We will load everything: demonstration of the ІXIA solution for load tests
Here we have already begun a series of publications about such a vendor as ІXIA. The company develops and markets solutions for a wide variety of load tests of any IT systems. Today we have a video of the presentation at booth IXIA, at the exhibition MUK Expo 2015 . It consists of two parts - a review of solutions, and a live demonstration of the solution ( from 10 minutes ): IXIA will load Juniper equipment
Here's a video
For those who do not want to watch the entire video - under the cut decoding with screenshots
Disclaimers:
1. Transcript with small editing.
2. Please remember the difference in written and oral speech.
3. Screenshots in large size, otherwise nothing can be disassembled.
- Good afternoon, dear colleagues. My name is Sergey Polishchuk. I am grateful to you that you attended our event, in particular, that you paid your attention to our IXIA stand.
')
- We will divide our demonstration into two parts: I will tell you a little about the company briefly, and then Andrew will show you the hardware and software solution, which is on the stand to the left.
- Probably for many this manufacturer is quite new. I would like to briefly tell you a little bit about what the company offers the solution and in general in which market and in which segment it works. IXIA began its work in 1997. She presented solutions for testing in IP Ethernet networks. That is, these were her classic products with which she started her business. And then, in principle, she developed all of her solutions in close to this segment, and also bought some of her successful competitors.
And now IXIA has a wide enough portfolio that covers not only solutions for testing in IP Ethernet, it is also solutions for testing in wifi networks, solutions for testing wireless mobile operators, that is, 2G, 3G, LTE, GPRS - everything what is connected with mobile networks; it is also a security testing solution called BreakingPoint. That is, it was a unique company acquired by IXIA, a security testing company. Then I will briefly also talk about this decision.
In fact, if you describe the company's philosophy, then it can be described with two proverbs. “Trust, but verify” - as a rule, we have, let's say, the maximum synthetic tests are made when choosing equipment. IXIA offers tools that will allow you to not trust the word, yes, but to check and make sure that, indeed, the solutions that are bought, which are installed on the network, they meet your requirements, and that later you will not regret the money spent. And also the proverb "Measure a hundred times, cut once." But instead of measuring out a hundred times, you again get a professional device that will allow the engineering department, the department that maintains the network, to do it all in a short time and professionally simulate the network, simulate any segment of the network and check, save time to save time. That is, tasks that are solved, for example, with operators, with corporate customers in 2-3 months, with the help of these kits are solved literally in weeks. That is a crazy time saver.
IXIA's hardware helps customers answer questions such as: will the network design be viable? That is, even at the design stage, we can check all this in demonstration conditions, emulate some part of the network, create conditions for the experimented device, create a virtual network that will meet the conditions of the customer. And thus, to make sure before the introduction whether the project is viable, to confirm whether we really designed everything correctly. It is also, in principle, cost savings, because in any purchase, in most cases, everyone is guided by the maximum of any correspondences that are prescribed by each vendor: corresponds / does not match. Using solutions from IXIA, it is possible to verify this with your own eyes. That is, just take the device, generate traffic, and the traffic is the one that is specific to your network, which is important.
