Overview of Cisco UCS Initial Setup

It is generally accepted that Cisco UCS server solutions are very difficult. We decided to visually show the ease of setting up such solutions. Under the cut video review, as well as a transcript with screenshots (Caution, traffic! Many full-size screenshots, if you squeeze them - do not make out anything) .
Disclaimer: of course, the entire configuration process of the Cisco Blade takes about 2 hours, we noted the key and main points. And imagine all this live record? - it will not be interesting to anyone.
The video review itself
')
Transcript (with small editing)
Today we look at the basic configuration of the Cisco blade system. For several years, these systems have been disturbing the market. First, let's see how the boxes and the basic kit look.

A small educational program on the blade system from Cisco.
Firstly, these are 2 universal switches that can transmit traffic and Ethernet and FibreChannel, they are based on Cisco Nexus.
The second component is the blade chassis itself and the servers that are installed in this chassis. The peculiarity of the system is that we will need a maximum of two universal Fabric Interconnect switches (hereinafter referred to as FI), for almost any number of servers that we have in the data center.

For example, we need 1, 2, 10, 20 chassis, all the same, we will only need two of the above switches. This is a huge savings for large enterprises.
What is the feature? If we suddenly need two Ethernet ports for each server, 4, 10, 100 Ethernet ports that are responsible for each server, or FibreChannel doesn’t matter how many, we still need only two such FI switches. This is done thanks to Cisco technology, which allows you to see from the management console any number of interfaces that we will create on each server.
They are created virtually, but for the software environment they are seen as hardware components. Similarly for switches.
Now program tincture
We connect already familiar to many console cable.

We will connect it to each switch for configuration.
Further configuration is via the web interface.
It is worth paying attention to the back side of the blade chassis. You can see here a special FI expansion module called the Fabric Extender.

In order for the chassis to connect to FI, an extender is used — it simply expands the switch with an additional number of ports from the blade servers. Now in our configuration, each switch is connected to an extender using four 10 Gigabit connections.

If necessary, we can dynamically reduce / increase the number of connections - to change the connection speed to the chassis. For reservation, a second extender is used.
First we ask how we want to configure it: through the console, new / old setting, password, etc.

We try to enter a simple password "password", and I am asked to enter a more complex option.
Next comes the survey from the system: will there be a second FI switch? Next, we assign which of them is the first, and who is the second. Then - the name of the system. We give IP-addresses, for the sake of which we connected to them with the console. Address of the first switch: 192.168.0.11, gateway: 192.168.0.1
Now the interesting thing is, the virtual address 192.168.0.1, which will move between the switches in the event that one of them fails. DNS will not configure yet.
Then we are asked: "Do we like everything in the configuration?", We say - yes, and the configuration is applied. Configuration from the console is complete.
Now set up the second FI factories.
We will configure from the console. Found another FI, question - download configuration from it? Download Then we set the IP address of the second FI.
We select application of a configuration. Configuration from the console is complete. All further configuration will be done by the graphical interface. The only thing for which the console is needed is to configure IP addresses.

Enter the IP address that we configured from the console into the browser. Java console starts.

Enter the username and password that we asked from the console. And here we see a graphical interface for managing our entire system. Now we see two fi. They are united in a cluster. Servers we do not see.

