How to analyze a file for malware?
If you believe the latest report from Verizon for 2015, then today 70-90% of all malicious code is unique for each organization and therefore situations often occur when an organization has a channel (mail, Web, flash drive, mobile device, etc.) .) comes a file that causes suspicion, but the antivirus is “silent” and does not signal anything about this file. How to be in this situation? Let the file get into the network and start spreading over it? Or delete it? Or put in quarantine? Or maybe there is a way to still analyze the file and issue a verdict on it? Albeit without the name of a virus or trojan. Yes, there is such an option - it is called the Threat Intelligence Platform.
So, we have antiviruses installed in our organization at workstations. On the mail server is also antivirus. Anti-Virus is even integrated via ICAP or WCCP with a firewall. Can we be sure that everything that falls into our network is pure as a tear of a baby? Alas ... As the statistics of various companies show, the average time of network hacking / compromise detection (time-to-detect, TTD) is 200 (!) Days. Imagine two hundred days you do not know that you have already attacked and pull out of you confidential information. And suddenly, at some point in time you see this picture on the screen of your computer.
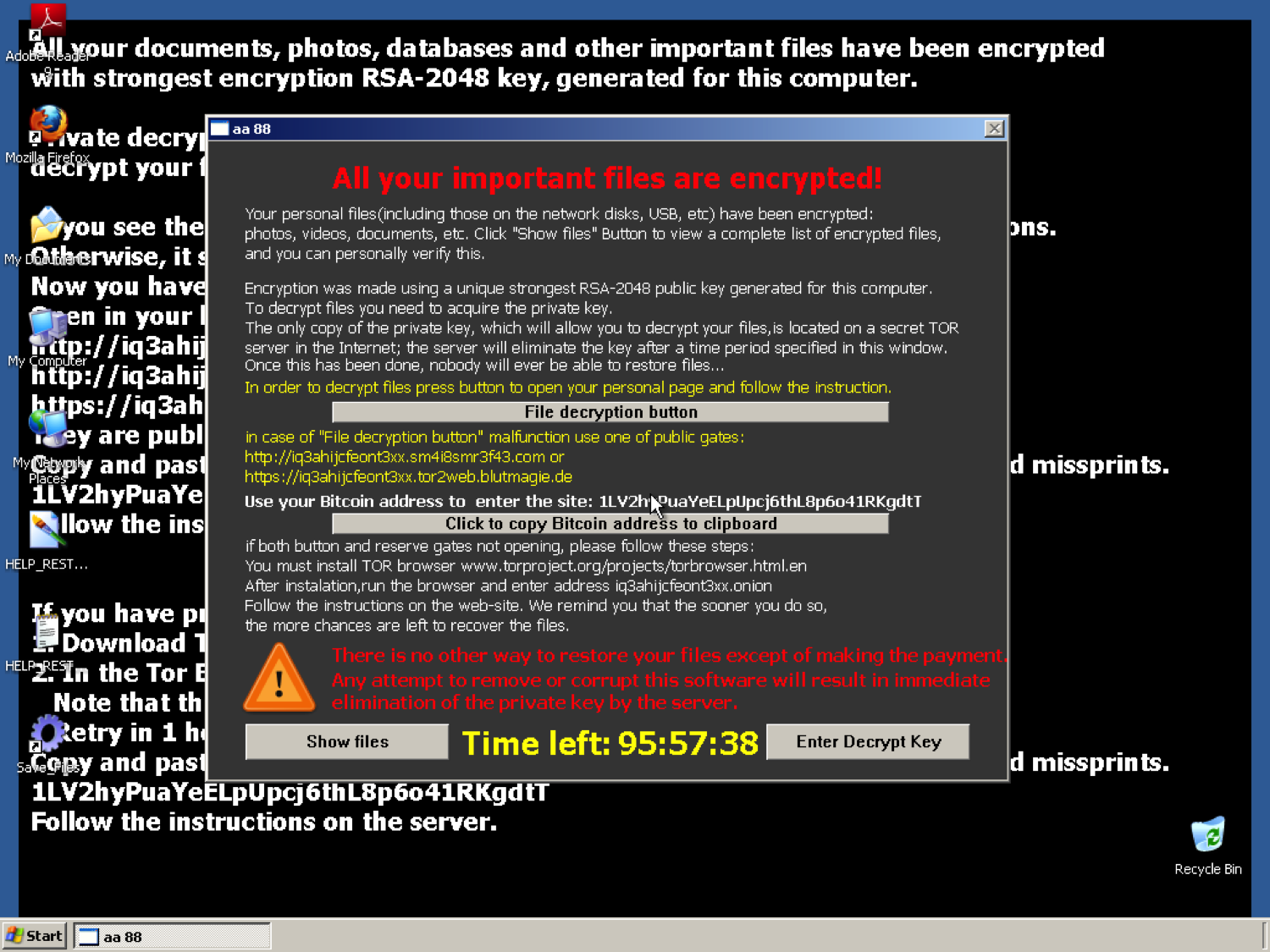
In the dynamics, and we are talking about TeslaCrypt encryption, it all looks even more interesting (until 2:30, everything is boring and ordinary):
')
You damn your antivirus, which caught nothing and already hoping a little, start communicating with the antivirus company. What if they help and decrypt the hard drive. But alas ... the antivirus company is not able to help you. Its task is to sell and maintain the antivirus, and not to work for you for free, being engaged in the analysis of your suspicious files. Perhaps over time, antivirus analysts will parse the file you sent and equip your antivirus with knowledge of it. But it will be only later, but for now you are facing the dilemma of “ Pay or not pay extortionists? ” At the recently held in Kazan conference “Information Security Code” I conducted a blitz survey on the topic: “If you sent suspicious files to antivirus companies, then Did you get a positive and prompt response? ” Alas, I can not boast of the forest raised in response to this question.
Suppose you learned a lesson from what happened and the next time you receive a suspicious file you want to do something with it. But what? At the hearing of many service Virus Total , which is presented by many as a means of analyzing malicious code. But it is not so. VirusTotal is essentially an automation tool for scanning more than 50 antiviruses to detect malicious code uploaded to the portal (or not to detect). VirusTotal simply automates the process of launching fifty antiviruses and gives you a verdict - detected or not. If there is no information about your file in the anti-virus database, then VirusTotal will not tell you anything either. In other words, the task of VirusTotal is to check the effectiveness of antiviruses, but not to help you analyze your files.

