Phishing Email Examples

I did not accidentally put a picture of a cat in the title of the post. This is one example of the manipulation of human consciousness, an appeal to pity. Methods of exposure to intruders using such techniques are in the field of practical psychology and are related to social engineering. Playing on the emotions, feelings, fears and reflexes of people, attackers gain access to the information of interest. All these methods are used by hackers when creating phishing emails.
Attention, under the cut a lot of images.
Unfortunately, the level of awareness of users about modern threats is quite low, so, as promised, I will try to describe the main techniques.
')
When attacking email users from intruders, there are now two main goals: find out the user's password or try to get a download file. In order to collect the main vectors on the first occasion - I created a box and “ordered” it to be hacked at several sites, which I found quite easily with the help of search engines.
I will not consider the presented phishing domains and email addresses: an ordinary user will not remember how google.com/index.php differs from google.com.indexphp.cc. The main thing that I want to convey - do not blindly follow any instructions in the mail, especially those that encourage you to perform certain actions here and now, otherwise something bad will happen.
Gmail - documents
The letter was sent from the gmail address and reports on some documents. In business correspondence, especially with a large flow of letters, it is easy to click on a document once on the phishing page:
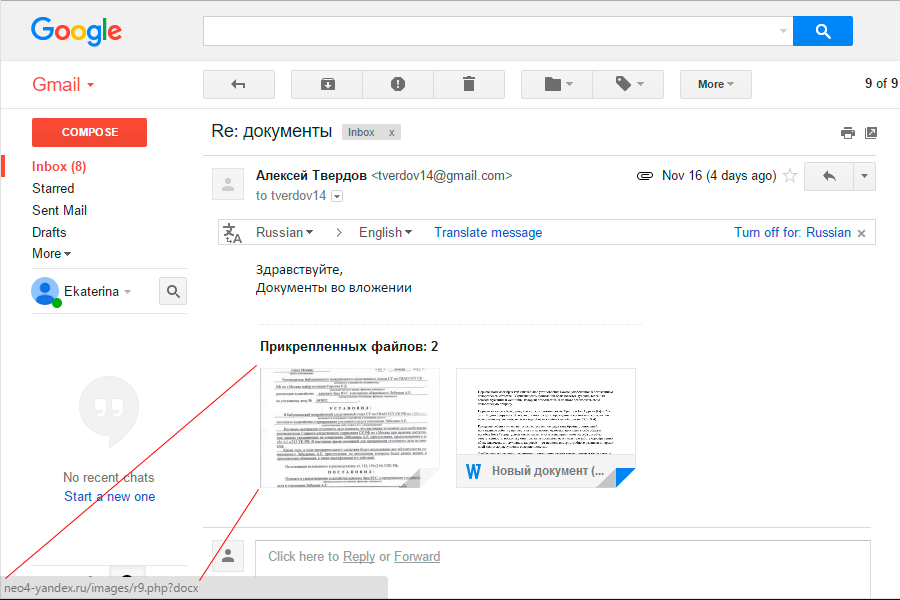
Although the address of the “documents” leads to neo4-yandex.ru, nevertheless, a redirect occurs to this domain from:
(a sniffer is installed in the page code, which logs all visits to the page -

s-mail-google.com/myaccount/ru/index.php?id=&/id=20154748705121097
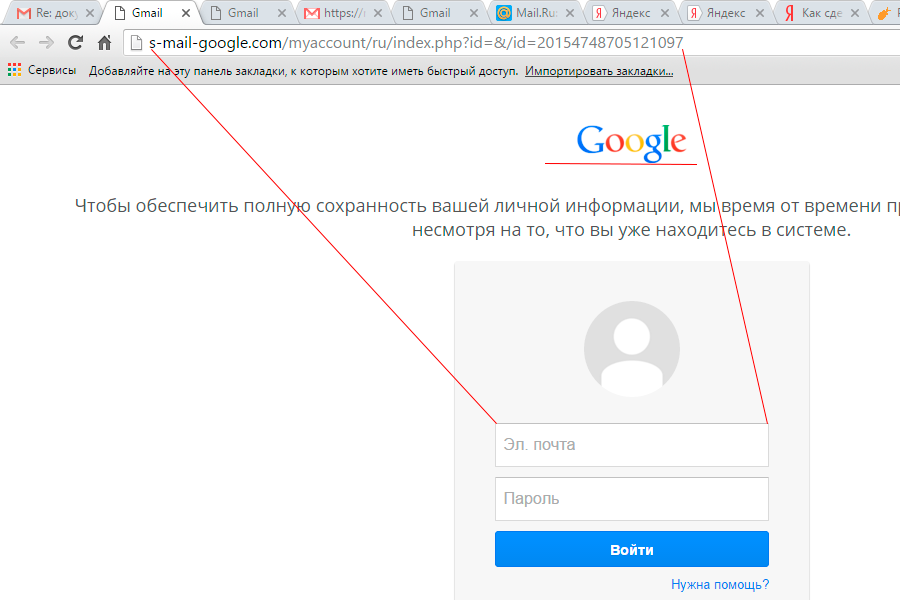
Notice the old Google logo on the phishing page - have many of you mentioned that it is old? Do many users remember or know that Google already has a new logo? Most likely, the form was made using the Social-Engineer Toolkit , this logo is not updated in it. Or maybe the attackers simply do not pay any attention to it and do not update their crafts.
Gmail - undeliverable message
A letter arrives, stating that some letters were not delivered. And if something important is lost?
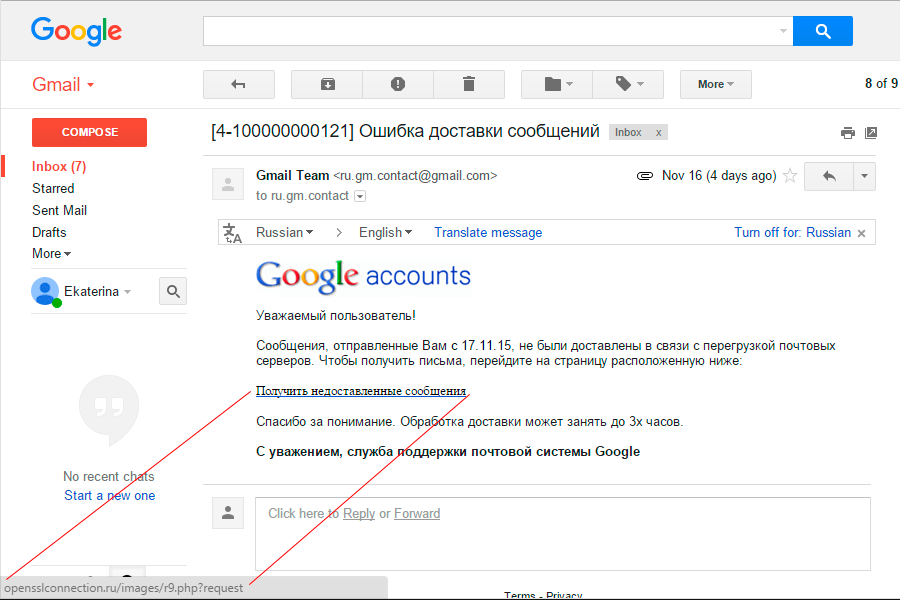
Many people are by nature suspicious, so click on the link, and there is already a known redirect to: s-mail-google.com/myaccount/ru/index.php?id=&/id=20154748705121097
Gmail - urgently change your password
User, some bad personality hacked your password!

