10 relatively honest ways to hack mail
As you know, Ostap Bender knew 400 relatively honest ways to withdraw money . We, unfortunately, cannot boast such wealth, but we will try to gain a dozen.
Recall that in the first part of our e-mail protection cycle, we considered methods of protection. The second part is devoted to hacking. In this article we will not only tell the theory, but also show the practice of hacking. Methods of hacking mail are shown purely for academic reasons, and we are not responsible for unlawful acts committed by third parties after reading this article. The purpose of the article is to show users and administrators possible hacking options in order to know how to protect against them. We checked the methods described in the article on our employees and the results were very surprised. Therefore, this article can be considered as a guide for the administrator to check email security in the enterprise.

Next will be considered ten different ways to hack a mailbox. Each method has its own efficiency and complexity. The only protection against all methods of hacking is encryption . Even if someone gets access to the mailbox, he is unlikely to be able to read the messages, since all of them (or the most important ones) will be encrypted.
')
Quite a common way to gain access to someone else's mailbox is to send emails with built-in viruses. More precisely, the virus is not embedded in the letter itself, and the letter only contains a link to the virus. Typically, the content of the letter should somehow “hook” the user. It should be such that the user can not not respond.
Trojan examples are DarkComet RAT, SpyEye, Carberp. We have already written about DarkComet RAT , it was written about Carberp on Habré. SpyEye is our Russian Trojan, designed by Alexander Panin, who even appeared in the FBI reports.
We used a modified version of the ZeuS Trojan. At the time of creation (10/29/15), no anti-virus was detected by our version (Fig. 1), and it also had the function of disabling processes, including Dr.Web. However, Comodo was installed on the victim's computer - even better.
As a victim, we chose an accountant for our management company, Julia. For the sake of the purity of the experiment, she did not suspect anything that we were going to do. I think this was not worth even talking about.
So, we have a modified ZeuS, but how to make Julia run it? If you just send her a link, I understand the case, she will not go over it. To promise the mountains of gold in a letter is also the last century; users no longer react to this.
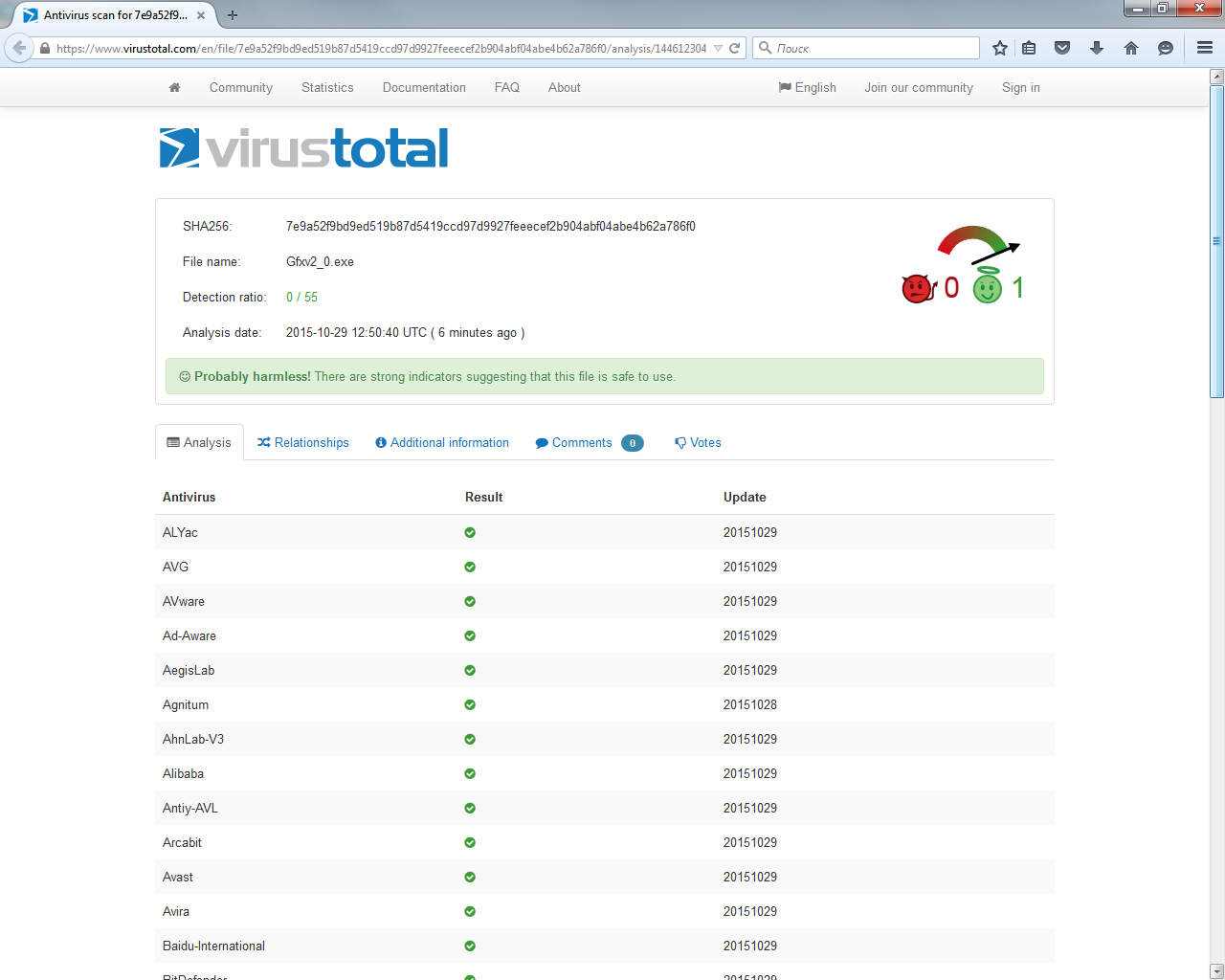
Fig. 1. VirusTotal report
Then we decided to send a letter allegedly on behalf of the Federal Tax Service (Fig. 2). We chose that "hook" the victim.
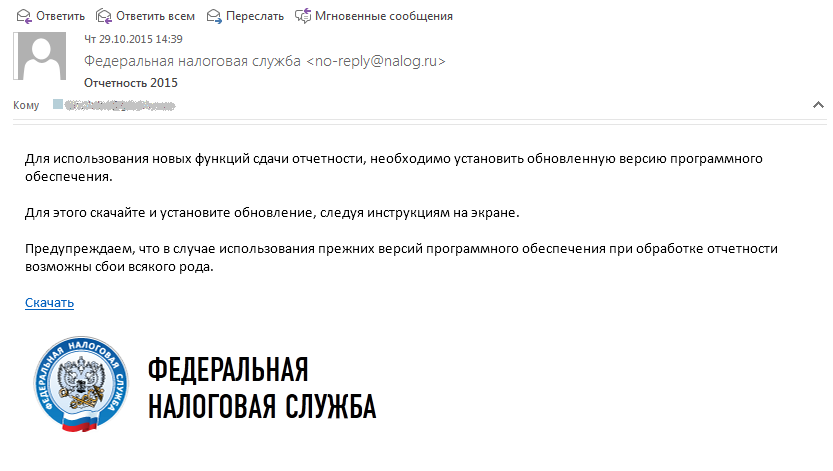
Fig. 2. Letter from tax