Because even in principle, more or less identical in class devices can work differently. Therefore, you check it all on your network, with your traffic. There are also answers to questions, for example: how to improve the efficiency of application transfer on the network, how to identify bottlenecks on the network, how to implement a new service. That is, you can simulate the traffic or service that you run on your network, be it video, voice, data - in any form, that is, configure your profile and run it on the network, reveal, for example, how ready your network is to deploy this service. Portfolio, as I have already said, IXIA's company consists not only of solutions for testing IP Ethernet and others.
- The company MUK in its laboratory has a hardware and software device, presented by Andrew on the rack. It is called IXIA XM2. It is equipped with modular cards, in principle, is typed by any cards, and their main value is the processor power that generates traffic at the port speed. It means that the classic IXIA software products are working here, which are called IxNetwork and IxLoad. IxNetwork generates traffic of the second and third levels, respectively, that is, it is more functional testing, for example, routing, switching, NPLS, it can be any variations of CarrierGrade, CarrierEthernet, it can be IP-Multicast, that is, any client scenario in principle You can test, simulate using this kit.
And also the second software product is an IxLoad product that generates traffic level four-seven. That is, it is the application itself. IXIA has very good expertise and, in principle, many companies in the world, the main customers are, of course, manufacturers of network equipment, that is, everyone, in principle, the manufacturer represented here has 100% probability in his laboratory IXIA test kits. IXIA also has national operators among the key customers, and now the company after buying BreakingPoint, which has been involved in security testing, and Net Optics, if someone heard, probably, has expanded its corporate portfolio and entered the corporate market. That is, it works quite tightly now with the public sector.
In the world, I can give you an example, it is used at NATO command and staff exercises, maybe someone heard. With the help of the IXIA BreakingPoint kit, the IT staff of NATO and the European command of the US forces in Europe are trained. That is, this is an annual command and staff exercise. And specifically for cyber protection, BreakingPoint is used. That is, sits a few teams. One team generates attacks, another - traffic, and the third is trying to somehow implement the protection, adjust the protective means that are tested. Also, as an example, I can cite the close cooperation of IXIA with such organizations that are engaged in expertise in the IT industry: this is Miercom, this is Tolly Group, this is NSS Labs. Those security people probably know what I’m talking about. All the techniques that NSS Labs uses are techniques that are created in conjunction with IXIA.
- Probably, now let's move on to the demo part, pass the word to Andrei Kostretsky - this is an engineer in the direction of IXIA - and he will introduce you closer and briefly to the decision of IxNetwork and describe which demonstration region we have built on the stand.
Demonstration ( from 10 minutes )
Colleagues, hello. Let's go to our booth. What do we have? We have the IXIA and we will load the Juniper SRX240. What is our scenario today? This is what the RX-Network interface looks like. In the center we have a device that will be tested, or a group of devices, the so-called “blow” device, an undertest. One port is included in IXIA and it will emulate the work of BGP here. We will announce 600 thousand routes. On the other hand, we will have OSPF announced in BGP 20 thousand routes. That is, such a border for some small provider for a corporate network. In fact, this is a simple test, you can make a much larger network scale, you can completely emulate your network. For example, it could be some PE device, we can put a neighbor to it, we can put a CE device on each, we can emulate some subscribers, on the other hand we can put P-routers, we can put PE, CE, we can emulate L2- L3 VPN It can be used to test the brace, emulating subscriber, that is, there are many options.