Ordinary users are likely to go to change their password, only the address for the change is completely inappropriate: google.mail.com.ru-id322322.ru/548589203339099000020039939/o/p/l/?id376=YWtzZWthdHlhQGdtYWlsLmNvbXxha3Nla2
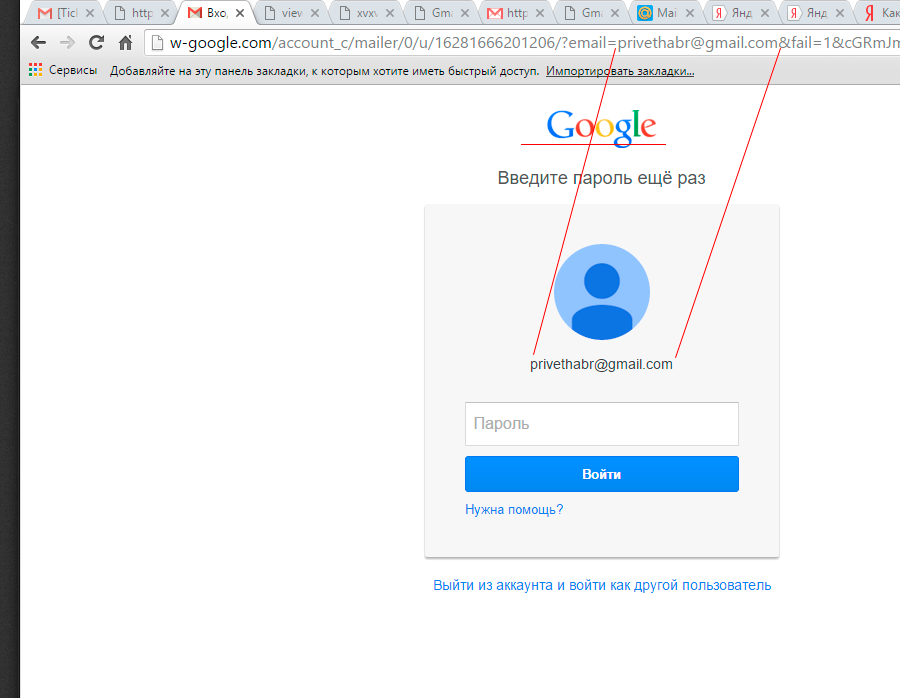
Gmail - your mail will be blocked
You did something wrong (after all, ordinary users "do not understand computers"), now you need to fix everything, otherwise delete the box:
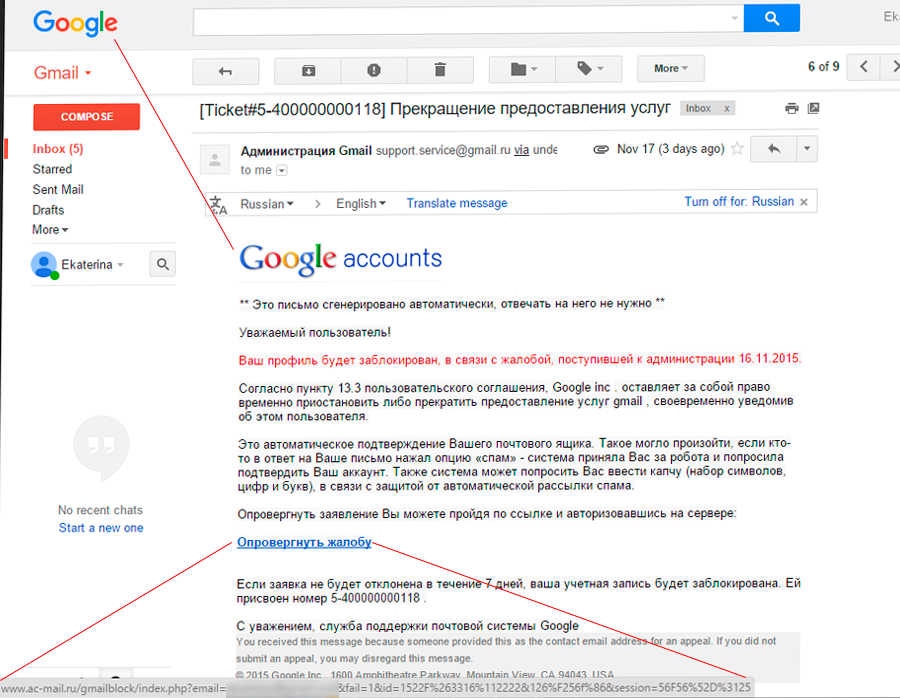
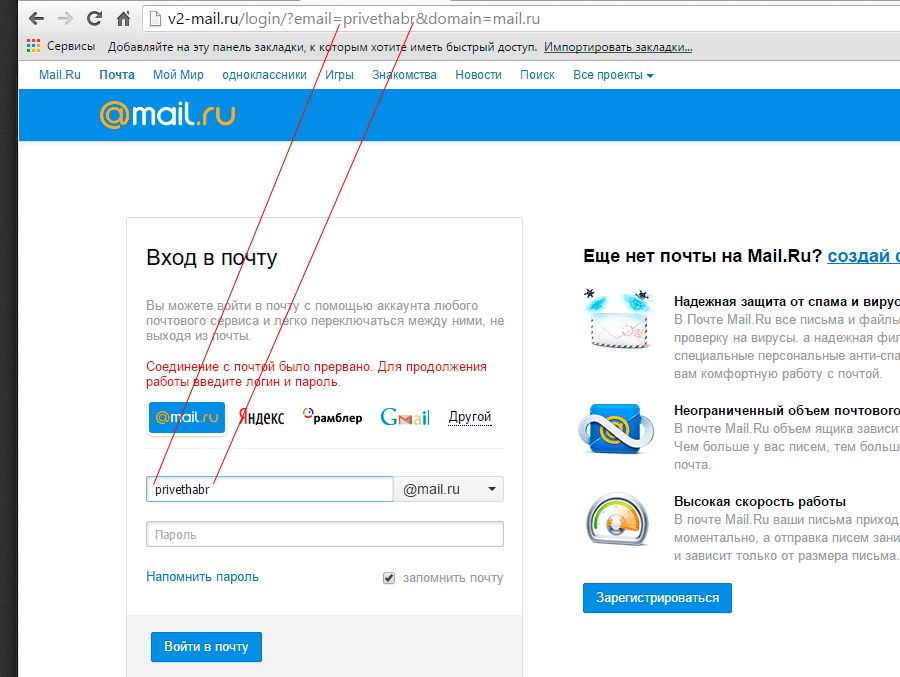
What we have here? Again, the old logo, but there is something new - the URL of the attacked mailbox is sent to the URL, for greater accuracy. A user clicks on the link of the form: w-google.com/account_c/mailer/0/u/16281666201206/?email=privethabr@gmail.com&fail=1&cGRmJmhsPV3N0BJmhsPXJnbWFpbC5j1VyJmFjdb20mbGV0EVyucGRmJmhsPVyPXZ5cGlza2EucGRdVyGmJmhsPXJ1JmFjdD1%27 and falls on "personal page":