You can try to refer to another free resource - Malwr , which is a sandbox in which you can analyze suspicious files for malware.

However, the number of analysis methods on this service is not so great and modern malicious code, especially designed specifically for circumventing sandboxes (and this is becoming more and more), may go unnoticed by Malwr. In addition to it, there are a number of other platforms for analyzing malicious code. At the forum held in Moscow on the IT Security and Response Center for the SOC Forum, I gave a separate report with a brief overview of such platforms. Among others, I mentioned our own platform - Cisco AMP Threat Grid , which I would like to talk about in more detail.
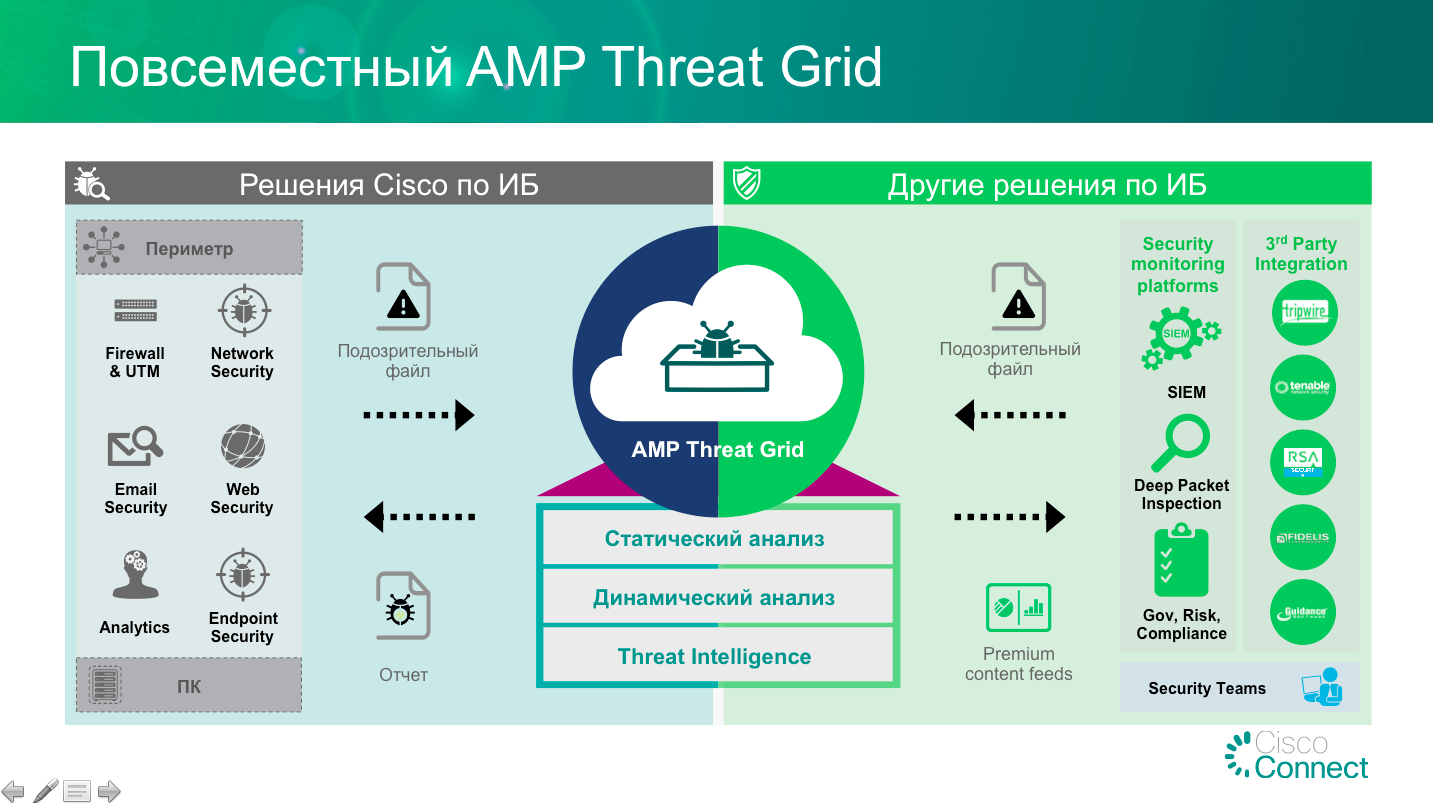
But for starters, I would like to show how it works on the example of the analysis of the TeslaCrypt coder, the result of which I showed in the picture above:
This platform extends the functionality of our malware detection solution - the Cisco Advanced Malware Protection (AMP) platform, which, being installed on firewalls, intrusion prevention systems, E-mail and Web protection systems, as well as on routers and end devices (PCs under Windows, Linux, Mac, Android), allows you to automatically detect known and unknown malicious code in automatic mode. For the study of the files that got into the organization not through the network or are suspicious, Cisco offers the Cisco AMP Threat Grid service , which allows analyzing any files for damage. Cisco AMP can transfer files to the Threat Grid service automatically, but you can also use it as a portal for analysts of incident response services, incident investigation services, information security monitoring centers. The video above shows just the work through the portal.
Please note - the analysis is carried out in just a few minutes and in fully automatic mode. You just need to download the file you are interested in and after some time get the generated report in a readable format. You can also get the report in JSON format to connect to your own systems and even get a PCAP file for additional analysis using any network incident investigation systems. For example, if you run this PCAP file through Wireshark or Cisco NGIPS, you can create signatures for intrusion detection systems that can detect the analyzed malicious code in the future.