Let's deal with the management interface.
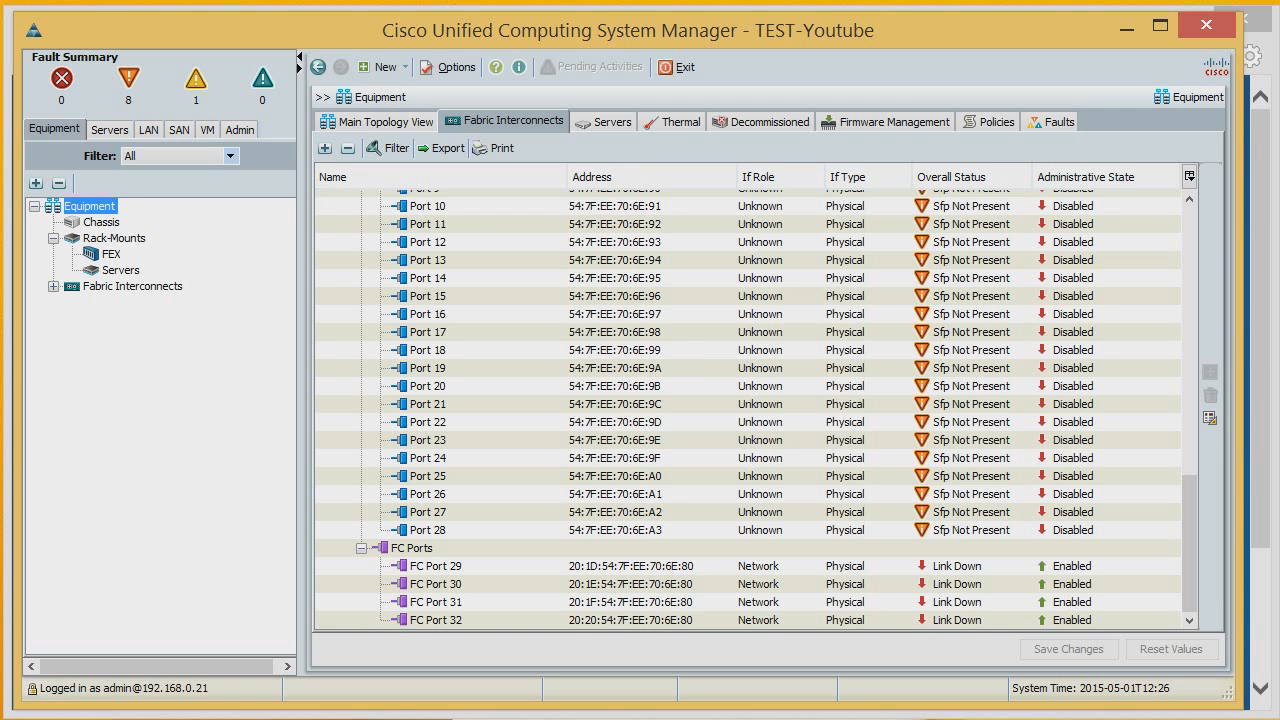
We can see which ports are on which FI interfaces - which of them are now FC, which Ethernet.
Information on heat generation - here you can see if everything is normal with the cooling system, power supply units.

And now the firmware control menu. From here, we can centrally update or downgrade firmware to various components.
Here the firmware is downloaded and immediately applied.

You can download the new firmware from the local system or via FTP, SFTP.

Now the policy menu. The first policy is 10 gigabit links. Whether to connect them to the Port Channel or not. Set to connect. From here you can specify the redundancy of power supplies and some other parameters.

Now we will make our servers visible. To do this, those ports on the switches that go to the blade chassis must be assigned a special server type.

Here are the first four ports, they are connected to the blade chassis.

Open the port and assign it to the server.

Thus we activate all ports.
Since we have assigned in the policies that all the ports that go to the blade chassis will be assembled on the Port Channel, we get two 40-gigabit links. One will go from one switch, another from the second.
Now configure the second FI. Ports leading to the chassis can be anywhere - at the beginning, in the middle or at the end, as we assign them, so it will be.
Let's see what was discovered through the activated ports.
There are two servers. We can see what serial numbers they have, on the adapters that are inserted in them, on the CIMC version (analogue of Cisco iLo). You can also view information on the processors in the servers.

You can see the memory, RAID-controllers, locally installed drives.