Gmail spam
You sent spam, now you can not send emails. Account verification required:
Again the old logo. The vector seems to be new, but leads again to the page we already know: s-mail-google.com/u/0/accounts/index.php?id=&/id=d7115e86e7423e7aea202cebf544de21
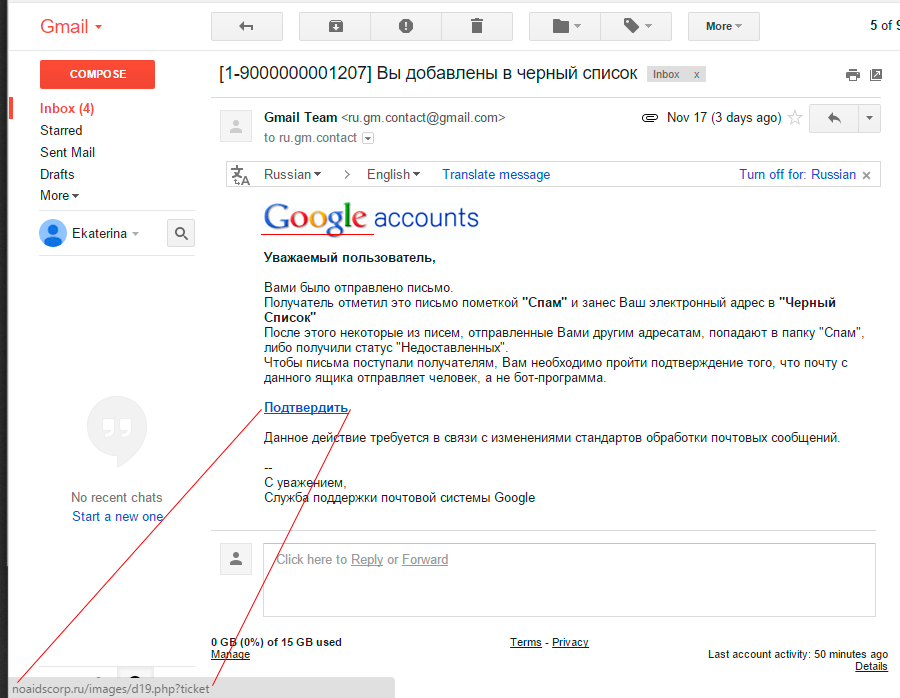
Gmail blacklist
You have been added to the blacklist, the jokes are over. Urgently confirm that you are not a bot program:

The link is already known address: google.mail.com.ru-id322322.ru/?login=YWtzZWthdHlhfGFrc2VrYXR5YUBnbWFpbC5jb20=
Gmail - time to increase volume
The mailbox is almost full, you need to increase its volume. It is necessary, it is necessary:
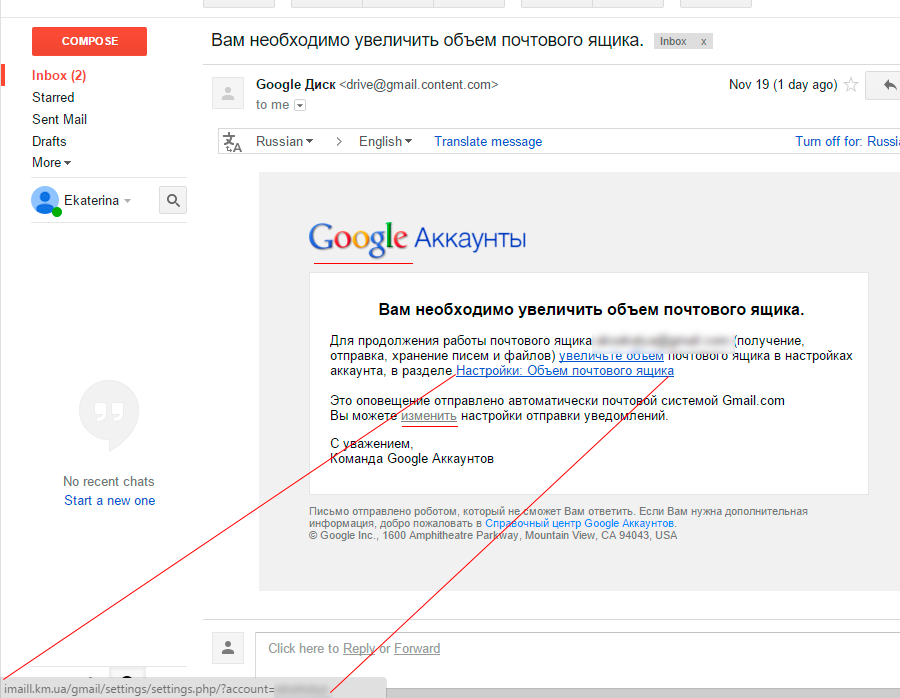
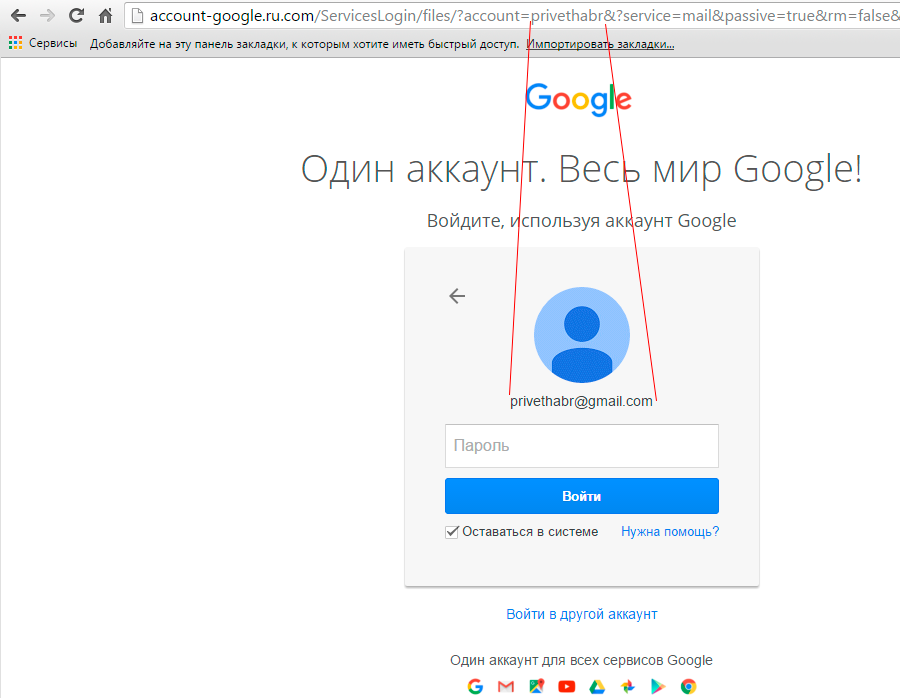
I liked this letter. I expected the standard login form, but no, the attackers went the other way. Such attention to detail: the victim's login is specified, the “change” link