So that the From field contains an impressive name, and not xaker134566788@mail.ru, we have forged the letter headers. This is done quite simply, and how exactly it will be shown in method 5. For now, we will not be distracted by this.
As we expected, Julia downloaded the program and launched the update installer of the reporting form (Fig. 3). The installer is made using Inno Setup in 5 minutes. It is he who installs and launches our Trojan.
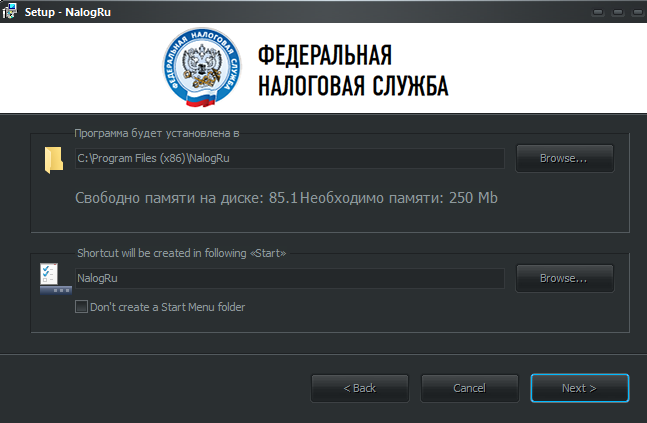
Fig. 3. Installing Trojan
After that, we can fully control the victim's computer (Fig. 4).
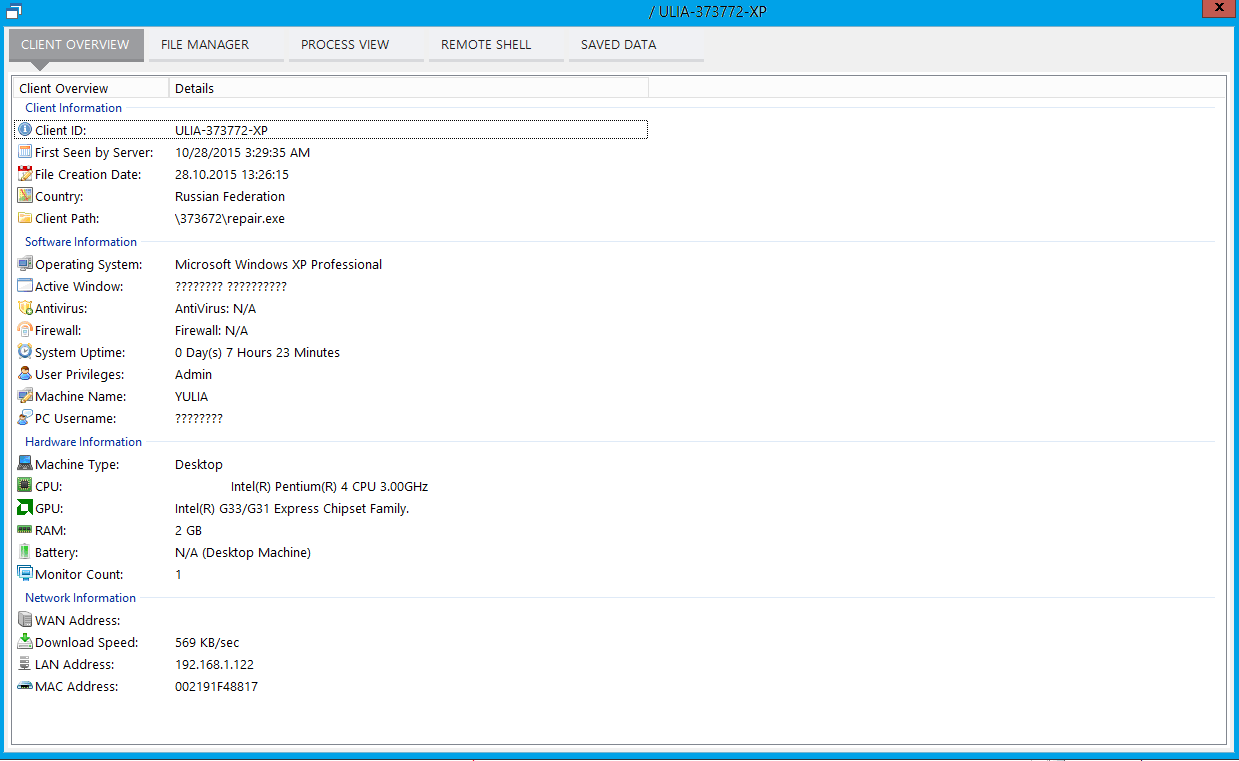
Fig. 4. Managing the victim's computer
What we can? For the sake of interest, we can view a list of computer processes in which, of course, there will not be our Trojan (Fig. 5). We can browse the file system (Fig. 6).
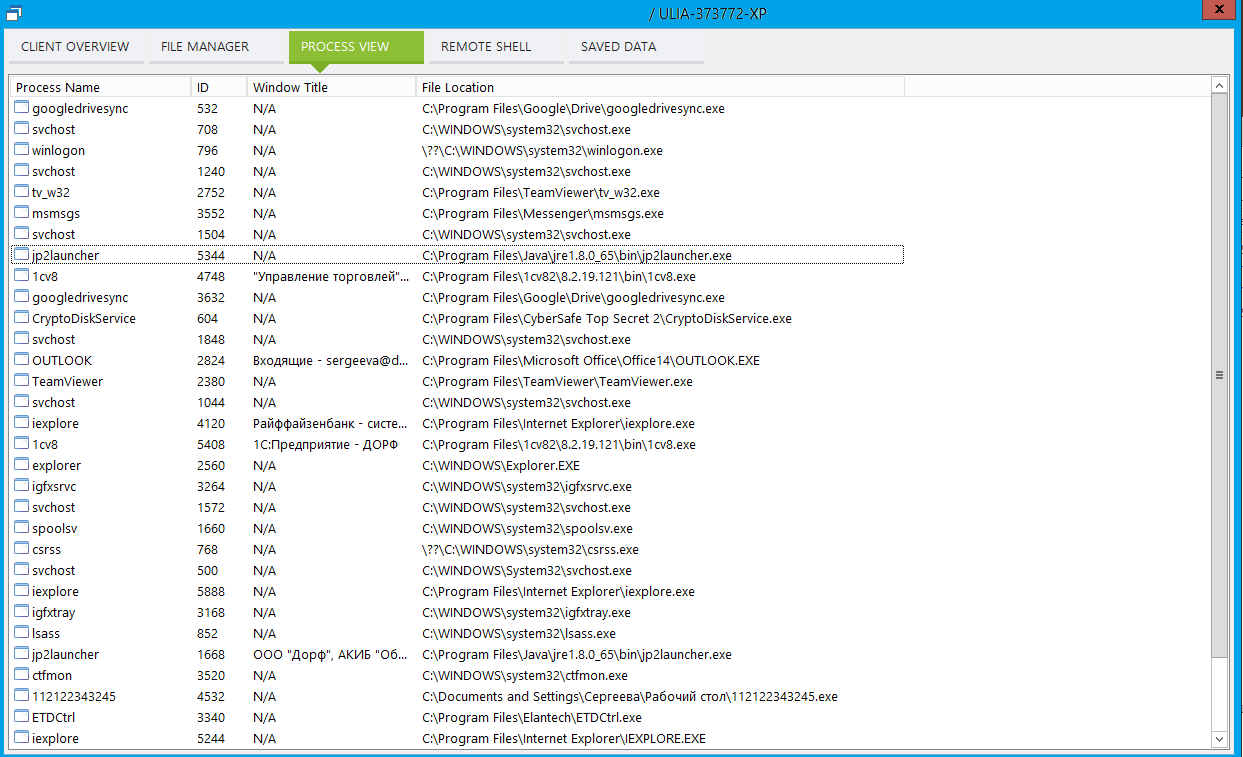
Fig. 5. The list of processes on the victim's computer
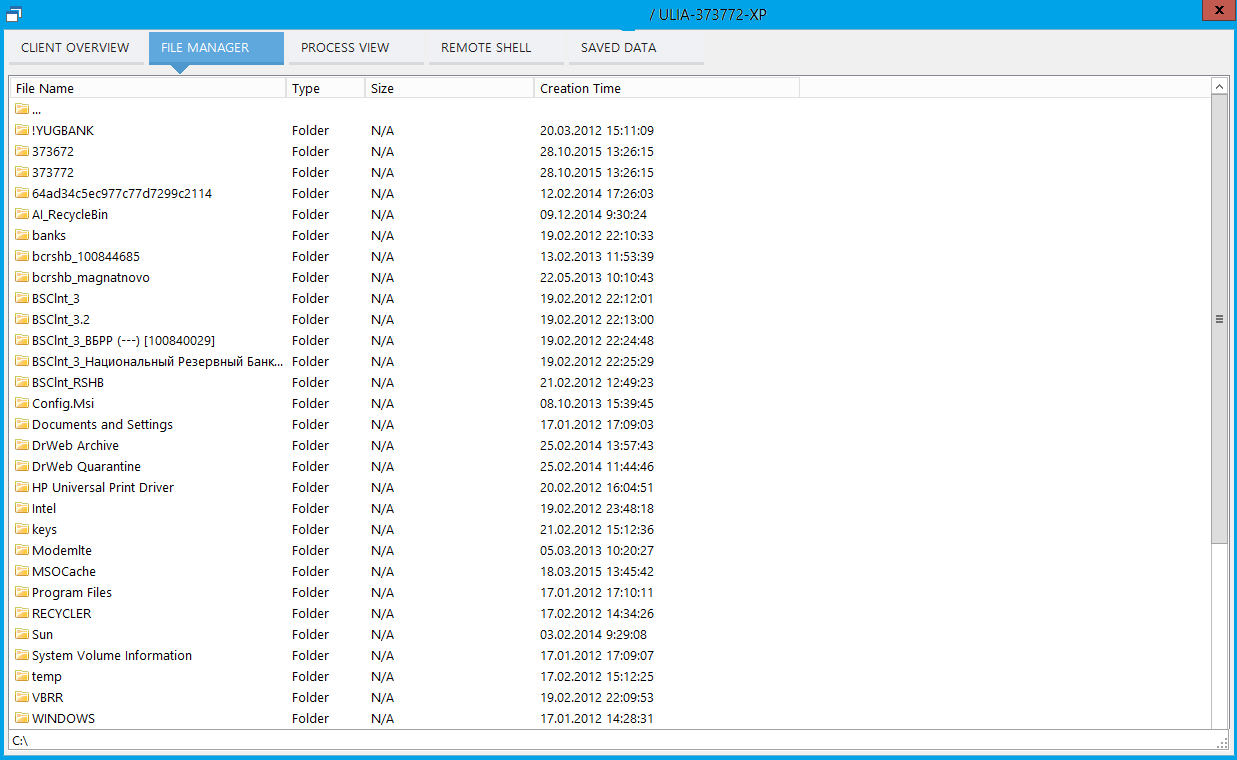
Fig. 6. The file system on the victim's computer
Of course, the most important thing for which all this was started was a list of passwords stored in the browser (Fig. 7).
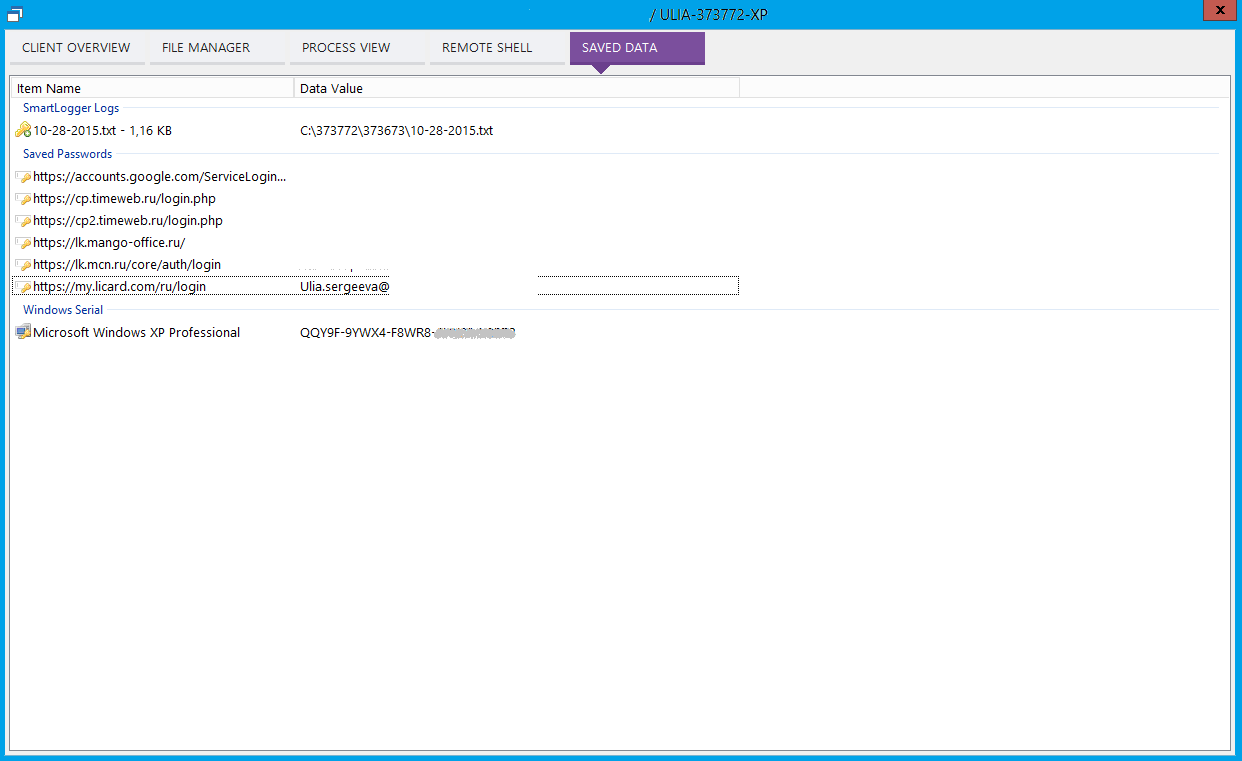
Fig. 7. And here are the passwords
The letter and installer are far from ideal, since everything was done in a hurry. However, our idea was a success. To achieve our goal, we have combined two methods - social engineering and a "fake" letter. Both of these methods will be discussed below.
Efficiency: average
Difficulty: Medium
Cost: low
The essence of this method is as follows. The attacker needs to know the phone number of the victim, specified when registering the mailbox. When resetting the password, the postal service requires you to enter the last characters of the phone number (or select a phone number from the list). An SMS with a password reset confirmation code will be sent to this number. Then the attacker sends the second SMS with the requirement to specify the code from the previous SMS.
The user, unaware, sends the code from the first SMS. The biggest drawback of this method is that the first SMS will come from Google, and the second from an unknown number. The success of this method depends on the acumen of the victim. Let's look at this method in practice.
The first thing we will try is to just reset the password, after which Google will ask you to enter the password that we remember. Understandably, we do not remember the password, so we press the button. I find it difficult to answer (Fig. 8).
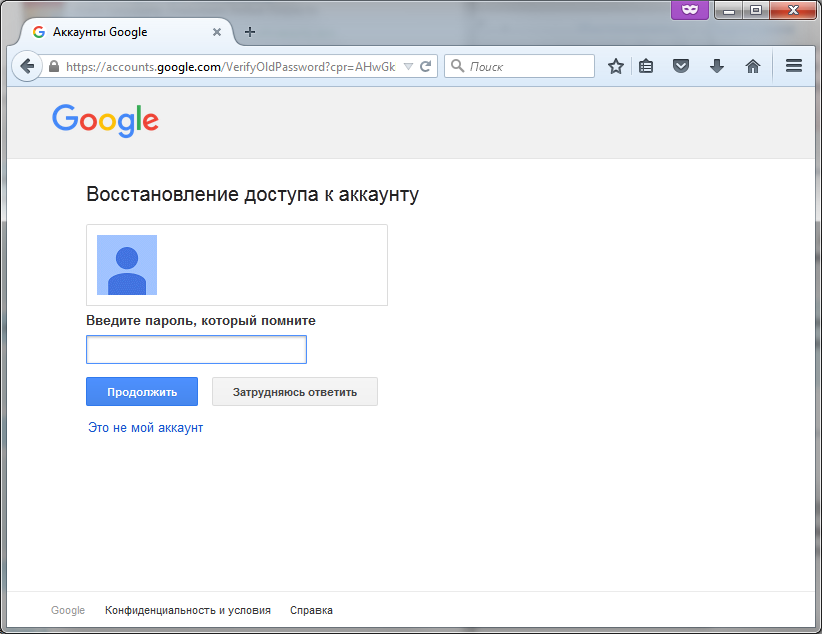
Fig. 8. Password recovery request
Further, if your victim was tied to an Android phone account, then Google will offer to send an alert (Figure 9), which looks like the one shown in Figure. 10. It is remarkable, but the smartphone did not make a single sound, but simply displayed an alert. If he is not in front of the user's eyes, there is a chance that he will not notice him. If the user clicks No, then do not despair - repeat this process several times - later you will understand why.