About the interface. Here he is. It looks like this. I have already prepared the script, and we are launching it. Now we will see how the protocol gradually begins to rise: the Ethernet level, then IPO4, BGP and OSPF. The fact that we have green is started, red is something that does not work, and when we have yellow it means 50 to 50, something works, something doesn’t, for example, if subscriber: one doesn’t work , 10 thousand work - will be yellow. So, BGP has risen, OSPF does not rise, let's look at what. But in fact, it’s immediately obvious why it doesn’t rise - there is still an exchange of routes.

You can go to Juniper, see what it looks like from his side. Yes. That is, here the session has risen, and the routes are loaded. Not all yet, but here, little by little. We look that we have with OSPF. So, OSPF is loaded a little slower, we will wait until it rises. Here it is. Further, over the configured protocols, we can see which routes will then be received from our router. Now everything is loaded, they will change routes, I will show you how.

Next we can create traffic. We can create layer2-layer3 traffic, drive them as from one subscriber to another at different ends, so we can make a random group into a group, in one direction, in two directions, we can set the packet size, we can specify some kind of traffic mix - there are many options. Let's show what our traffic looks like that will go. That is, it is built very simply.

There are such wizards on which we set up a group, say, with BGP with a network of group two, we will send a route to OSPF, to group one. Yes, then there are wizards: you can build QoS, you can build VLan, we can adjust the specified speed level, it can be some manually defined, or it can be line-rate. That is, we have a gig interface, it will send hygiene, yes, maybe 50% - it will be half a gig. So, look at our script. OSPF has risen, BGP is working.
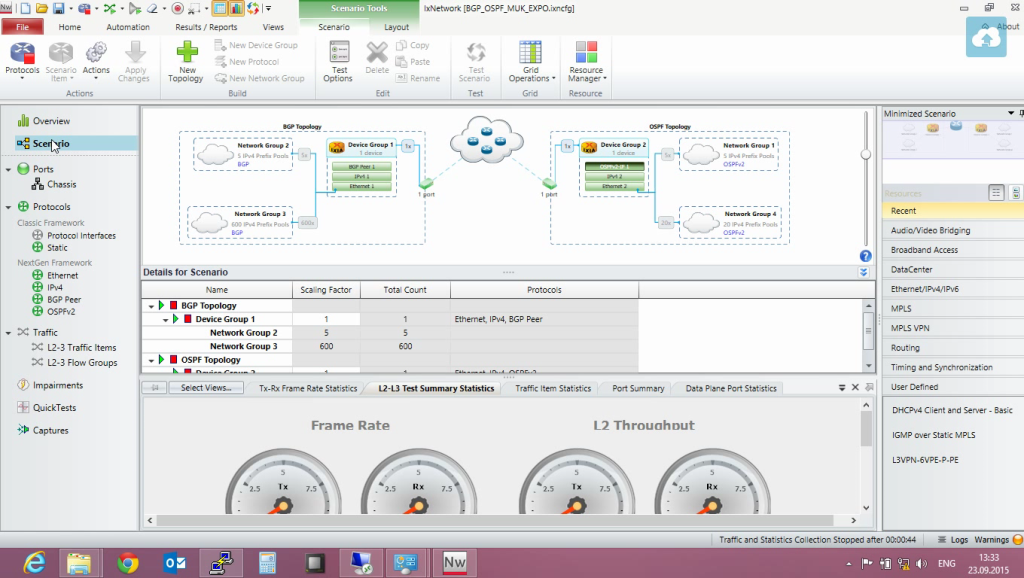
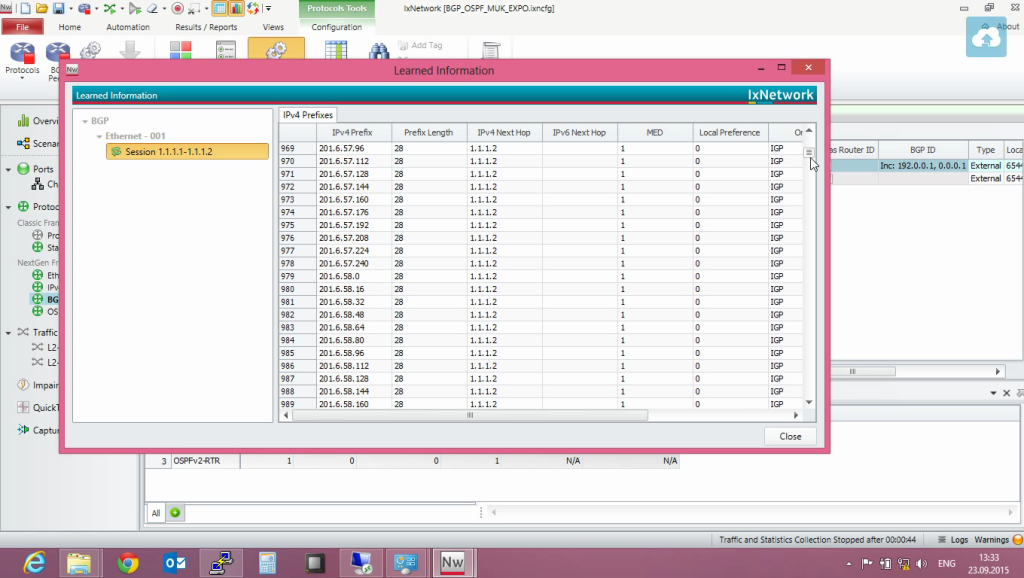
We look that we have routes. So, there are 20 thousand routes, and BGP also has 60 thousand routes. This is where the redistribution policy is configured, and we redistribute our OSPF routes to BGP. We can see what our IXIA received. We go in the protocols, we look. And here are the routes we get from Juniper. We look at everything, now they are already in the table. Yes, all loaded. Let's start the traffic, see how it all looks with the traffic.
So, actually, here we have sent packets on the left, here are the received packets, we can look at the statistics sessions. Actually, we are looking at which interface, which interface, which address, which address, which quantity is received-sent, the number of losses. That is, there are a lot of options for setting up monitoring.
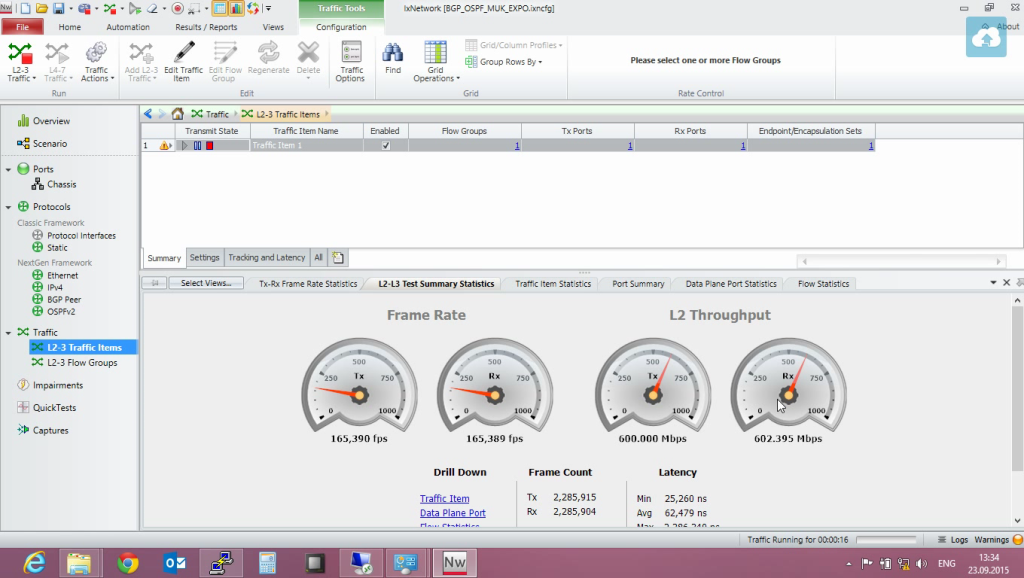