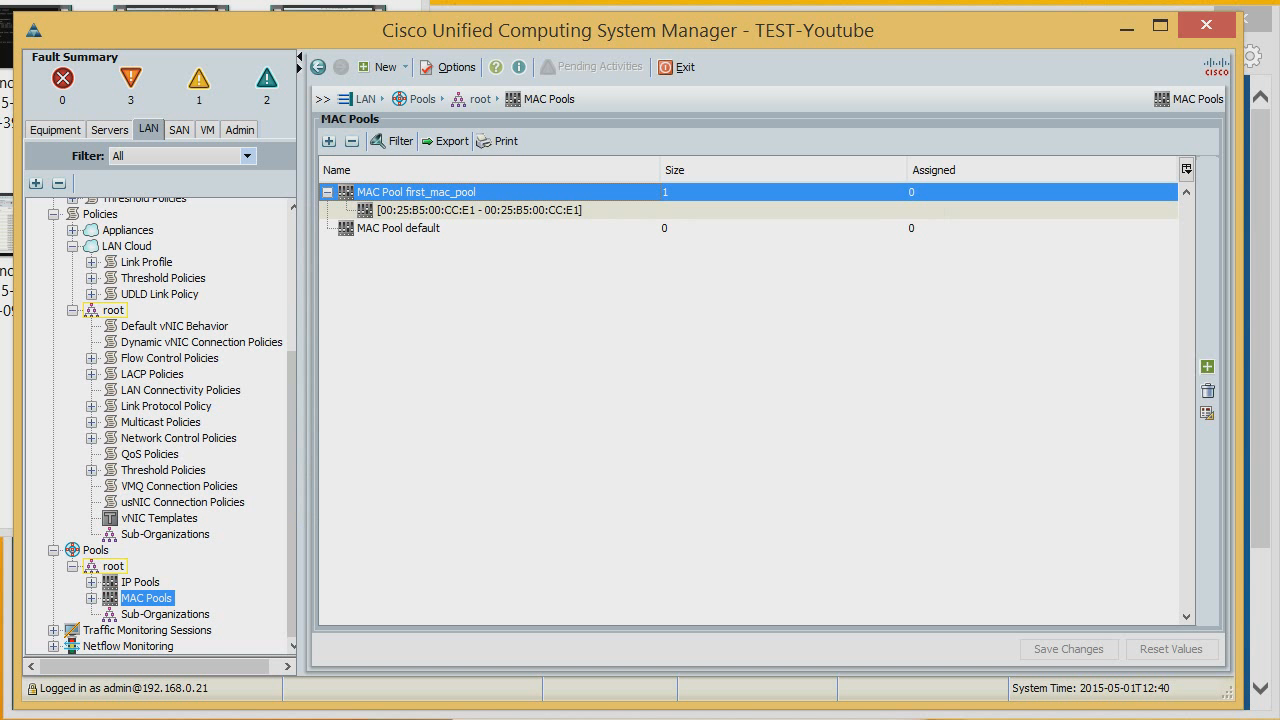
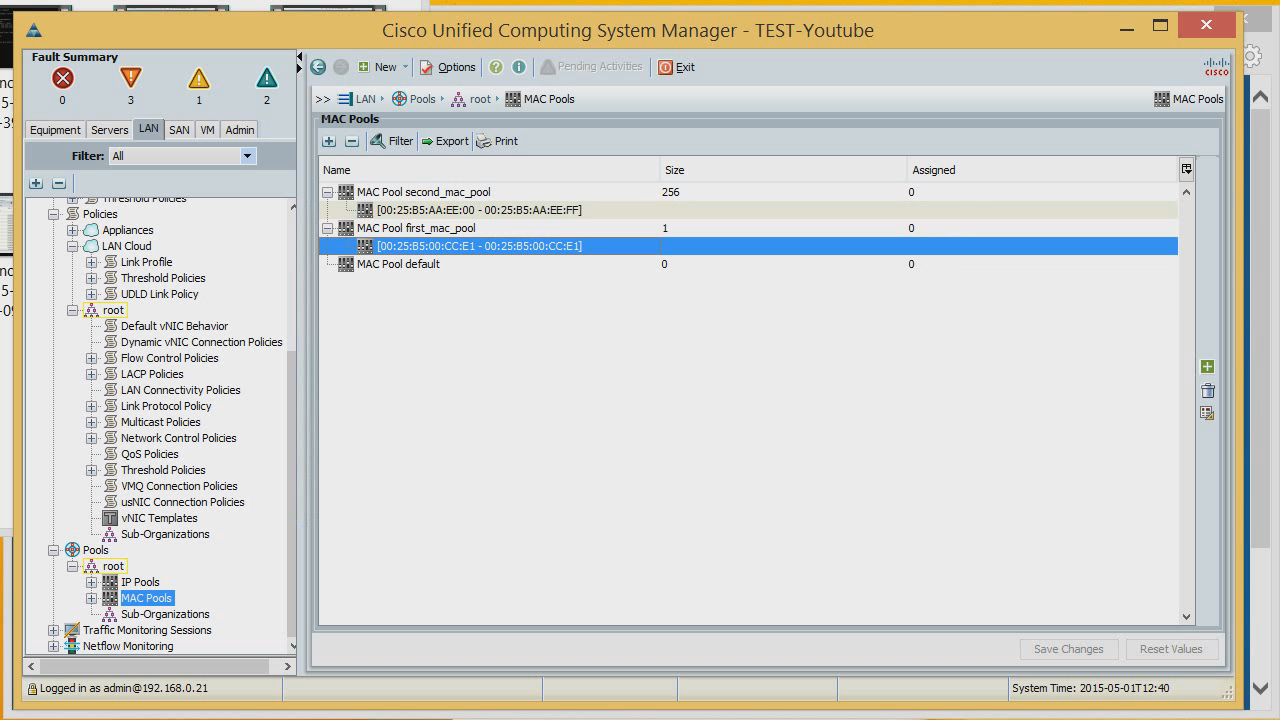
Now let's get down to setting it up. The first thing we do is create MAC addresses for our servers. What is it for? We can reflash absolutely all server hardware settings. We create the first pool of MAC addresses, and give the MAC system that we already had and on which security was configured. Exactly one MAC address.