Fig. 9. Offer to send an alert
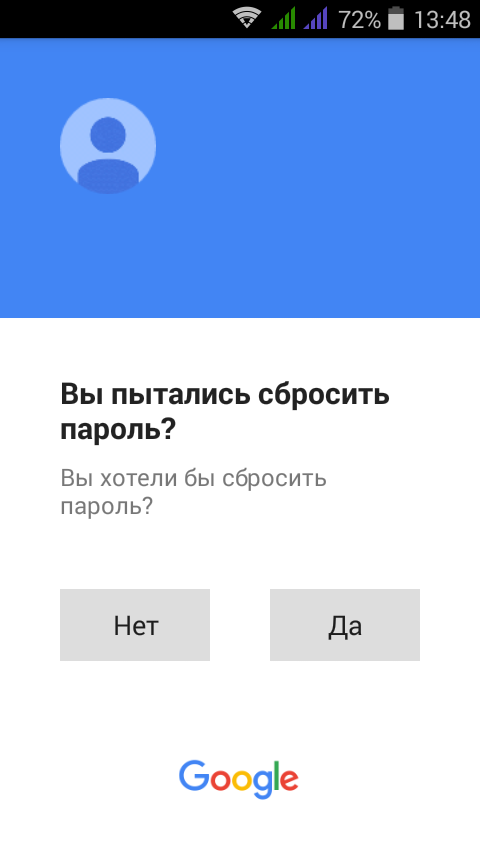
Fig. 10. Google Alert
After clicking the Send Alert button, the page shown in Figure 2 will open. 11. Follow the link Reset password in another way. This will open the classic password reset page via SMS code (Fig. 12). The same page will open if there is no Android phone attached to the account.
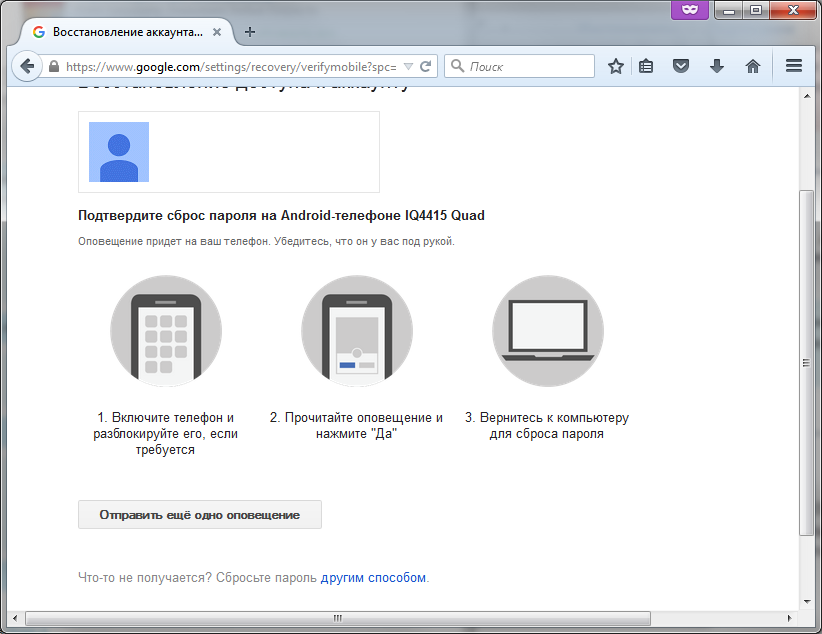
Fig. 11. Instructions for working with alert
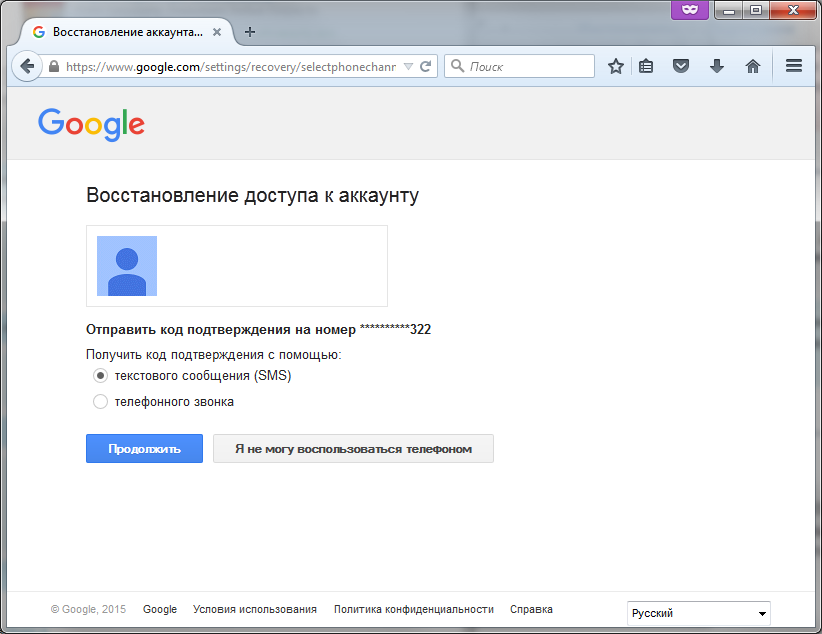
Fig. 12. Sending SMS code
It is the climax. The victim receives a Google confirmation code (Fig. 13).
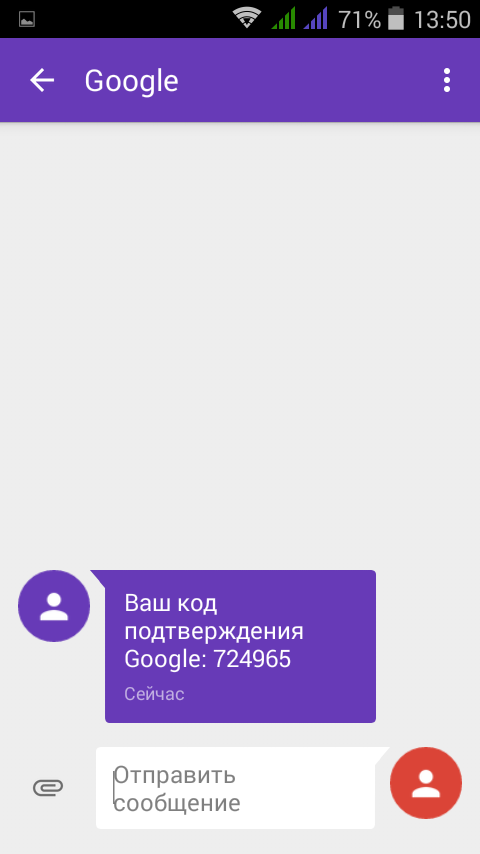
Fig. 13. Confirmation code
Then you should immediately send another message from another phone:
An attempt to log in to your Google Account has been prevented Send the Google verification code to unlock your account.
In fig. Figure 14 shows how this message looks on the phone screen.
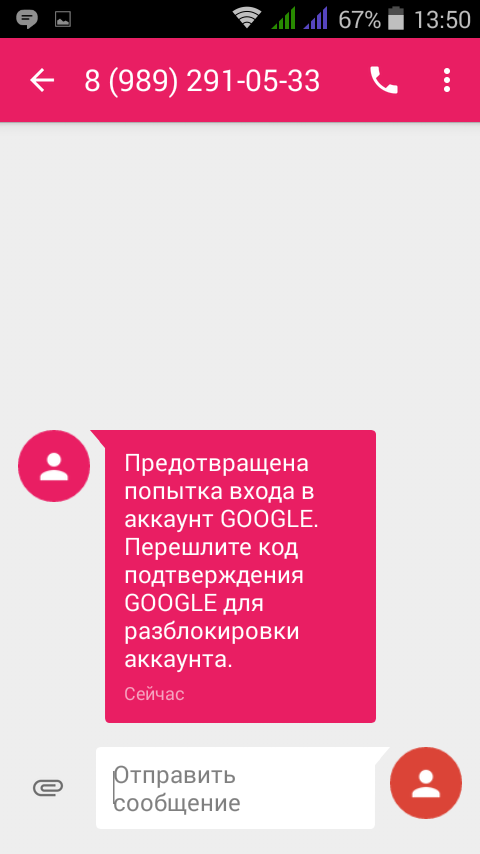
Fig. 14. Message from the attacker
On the one hand, the user can pay attention to an unknown number. On the other hand, put yourself in the place of the average user. First, he receives a password reset notification, then an SMS with a confirmation code, and then a message that suspicious activity has been noticed. Of course, you can complicate things a little and start a short number from which SMS will be sent. Getting a short number with the name of the service, for example, Google Security, is not a problem . This will only increase the likelihood of success.
In our case, everything turned out without a short number. We received an activation code, which was then listed on the password recovery page. Thus, we managed to reset the account password and get access to the mailbox.
Getting access to your mailbox is not everything. To prevent the victim from guessing that her box has been taken away, after resetting the password, you need to create a temporary password and send it by SMS, and in the meantime, forward the password to the “hacker” box. So you can get control of the box without causing special suspicion.
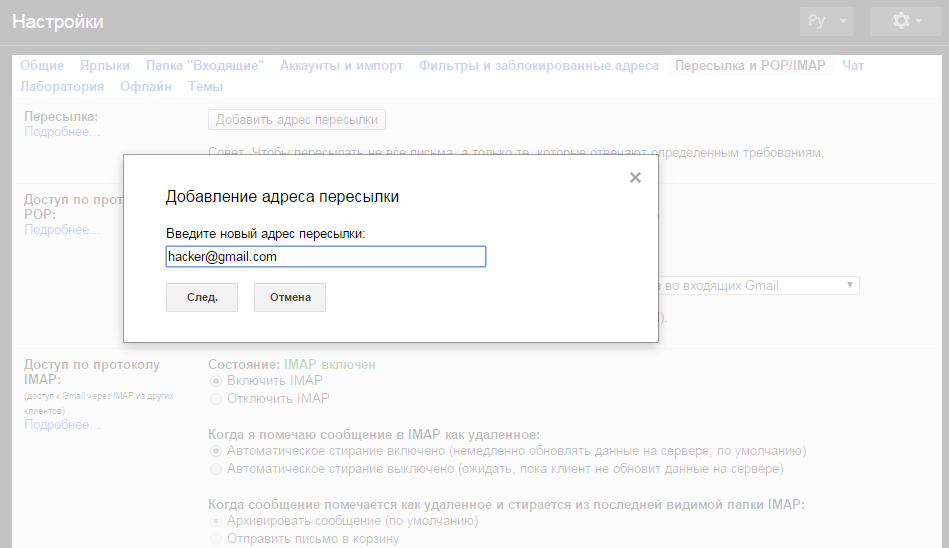
Fig. 15. Setting up forwarding
Efficiency: average
Difficulty: low
Cost: low
If you have access to the victim's computer, you can assume that you have already hacked mail. You can run either a keylogger or a program for “recovering” passwords of mail accounts on a computer.
The essence of the keylogger is that in a special file it records everything that the user enters from the keyboard. You will only have to go to the computer a second time to pick up the resulting file (or receive it by mail).
The advantages of the keylogger include the fact that it records everything. Therefore, in addition to passwords, you can still get a lot of interesting information about your victim. But they have a lot of disadvantages. The most significant - most keyloggers are successfully detected by antiviruses and if antivirus is installed on the victim's computer, the keylogger will not work. It is not always possible to disable the antivirus.
The second disadvantage stems from its dignity. In the resulting file is placed a lot of unnecessary information. It is not enough to collect information from the keyboard, you still need to find among all the excess that you need - a password.
The third drawback is that if the victim uses an email client and not a web interface, then the keylogger will not help at all. Most likely, the password has already been entered into the mail client and is remembered, so the victim does not enter it every time the mail is checked. Consequently, the keylogger will write to the file everything that the user enters, except for what you need.
There is one more drawback - if the selected keylogger does not support sending the resulting file by e-mail, you will have to go to the computer one more time. An example of a keylogger - SniperSpy - in case you want to use it.
Programs for "recovering" passwords of mail accounts allow you to immediately get all the passwords you are interested in without having to read megabytes of text to find the password you need. In addition, the antivirus does not respond to them. One of these programs is Mail PassView . It allows you to recover passwords for the following mail accounts:
We checked the program on our computers and declare that it works (Fig. 16). In fig. 16 passwords, as well as e-mail addresses are overwritten for obvious reasons.
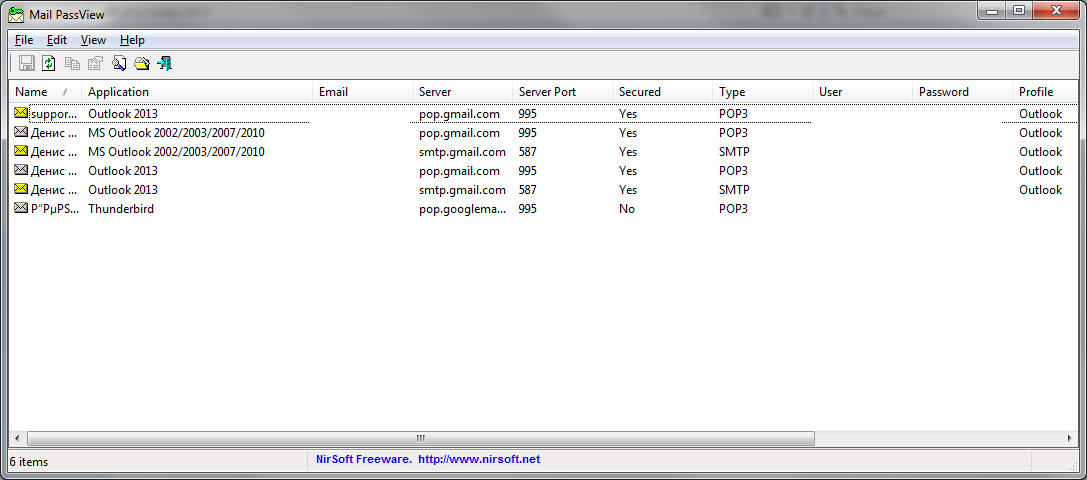
Fig. 16. Mail PassView
Mail PassView is not the only program of its kind. There are other programs:
All that is needed is to know which email client uses the victim. Finding a program to “recover” a password from this email client is not a problem. If the victim uses the web interface to read his mailbox, then it is better to use the WebBrowserPassView program. It supports all versions of Windows from 2000 to 10. Older versions like 98 / ME are not supported.
We tested this utility. The program successfully recovered all passwords stored in IE, Firefox, Chrome and Opera browsers (Safari was not tested by us, but we believe that there will be a complete “order” there), see fig. 17. Even if you don’t find the password from the mailbox among this list, this list will also be useful - people often use the same passwords for different services.
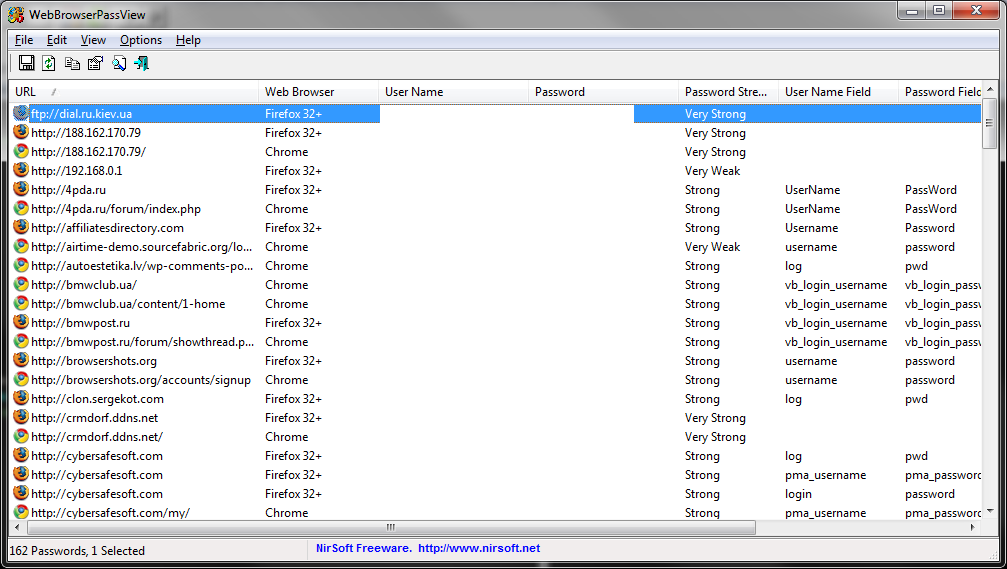
Fig. 17. Recovered Passwords
For convenience, the program allows you to save selected passwords to a text file, which you can then slowly study on your computer.
Since we have already started talking about password recovery, then Dialupass , which restores dialup / RAS / VPN passwords, may be useful to you. The program supports Windows 2000, Windows XP, Windows 2003/2008, Windows Vista, Windows 7, Windows 8 and Windows 10
Efficiency: high
Difficulty: low
Cost: low
About this method did not write just lazy. Much has already been said. It seems to you that this method is not as effective as they say about it? You're wrong.
Most recently, the post of CIA Director John Brennan was hacked . The absurdity of the situation is that the mail was cracked not by an “experienced” hacker, but by an ordinary teenager, having correctly gathered information about his “victim”. The teenager first contacted the mobile operator, posing as a technical support officer, clarified the details of the Brennan account.
After that, he allowed in AOL and, posing as Brennan, asked to reset his password. Since he knew all the necessary information (e-mail account number, last digits of a bank card, 4-digit PIN code, phone number), the password was reset and no one suspected anything.
A little later, Wikileaks published letters from the director of the CIA, see fig. 18.
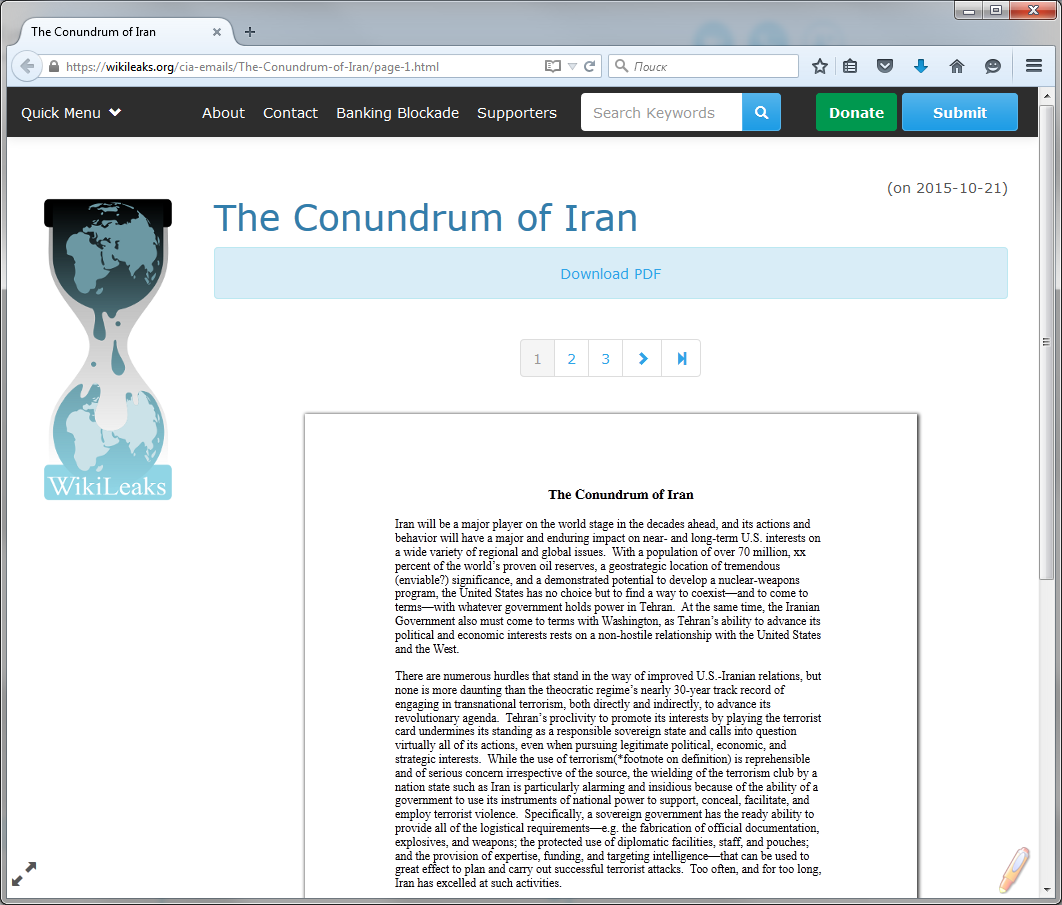
Fig. 18. Letters of the Director of the CIA, published by Wikileaks
The advantage of this method is that you do not need to have any special knowledge and this method can be done by anyone. The success of this method depends on the ingenuity of the “attacker” - whether he can find the necessary information or not.
Efficiency: high
Difficulty: Medium
Cost: low
Ask the user himself to tell us your password. No, this method does not imply physical violence and none of the users will suffer as a result of the experiment. Anyway, physically.
The essence of this method is as follows: you need to create a fake authorization page of the service that you want to hack. For example, if you want to receive a password from GMail.com mail, then you need to create the same login page.
Next you need to lure the user to the fake page. This can be done in several ways:
Very often only the “general direction” is described. We tried to implement it in our own company and see the reaction of ordinary users. The method is quite complicated and its implementation will require both PHP programming skills and some financial investments. After all, we need hosting with PHP support (to execute a PHP script and host an authorization form) and a domain name that is “similar” to the name of the service being hacked. Of course, an experienced user will immediately notice the forgery, but let's see how the most ordinary users will react.
So, we created an authorization form, similar to the Google login form. The result of our suffering is shown in Fig. 19. Of course, it could have been better, but we were in a hurry.
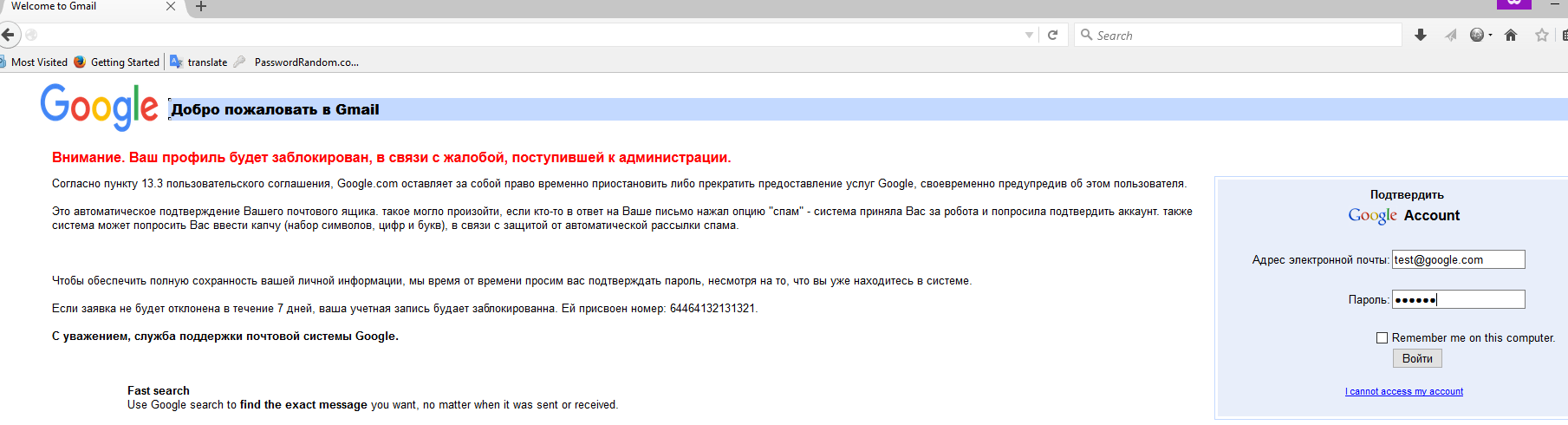
Fig. 19. Login form
Then we sent a message to some employees that their mailbox would be blocked. Please note that the design of the letter even remotely (except for the logo) does not resemble the design used by Google. But, as practice has shown, this was enough for our users. It would be possible to take the source code of the letter, which is sent by Google, to make everything better. In real conditions, the attacker will do just that - be sure of that.
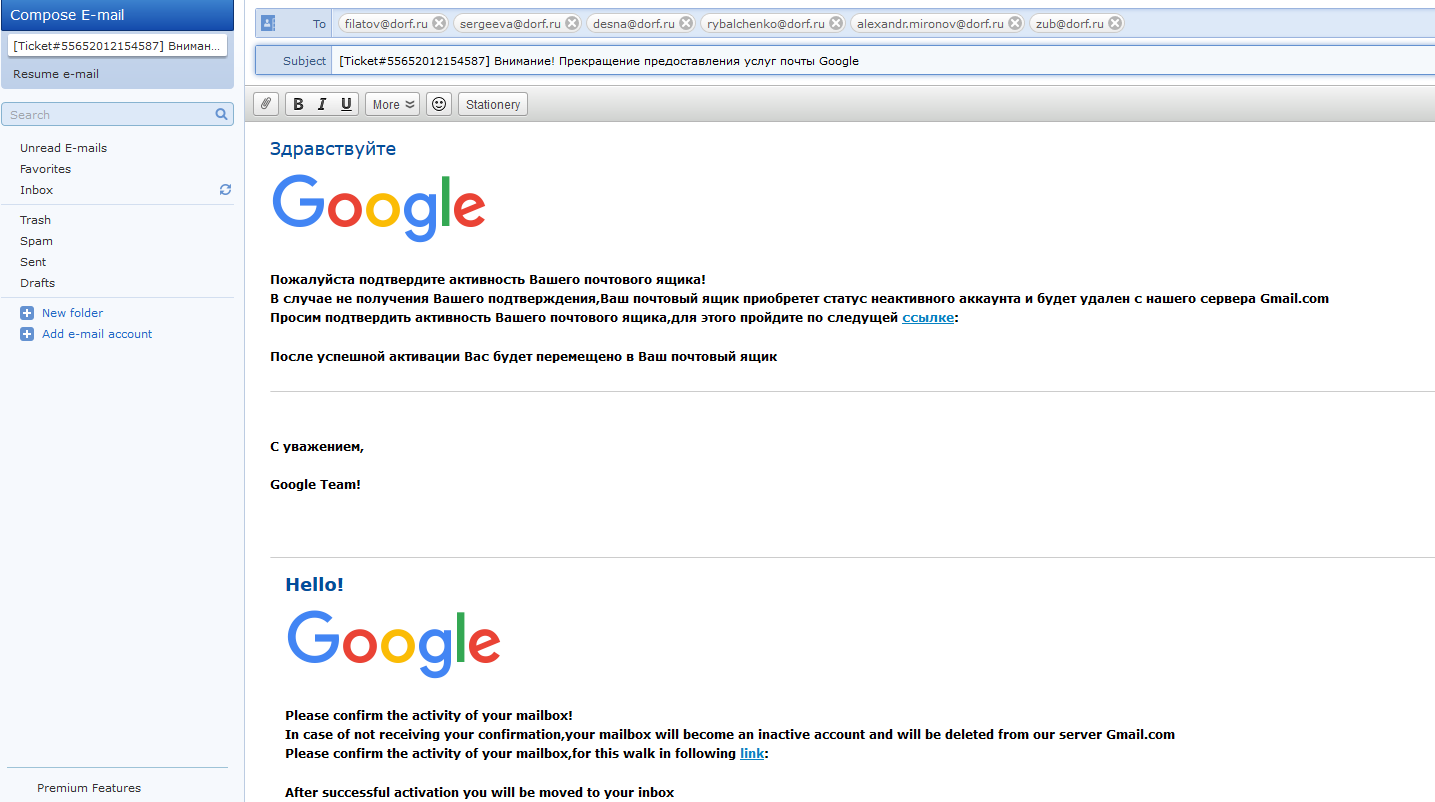
Fig. 20. Letter that we sent to users
What happened next? Then users read the letter, followed the link and naively entered the username and password, which were transferred to the script. The script takes this data and writes it to a text file. Any newcomer to the basics of PHP can write such a script. Sample script code (this is not the script we used) is shown in Listing 1.
Listing 1. The simplest script for writing passwords
The result of our script is shown in Fig. 21.