Head over to Juniper, see what traffic there really is. So, here we see that we have traffic. I started the traffic ... So, now I’ll open the load network.

That is, our traffic goes only in one direction, it was possible to send in two directions, but so far only with BGP on OSPF. That is, we now have a table loaded to capacity and 600 Mbit MX are running. We can see the percentage of losses. That is, in principle, Juniper corresponds to the data readings.
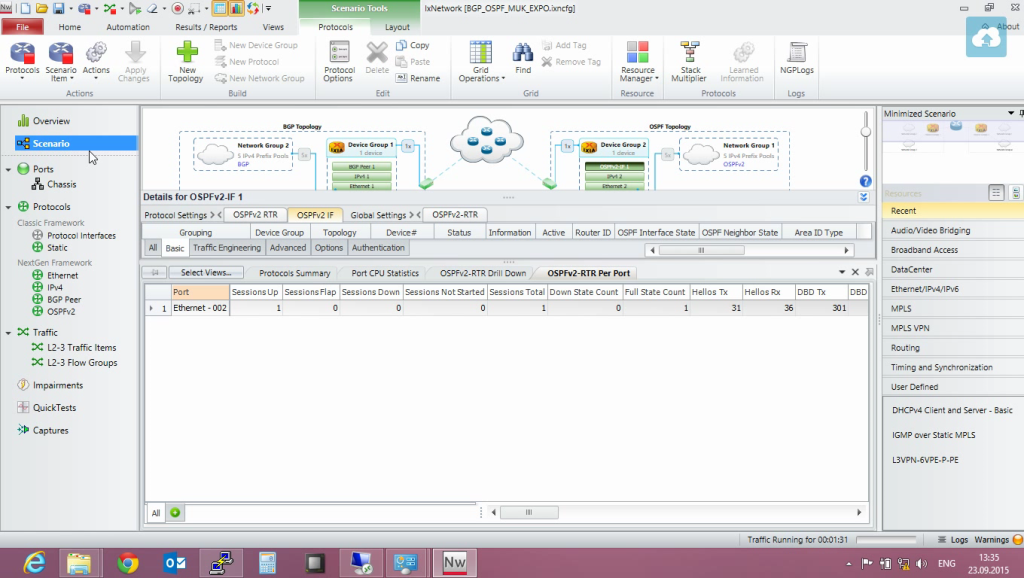
That is, you can ship more, begin packet losses, and so on. That is, with such scenarios, you can check the performance of the device, as far as it corresponds to data shits. This may not be a single device, it may be a number of devices. You can emulate the work of different protocols. If you need to drive away some more specific traffic, X-Load is used for this, it allows you to collect the necessary traffic from Layer 1 to Layer 7, check not just “does not reach,” comes with what quality, check jitter and other, other. Well, actually, this is such a simple demonstration.
Let's.
- “How can I check encryption? For example, a VPN-channel 100 Mbit, encryption ... "
Yes, everything can emulate.
- We can show in the demonstration laboratory of the MUK company or we can come to you. And show you.
- Thank you, Andrei. I would also like to, of course, show you the work of the solution, that’s how a colleague asked for security, this is a very interesting decision. Our company has already held several demonstrations and testing in Ukrainian banks. They were satisfied. Vladimir and I were recently at a banking conference, and there the guys praised the IXIA very much, thanks to them. Well, probably, you have already realized that IXIA is not what stands on the net, it is what stands in your laboratory and helps you technically. I would very much like you to have an understanding that this is not an expenditure part of the IT budget. This tool, however, in the long run, which will help save money. Here it is important that customers in Ukraine understand this. We make every effort for this.
For questions about IXIA decisions contact: dcs@muk.ua.
Distribution of IXIA solutions in Ukraine , Belarus , CIS countries .
Juniper distribution in Ukraine , Georgia , Azerbaijan, Belarus , Armenia , Moldova , CIS countries - juniper@muk.ua
Training courses and trainings on Juniper solutions (TC MUK, Kiev)
Training courses / trainings / workshops in various IT areas - MUK Training Center (Kiev)
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Here's a video
For those who do not want to watch the entire video - under the cut decoding with screenshots
Disclaimers:
1. Transcript with small editing.
2. Please remember the difference in written and oral speech.
3. Screenshots in large size, otherwise nothing can be disassembled.
- Good afternoon, dear colleagues. My name is Sergey Polishchuk. I am grateful to you that you attended our event, in particular, that you paid your attention to our IXIA stand.
')
- We will divide our demonstration into two parts: I will tell you a little about the company briefly, and then Andrew will show you the hardware and software solution, which is on the stand to the left.
- Probably for many this manufacturer is quite new. I would like to briefly tell you a little bit about what the company offers the solution and in general in which market and in which segment it works. IXIA began its work in 1997. She presented solutions for testing in IP Ethernet networks. That is, these were her classic products with which she started her business. And then, in principle, she developed all of her solutions in close to this segment, and also bought some of her successful competitors.
And now IXIA has a wide enough portfolio that covers not only solutions for testing in IP Ethernet, it is also solutions for testing in wifi networks, solutions for testing wireless mobile operators, that is, 2G, 3G, LTE, GPRS - everything what is connected with mobile networks; it is also a security testing solution called BreakingPoint. That is, it was a unique company acquired by IXIA, a security testing company. Then I will briefly also talk about this decision.
In fact, if you describe the company's philosophy, then it can be described with two proverbs. “Trust, but verify” - as a rule, we have, let's say, the maximum synthetic tests are made when choosing equipment. IXIA offers tools that will allow you to not trust the word, yes, but to check and make sure that, indeed, the solutions that are bought, which are installed on the network, they meet your requirements, and that later you will not regret the money spent. And also the proverb "Measure a hundred times, cut once." But instead of measuring out a hundred times, you again get a professional device that will allow the engineering department, the department that maintains the network, to do it all in a short time and professionally simulate the network, simulate any segment of the network and check, save time to save time. That is, tasks that are solved, for example, with operators, with corporate customers in 2-3 months, with the help of these kits are solved literally in weeks. That is a crazy time saver.
