New PandaLabs Quarterly Lab Quarterly Report

The PandaLabs anti-virus laboratory of Panda Security warns in its next quarterly report on the wave of cyber-attacks, as a result of which the security of information stored in various government bodies.
The so-called cyber-wars between countries have been observed for the past few years, but PandaLabs has found a growing interest among various countries in undermining security and theft of information from the governments of other countries of the world. Taking into account this fact, one of the most powerful attacks during the third quarter was the attack on the Hacking Team, which controls a variety of tools for cyber espionage and cyber attacks delivered to governments around the world.
')
“This case is particularly alarming because hackers were able to decipher the passwords of the most secure systems in the world,” explains Luis Corrons, Technical Director of PandaLabs. “The criminals not only wanted to know which customers from among the governments and special services of different countries use cyber-espionage services, but also which products they used.”
This wave of attacks, which took place in the third quarter of this year, also showed the hacking of the unclassified Pentagon mail system. It was carried out with the help of a complex attack, the customer of which, most likely, was the government of one of the states. Moreover, the FBI confirmed that it was able to detect an increase in interest from terrorists in conducting cyber-terrorist attacks against the United States, which, apparently, are currently at the planning stage.
Over 21 million new malware samples
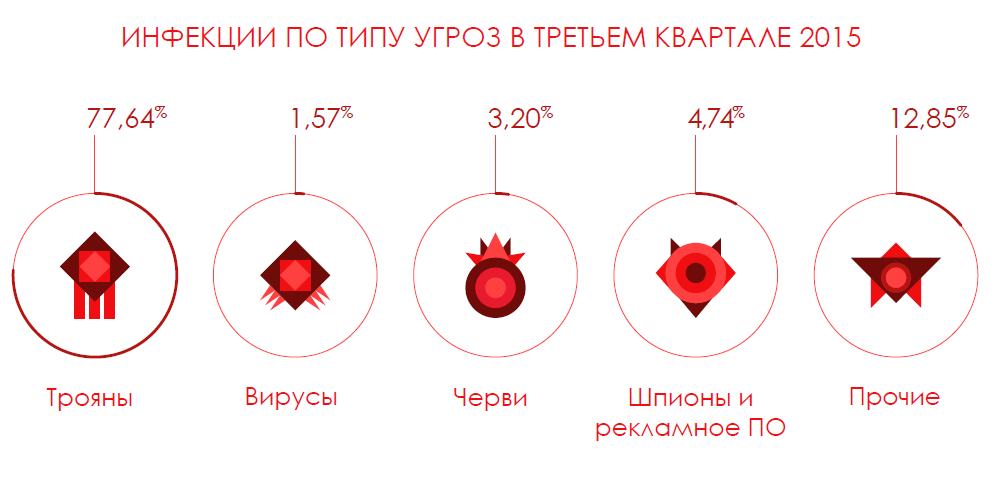
The quarterly report PandaLabs also contains information on the number of new malware samples created during this period. Although, as a rule, in the summer months there is a decrease in the number of new threats, the current year was an exception: in the third quarter there were 21 million new threats, which corresponds to a level of approximately 230,000 threats daily.
To carry out their attacks, hackers use Trojans, which are the most common type of malware (69.15%) and also cause most infections (77.64%). In second place with a large margin are classic viruses (11.34%). At the same time, special attention should be paid to potentially unwanted programs (PUP), which are contained in the “Others” category (7.96%).
Monitoring devices: the most common method
Third quarter confirmed that the Internet of things is now an integral part of our digital life. But their use carries with it new risks, which increases our chances of becoming victims of an attack. As the regular quarterly report showed, there are new methods that are used to put our security at risk.
Hackers are still attacking social networks and mobile devices, but now we have begun to observe the emergence of techniques for hacking routers at home and in the office, with the result that they fall under complete control by the hacker, while the victims do not even know about it.
Companies such as Jeep Cherokee and Land Rover also faced attacks on their cars. The latter was even forced to inform its users about errors in software from 65,000 machines that were sold during 2013. These errors allowed criminals to unblock the door through the Internet.
China remains the country with the highest infection rate
The PandaLabs report showed the distribution of infections in the world. The world average infection rate was 32.12%. As before, China topped the list of the most infected countries in the world, showing an infection rate of 45.35%. Behind him are Peru (42.89%) and Turkey (40.99%). Russia took the "honorable" fourth place, showing an infection rate of 38.32%.
Among other countries in which the infection rate was higher than the average world level, Poland (34.54%), Slovenia (33.98%), Colombia (33.11%), Spain (32.50%) and Costa Rica should be singled out. Riku (32.22%).
The top three countries with the lowest infection rate include Norway (20.12%), Sweden (21.33%) and Japan (22.75%).
You can view the full report here .
Source: https://habr.com/ru/post/271341/
All Articles