Fig. 21. Script result
Once again, we note that everything was done in haste. And to send the message, Yahoo! mail was used in order not to fight anti-spam. But one could take a different path. For example, find an SMTP server with free sending of letters (without authorization). Typically, this will be an incorrectly configured SMTP server of some small organization. Lists of such servers are regularly updated on special resources. I think it will not be difficult to find such a list, for example, this one . You can then deploy a web server with PHP support on your local computer. Then you will have access to php.ini and it will be possible to specify the SMTP server through which the mail () function will send letters.
On the other hand, you can try to send a message through your own hosting (it is not necessary to install a local web server). It all depends on its settings. For example, we used our hosting to execute the script for sending our message. On it, the mail () function has been executed without any complaints. It is clear that if you view all the headers of the letter, the “trace” will lead to us. But for us it is not important now. Now it is important that in the mail client the “From” field contains what we need. In the first method, we did just that, that is, we used the mail () function to send a message.
The standard PHP mail function () allows you to easily specify both the text of the letter and its headers. For example:
Emails sent this way passed Google’s antispam (didn’t get into the Spam folder) and were normally displayed, both in the mail client (checked in Outlook and The Bat!) And in the web interface. Of course, before sending a message to the victim, it is better to send it to your mailbox and make sure that the letter is displayed correctly, at least that the email client correctly determines the encoding. If this is not the case, add headers to the $ headers describing the encoding of the letter.
We obtained certain results using this method. Some of the users have left their real passwords. Some did not respond to this email and turned to the administrator. And some have guessed what was the matter and instead of the password entered the abracadabra. Such mediocre results are due to the fact that we did not prepare ourselves and made both the entry form and the letter itself very poor quality. But still we got a few real passwords, so this method works despite all skepticism.
Efficiency: high
Difficulty: High
Cost: High
Now let's try to remember what we never knew - the password from the victim's mailbox. Very often, postal services allow you to recover a forgotten question. And to make sure that the user who is trying to regain access to the mailbox, is his owner, the postal service asks the security question specified when registering the mailbox (Fig. 22). If you are trying to hack into the box of a person you know, then there is a chance that you already know the answer to this question. If you crack a stranger's password, the first thing to do is to study the victim.
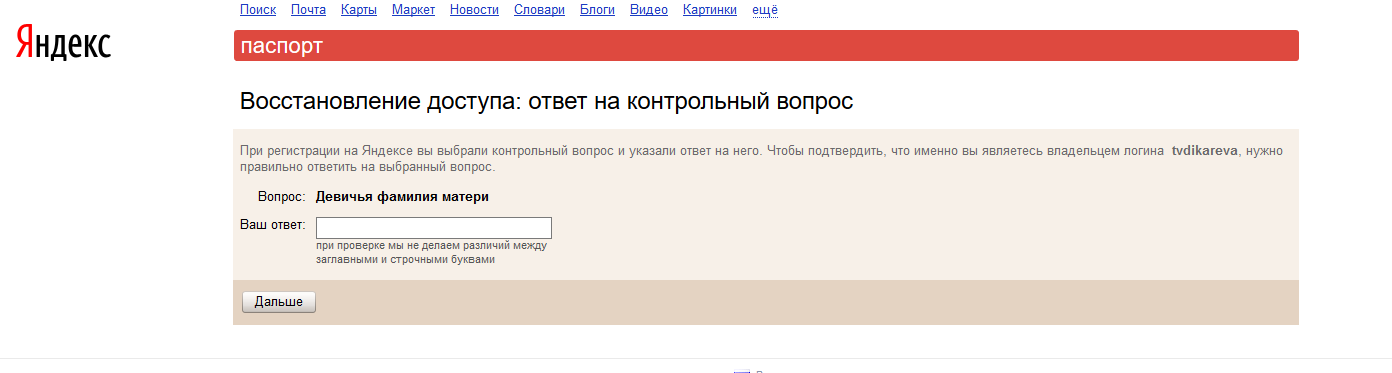
Fig.22. Recovering a password on Yandex.
The more you collect information about the victim, the easier it will be to crack the mailbox. Information can be collected in different ways - you can rub into the trust to the victim and find out, as it were, by chance, the information you need from him (for example, the mother's maiden name, see fig. 22), or you can make friends with the victim's friends. Fortunately, social networks allow you to quickly find not only the victim, but also her friends.
Efficiency: high
Difficulty: Medium
Cost: low
One of the ways to hack email is to use XSS vulnerabilities. But you can hardly call it effective. First, all XSS vulnerabilities found in popular mail services are quickly eliminated. Secondly, taking into account the “first”, it is necessary to look for the XSS vulnerability myself (after all, all the found vulnerabilities are already closed). And the search will take some time. And the implementation of the attack through XSS-vulnerability requires advanced skills. Alternatively, this method can be considered. Especially from academic interest. But if you need to quickly hack mail, the same social engineering will be more effective. If you want to look at hacking using XSS, you can read this article.. It describes how to divert someone else's cookies. If you develop a theme, you can replace your cookies with someone else and get access to someone else's box.
Efficiency: low
Complexity: high
Cost: low
Another good way to access your mailbox is to steal cookies. Of course, it is effective if the victim stores his passwords in the browser. Even if you don’t get your mailbox password, you can get passwords to other services. Users often use the same passwords to access different services. Therefore, if you find a password for one service (for example, a blog, forum), you can try to use it when logging into your email account. There is a chance that he will do.
How to steal cookies? There are various ways - from using a trojan (see fig. 23) to banal copying to a USB flash drive or your FTP if you are at the victim’s computer. Is there an application for obtaining passwords at hand (see method 3)? No problem!You can simply copy the directory from the cookies and analyze on your computer. A variety of utilities can be used to analyze cookies, one of which is CookieSpy , which supports not only installed, but also portable browsers, which allows you to "slip" a program directory with cookies (Figure 24)
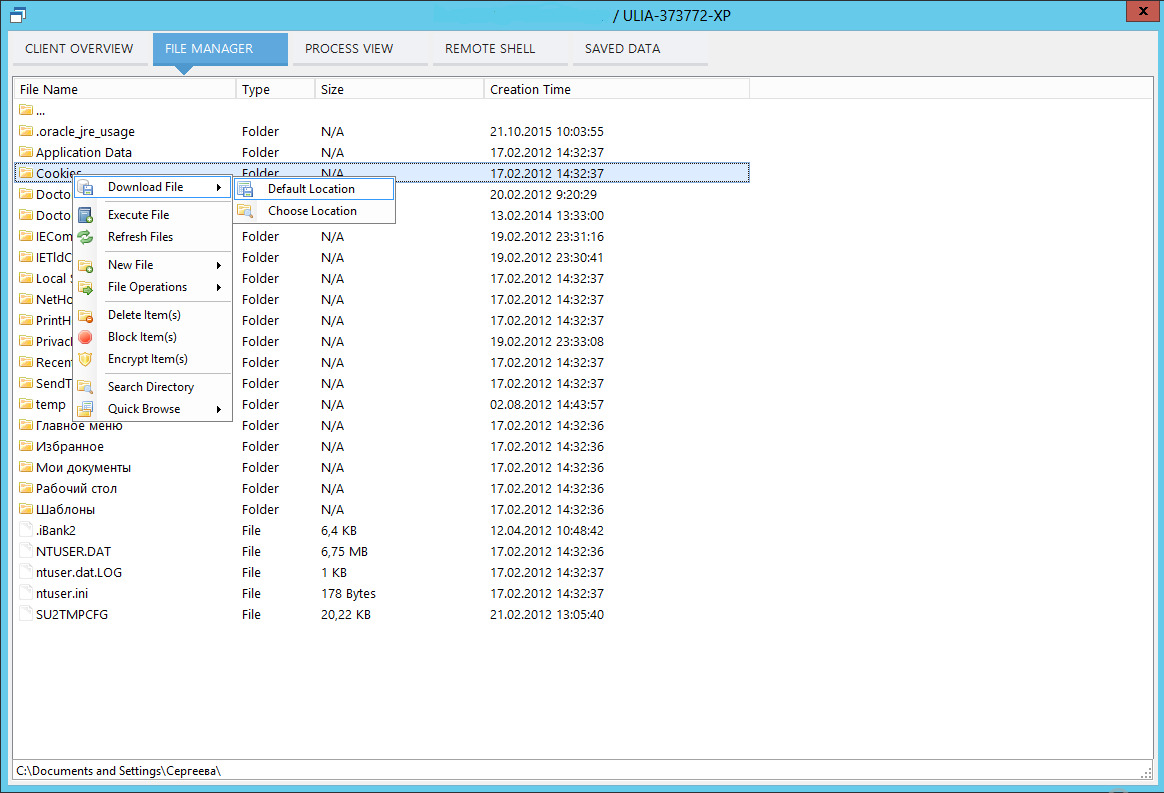
Fig. 23. Theft of cookies using Trojan
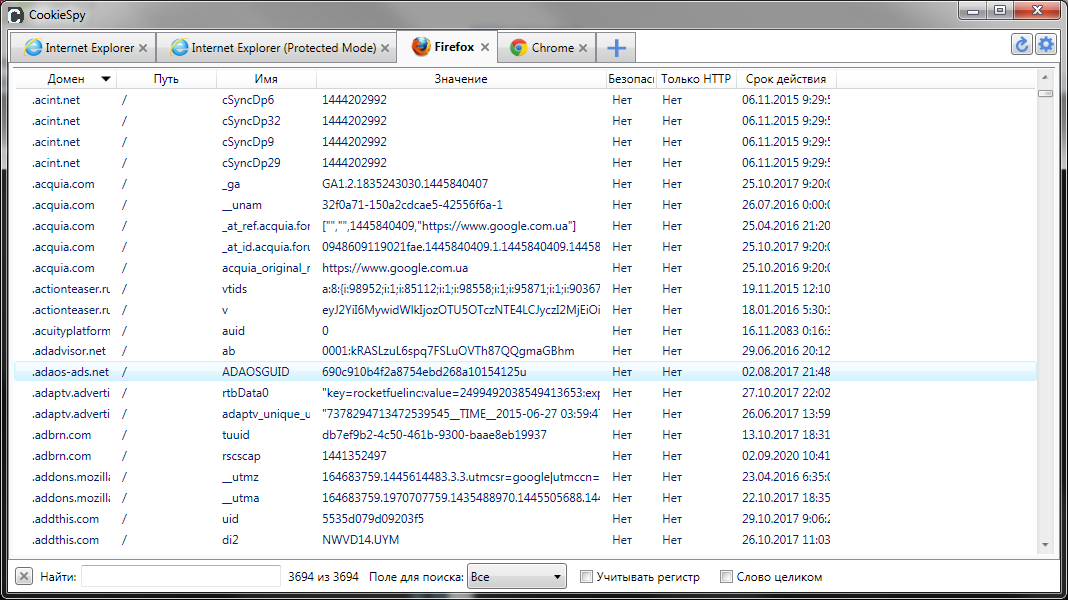
Fig.24. CookieSpy Cookies Analysis
Efficiency: Medium
Difficulty: High
Cost: Low
The most inefficient way. It consists in sorting the password through the list. The program simply tries to pick up a password using the “spear” method (aka the Cauchy method). Of course, under ideal conditions, she will succeed sooner or later. But almost all services will block the mailbox after 3-5 failed attempts. Therefore, it is unlikely that you will be able to use the “brute force method”. If you still want to try, then you can try using the Brutus utility, the use of which is discussed on hackerthreads .
There is one more quite popular utility - THC-Hydrathat allows you to hack a variety of services: Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, S7-300, SAP / R3, SIP, SMB, SMTP, Enum SMTP, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak ( TS2), Telnet, VMware-Auth, VNC and XMPP.
Efficiency: low
Difficulty: Medium
Cost: low
On the Internet, it will not be difficult to find contacts of a “professional” engaged in mail hacking. This is the easiest way. Its effectiveness depends on the correctness of the choice of a specialist. The advantage is that practically everything described in this article will be done for you (maybe a little more, maybe a little less) and you yourself will not have to do anything. The disadvantage is that a “hacker” may turn out to be an elementary scam. As a result, no hacked mailbox, no money. There are even special forums on the Internet where you can easily find a “specialist” (fig. 25). We deliberately erased the address of the forum in order not to make any extra advertising. However, if you wish and have the ability to use a search engine, you can easily find not only this forum, but also hundreds of others like it.

