Experience of using the cloud in managing access control to databases in a software project
Thank you very much for preparing the article, Nikolay Sinitsin, Aplan’s senior software engineer , for his help in writing this article. Our remaining Azure articles can be found on the azureweek tag .
Hello!
Once, in one of the projects, a task was set, the terms of which were to ensure the need for software to access various databases with access control - literally, who has a license, in order to give access, otherwise block access. Additionally, it was necessary to be able to change the connection to another database, and for the software to know that the address had changed. Several ways were found to do this, but in the end they came to the option of using Azure cloud services - how the decision was made and why and how we used the cloud - read under the cat.
At first, they thought of following the path fairly obvious - there are databases, users are created on each database who have “licenses”. The problem of access was decided, but, as you probably understand, it is very inconvenient to manage such a system - add, delete users. In order to solve the problem of changing servers, it would be necessary to write a certain conditional service that would also keep in itself users who have access. And everyone would know the address where the database server is located.
This method has several drawbacks:
- Need to write a service;
- There is no single user repository with access to the system;
- It is difficult to maintain the relevance of data on users on different databases.
Let's go through the minuses.
Minus: You need to write a service .
')
“What service we needed was,” you ask. Service management control access to databases for software products deployed on different machines. Writing services is not bad. But when it is necessary to write a service from scratch, it is possible to catch various errors, incl. the most difficult is human. This is especially true when you write access control and role distribution services. One mistake - and instead of giving one user rights to a resource, you may be confronted with the fact that rights are given to a greater number. The cost of error is very high.
Minus: There is no single user repository with access to the system .
In addition to the fact that there must be a service that will allow to provide different access, a single user database and a management manager are needed, which will allow you to easily manage this database. Write yourself from the very beginning = spend a lot of time.
Minus: It is difficult to maintain the relevance of data on users on different databases .
If we use the variant in which users are set up on each database, we have the problem of synchronizing several databases among themselves.
Due to the fact that there are problems described, it was decided to look at the cloud services, which would solve the tasks and minimize or completely get rid of the above minuses + there was the possibility of a transition to the cloud database and site deployment in the cloud.

Consider briefly the cloud services that have been analyzed and used in solving the problem:
Azure Active Directory ( AAD or Azure AD ) is a multi-user cloud directory and identity management service. It is similar to working with Active directory, which comes with Windows Server. However, AAD is designed for users to work not in the local infrastructure of the company, but when working with cloud applications (for example, Azure Key Vault) With this service we solve the problems “there is no single user repository with access to the system” and “it’s hard to keep users up-to-date on different databases. " It was recently announced that AAD will support the ability to deploy domains.
Azure Key Vault - HMS as a Service ( Hardware security module ). HMS is a dedicated hardware that allows you to store, manage keys / secrets, and encrypt / decrypt, put / check signatures as safely as possible and quickly enough (specific hardware sharpened for encryption, according to applications, works quickly, but how many or what measurements were taken no information). Previously, KV was known as BYOK (bring-your-own-key). ( Link to article ). With this service, you can keep secrets related to access to a particular database (username, password, address, database type, etc.). Thus, users authorized by AAD obtain Token using which they access the secret. And the program, based on these data, is connected to the desired database.
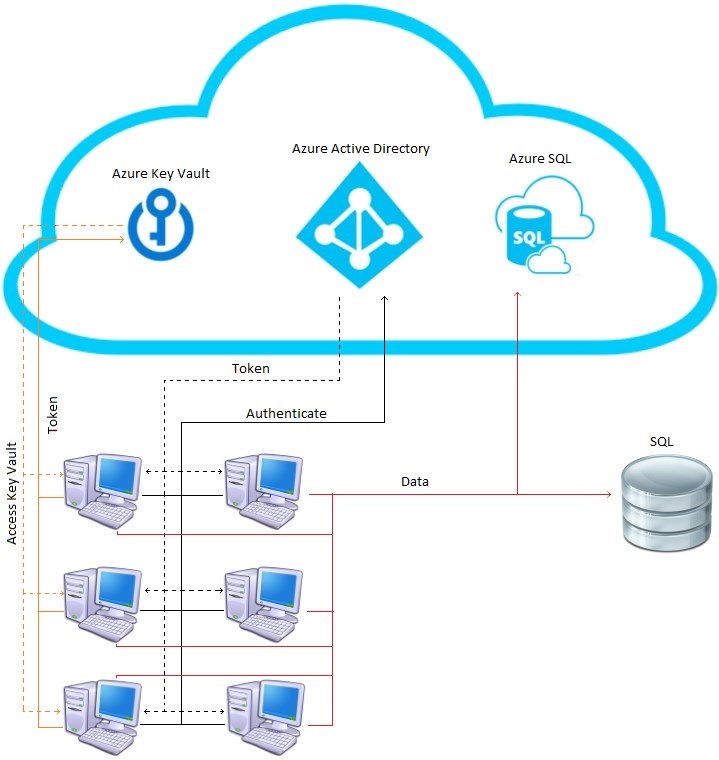
Using Azure Active Directory and Azure Key Vault
In the diagram above, you can see that access control, unified user repository, and management manager have been transferred to cloud services, such as AAD and Azure Key Vault. The interaction scheme is very simple. Each user of the software knows the login and password that the service administrator has given him. With it, the program is authorized in AAD and gets an authorization token, with which the software product accesses the Azure Key Vault service in which secrets are stored. Further using secrets, the software establishes a connection to the database.
In case you need to remove access to the database, you can delete the user from AAD and generate a new password to the database. The remaining systems, having lost the connection, will restart the secret and establish the connection.
If we change the address or location of the database, we only need to change the information in secret and the system will automatically connect to another database that will come in from Key Vault.
Advantages of this approach:
- A single point of entry and access control is used . This plus allows you to easily manage the entire system of interaction with the database. There is no need to write and check services for errors; this is all done for us by Microsoft employees and the user community using these services.
- The simplicity of the extension , since we can move between databases easily without changing anything. We can change from the database deployed on our host to the database in the cloud.
- Convenient access control interface . There is no need to spend time and money on writing the access control interface. Everything is done and timed out.
Among the minuses one can be singled out - in this implementation, after deleting the user, we need to change the password to the database. And this is not very good, since the system is already being used.
Such was the experience of using the cloud to solve a specific problem. Thanks for attention!
Source: https://habr.com/ru/post/270731/
All Articles