If you already had some kind of configured system, we can create a new server with such MAC addresses, and you will not need to reconfigure the network.
Create another pool where you can create many MAC addresses - say, 256.
The pool of MAC addresses that we will assign to servers is ready.
Next, create the IP addresses that will be used to manage the servers. We already have a pre-prepared list of external management.
Let's add here a block of IP addresses that will manage the servers. There will be ten of them in the block. Assign the Default Gateway.

To show that we can have more addresses besides the first pool, we will create another pool.

Now we have a list of MAC addresses and IP addresses that we will give to servers. The next thing that may be required is setting up one-sided adapters, that is, Host Bus adapters. Let's create WWNN-us. We already have a ready list, let's create another one. We come up with a random value, for example 256.
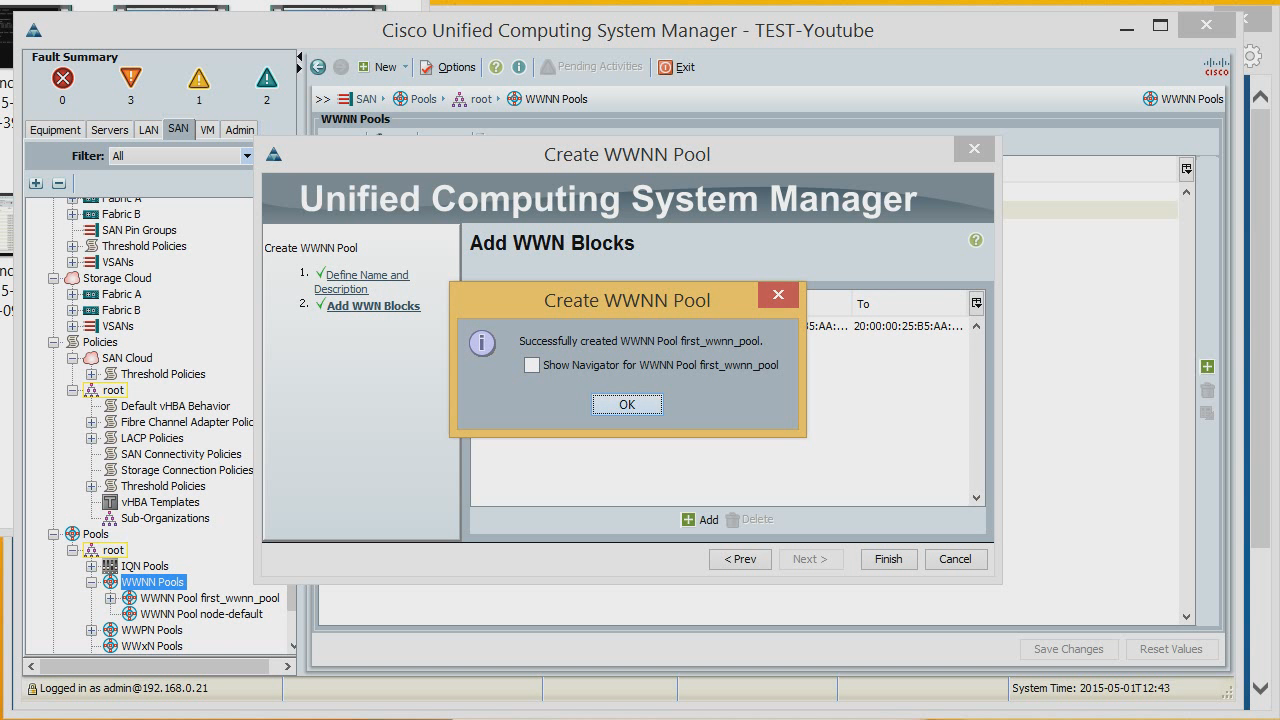
Now a list of tails.


