Security Week 46: Versatile Java Bug, Life for Crypto-Folders, 17 Adobe Flash Patches
 In the new episode of our series:
In the new episode of our series:- A serious vulnerability in the Apache Commons Collections library jeopardizes Java-based services from several companies, such as Oracle WebLogic and IBM WebSphere. Like any other vulnerability in common and widely used libraries, this patch is a talk of heightened tales about what to do and who is to blame. In fact, the vulnerability was discovered back in January, but since there was no cool name for it and no logo was drawn, no one paid attention.
- Cryptowall - a cipher trojan recently recognized as the most profitable member of the family, changes behavior. Now, in addition to encrypting the content, the file names were also distributed, which leaves even less (although there were few) chances of decrypting the data without a ransom. It is distributed, among other things, with the help of fairly obvious infected email attachments.
')
- Flash patch again, again serious vulnerabilities. We continue the heading “critical dullness”.
Seals are not included. Rules: Every week, the editors of the news site Threatpost selects the three most significant news, to which I add an extended and ruthless comment. All episodes of the series can be found by tag .
Vulnerability in Apache Commons Collections or how the industry for 9 months could not see a serious bug in a common library
News The source code of the patch with comments. Oracle Advisory . Presentation of the January study. Research authors Proof of Concept.
The vulnerability found in the Apache Commons Collections is in many ways similar to the one found earlier in Bash. Here we also have vulnerability in free software, which is used in many projects, and accordingly puts them at risk. The main difference between this story and Shellshock is the fact that the details of the vulnerability were revealed back in January of this year, but only 9 months later, software developers using the library realized that the problem is serious and concerns them directly. However, if you tell the story in order, then you need to start with serialization .
Serialization is a fairly simple programming concept. We have some object (for example, located in the RAM), and it needs to be transferred to someone - for example, to another process or to another machine or something else. To do this, the state of the object must be preserved so that it is possible to accurately recreate it later - that is, consistently take it from beginning to end, hence the name. There are a great many methods of reading and recreating (in the “Cryptonomicon” it was called “instillation” and “digging”).
In January of this year, researchers Gabriel Lawrence and Chris Frohoff from Qualcomm spoke at the AppSecCali 2015 conference with the results of an interesting study. The main, in their opinion, the problem of serialization lies in the fact that developers trust this process (more precisely, how it is implemented in their development tool or some kind of software environment) somewhat more than necessary. This, in turn, leads to such a potential trouble, when data from the user is serialized, and in the process of de-serialization, it turns out quite arbitrary executable code. It turns out remote code execution vulnerability.
Researchers showed features of the serialization and de-serialization processes using the example of the PHP programming language, and then turned to examples that allow to run arbitrary code — for example, in Ruby and in Java . But although the researchers made it clear that the problem was, and serious, their work was rather theoretical. Perhaps that’s why they didn’t pay attention to it until the end of last week, when researchers Stephen Breen and Justin Kennedy from NTT Com Security showed a working proof of concept attack using de-serialization on the Apache Commons Collections library. Their work was based on that January study.
And then everyone realized! The Apache library is based on the Java Development Kit — also an open development tool (since 2008). Suddenly (tm) it turned out that it is actively used in a huge number of Java-based products and services, including, for example, IBM WebSphere, Oracle WebLogic, Red Hat JBoss, Jenkins and OpenNMS. And yes, they are all subject to this type of attack. The authors of the proof of concept were immediately put in a look - what did you not warn us about? To which they respond that for more than 9 months the possibility of such an attack was known, and no one even scratched.
In general, again, did not agree. It’s really hard to assess the real consequences of a theoretical study, but with the interaction between security experts and the IT industry in general, something needs to be done. In this case, the dialogue between Researchers and Industry looked like this:
Researchers : In some cases, the de-serialization process can be used to attack; developers trust it by default.
Industry :

Researchers : Including Java, which is used in many places, and somehow it all does not look very safe.
Industry :

Researchers : Hello! How many can you repeat that you can be hacked, take control of the server and steal everything ?
Industry :

