Two-factor authentication of Cisco AnyConnect clients. FreeRadius and Google Authenticator

In a previous article, I looked at setting up two-factor user authentication to connect to corporate resources through Cisco AnyConnect based on Active Directory and Microsoft Azure Multi-Factor Authentication Server (MFAS). Today I suggest you consider the option using FreeRadius and Google Authenticator.
From the advantages of this option, it can only be noted that this solution is free.
The disadvantages include:
- Integration with AD. Of course, FreeRadius can be integrated with AD via LDAP, but the architecture features of this solution provide for storing user profiles locally on the FreeRadius server.
- Only one type of authentication - Time-Based One Time Password (TOTP).
- The obviousness of the need to use the second factor (explained in the article).
Component installation
To install FreeRaduis, I used Debian Jessie 8.0 on a virtual machine.
Due to the fact that TOTP will be used for authorization, the time on the server must be correct. The best way to synchronize time is to install NTP.
sudo apt-get update sudo apt-get install ntp sudo apt-get install build-essential libpam0g-dev freeradius libqrencode3 git Download and install Google Authenticator: cd ~ git clone https://code.google.com/p/google-authenticator/ cd google-authenticator/libpam/ make make install We also need a group for users that we no longer want to authenticate: addgroup radius-off FreeRadius Setup
Since FreeRadius must have access to the .google_authenticator tokens in all user directories, it must have root privileges . To grant permissions, edit the file /etc/freeradius/radusd.conf .
Find the lines:
user = freerad group = freerad And replace with: user = root group = root Here, and in the future, do not forget to save the changes.Next, edit / etc / freeradius / users . We have to add the previously created “radius-off” group to the “Deny access for a group of users.” Section.
After the lines:
# Deny access for a group of users. # # Note that there is NO 'Fall-Through' attribute, so the user will not # be given any additional resources. # Add: DEFAULT Group == "radius-disabled", Auth-Type := Reject Reply-Message = "Your account has been disabled." DEFAULT Auth-Type := PAM Now edit / etc / freeradius / sites-enabled / default .
Find:
# Pluggable Authentication Modules. # pam And uncomment the line with pam')
We edit / etc / pam.d/radiusd . We tell FreeRadius to authenticate users on the basis of the local unix password + Google Authenticator code.
Here we must note out all lines that begin with @:
#@include common-auth #@include common-account #@include common-password #@include common-session And add: auth requisite pam_google_authenticator.so forward_pass auth required pam_unix.so use_first_pass Now we need to add a Radius client to FreeRadius to process requests from CISCO ASA. Add to the /etc/freeradius/clients.conf file: Client 192.168.110.6 { secret = Password shortname = ASA } User setup
Create user:
adduser mfatest Create a google-authenticator for it: cd /home/mfatest/ su mfatest google-authenticator In response, we get a QR code:
After that, you need to restart the FreeRadius service:
sudo service freeradius restart The Google Authenticator application must be installed on the mobile device (links for iOS and Android ).
Scan QR code using the Google Authenticator application. As a result, the mfatest account is tied to your mobile device.