We have all the basic settings. What do we still lack? There is not enough server serial number or its UID. They are assigned in the server section.
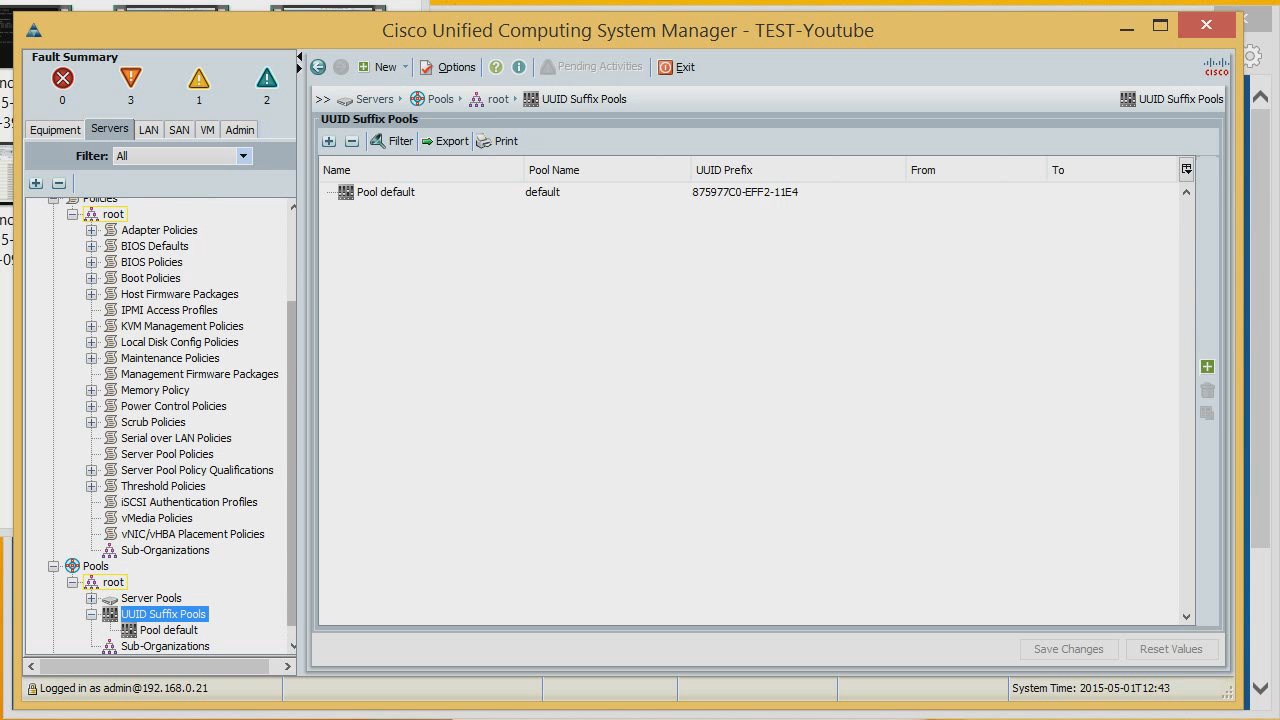
By default, the UID is flashed to the server at the factory by the manufacturer, and cannot be changed later. And in our case, you can. You can make both one UID and a pool, which will be assigned to our servers in turn.

Now we create the server itself. Select the expert mode. We give the server, or profile, which will be applied to the server, the name. A profile is what the server itself will look like. Choose from the list of UID, which has already been created. Click Next.

Then you can choose dynamic network adapters. These are adapters that are used in VMware and can be dynamically added or removed. And now we create not dynamic, but static IP addresses. Also, there is an MTU setting for this adapter and some tuning for a specific operating system. Suppose we have VMware.


Let's create another couple of adapters in the systems - let there be four.

Now setting up the storage system. By default, we do not have any disks here, so we will create a special policy that will display so that the server does not use any disks at all. We can choose in which RAID to collect disks on the server, or indicate that there are none at all. There are no SD cards either, so we set everything to Disable. And we select the application of the newly created policy to this profile.

