Critical vulnerability in Dell computers allows hackers to access almost any data: How to protect

On November 22, 2015, the network received information about the critical vulnerability to which a number of Dell products are susceptible (here is the mention of it on Habré). The programmer Joe Nord, who described it on his blog, was the first to notice the error. The developer reported that he had purchased a Dell Inspiron 5000 laptop, which was preinstalled with a root security certificate called eDellRoot
The problem is that the private key of this root certificate is stored on the computer itself, which opens up a wide range of possibilities for attackers to conduct man-in-the-middle attacks.
')
Learn more about eDellRoot
As Nord found out, the eDellRoot certificate is by default trusted in the system and is intended for “any” purposes - that is, the certificate is more “powerful” than the fully legitimate certificate from DigiCert. Its validity is limited to 2039 year. In addition, the description of the certificate means that the user has a secret key for him - which he usually should not have.

Thus, an attacker who gains access to this secret key for a certificate can forge other certificates to access any sites, and the computer will take them as trusted — all this opens up possibilities for conducting a man-in-the-middle attack, characterized by the substitution legitimate resources by their malicious copies.
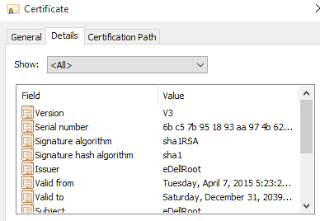
In this case, access to this key is not difficult, since it is installed on many new Dell computers models XPS, Precision and Inspirion, and is stored locally on each such device.
Dell began shipping devices preinstalled with eDellRoot in August of this year.
What to do
Representatives of the device manufacturer stated that the eDellRoot certificate is not malicious (“malware or adware”), with its help the company did not collect any personal information, but only wanted to be able to quickly identify the device model when the owner turned to the support service.
According to the representative of Dell Laura Thomas (Laura Thomas), the company just wanted to increase the level of service and reduce the waiting time for the support service.
"Sometimes good intentions, such as faster access to customer machines to speed up service, can have dire consequences in terms of system security, if the implementation of such measures may carry security risks."
In addition, the company also published instructions for deleting the certificate from the computer. From this instruction, in particular, it is clear that deleting a certificate just won't work out - the included .DLL plug-in after installing the file installs the certificate again. Therefore, to completely remove the certificate, you need to delete the .DLL itself — Dell.Foundation.Agent.Plugins.eDell.dll —and the eDellRoot certificate itself.
In a statement on its website, Dell also promised not to use unsafe certificates in the future.
You can check your computer for a certificate at edell.tlsfun.de .
Conclusion
Obviously, the root certificate and the private key accessible to all are a serious loophole that opens the way to the system. This security bug makes it possible to potentially intercept even the secure connections of some applications, replace data, install applications bypassing protective devices, and so on.
In this regard, the statements of the representatives of the vendor that they did not consider and could not take into account possible malicious actions using this certificate and making changes to the system. It can be argued with a high degree of confidence that in the near future the attackers will take advantage of this.
Experts at Positive Technologies recommend that users check their system and, if necessary, use the above recommendations and delete the certificate and related modules. Such a test is recommended to pass not only the "happy" owners of these laptops, since other Dell models may also contain this flaw.
Recall that Dell was not the only IT company caught in the scandal because of inadequate security for users of its products. Many netizens and journalists compared the current situation with the one in which Lenovo got into last winter.
Then the “spy” functionality of the Superfish program shipped with Lenovo computers caused a serious scandal in the winter of 2015. After a flurry of criticism, Lenovo recognized the problem and presented various ways to remove the utility. However, this did not save the company from revenge from hackers from Lizard Squad, who hacked into Lenovo.com.
Source: https://habr.com/ru/post/271649/
All Articles