Test authentication:
radtest <username> <unix_password><google_auth> localhost 18120 testing123 Where:- <unix_password> <google_auth> is the unix password + code from the application in one line. In this case, the password is Pass_123, the code is 731923.
- localhost 18120 testing123 are the parameters of the standard local client radius.
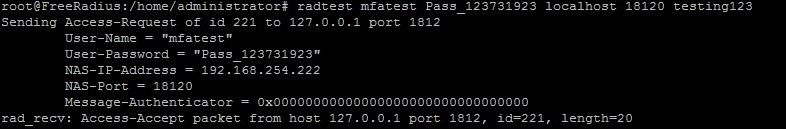
The result is:
radtest mfatest Pass_123731923 localhost 18120 testing123 If everything is set up correctly, you should get something like:
Configuring CISCO ASA
On the ASA, I recommend that you configure AnyConnect VPN gateway with local authentication. Make sure that the connection works, and then proceed to setting up authentication through Radius.
Configure RADIUS:
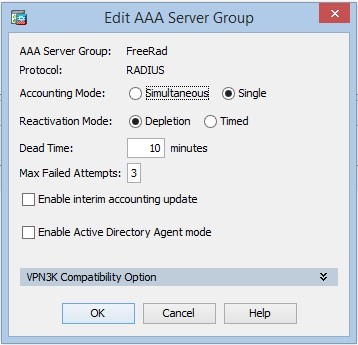
- Go to Configuration / Remote Access VPN / AAA / Local Users / AAA Server Groups and create a group:
- Add a server to the group:
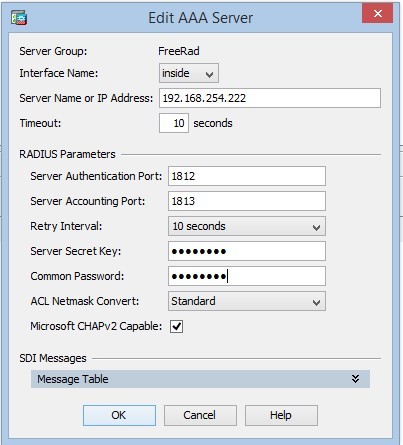
Where Server Name or IP Address is the address of our FreeRadius, Server Secret Key is the key that we configured for the client. - We are testing a bundle with a RADIUS server:
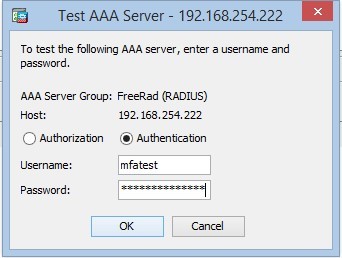
Where Password is a user password + code from Google Authenticator
If the test is successful, on the previously configured “AnyConnect Connection Profiles” we change the authentication from the local to the FreeRad group:
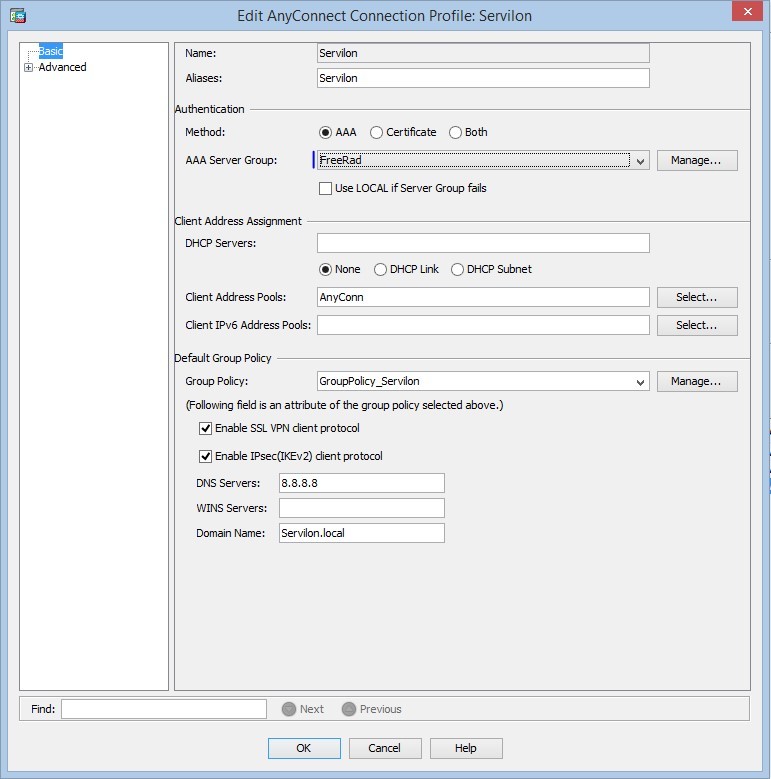
This completes the settings. To make sure everything works, we initiate a test connection.

This is where the non-obviousness about which I spoke appears. FreeRadius does not use phased authentication, it does not know how (at least I did not find it) to request the code for Google Authentication separately. Therefore, for successful authentication, as in the tests, in the Password box we enter the password + code. For an inexperienced user, this can be a barrier to comfortable use of the service.
This scheme is universal and can be implemented for any services that support authentication using the Radius protocol.
Our remaining articles http://servilon.ru/stati/
Source: https://habr.com/ru/post/271259/
All Articles