IXIA's hardware helps customers answer questions such as: will the network design be viable? That is, even at the design stage, we can check all this in demonstration conditions, emulate some part of the network, create conditions for the experimented device, create a virtual network that will meet the conditions of the customer. And thus, to make sure before the introduction whether the project is viable, to confirm whether we really designed everything correctly. It is also, in principle, cost savings, because in any purchase, in most cases, everyone is guided by the maximum of any correspondences that are prescribed by each vendor: corresponds / does not match. Using solutions from IXIA, it is possible to verify this with your own eyes. That is, just take the device, generate traffic, and the traffic is the one that is specific to your network, which is important.
Because even in principle, more or less identical in class devices can work differently. Therefore, you check it all on your network, with your traffic. There are also answers to questions, for example: how to improve the efficiency of application transfer on the network, how to identify bottlenecks on the network, how to implement a new service. That is, you can simulate the traffic or service that you run on your network, be it video, voice, data - in any form, that is, configure your profile and run it on the network, reveal, for example, how ready your network is to deploy this service. Portfolio, as I have already said, IXIA's company consists not only of solutions for testing IP Ethernet and others.
- The company MUK in its laboratory has a hardware and software device, presented by Andrew on the rack. It is called IXIA XM2. It is equipped with modular cards, in principle, is typed by any cards, and their main value is the processor power that generates traffic at the port speed. It means that the classic IXIA software products are working here, which are called IxNetwork and IxLoad. IxNetwork generates traffic of the second and third levels, respectively, that is, it is more functional testing, for example, routing, switching, NPLS, it can be any variations of CarrierGrade, CarrierEthernet, it can be IP-Multicast, that is, any client scenario in principle You can test, simulate using this kit.
And also the second software product is an IxLoad product that generates traffic level four-seven. That is, it is the application itself. IXIA has very good expertise and, in principle, many companies in the world, the main customers are, of course, manufacturers of network equipment, that is, everyone, in principle, the manufacturer represented here has 100% probability in his laboratory IXIA test kits. IXIA also has national operators among the key customers, and now the company after buying BreakingPoint, which has been involved in security testing, and Net Optics, if someone heard, probably, has expanded its corporate portfolio and entered the corporate market. That is, it works quite tightly now with the public sector.
In the world, I can give you an example, it is used at NATO command and staff exercises, maybe someone heard. With the help of the IXIA BreakingPoint kit, the IT staff of NATO and the European command of the US forces in Europe are trained. That is, this is an annual command and staff exercise. And specifically for cyber protection, BreakingPoint is used. That is, sits a few teams. One team generates attacks, another - traffic, and the third is trying to somehow implement the protection, adjust the protective means that are tested. Also, as an example, I can cite the close cooperation of IXIA with such organizations that are engaged in expertise in the IT industry: this is Miercom, this is Tolly Group, this is NSS Labs. Those security people probably know what I’m talking about. All the techniques that NSS Labs uses are techniques that are created in conjunction with IXIA.
- Probably, now let's move on to the demo part, pass the word to Andrei Kostretsky - this is an engineer in the direction of IXIA - and he will introduce you closer and briefly to the decision of IxNetwork and describe which demonstration region we have built on the stand.
Demonstration ( from 10 minutes )
Colleagues, hello. Let's go to our booth. What do we have? We have the IXIA and we will load the Juniper SRX240. What is our scenario today? This is what the RX-Network interface looks like. In the center we have a device that will be tested, or a group of devices, the so-called “blow” device, an undertest. One port is included in IXIA and it will emulate the work of BGP here. We will announce 600 thousand routes. On the other hand, we will have OSPF announced in BGP 20 thousand routes. That is, such a border for some small provider for a corporate network. In fact, this is a simple test, you can make a much larger network scale, you can completely emulate your network. For example, it could be some PE device, we can put a neighbor to it, we can put a CE device on each, we can emulate some subscribers, on the other hand we can put P-routers, we can put PE, CE, we can emulate L2- L3 VPN It can be used to test the brace, emulating subscriber, that is, there are many options.

