How the second chip allows hackers to bypass the verification process of a bank card

When you selected or changed PIN codes for your credit card and cell phone, you did everything right: you avoided the temptation to use the year of your birth, while choosing different codes for the card and phone. However, these precautions can be useless if a cyber criminal has intercepted your credit card at a point of sale.
The standard verification process for debit or credit card payments requires a card with an integrated chip and a PIN. However, a group of researchers from the École Normale Supérieure (ENS) in Paris recently published a report in which they explained how a group of hackers found a way to get around This system and managed to steal 600 000 euros from the hacked cards. Fortunately, good news - soon after that they were arrested.
')
A group of hackers stole 40 credit cards that supposedly should have been useless in the hands of criminals if they did not know the PIN codes of these cards. However, the criminals turned out to be “not badly made” and modified the cards, adding a second chip inside the cards, which could not be seen when looking at the card.
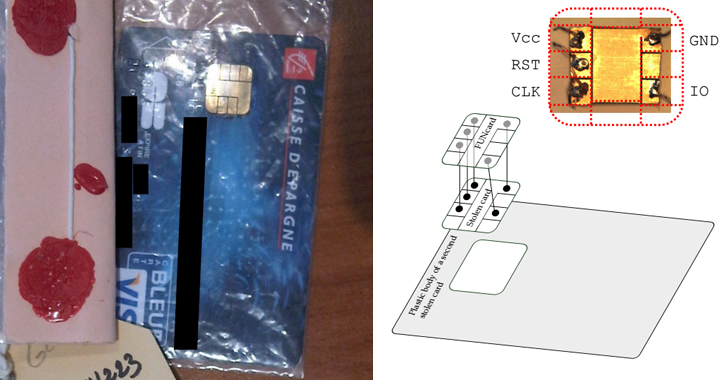
When the card was placed in the payment terminal (POS-terminal), they used the EMV vulnerability and carried out a man-in-the-middle attack , which allowed them to intercept communications between the card and the system.
At this point, the second chip entered the game, which allowed hackers to complete the transaction using any PIN code . This method was so simple that they used it more than 7,000 times.
Despite the fact that, according to the researchers, these vulnerabilities were corrected, and the fraudsters were arrested, this case showed the importance of contacting your bank in case the wallet is stolen or your bank card is lost.
Moreover, card modification is not the only way that criminals can use to “clear out” you if the card is in their hands. Ross Anderson, a professor of security engineering at the University of Cambridge, has been investigating for many years how hackers can gain control of a credit card, and recently summarized their research, indicating open opportunities for cyber criminals.
Some of the methods that cyber criminals could use include copying card information from a POS terminal to send to a third party, transferring chip information and card PIN to the magnetic strip of another card, or even manipulating the POS terminal to intercept the card. during the transaction and sending information to a cell phone.
So, what can users do now, what do they know about these vulnerabilities? In fact, not so much they can do, because Most of these scams use the disadvantages of standard POS terminals. This means that bank card manufacturers and banks themselves must ensure that transactions are as secure as possible.
Among the recommendations are the following: use a bank card to pay only in those outlets that you trust, do not keep all your savings on the same account, periodically check the status of your accounts to make sure there are no suspicious transactions.

Knowledge of credit card vulnerabilities can also help us choose other alternatives, such as cards with fingerprint scanners. This method of protection allows you to seriously protect yourself from cyber criminals.
Over the past year, MasterCard introduced the first card with a fingerprint scanner, made in collaboration with the Norwegian startup Zwipe. We also witnessed how major credit card manufacturers claimed they would experiment with face recognition technology for online orders.
This development of technology may contribute to the abandonment of traditional passwords in the next few years, which could be a solution to problems with chip and PIN card vulnerabilities. At the same time, the best thing to do now is to be aware of the risks that we may encounter when using bank cards.
Source: https://habr.com/ru/post/270231/
All Articles