Void tracking, or attacks on non-existent resources
Recently there has been a lot of talk about the fact that social networks and instant messengers are looking into personal correspondence and using it for their own purposes. After another throw in the direction of the modern-day Telegram, it was thought to conduct another study on this subject.
At the end of September, a colleague and I participated in the filming of the story for Channel One with a story about phishing schemes of Internet fraudsters. To show some details of such a “fishing” to journalists, the Odnoklassniki.ru counterpart was registered at m.odnoklassnliki.ru . A copy of the mobile version of the social network with an extra letter “l”, created in a couple of minutes using the Social-Engineer Toolkit (SET), was not added to any search engines and was intended for practical demonstration of data interception.
After the filming, the fake was removed, but even during the preparation we were interested in the statistics of page visits: The guest's IP-addresses belonged to mail.ru, Microsoft, LeaseWeb, Selectel Ltd. We decided to make another empty site on another domain - milcrosoft.com , in order to systematize the interest shown to an unknown "phishing" site by various monitoring systems, and then see who appears in the logs if the link is sent with a personal message to the domain level above - office365.milcrosoft.com .
')
Initial configuration
There was no text or multimedia data on the page, and the nginx settings meant giving a blank page when visiting a resource:
server {
listen 80;
server_name milcrosoft.com www.milcrosoft.com;
if ($ host! ~ ^ (milcrosoft.com | www.milcrosoft.com) $) {
return 444;
}
if ($ request_method! ~ ^ (GET) $) {
return 444;
}
access_log /var/log/access.log main;
error_log /var/log/error.log;
location / {
root / var / www / milcrosoft;
index index.php index.html index.htm;
}
error_page 404 500 501 502 504 /error.html;
}
Identical configuration was used for the second office365.milcrosoft.com domain.
Part One - Internet bots
The fastest was Chinese with the address 110.75.105.9, owned by Zhejiang Taobao Network Co., Ltd. This bot appeared on the first day of the site.
The next day, search bots of Google, Yahoo, BING, Baidu visited the page with GET / HTTP / 1.1 and GET /robots.txt HTTP / 1.1 requests.
Among the companies involved in security, it is worth noting “Kaspersky Lab”, its bot c IP 93.159.230.39, perhaps, analyzed the page for its reputation system. The rest of the antivirus companies did not visit the page. Similar statistics were apparently collected by phishmongers.com (198.186.192.44), “competitive intelligence agents” with aiHitBot spy, and the creators of the anti-phishing panel, Netcraft, which sent a HEAD / HTTP / 1.1 request on the 14th day of its life.
“Crawlers” from DomainSONOCrawler, who visited us several times a day under different user agents, as well as Chinese from crawl.baidu.com, showed considerable curiosity .
It is worth noting the South Korean visitors from BORANET (211.36.137.129) with a GET / hardware / warr HTTP / 1.1 request (probably addressed to microsoft.com/hardware/warranties ) coming from the SAMSUNG SM-G920L smartphone. In general, there were a lot of requests from mobile devices, most of all from the iPhone, and most likely they were the results of errors when typing the name of the official MS website.
Also surprised guests from CHINANET (115.195.117.24) with user agent WIN98.
Attacks on admin panel
On the third day, from the address 91.210.145.15, located in Zhovti Vody, near Dnipropetrovsk, the admins began to knock. The following requests were received from the ICTNET-UA-NET network name:
GET /wp-login.php HTTP / 1.1 (WordPress admin panel definition)
GET /administrator/index.php HTTP / 1.1 (Joomla panel definition!)