Fig.25. Forum with announcements of mail hacking offers
Efficiency: average
Difficulty: low
Cost: High
Next week, CyberSoft plans to release its plug-in and portable-version of mail encryption, which will take into account all possible hacking methods described in the two previous articles.
Recall that in the first part of our e-mail protection cycle, we considered methods of protection. The second part is devoted to hacking. In this article we will not only tell the theory, but also show the practice of hacking. Methods of hacking mail are shown purely for academic reasons, and we are not responsible for unlawful acts committed by third parties after reading this article. The purpose of the article is to show users and administrators possible hacking options in order to know how to protect against them. We checked the methods described in the article on our employees and the results were very surprised. Therefore, this article can be considered as a guide for the administrator to check email security in the enterprise.

Next will be considered ten different ways to hack a mailbox. Each method has its own efficiency and complexity. The only protection against all methods of hacking is encryption . Even if someone gets access to the mailbox, he is unlikely to be able to read the messages, since all of them (or the most important ones) will be encrypted.
')
Method 1: use a trojan
Quite a common way to gain access to someone else's mailbox is to send emails with built-in viruses. More precisely, the virus is not embedded in the letter itself, and the letter only contains a link to the virus. Typically, the content of the letter should somehow “hook” the user. It should be such that the user can not not respond.
Trojan examples are DarkComet RAT, SpyEye, Carberp. We have already written about DarkComet RAT , it was written about Carberp on Habré. SpyEye is our Russian Trojan, designed by Alexander Panin, who even appeared in the FBI reports.
We used a modified version of the ZeuS Trojan. At the time of creation (10/29/15), no anti-virus was detected by our version (Fig. 1), and it also had the function of disabling processes, including Dr.Web. However, Comodo was installed on the victim's computer - even better.
As a victim, we chose an accountant for our management company, Julia. For the sake of the purity of the experiment, she did not suspect anything that we were going to do. I think this was not worth even talking about.
So, we have a modified ZeuS, but how to make Julia run it? If you just send her a link, I understand the case, she will not go over it. To promise the mountains of gold in a letter is also the last century; users no longer react to this.

