Light Speck block cipher, or a speck of dust from an agency that does not exist

In June 2013, the NSA published a description of two light block ciphers - Simon and Speck [1] .
It happened in the midst of a scandal with Snowden, so the news was met with understandable skepticism. Especially because the article did not contain the results of cryptanalysis, but only a description of the algorithm and performance data.
')
Two years passed, no practical attacks on Simon or Speck appeared [2] , and the advantages (simplicity and flexibility) remained.
Unlike his younger brother Simon, which is optimized for hardware, Speck is designed for software implementation, including on devices with limited capabilities like microcontrollers. Since there are probably more programmers among readers than apparatchiks, the rest of the article will be about Speck.
Why do you need Speck when there is AES
Speck is intended for use in cases where AES is too heavy. In addition to conventional processors, which not only can quickly execute AES programmatically, but sometimes even contain its implementation in hardware, there are many small and weak processors around us that have every byte, clock and milliwatts in the account. With the growth of the Internet of things they will become even more.
This niche occupied RC4 for a long time until it became old. Speck's closest competitor is rather not AES, but ChaCha20.
What's inside
Speck is an ARX cipher (uses modulo addition, cyclic shift and exclusive OR). You can choose the length of the block and key depending on the task:
| Title | Block size, bits | Key length, bit | Number of rounds |
|---|---|---|---|
| Speck 32/64 | 32 | 16 * 4 = 64 | 22 |
| Speck 48/72 | 48 | 24 * 3 = 72 | 22 |
| Speck 48/96 | 48 | 24 * 4 = 96 | 23 |
| Speck 64/96 | 64 | 32 * 3 = 96 | 26 |
| Speck 64/128 | 64 | 32 * 4 = 128 | 27 |
| Speck 96/96 | 96 | 48 * 2 = 96 | 28 |
| Speck 96/144 | 96 | 48 * 3 = 144 | 29 |
| Speck 128/128 | 128 | 64 * 2 = 128 | 32 |
| Speck 128/192 | 128 | 64 * 3 = 192 | 33 |
| Speck 128/256 | 128 | 64 * 4 = 256 | 34 |
The block is divided into two words, the key length is a multiple of the word length. All operations are performed on words, addition and subtraction are performed modulo 2 to the extent of word size.
Round function is similar to Threefish:
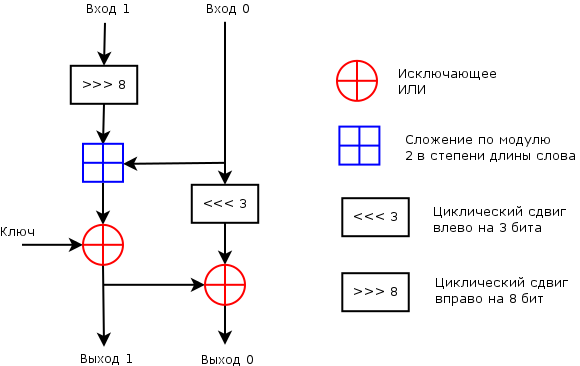
In Speck 32/64 cyclic shifts by 7 and 2 bits instead of 8 and 3.
The same function is used to get round keys (the round number is given to it as a key). Bruce Schneier praised the NSA for that .
 In the picture to the right are three rounds of Speck, where the length of the key is equal to the length of the block.
In the picture to the right are three rounds of Speck, where the length of the key is equal to the length of the block.This approach allows you to reuse the code of the round function and gives additional flexibility - if you need to optimize the speed of execution, you can count the round keys in advance, and if you want to save memory, you can read them on the go. The second option is also more convenient if you need to encrypt one block on a new key.
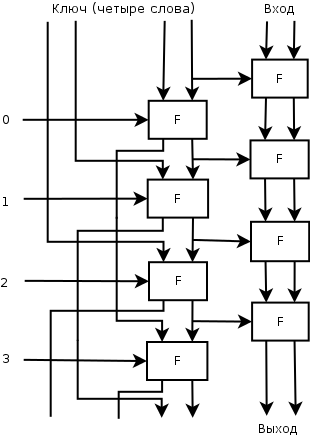 If the key is longer than a block, the key words are used in a circle. The picture on the left is four rounds, then everything is the same.
If the key is longer than a block, the key words are used in a circle. The picture on the left is four rounds, then everything is the same.Distinctive features of Speck are simplicity of implementation and a small amount of used memory. There are no magic constants or black permutation permutation boxes. There is not even a whitening key, this makes the first round.
Here’s what one of the possible Speck 128/128 implementations in C ++ looks like:
#include <inttypes.h> static inline void speck_round(uint64_t& x, uint64_t& y, const uint64_t k) { x = (x >> 8) | (x << (8 * sizeof(x) - 8)); // x = ROTR(x, 8) x += y; x ^= k; y = (y << 3) | (y >> (8 * sizeof(y) - 3)); // y = ROTL(y, 3) y ^= x; } void speck_encrypt( const uint64_t plaintext[2] , const uint64_t key[2] , uint64_t ciphertext[2] ) { uint64_t b = key[0]; uint64_t a = key[1]; ciphertext[0] = plaintext[0]; ciphertext[1] = plaintext[1]; for (unsigned i = 0; i < 32; i++) { speck_round(ciphertext[1], ciphertext[0], b); speck_round(a, b, i); // } } In this example, the cyclic shift is implemented slightly cumbersome through the usual shifts. If the compiler offers functions like _lrotl () and _lrotr (), then you can use them.
The above code is already enough to use in counter mode (CTR). Perhaps that is why the source publication does not even have a sample code for decoding.
In order to use CBC, the decryption function will still have to be added in the CBC mode. It is easy to do this - it is enough to change the order of operations in the round function to the opposite one, replace the addition with subtraction, shift right to shift to the left and vice versa. To consider round keys in advance and then go backward on them, or once calculate the last round key and then apply an inverted round function to it. Examples: Speck 64/128 , Speck 128/128 .
Not encrypted by one
Block ciphers are used not only in cryptography, but also for example in pseudo-random number generators. It is enough to take an arbitrary key, encrypt 0 on it, then 1, and so on. The resulting stream should look very random. Speck runs the classic Big Crush battery of pseudo-random number generators Test01 . At the same time, the Speck execution time is only three times slower than PCG32 (this is one of the fastest modern pseudo-random number generators, but without any claims to crypto resistance).
To believe or not to believe
Perhaps the NSA has left a loophole as in the notorious Dual_EC_DRBG or knows the unpublished attack method that some non-classified cryptographers are about to find. But given the simplicity of Speck, it’s hard to imagine exactly where such a loophole can be hidden, and Speck is more like DES in this respect.
Historical retreat
At one time, the NSA (possibly with an IBM filing) amended the DES lookup tables for very few obvious reasons, which gave rise to a lot of conspiracy theories. Subsequently, it turned out that these changes made DES more resistant to differential cryptanalysis, an unknown at that time cryptological community, and DES was never cracked in its long service history.
Free of charge
Speck is public domain (located in the public domain).
Links to primary sources
[1] Ray Beaulieu, Douglas Shors, Jason Smith, Stefan Treatman-Clark, Bryan Weeks, Louis Wingers
[2] Ray Beaulieu, Douglas Shors, Jason Smith, Stefan Treatman-Clark, Bryan Weeks, Louis Wingers Simon and Speck
Source: https://habr.com/ru/post/271435/
All Articles