That's how we live.
Cryptowall Trojan now encrypts files too
News The news about the crypto-loser for Linux. Lab service for decrypting data encrypted with CoinVault and Bitcryptor cryptors.
Almost every news about encryption Trojans on Threatpost is doomed to popularity: they follow the topic, because the topic is important. According to our data, 45% of companies take the risk of data loss as a result of this type of attack very seriously. Recently, there has been a lot of news about cryptographs, let's go through the main ones.
Updating the Cryptowall encrypter once again makes it clear that a crypto attack, like a fire, is easier to prevent. Researchers at Bleeping Computer discovered a new version of a cryptotanyan that encrypts not only the data of the files, but also their names. It seems to be a simple innovation, but it closes and so a small number of loopholes, allowing you to restore at least some data without paying a ransom. And, of course, it adds frustration, because your files after the attack will look like this:
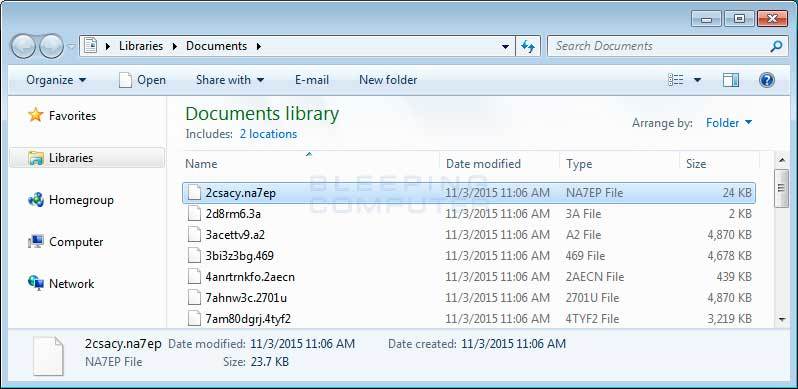
Screenshot from the Bleeping Computer study .
From a technical point of view, this is certainly not a breakthrough in the technology of malware. But the creators of Cryptowall on technology and do not earn. They earn on a well-built business, or, more precisely, on a good organization of the criminal community. Cryptowall is considered one of the most profitable cryptographers, which has caused damage to companies of more than 300 million dollars. And on such a scale, not only high-quality malware is required, but also an expanded sales network (for example, using exploit whales ). And also marketing:
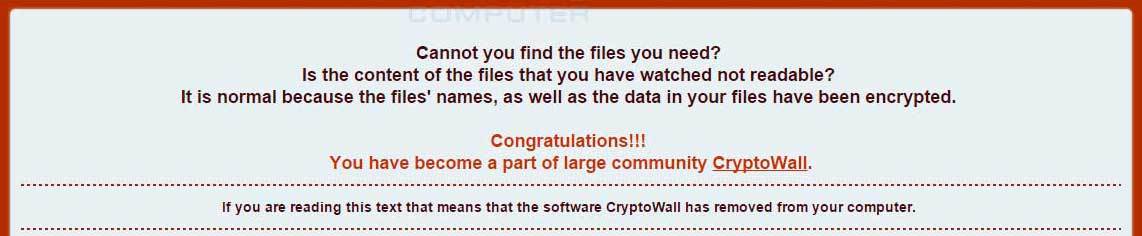
No, you saw it? Welcome to the worldwide community of
However, not everyone is so lucky. The Linux-encoder Linux.Encoder.1 discovered by Dr.Web (Ransom.Linux.Cryptor and Trojan-Ransom.FreeBSD.Cryptor in our classification) was not the first attempt to spread the familiar scheme of extortion to the world of open source, but certainly the most unsuccessful. Firstly, no exploits and cunning methods of attack were observed. Secondly, after a couple of days, BitDefender experts found that the stuffing could be turned back: the Trojan used the system time and date to generate keys, and this is not the best way to encrypt.
In Adobe Flash, 17 vulnerabilities were closed, of which 15 are dangerous.
News Adobe Advisory .
The pace of closing holes in Flash and Reader / Acrobat, Adobe is soon able to take the bar of 100 vulnerabilities per quarter. In October, 69 pieces were closed, then three more, but one of them was very serious, and a patch was released yesterday covering 17 more holes. Of these, 15 belong to the type of vulnerabilities when working with memory (use-after-free), and another one - to the type object type confusion. The last, 17th bug bypasses the Adobe security system and also leads to the execution of arbitrary code.
Adobe, of course, well done, but such frequent and abundant patches somewhat complicate the process of keeping Flash up to date even for the user, not to mention companies. In addition to its own patches, Adobe has prepared an updated version of the Flash module for Internet Explorer and the Edge browser, and this update has already been included in the traditional Patch Tuesday fixes from Microsoft. Meanwhile, the creators and distributors of exploit packs build their business on Flash vulnerabilities almost entirely .
What else happened:
Google Chrome developers will no longer support Windows XP and Vista, as well as Mac OS X up to version 10.8.
Comodo 's Certification Authority (CA) has issued certificates that violate the basic security rules for those: they contain the names of internal servers (for example, help and mailarchive). Since administrators in different companies call internal resources without imagination, such lines theoretically open up the possibility of MiTM-attacks and generally allow using certificates not where they originally intended.
 Antiquities:
Antiquities:"Shadow-723"
Nonresident very dangerous virus. It scans the directories of the current disk and standardly infects .COM files found in them. In July, he tries to format the disks A: and C :, and then publishes (with the aid of a speaker) the sound of a dying hard drive (T-P-P-P-p-pppd ...).
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 82.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/270815/
All Articles