Fig. 1. VirusTotal report
Then we decided to send a letter allegedly on behalf of the Federal Tax Service (Fig. 2). We chose that "hook" the victim.

Fig. 2. Letter from tax
So that the From field contains an impressive name, and not xaker134566788@mail.ru, we have forged the letter headers. This is done quite simply, and how exactly it will be shown in method 5. For now, we will not be distracted by this.
As we expected, Julia downloaded the program and launched the update installer of the reporting form (Fig. 3). The installer is made using Inno Setup in 5 minutes. It is he who installs and launches our Trojan.

Fig. 3. Installing Trojan
After that, we can fully control the victim's computer (Fig. 4).

Fig. 4. Managing the victim's computer
What we can? For the sake of interest, we can view a list of computer processes in which, of course, there will not be our Trojan (Fig. 5). We can browse the file system (Fig. 6).

Fig. 5. The list of processes on the victim's computer

Fig. 6. The file system on the victim's computer
Of course, the most important thing for which all this was started was a list of passwords stored in the browser (Fig. 7).

Fig. 7. And here are the passwords
The letter and installer are far from ideal, since everything was done in a hurry. However, our idea was a success. To achieve our goal, we have combined two methods - social engineering and a "fake" letter. Both of these methods will be discussed below.
Efficiency: average
Difficulty: Medium
Cost: low
Method 2: hacking by phone number
The essence of this method is as follows. The attacker needs to know the phone number of the victim, specified when registering the mailbox. When resetting the password, the postal service requires you to enter the last characters of the phone number (or select a phone number from the list). An SMS with a password reset confirmation code will be sent to this number. Then the attacker sends the second SMS with the requirement to specify the code from the previous SMS.
The user, unaware, sends the code from the first SMS. The biggest drawback of this method is that the first SMS will come from Google, and the second from an unknown number. The success of this method depends on the acumen of the victim. Let's look at this method in practice.
The first thing we will try is to just reset the password, after which Google will ask you to enter the password that we remember. Understandably, we do not remember the password, so we press the button. I find it difficult to answer (Fig. 8).

Fig. 8. Password recovery request
Further, if your victim was tied to an Android phone account, then Google will offer to send an alert (Figure 9), which looks like the one shown in Figure. 10. It is remarkable, but the smartphone did not make a single sound, but simply displayed an alert. If he is not in front of the user's eyes, there is a chance that he will not notice him. If the user clicks No, then do not despair - repeat this process several times - later you will understand why.

Fig. 9. Offer to send an alert

Fig. 10. Google Alert
After clicking the Send Alert button, the page shown in Figure 2 will open. 11. Follow the link Reset password in another way. This will open the classic password reset page via SMS code (Fig. 12). The same page will open if there is no Android phone attached to the account.

Fig. 11. Instructions for working with alert

Fig. 12. Sending SMS code
It is the climax. The victim receives a Google confirmation code (Fig. 13).

Fig. 13. Confirmation code
Then you should immediately send another message from another phone:
An attempt to log in to your Google Account has been prevented Send the Google verification code to unlock your account.
In fig. Figure 14 shows how this message looks on the phone screen.

Fig. 14. Message from the attacker
On the one hand, the user can pay attention to an unknown number. On the other hand, put yourself in the place of the average user. First, he receives a password reset notification, then an SMS with a confirmation code, and then a message that suspicious activity has been noticed. Of course, you can complicate things a little and start a short number from which SMS will be sent. Getting a short number with the name of the service, for example, Google Security, is not a problem . This will only increase the likelihood of success.
In our case, everything turned out without a short number. We received an activation code, which was then listed on the password recovery page. Thus, we managed to reset the account password and get access to the mailbox.
Getting access to your mailbox is not everything. To prevent the victim from guessing that her box has been taken away, after resetting the password, you need to create a temporary password and send it by SMS, and in the meantime, forward the password to the “hacker” box. So you can get control of the box without causing special suspicion.

Fig. 15. Setting up forwarding
Efficiency: average
Difficulty: low
Cost: low
Method 3: computer access
If you have access to the victim's computer, you can assume that you have already hacked mail. You can run either a keylogger or a program for “recovering” passwords of mail accounts on a computer.
The essence of the keylogger is that in a special file it records everything that the user enters from the keyboard. You will only have to go to the computer a second time to pick up the resulting file (or receive it by mail).
The advantages of the keylogger include the fact that it records everything. Therefore, in addition to passwords, you can still get a lot of interesting information about your victim. But they have a lot of disadvantages. The most significant - most keyloggers are successfully detected by antiviruses and if antivirus is installed on the victim's computer, the keylogger will not work. It is not always possible to disable the antivirus.
The second disadvantage stems from its dignity. In the resulting file is placed a lot of unnecessary information. It is not enough to collect information from the keyboard, you still need to find among all the excess that you need - a password.
The third drawback is that if the victim uses an email client and not a web interface, then the keylogger will not help at all. Most likely, the password has already been entered into the mail client and is remembered, so the victim does not enter it every time the mail is checked. Consequently, the keylogger will write to the file everything that the user enters, except for what you need.
There is one more drawback - if the selected keylogger does not support sending the resulting file by e-mail, you will have to go to the computer one more time. An example of a keylogger - SniperSpy - in case you want to use it.
Programs for "recovering" passwords of mail accounts allow you to immediately get all the passwords you are interested in without having to read megabytes of text to find the password you need. In addition, the antivirus does not respond to them. One of these programs is Mail PassView . It allows you to recover passwords for the following mail accounts:
- Outlook Express
- Microsoft Outlook 2000 (POP3 and SMTP Accounts only)
- Microsoft Outlook 2002/2003/2007/2010/2013 (POP3, IMAP, HTTP and SMTP Accounts)
- Windows mail
- IncrediMail
- Eudora
- Netscape 6.x / 7.x
- Mozilla thunderbird
- Group Mail Free
- Yahoo! Mail - if the password is stored in the Yahoo! Messenger.
- Hotmail / MSN mail - if the password is stored in MSN Messenger.
- Gmail - if your password is saved in Gmail Notifier, Google Desktop, or Google Talk applications.
We checked the program on our computers and declare that it works (Fig. 16). In fig. 16 passwords, as well as e-mail addresses are overwritten for obvious reasons.

