 3 Kb. One of the most convenient on the form factor and ease of use at the moment such carriers are smart cards with increased memory capacity (for example, HID i-Class).
In this case, the person consistently presents the palm of the system (with the help of a vein reader) and the image of the palm of the information carrier (with the help of an appropriate reader). The software device compares the presented images and, with complete coincidence, sends the corresponding command to the execution unit.
The system of the accounting of working hours can work in any of the described modes. Thus, identification methods can be varied, which will lead to a significant increase in decision making reliability. For example, several options:
- Figure veins. Identification by one hand only. Reading a second hand means access under duress.
- Figure veins. Identification by both hands (sequential reading).
- Figure veins + access card
- Vein pattern + digital password
The PalmSecure reader itself does not imply any feedback from the user. But at the same time there is a wide selection of guide stands, the case of which allows you to upgrade the functionality of the device. So, the company Tendo significantly refined the body of the reader. Red and green LEDs were added to visualize the interaction of the reader with the user, and a speaker was installed for sound feedback. In addition, if necessary, you can install a hand sensor in the case, which will automatically turn on the reader when you bring your palm to it.
Analytics provided by the staff time tracking program
When using the staff time tracking program, the personnel department can view various types of reports that are automatically generated by the system — reports on the working time of each employee or departments as a whole, time sheets for the month and year, and reports on sick days, holidays and departures.
- The reports on the working time of each employee indicate the time of arrival and the time of leaving the employee, the rate of working time, as well as discrepancies between the hours worked and the rate of working time. It also reflects the work schedule, which can be set individually for each employee.
- In addition to the listed information, department reports also indicate the departments to which each employee belongs.
- The month card reflects daily information on the number of hours worked by each employee for each day of the month.
- The table for the year for each employee indicates the number of days worked per year, the number of absenteeism, vacation days, visits to the client, the number of days of absence and travel.
- The report on holidays and sick leave for each employee reflects the total number of holidays and sick leave per year, as well as the total number of holidays and sick leave for each month of the year.
- The departure report for each field employee reflects the number of trips, the amount of travel expenses and transportation costs.
findings
Many trade organizations, as well as banks, organizations of the service sector, state institutions show a greater interest in automatic time tracking systems, regarding these technologies as a means of improving the discipline and productivity of employees. With the use of Fujitsu PalmSecure technology in an ACS or SURV, not only the reliability of the system, but also the degree of protection of personal data of employees required to record working time significantly increases.
Source: https://habr.com/ru/post/271721/
All Articles