Accidental hacking: why break low-visited sites

Every year, the growth in the number of attacks on web applications is only increasing. More and more cases of resonant hacking of large companies and services (an example of hacked companies in the last two weeks):
Hacker discovered zero-day vulnerability in vBulletin, one of the most popular forum engines. Detailed information about the breach is currently unavailable, but it is assumed that the attacker carried out a SQL injection, after which he uploaded his own shell to the official vBulletin forum and stole the personal data of all registered users, including logins, initials, secret questions and answers to these, as well as salt values for passwords.
A British telecom operator TalkTalk confirmed the fact of hacking into its computer system, which resulted in the attackers stealing the personal data of the company's clients. Information included names, account numbers, addresses, and phone numbers of users.
')
The company 000Webhost, which is the most popular free hosting in the world, carried out a cyber attack, during which data of 13.5 million users were compromised. Stolen information includes first names, last names, passwords in plain text, email addresses and IP addresses.
These are large companies and such incidents, as a rule, appear in the tops of news feeds. As for small and low-visited sites - they are broken by thousands every hour (for example, one of the deface-mirroring tapes ). These attacks are aimed at specific sites and attackers attack one target until they achieve their result (or leave the victim alone, failing to overcome defenses). This is the so-called. “Targeted attacks”, with the choice of a specific victim, the attack goes to the minimum number of victims with the maximum amount of effort by intruders.
However, in more than 90% of cases, victims of hacker attacks are sites that have been “dealt” randomly, as a result of such impersonal automated attacks, which are called “untargeted”. A non-target attack on a site is an attempt to gain unauthorized access to a web resource, in which the attacker does not intend to hack a specific site, but attacks hundreds or thousands of resources selected by some criterion. For example, sites running on a specific version of the content management system. Such attacks hit the “squares”, trying to cover the maximum number of sites at the lowest cost.
No purpose attacks
A non-target attack is an attack that is actually carried out “for good luck”, and random websites, regardless of popularity, size of business, geography or industry, become its victims. An attacker selects sites by certain criteria (for example, sites that run on a vulnerable version of a CMS Wordpress plugin are selected), and then tries to exploit this vulnerability on all sites from the list. If a successful attempt is made, the hacker tries to take advantage of it: to gain a foothold on the site by downloading the hacker script (backdoor, web shell), add another administrator, inject malicious code, or obtain the necessary information from the database.
For example, one of the last serious vulnerabilities affects the popular worldwide CMS Joomla, on the basis of which a fairly large number of sites operate:
The developers of the popular content management system Joomla have released a security patch that fixes three vulnerabilities. One of the gaps allowed the attacker to remotely elevate privileges using a SQL injection and obtain administrator rights on most web sites running Joomla. The vulnerability can also affect resources managed by the VirtueMart platform, since it is based on the vulnerable version of the Joomla kernel module. Since the flaw was found in a kernel module that does not require add-ons, all web sites based on Joomla 3.2 and later versions are vulnerable to attack. In this regard, all resources managed by VirtueMart may also be compromised.Typically, the attackers in this situation are two steps ahead of the site owner: the software vendor needs time to eliminate the vulnerability, and the site owner needs to install an update / patch.
In fact, as soon as the site gets into search results, it immediately becomes the object of non-targeted attacks. It does not matter what the scale of the site is, how many visitors it has, what citation index, how much per day it sells goods and services and what topics it relates to. Only the technical characteristics, according to which he can get into the hacker sample, are important. Malicious users find potential sites that are vulnerable and try to exploit them.
The growing popularity of non-targeted attacks
According to statistics from our partners from the company Revizium, about 3/4 of the attacks are non-targeted . Our own statistics collected from the autoscan service only confirms this data: in 2015 there are quite a few vulnerabilities that allow attackers almost immediately to attack the site:
First, it is the simplicity (accessibility) of the execution of attacks. Currently, there are a lot of tools in open access - various scripts, applications for Windows and Unix platforms - with the help of which even an ordinary schoolchild can conduct non-targeted attacks on thousands of sites.
Secondly, it is high efficiency and effectiveness of attacks (both economic and technical). At low cost — sometimes practically nil — literally in half an hour, you can hack hundreds of thousands of sites and gain access to a large array of resources. Well, there are quite a few models of monetization of hacked sites today.
As a rule, the victims of mass attacks are the so-called “average sites”, whose owners do not pay attention to security and protection issues — do not update or regularly update the site and server software, use weak administrator passwords, do not change the default settings, set “broken »Versions of plugins and templates.
Hacking a small site for its owner can carry quite big problems and troubles: using the site to send spam and malware (including quite dangerous varieties of crypto-fiber):
Sample letter:
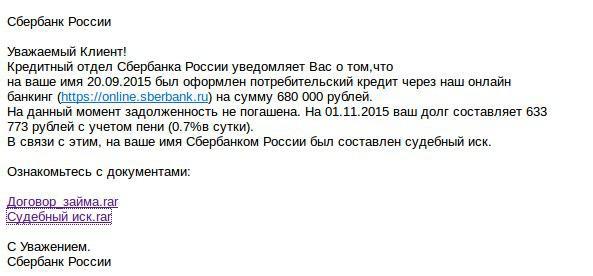
Malicious file on the link from the letter:

The result of checking the file on virustotal.
The site itself is not interesting to attackers, but they use it as a platform for attacking users and spreading malware. This destroys one of the big misconceptions of the owners of small sites - “why break it, and who needs it”. This misconception is found among site owners who have not yet encountered a burglary.
A hacker may not be interested in the site itself, but in a hosting resource from which, for example, you can send spam or on which you can host a phishing page that “steals” confidential user data. And the number of visitors to the site does not matter - the traffic is either not needed, or can be generated in another way. In some cases, attackers use hacked sites as resources to attack other web projects (for example, to conduct brute force or DOS attacks) or as an intermediate link to redirect visitors to other infected sites and pages, that is, turn them into a link in the so-called A bunch of exploits, systems for exploiting vulnerabilities in user browsers.
Recommendations to site owners
Every day, tens of thousands of unsuspecting site owners are victims of web attacks. However, do not despair - it is easy to prevent an unauthorized invasion - all you have to do is stop being the owner of an “average” web resource and accept the aggressiveness of the web environment.
It is necessary to carry out procedures for updating the site and its components, check the integrity and create backup copies in time, and stop using simple passwords. If any components or service scripts are not used, delete them. It is also necessary to carry out preventive measures - a security audit, it is necessary to periodically check your site for the presence of vulnerabilities . The main thing to realize is that security is not a one-time procedure, but an ongoing process that needs to be given constant attention.
Source: https://habr.com/ru/post/270633/
All Articles