About the interface. Here he is. It looks like this. I have already prepared the script, and we are launching it. Now we will see how the protocol gradually begins to rise: the Ethernet level, then IPO4, BGP and OSPF. The fact that we have green is started, red is something that does not work, and when we have yellow it means 50 to 50, something works, something doesn’t, for example, if subscriber: one doesn’t work , 10 thousand work - will be yellow. So, BGP has risen, OSPF does not rise, let's look at what. But in fact, it’s immediately obvious why it doesn’t rise - there is still an exchange of routes.

You can go to Juniper, see what it looks like from his side. Yes. That is, here the session has risen, and the routes are loaded. Not all yet, but here, little by little. We look that we have with OSPF. So, OSPF is loaded a little slower, we will wait until it rises. Here it is. Further, over the configured protocols, we can see which routes will then be received from our router. Now everything is loaded, they will change routes, I will show you how.

Next we can create traffic. We can create layer2-layer3 traffic, drive them as from one subscriber to another at different ends, so we can make a random group into a group, in one direction, in two directions, we can set the packet size, we can specify some kind of traffic mix - there are many options. Let's show what our traffic looks like that will go. That is, it is built very simply.

There are such wizards on which we set up a group, say, with BGP with a network of group two, we will send a route to OSPF, to group one. Yes, then there are wizards: you can build QoS, you can build VLan, we can adjust the specified speed level, it can be some manually defined, or it can be line-rate. That is, we have a gig interface, it will send hygiene, yes, maybe 50% - it will be half a gig. So, look at our script. OSPF has risen, BGP is working.

We look that we have routes. So, there are 20 thousand routes, and BGP also has 60 thousand routes. This is where the redistribution policy is configured, and we redistribute our OSPF routes to BGP. We can see what our IXIA received. We go in the protocols, we look. And here are the routes we get from Juniper. We look at everything, now they are already in the table. Yes, all loaded. Let's start the traffic, see how it all looks with the traffic.

So, actually, here we have sent packets on the left, here are the received packets, we can look at the statistics sessions. Actually, we are looking at which interface, which interface, which address, which address, which quantity is received-sent, the number of losses. That is, there are a lot of options for setting up monitoring.


Head over to Juniper, see what traffic there really is. So, here we see that we have traffic. I started the traffic ... So, now I’ll open the load network.

That is, our traffic goes only in one direction, it was possible to send in two directions, but so far only with BGP on OSPF. That is, we now have a table loaded to capacity and 600 Mbit MX are running. We can see the percentage of losses. That is, in principle, Juniper corresponds to the data readings.

That is, you can ship more, begin packet losses, and so on. That is, with such scenarios, you can check the performance of the device, as far as it corresponds to data shits. This may not be a single device, it may be a number of devices. You can emulate the work of different protocols. If you need to drive away some more specific traffic, X-Load is used for this, it allows you to collect the necessary traffic from Layer 1 to Layer 7, check not just “does not reach,” comes with what quality, check jitter and other, other. Well, actually, this is such a simple demonstration.
Let's.
- “How can I check encryption? For example, a VPN-channel 100 Mbit, encryption ... "
Yes, everything can emulate.
- We can show in the demonstration laboratory of the MUK company or we can come to you. And show you.
- Thank you, Andrei. I would also like to, of course, show you the work of the solution, that’s how a colleague asked for security, this is a very interesting decision. Our company has already held several demonstrations and testing in Ukrainian banks. They were satisfied. Vladimir and I were recently at a banking conference, and there the guys praised the IXIA very much, thanks to them. Well, probably, you have already realized that IXIA is not what stands on the net, it is what stands in your laboratory and helps you technically. I would very much like you to have an understanding that this is not an expenditure part of the IT budget. This tool, however, in the long run, which will help save money. Here it is important that customers in Ukraine understand this. We make every effort for this.
For questions about IXIA decisions contact: dcs@muk.ua.
Distribution of IXIA solutions in Ukraine , Belarus , CIS countries .
Juniper distribution in Ukraine , Georgia , Azerbaijan, Belarus , Armenia , Moldova , CIS countries - juniper@muk.ua
Training courses and trainings on Juniper solutions (TC MUK, Kiev)
Training courses / trainings / workshops in various IT areas - MUK Training Center (Kiev)
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/271577/
All Articles