In addition to Cisco solutions, you can also automatically upload data to the Threat Grid service using other solutions, some of which are also known in the former Soviet Union:
But the analysis of malicious code can be carried out not only in the AMP Threat Grid cloud. For specific applications (weak Internet, isolated network or other cases), it is possible to use a special Cisco AMP Threat Grid Appliance device, which is located on the customer's network and performs all the analysis of files uploaded to it.

The result of the Cisco AMP Threat Grid is a calculation of the threat rating (on a 100 point scale) with a detailed explanation of why a decision was made. About 450 different indicators in downloadable files are dynamically and statically analyzed - working with files, working with memory, working with the registry, working with the network, etc. For each parameter, the report contains a detailed description. Here's how, for example, a report looks like on the same TeslaCrypt coder. And this is how the report looks like a Zeus banking Trojan.
In modern conditions, when the malicious code is changing very actively and the established traditional means of detection are not able to recognize and block the threat in time, it remains to take the process in hand, expanding it by analyzing suspicious files using the Threat Intelligence Platform. And the Cisco AMP Threat Grid can help accomplish this.
Shl. Probably many have heard such an abbreviation - CIS, Center of Internet Security , which is known for issuing guides to the secure configuration of various platforms, devices, operating systems, etc. The CIS also created the MS-ISAC - Multi-State Information Sharing and Analysis Center. It also uses Cisco AMP Threat Grid to analyze malicious code, which is then promptly reported to various organizations connected to it.
So, we have antiviruses installed in our organization at workstations. On the mail server is also antivirus. Anti-Virus is even integrated via ICAP or WCCP with a firewall. Can we be sure that everything that falls into our network is pure as a tear of a baby? Alas ... As the statistics of various companies show, the average time of network hacking / compromise detection (time-to-detect, TTD) is 200 (!) Days. Imagine two hundred days you do not know that you have already attacked and pull out of you confidential information. And suddenly, at some point in time you see this picture on the screen of your computer.