is inactive, but the most interesting thing is further: account-google.com.com/ServicesLogin/settings/?account=privethabr&?service=mail&passive=true&rm=false&continue=https : // mail .google.com / mail /
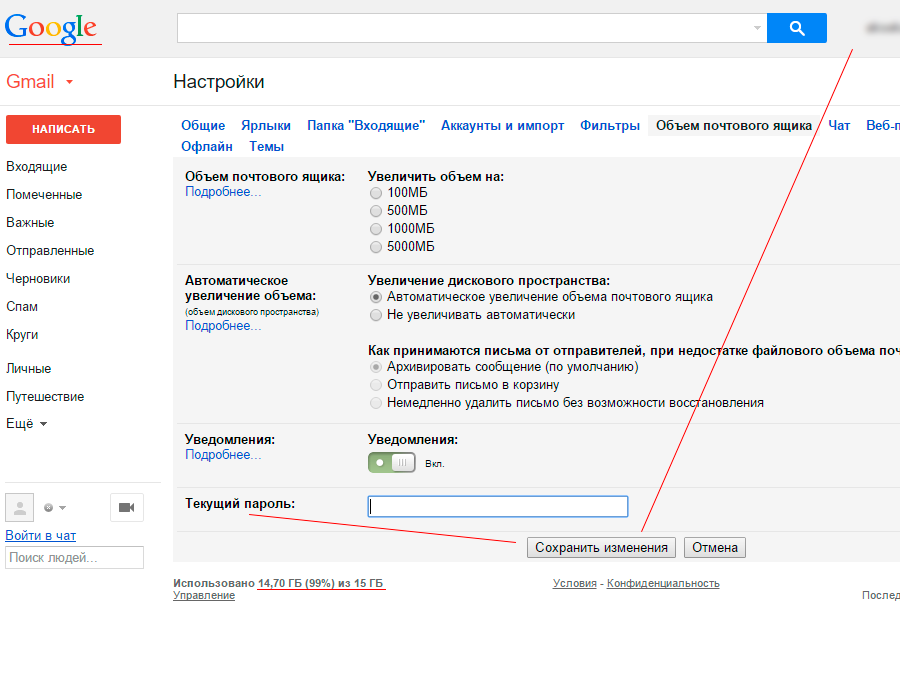
The login of the victim is indicated, the interface is clearly google, it is even clear that the place is really over. And the domain is chosen very much in the subject. But the logo is old again. In general, this is still the clear favorite phishing engineering.
Gmail - working moments
The method is doubtful for ordinary users, a letter with some kind of application or requisites:
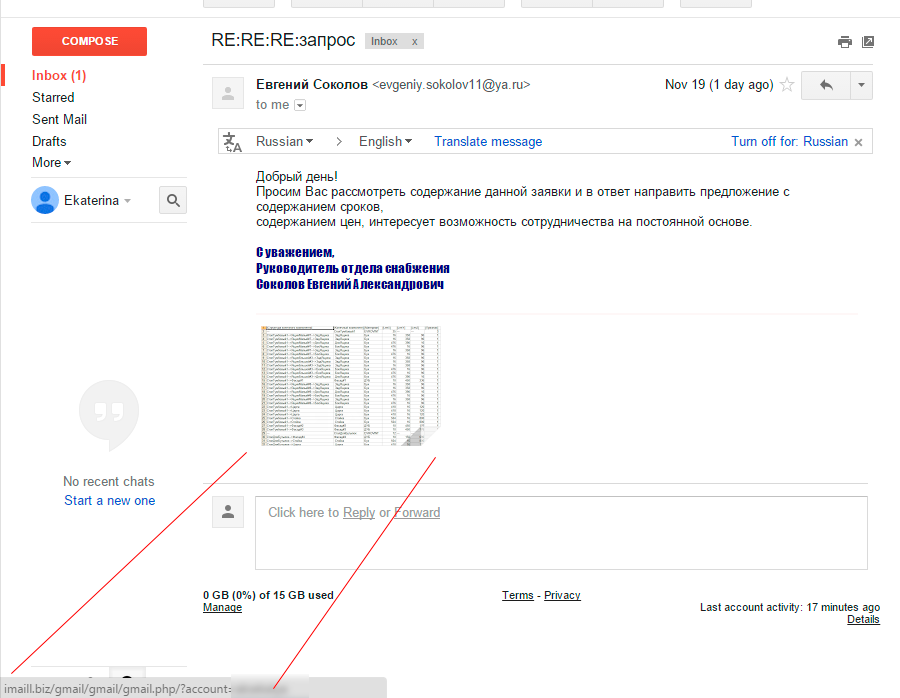
Redirect link to the domain account-google.com.com/ServicesLogin/files/?account=privethabr&?service=mail&passive=true&rm=false&continue=https : //mail.google.com/mail/&ss=1&scc=1<mpl=default<mplc = 1
The first form, on which stands a new logo.