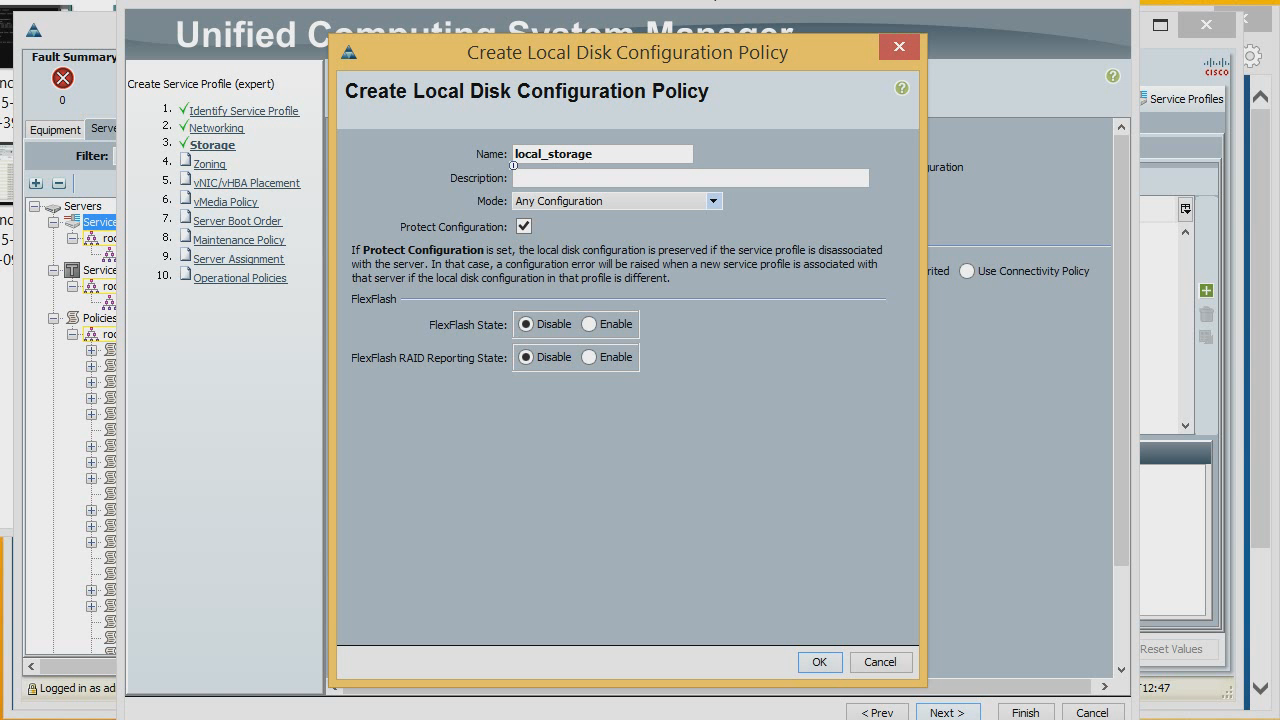
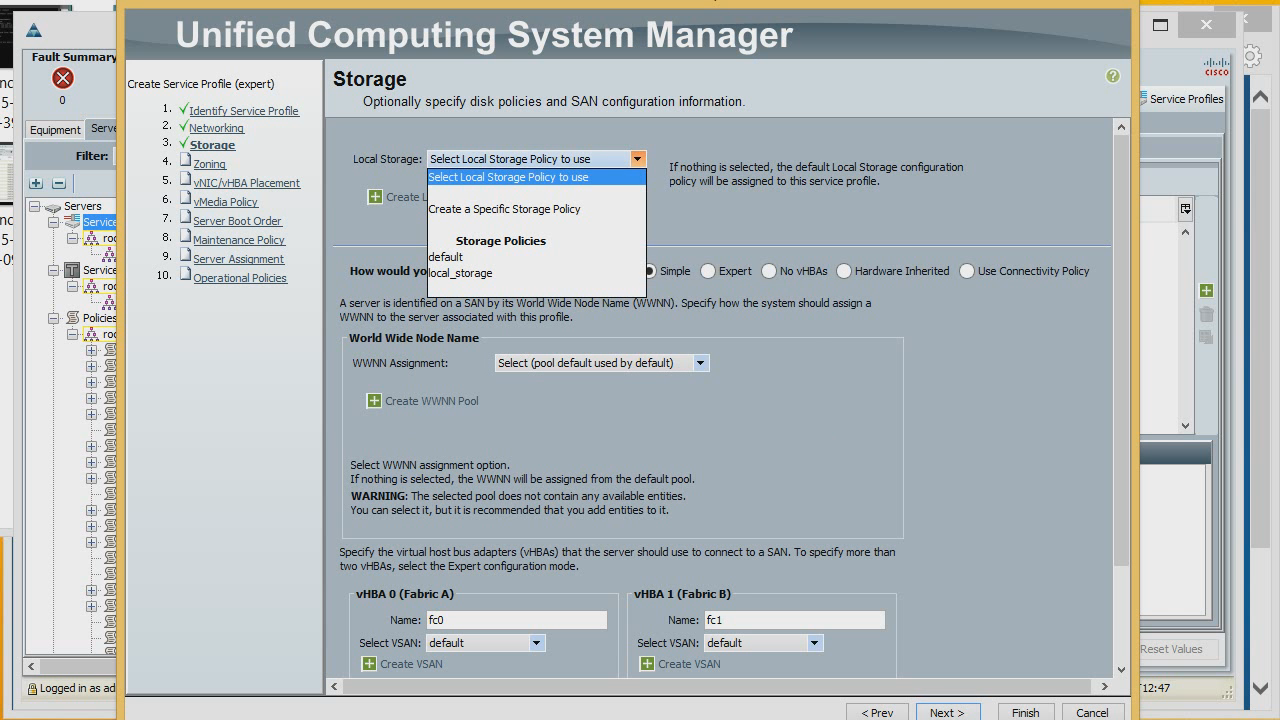
Now let's create Host Bus adapters in expert mode. WWNN take from the list we created. We give the adapter the name and porter from the list of portnames. It will be connected to FI A. We can connect it to a specific vSAN, and assign optimization to a specific policy.