In the dynamics, and we are talking about TeslaCrypt encryption, it all looks even more interesting (until 2:30, everything is boring and ordinary):
')
You damn your antivirus, which caught nothing and already hoping a little, start communicating with the antivirus company. What if they help and decrypt the hard drive. But alas ... the antivirus company is not able to help you. Its task is to sell and maintain the antivirus, and not to work for you for free, being engaged in the analysis of your suspicious files. Perhaps over time, antivirus analysts will parse the file you sent and equip your antivirus with knowledge of it. But it will be only later, but for now you are facing the dilemma of “ Pay or not pay extortionists? ” At the recently held in Kazan conference “Information Security Code” I conducted a blitz survey on the topic: “If you sent suspicious files to antivirus companies, then Did you get a positive and prompt response? ” Alas, I can not boast of the forest raised in response to this question.
Suppose you learned a lesson from what happened and the next time you receive a suspicious file you want to do something with it. But what? At the hearing of many service Virus Total , which is presented by many as a means of analyzing malicious code. But it is not so. VirusTotal is essentially an automation tool for scanning more than 50 antiviruses to detect malicious code uploaded to the portal (or not to detect). VirusTotal simply automates the process of launching fifty antiviruses and gives you a verdict - detected or not. If there is no information about your file in the anti-virus database, then VirusTotal will not tell you anything either. In other words, the task of VirusTotal is to check the effectiveness of antiviruses, but not to help you analyze your files.

You can try to refer to another free resource - Malwr , which is a sandbox in which you can analyze suspicious files for malware.

However, the number of analysis methods on this service is not so great and modern malicious code, especially designed specifically for circumventing sandboxes (and this is becoming more and more), may go unnoticed by Malwr. In addition to it, there are a number of other platforms for analyzing malicious code. At the forum held in Moscow on the IT Security and Response Center for the SOC Forum, I gave a separate report with a brief overview of such platforms. Among others, I mentioned our own platform - Cisco AMP Threat Grid , which I would like to talk about in more detail.

But for starters, I would like to show how it works on the example of the analysis of the TeslaCrypt coder, the result of which I showed in the picture above:
This platform extends the functionality of our malware detection solution - the Cisco Advanced Malware Protection (AMP) platform, which, being installed on firewalls, intrusion prevention systems, E-mail and Web protection systems, as well as on routers and end devices (PCs under Windows, Linux, Mac, Android), allows you to automatically detect known and unknown malicious code in automatic mode. For the study of the files that got into the organization not through the network or are suspicious, Cisco offers the Cisco AMP Threat Grid service , which allows analyzing any files for damage. Cisco AMP can transfer files to the Threat Grid service automatically, but you can also use it as a portal for analysts of incident response services, incident investigation services, information security monitoring centers. The video above shows just the work through the portal.
Please note - the analysis is carried out in just a few minutes and in fully automatic mode. You just need to download the file you are interested in and after some time get the generated report in a readable format. You can also get the report in JSON format to connect to your own systems and even get a PCAP file for additional analysis using any network incident investigation systems. For example, if you run this PCAP file through Wireshark or Cisco NGIPS, you can create signatures for intrusion detection systems that can detect the analyzed malicious code in the future.
In addition to Cisco solutions, you can also automatically upload data to the Threat Grid service using other solutions, some of which are also known in the former Soviet Union:
- General Dynamics Fidelis
- Guidance Software EnCase Cybersecurity
- RSA Security Analytics
- TripWire Enterprise 360
- Splunk Enterprise
- Malformity Labs Maltego
- IBM QRadar
- HP ArcSight
- Mcafee nitro
But the analysis of malicious code can be carried out not only in the AMP Threat Grid cloud. For specific applications (weak Internet, isolated network or other cases), it is possible to use a special Cisco AMP Threat Grid Appliance device, which is located on the customer's network and performs all the analysis of files uploaded to it.

The result of the Cisco AMP Threat Grid is a calculation of the threat rating (on a 100 point scale) with a detailed explanation of why a decision was made. About 450 different indicators in downloadable files are dynamically and statically analyzed - working with files, working with memory, working with the registry, working with the network, etc. For each parameter, the report contains a detailed description. Here's how, for example, a report looks like on the same TeslaCrypt coder. And this is how the report looks like a Zeus banking Trojan.
In modern conditions, when the malicious code is changing very actively and the established traditional means of detection are not able to recognize and block the threat in time, it remains to take the process in hand, expanding it by analyzing suspicious files using the Threat Intelligence Platform. And the Cisco AMP Threat Grid can help accomplish this.
Shl. Probably many have heard such an abbreviation - CIS, Center of Internet Security , which is known for issuing guides to the secure configuration of various platforms, devices, operating systems, etc. The CIS also created the MS-ISAC - Multi-State Information Sharing and Analysis Center. It also uses Cisco AMP Threat Grid to analyze malicious code, which is then promptly reported to various organizations connected to it.
Source: https://habr.com/ru/post/271191/
All Articles