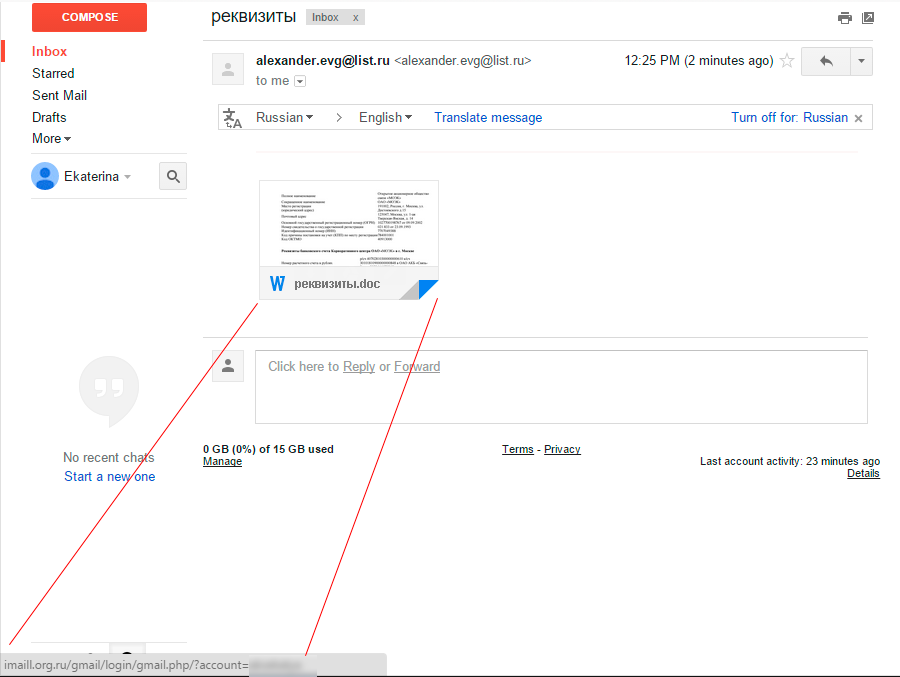
Mail.ru - working moments
It looks like the method mentioned above, they sent some documents, there can be quite a few variations:
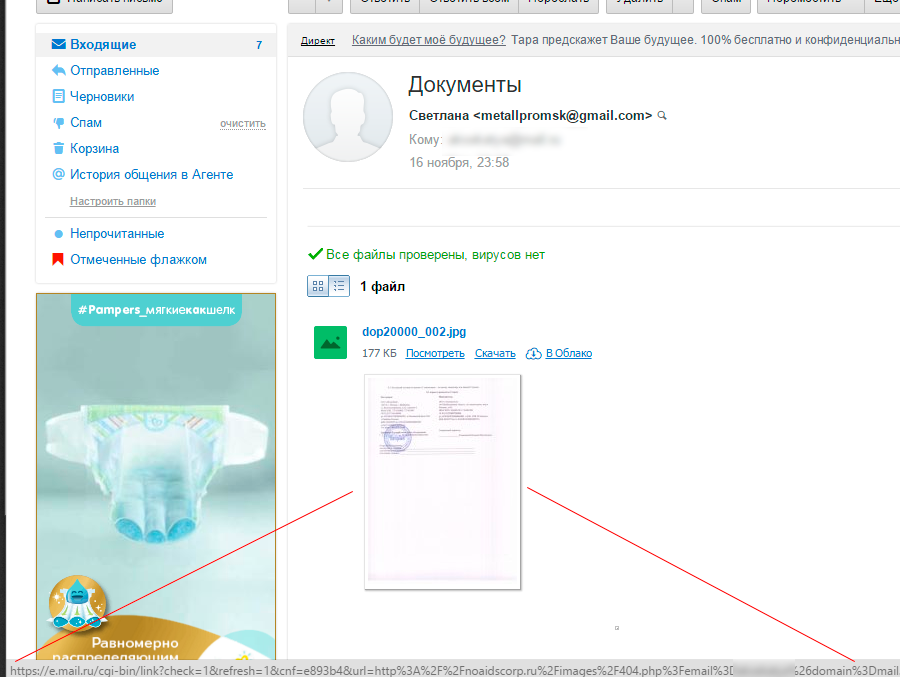

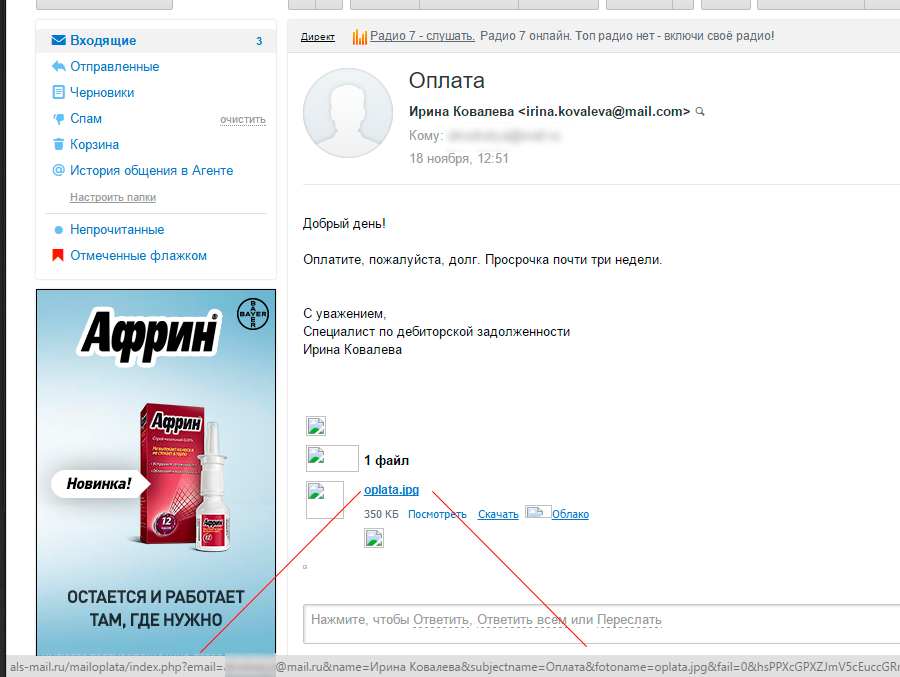
Click on the link and the user is prompted to enter a password. Since the login has already been substituted - the majority of ordinary users will enter their password “on the machine”:
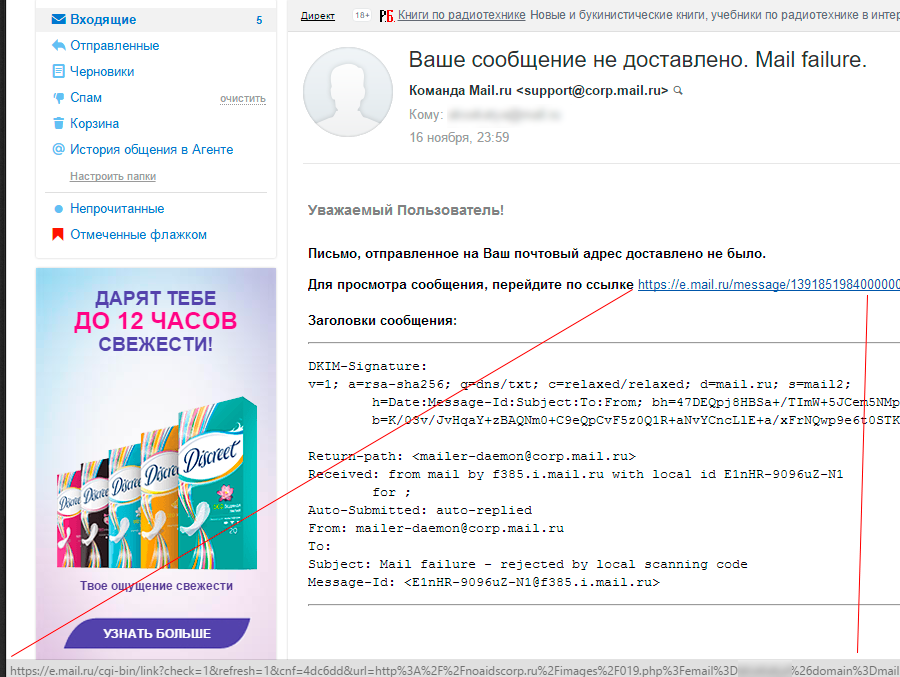
Mail.ru - the message was not delivered
You did not receive an important letter, but our service notified you about it, including some incomprehensible message headers for greater accuracy:
And there is already a familiar form:

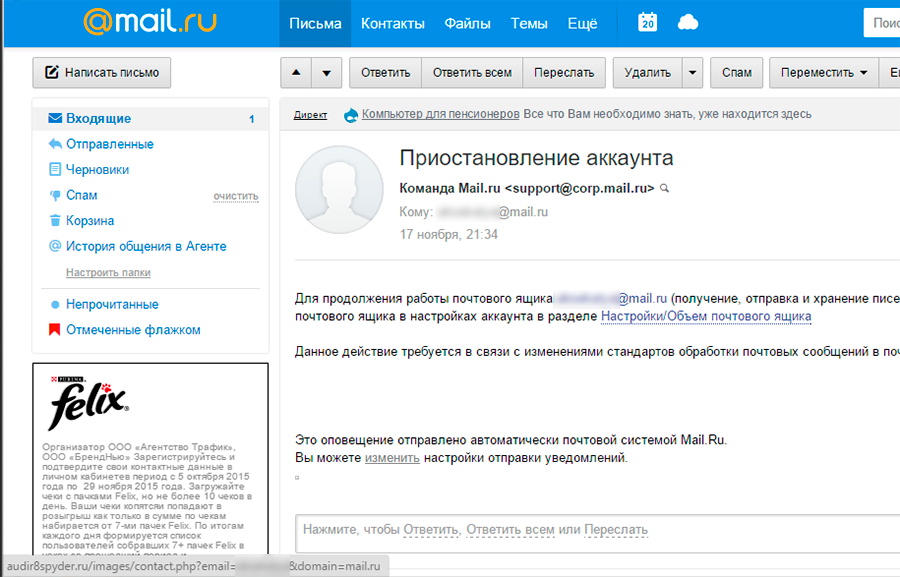