In the same way create another adapter. Next, we can configure zoning, but as long as we don’t have a connection to the storage system, we’ll skip this step. It can be done later.
Configure the queue for the appearance of adapters in the system and what interruption they will take

Now - setting the server load, where the OS will boot from. By default, there are several boot policies, but let's create our own. To do this, select Create a Specific Boot Policy. First, we will set the default boot from the CD / DVD connected via CIMC, add the name, boot from the zero adapter (fc0). If we click Add SAN Boot Target, we can specify additional boot settings. We now have two adapters, in the future it will be possible to add which specific target to load.
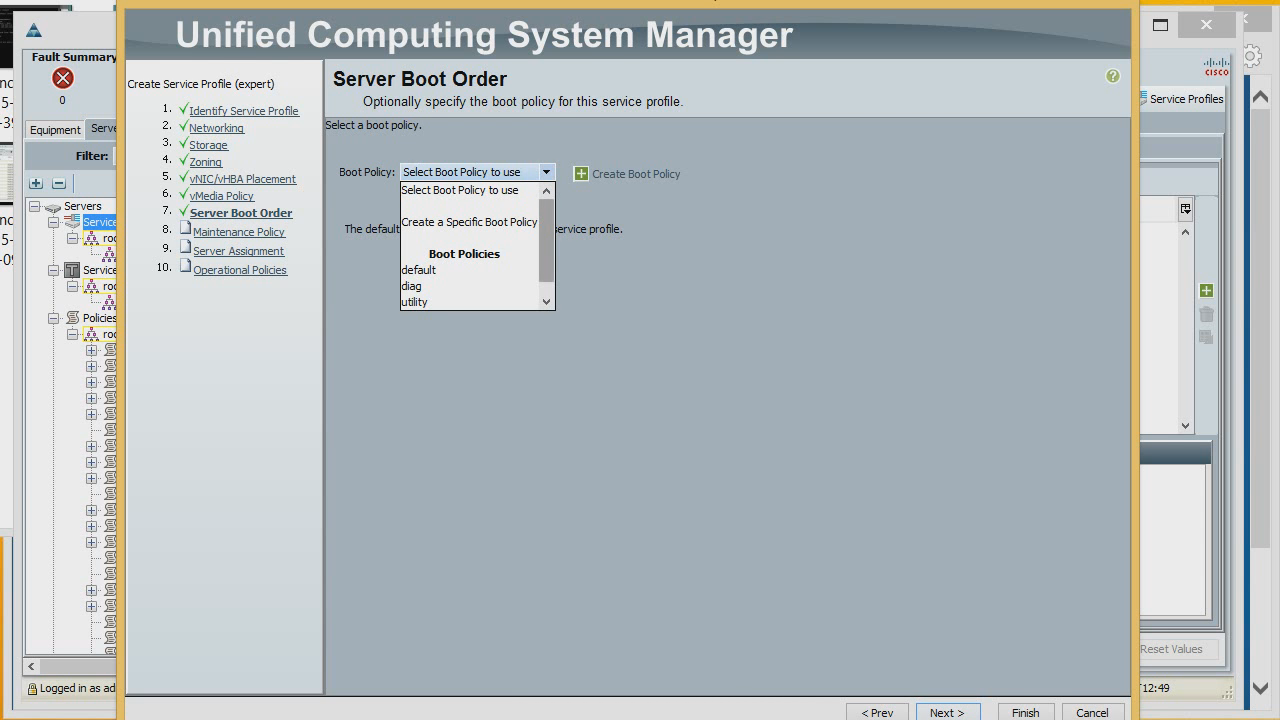

Select our newly created policy to use for the server profile.