GET /admin.php HTTP / 1.1 (admin panel definition)
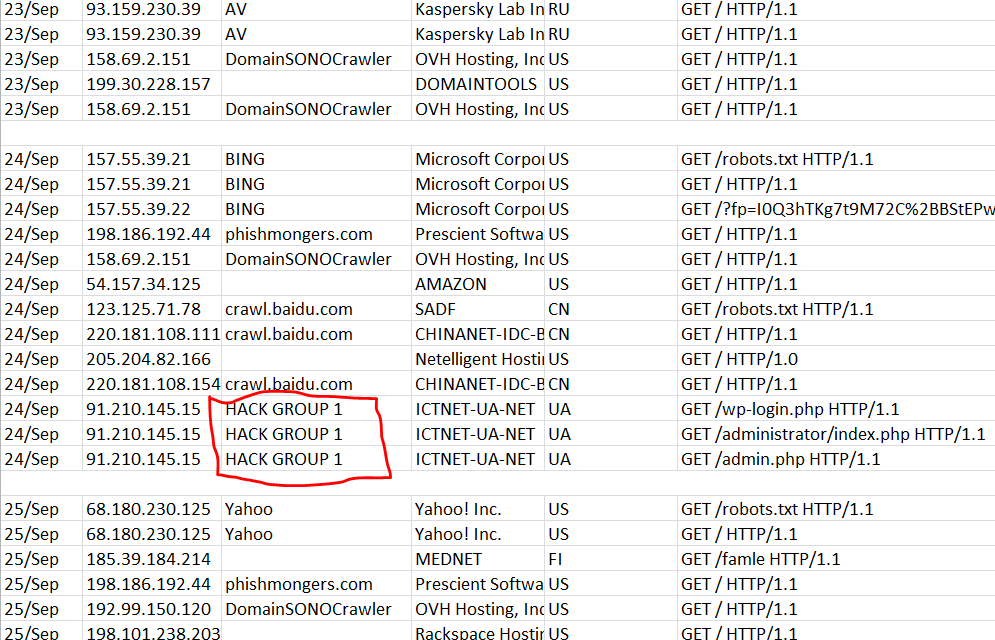
The next day, such requests were recorded from the address 193.201.227.78 (Ukraine), and then from the address 46.216.0.141 (Belarus). Geographical affiliation, of course, does not play any role, anyone can buy VPS anywhere.
What is the purpose of such requests? Since we did not set ourselves the goal of creating a full-featured hanepot, we can only assume that they carry the greatest threat to the newly created pages on such popular engines as WordPress or Joomla! .. If the owner did not manage to change the default password, they may not notice it share a malicious code or use the site to spam or intercept confidential information.
Among other visitors to the test page, it is worth noting the company Societe Francaise du Radiotelephone (93.20.177.34) with the request GET /favicon.ico HTTP / 1, numerous visits to www.best-seo-report.com from various addresses and guests from the TOR network (IP 192.99 .246.164) with the name tor-exit.ethanro.se and address in the title of the user agent www.pizza-tycoon.com .
One of the last days of our experiment with the Brazilian address 201.93.81.118 again checked access to the WordPress admin panel with a GET /wp-login.php HTTP / 1.1 request. In addition, the message GET /? Author = 1 HTTP / 1.0 was sent from IP 119.82.24.111.
Part Two - Reading Correspondence
Later, we checked how carefully social networks and popular instant messengers refer to links in personal messages. About two years ago, Microsoft had already caught this. Then two employees of the German Internet edition exchanged HTTPS links in Skype and after a few hours in the server logs found traces indicating a visit from the Microsoft IP address. And this fall, Reddit users discussed rumors at all that Facebook had learned to show contextual advertising depending on keywords in voice communication. One reader claimed that his FB began to show ads in Spanish after he became interested in Spanish TV shows.
It seems to us premature to investigate the espionage from the social networks for voice traffic, so we limited ourselves to sending a link to our page within messages to other subscribers. The recipient of the message did not go to this address so as not to introduce excess entropy.

As it turned out, bots Skype, Twitter, Facebook and VKontakte actively visit the page, the address of which is transmitted in private correspondence. Telegram does this, but if you enable the “Secret chat” mode in this messenger, the robot stops following the transmitted link.
Source: https://habr.com/ru/post/270819/
All Articles