Mail.ru - increase the volume of the box
Another leader of my credibility hit parade:

In the transition we get to the form of increasing the volume of the box:
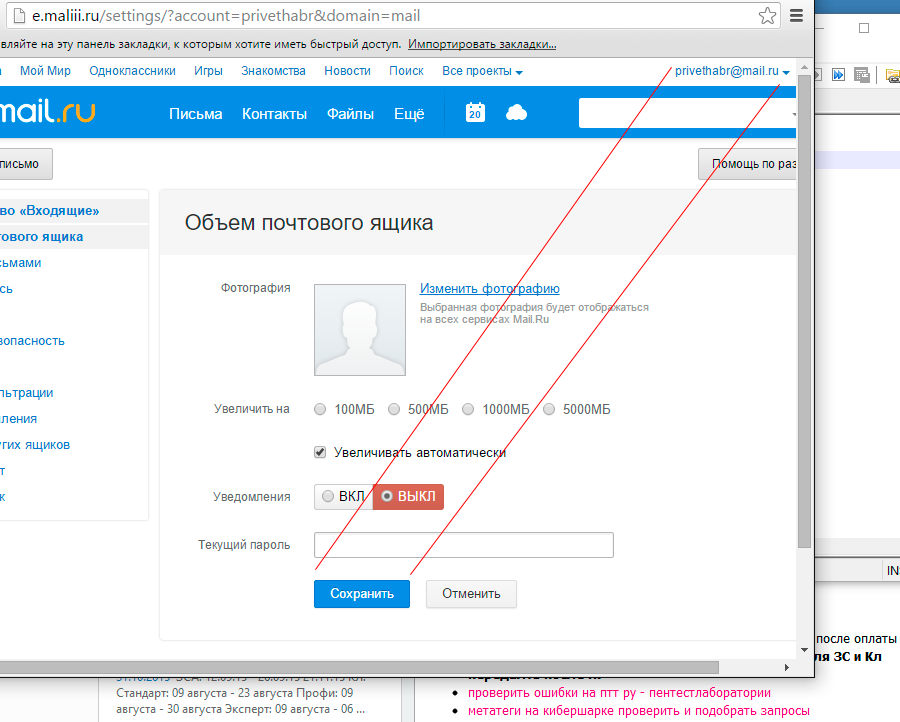
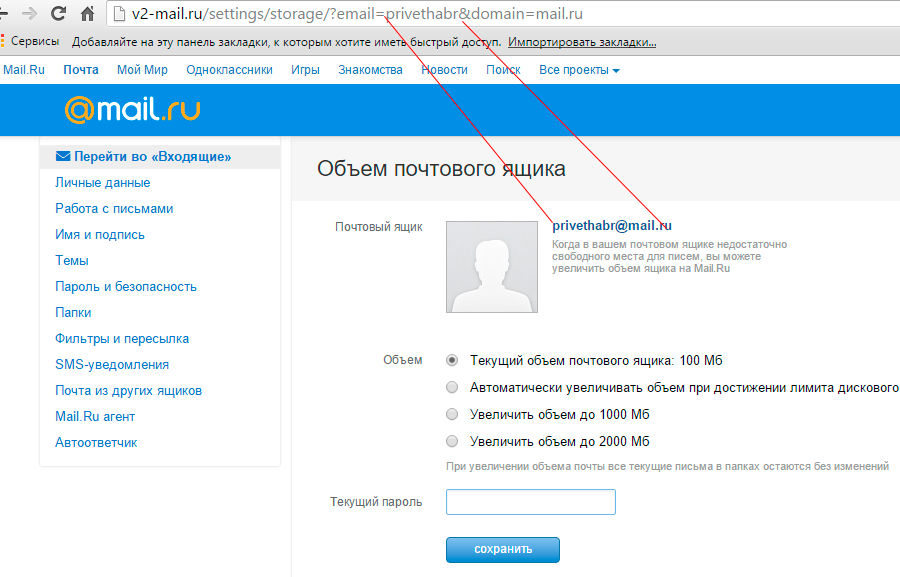
Another type of such letter:
Under the link we see the form:
It looks like the method above, but the phishing domain is no longer working:

Link to: cew-
Mail.ru - security notification
Someone hacked your mail, urgently run to change the password:
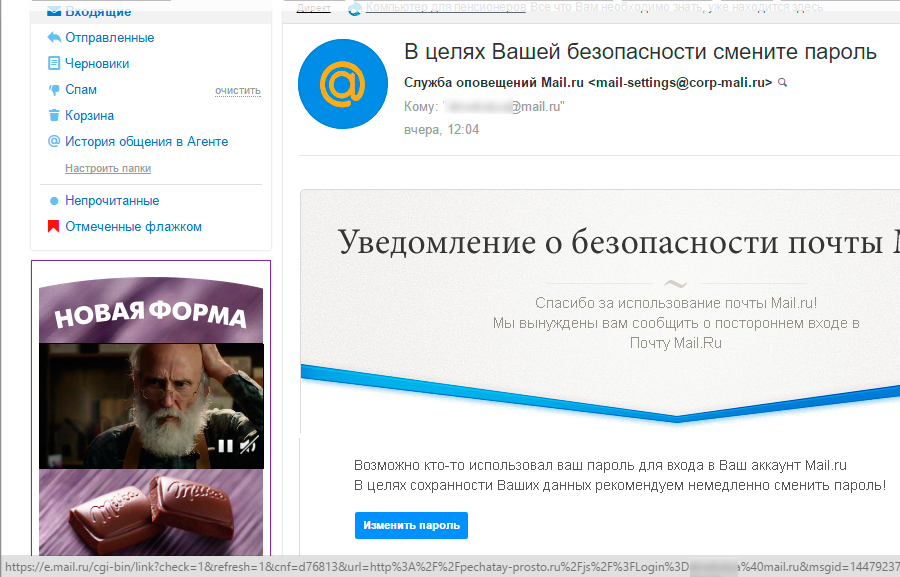
Phishing link redirect on pechatay-prosto.ru/js/?Login=privethabr@mail.ru (no longer works).
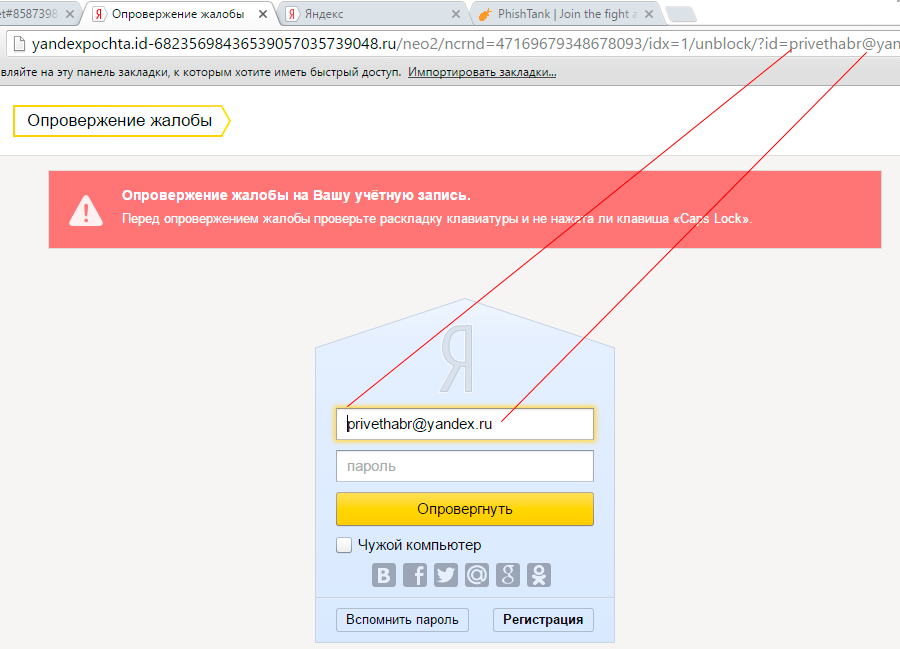
Yandex - security notice
Do not confirm the account - block the mail:

Under the link the form, with already substituted account name:
Yandex - mailbox reactivation
Again, you must perform some actions:

Added a lot of "believable" details:

Distribution of malicious files / cryptographs
Using the current economic situation and the fears of people, the attackers send out letters imitating notifications from payment systems and judicial or executive authorities:
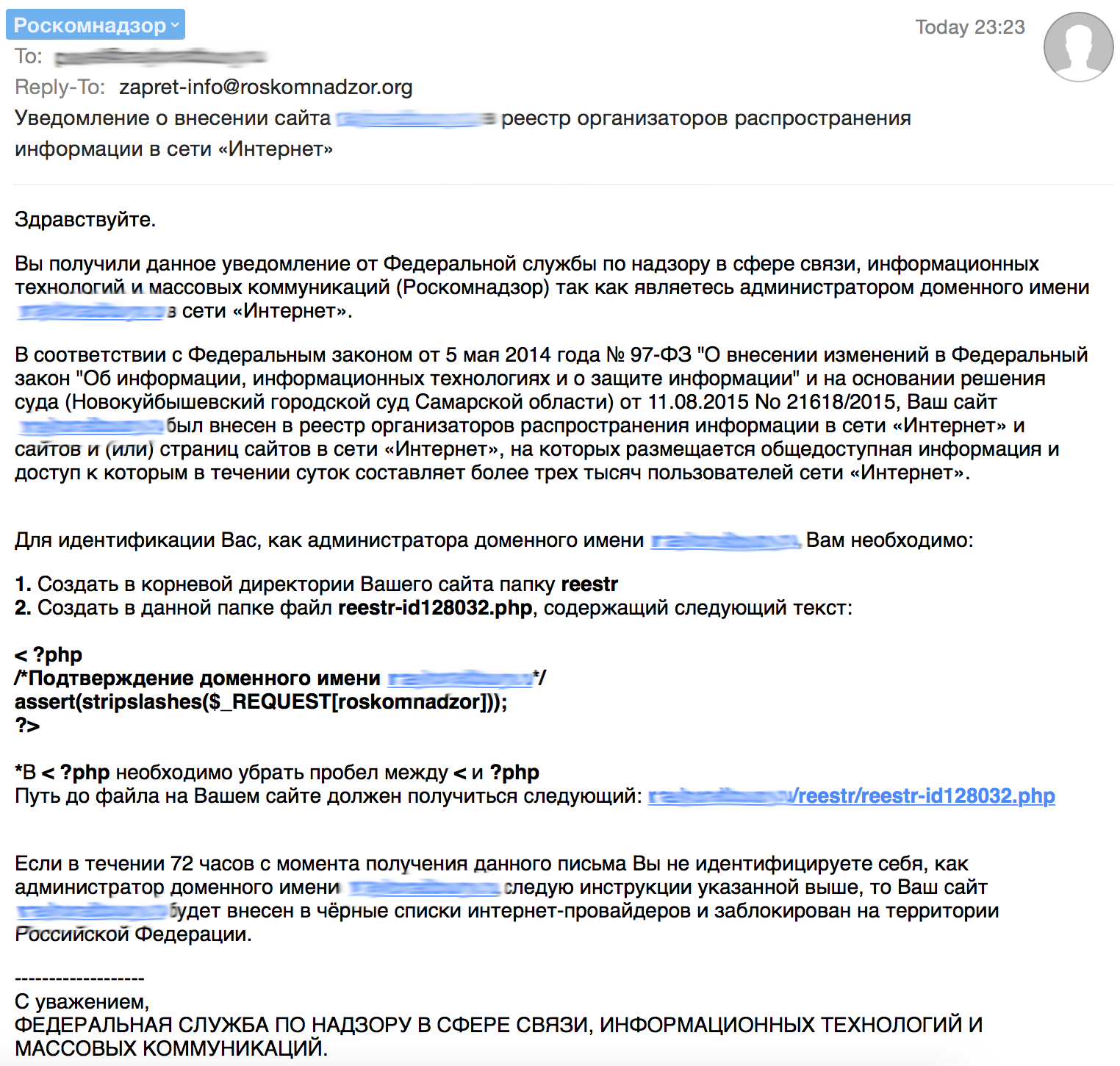
A letter containing instructions for "confirming" a domain name from Roskomnadzor (in fact, the user will install a shell on his site):
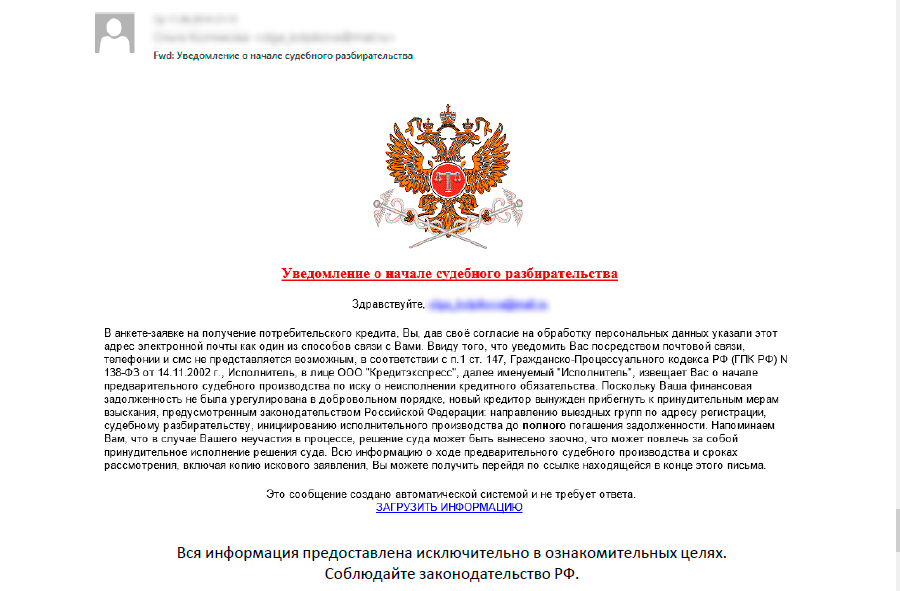
A letter from the arbitration court, containing a link to the crypto-fiber:
Letter from Sberbank on a loan issued (with reference to the crypto-glass):

Safety regulations
- A letter prompting you to take some immediate action should alert you: check who it came from, the domain and the link. If in doubt, ask the experts.
- If something is imposed on you or sent to something you do not have a relationship with, it is better to delete this letter.
- Do not follow suspicious links in the letter, even if they came in messages from your friends or from some official addresses.
- Letters from courts of law or organs: do not be lazy, find the telephone of this department and call. Just because no court decisions or notifications of overdue loans does not send. And in 99% of cases you will receive a notification by regular mail.
- Use two-factor authentication: most email services currently support this technology.
Source: https://habr.com/ru/post/271123/
All Articles