Immediately proceed to the last step - the BIOS setup of the newly created server. Let's create some new profile to see what we can assign and see in the BIOS settings of the created profile and server. First, standard parameters, such as Quiet Boot, what to do when Post Error, what to do when power is lost, processor properties, enable / not include Hyper Threading, virtualization technologies, etc. Then adjust the memory, serial port, USB, PCI, QPI , built-in adapters (what to do with them and how to perceive them), boot settings.







As you can see, most of the parameters that are in the BIOS can be assigned, and they will immediately apply to the server.
Moreover, profiles can be applied to one server as well as to several at once, and, accordingly, immediately propagated to all servers.
Here we choose which IP address or IP address pool to use for external administration.

Actually, the profile is created.
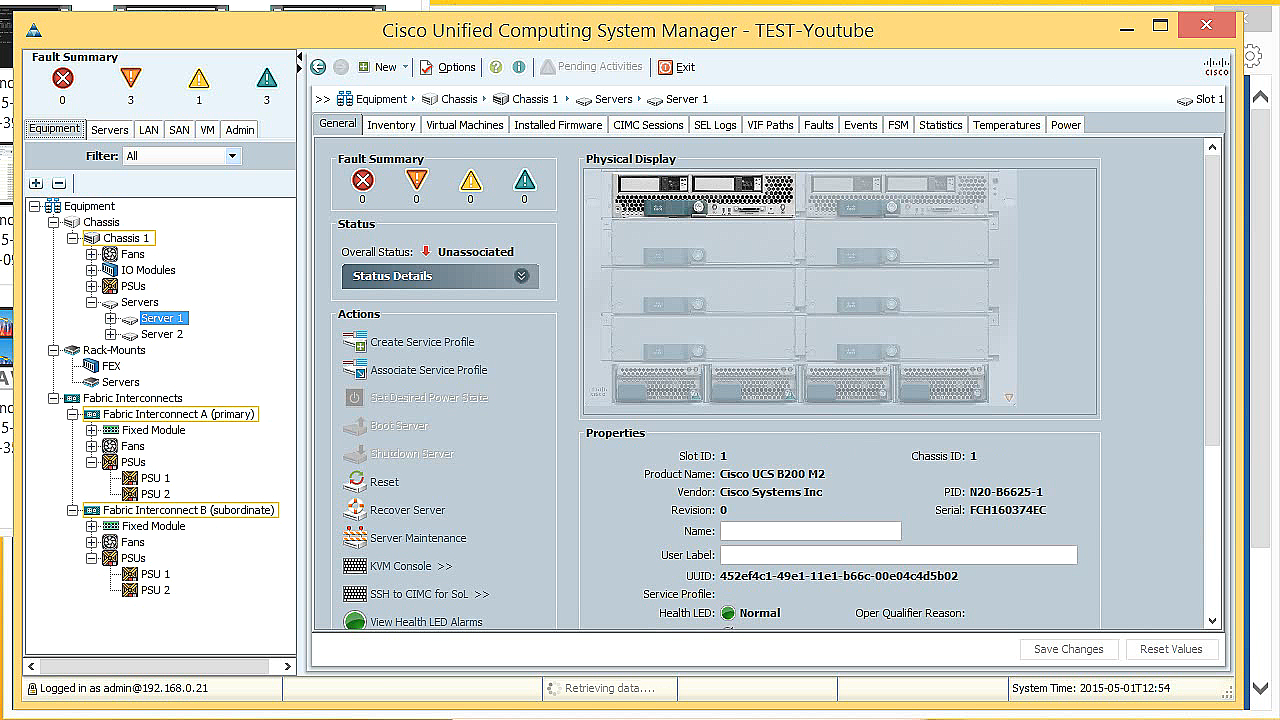
Now we can apply it. After a few minutes, our server fully complies with the profile we created.


Using the KVM console, you can see what is happening on the server itself.

All questions about Cisco@muk.ua solutions.
It should be noted that Cisco solutions through the group of companies are now available not only in Ukraine , but also in Moldova - a distribution contract was recently signed in this country.
Training courses / trainings / workshops in various areas of IT infrastructure - Training center MUK (Kiev)
MUK-service - client and corporate IT repair, service contracts
Source: https://habr.com/ru/post/271039/
All Articles