Fig. 16. Mail PassView
Mail PassView is not the only program of its kind. There are other programs:
- Outlook Password Decryptor - allows you to recover passwords from Outlook, including the latest versions (Outlook 2015, running under Windows 10);
- PstPassword - another program to recover passwords stored in Outlook;
- WebBrowserPassView - a program to recover passwords stored in the browser. Supported browsers are IE, Chrome, Opera, Safari, Firefox.
All that is needed is to know which email client uses the victim. Finding a program to “recover” a password from this email client is not a problem. If the victim uses the web interface to read his mailbox, then it is better to use the WebBrowserPassView program. It supports all versions of Windows from 2000 to 10. Older versions like 98 / ME are not supported.
We tested this utility. The program successfully recovered all passwords stored in IE, Firefox, Chrome and Opera browsers (Safari was not tested by us, but we believe that there will be a complete “order” there), see fig. 17. Even if you don’t find the password from the mailbox among this list, this list will also be useful - people often use the same passwords for different services.

Fig. 17. Recovered Passwords
For convenience, the program allows you to save selected passwords to a text file, which you can then slowly study on your computer.
Since we have already started talking about password recovery, then Dialupass , which restores dialup / RAS / VPN passwords, may be useful to you. The program supports Windows 2000, Windows XP, Windows 2003/2008, Windows Vista, Windows 7, Windows 8 and Windows 10
Efficiency: high
Difficulty: low
Cost: low
Method 4: social engineering
About this method did not write just lazy. Much has already been said. It seems to you that this method is not as effective as they say about it? You're wrong.
Most recently, the post of CIA Director John Brennan was hacked . The absurdity of the situation is that the mail was cracked not by an “experienced” hacker, but by an ordinary teenager, having correctly gathered information about his “victim”. The teenager first contacted the mobile operator, posing as a technical support officer, clarified the details of the Brennan account.
After that, he allowed in AOL and, posing as Brennan, asked to reset his password. Since he knew all the necessary information (e-mail account number, last digits of a bank card, 4-digit PIN code, phone number), the password was reset and no one suspected anything.
A little later, Wikileaks published letters from the director of the CIA, see fig. 18.

Fig. 18. Letters of the Director of the CIA, published by Wikileaks
The advantage of this method is that you do not need to have any special knowledge and this method can be done by anyone. The success of this method depends on the ingenuity of the “attacker” - whether he can find the necessary information or not.
Efficiency: high
Difficulty: Medium
Cost: low
Method 5: gullible users (phishing)
Ask the user himself to tell us your password. No, this method does not imply physical violence and none of the users will suffer as a result of the experiment. Anyway, physically.
The essence of this method is as follows: you need to create a fake authorization page of the service that you want to hack. For example, if you want to receive a password from GMail.com mail, then you need to create the same login page.
Next you need to lure the user to the fake page. This can be done in several ways:
- Send him a message allegedly on behalf of the administration of the service. In the message indicate something like "You have not been in your mailbox for a long time. If you do not use it before <D>. <M>. <T>, it will be deleted. ”. We draw a login button, clicking which the user gets on your login page.
- Send a message with a link that should interest the user. When he goes through it, he will see a message about the need to login to view the contents. Now many services allow you to log in using a GMail account or one of the social networks. So the user can not suspect anything.
Very often only the “general direction” is described. We tried to implement it in our own company and see the reaction of ordinary users. The method is quite complicated and its implementation will require both PHP programming skills and some financial investments. After all, we need hosting with PHP support (to execute a PHP script and host an authorization form) and a domain name that is “similar” to the name of the service being hacked. Of course, an experienced user will immediately notice the forgery, but let's see how the most ordinary users will react.
So, we created an authorization form, similar to the Google login form. The result of our suffering is shown in Fig. 19. Of course, it could have been better, but we were in a hurry.

Fig. 19. Login form
Then we sent a message to some employees that their mailbox would be blocked. Please note that the design of the letter even remotely (except for the logo) does not resemble the design used by Google. But, as practice has shown, this was enough for our users. It would be possible to take the source code of the letter, which is sent by Google, to make everything better. In real conditions, the attacker will do just that - be sure of that.

Fig. 20. Letter that we sent to users
What happened next? Then users read the letter, followed the link and naively entered the username and password, which were transferred to the script. The script takes this data and writes it to a text file. Any newcomer to the basics of PHP can write such a script. Sample script code (this is not the script we used) is shown in Listing 1.
Listing 1. The simplest script for writing passwords
<? php
// entered login
$ login = $ _POST ['Login'];
// user browser
$ browser = getenv ("HTTP_USER_AGENT");
// Password
$ pass = $ _POST ['password'];
// Write the data
$ text = "Login = $ login \ nPassword = $ pass \ nBrowser = $ browser";
// open the file
$ filelog = fopen ("log.txt", "a +");
// write the string
fwrite ($ filelog, "\ n $ text \ n");
fclose ($ filelog); // close
// redirect the user to the google login page to
// less suspicion
header ('Location: https://accounts.google.com/ServiceLogin?service=mail&passive=true&rm=false&continue=https://mail.google.com/mail/&ss=1&scc=1<mpl=default<mplcache=2&emr = 1 & osid = 1 # identifier ');
?>
The result of our script is shown in Fig. 21.

Fig. 21. Script result
Once again, we note that everything was done in haste. And to send the message, Yahoo! mail was used in order not to fight anti-spam. But one could take a different path. For example, find an SMTP server with free sending of letters (without authorization). Typically, this will be an incorrectly configured SMTP server of some small organization. Lists of such servers are regularly updated on special resources. I think it will not be difficult to find such a list, for example, this one . You can then deploy a web server with PHP support on your local computer. Then you will have access to php.ini and it will be possible to specify the SMTP server through which the mail () function will send letters.
On the other hand, you can try to send a message through your own hosting (it is not necessary to install a local web server). It all depends on its settings. For example, we used our hosting to execute the script for sending our message. On it, the mail () function has been executed without any complaints. It is clear that if you view all the headers of the letter, the “trace” will lead to us. But for us it is not important now. Now it is important that in the mail client the “From” field contains what we need. In the first method, we did just that, that is, we used the mail () function to send a message.
The standard PHP mail function () allows you to easily specify both the text of the letter and its headers. For example:
$ headers = 'From: Federal Tax Service <no-reply@nalog.ru>'. "\ r \ n".
'Reply-To: no-reply@nalog.ru'. "\ r \ n";
mail ($ to, $ subject, $ message, $ headers);
$ headers = 'From: Google <no-reply@accounts.google.com>'. "\ r \ n".
'Reply-To: no-reply@accounts.google.com'. "\ r \ n";
mail ($ to, $ subject, $ message, $ headers);
Emails sent this way passed Google’s antispam (didn’t get into the Spam folder) and were normally displayed, both in the mail client (checked in Outlook and The Bat!) And in the web interface. Of course, before sending a message to the victim, it is better to send it to your mailbox and make sure that the letter is displayed correctly, at least that the email client correctly determines the encoding. If this is not the case, add headers to the $ headers describing the encoding of the letter.
We obtained certain results using this method. Some of the users have left their real passwords. Some did not respond to this email and turned to the administrator. And some have guessed what was the matter and instead of the password entered the abracadabra. Such mediocre results are due to the fact that we did not prepare ourselves and made both the entry form and the letter itself very poor quality. But still we got a few real passwords, so this method works despite all skepticism.
Efficiency: high
Difficulty: High
Cost: High
Method 6: we study the victim and “remember” the password
Now let's try to remember what we never knew - the password from the victim's mailbox. Very often, postal services allow you to recover a forgotten question. And to make sure that the user who is trying to regain access to the mailbox, is his owner, the postal service asks the security question specified when registering the mailbox (Fig. 22). If you are trying to hack into the box of a person you know, then there is a chance that you already know the answer to this question. If you crack a stranger's password, the first thing to do is to study the victim.

Fig.22. Recovering a password on Yandex.
The more you collect information about the victim, the easier it will be to crack the mailbox. Information can be collected in different ways - you can rub into the trust to the victim and find out, as it were, by chance, the information you need from him (for example, the mother's maiden name, see fig. 22), or you can make friends with the victim's friends. Fortunately, social networks allow you to quickly find not only the victim, but also her friends.
Efficiency: high
Difficulty: Medium
Cost: low
Method 7: XSS vulnerabilities
One of the ways to hack email is to use XSS vulnerabilities. But you can hardly call it effective. First, all XSS vulnerabilities found in popular mail services are quickly eliminated. Secondly, taking into account the “first”, it is necessary to look for the XSS vulnerability myself (after all, all the found vulnerabilities are already closed). And the search will take some time. And the implementation of the attack through XSS-vulnerability requires advanced skills. Alternatively, this method can be considered. Especially from academic interest. But if you need to quickly hack mail, the same social engineering will be more effective. If you want to look at hacking using XSS, you can read this article.. It describes how to divert someone else's cookies. If you develop a theme, you can replace your cookies with someone else and get access to someone else's box.
Efficiency: low
Complexity: high
Cost: low
Method 8: Cookies Theft
Another good way to access your mailbox is to steal cookies. Of course, it is effective if the victim stores his passwords in the browser. Even if you don’t get your mailbox password, you can get passwords to other services. Users often use the same passwords to access different services. Therefore, if you find a password for one service (for example, a blog, forum), you can try to use it when logging into your email account. There is a chance that he will do.
How to steal cookies? There are various ways - from using a trojan (see fig. 23) to banal copying to a USB flash drive or your FTP if you are at the victim’s computer. Is there an application for obtaining passwords at hand (see method 3)? No problem!You can simply copy the directory from the cookies and analyze on your computer. A variety of utilities can be used to analyze cookies, one of which is CookieSpy , which supports not only installed, but also portable browsers, which allows you to "slip" a program directory with cookies (Figure 24)

Fig. 23. Theft of cookies using Trojan

Fig.24. CookieSpy Cookies Analysis
Efficiency: Medium
Difficulty: High
Cost: Low
Method 9: bruteforce
The most inefficient way. It consists in sorting the password through the list. The program simply tries to pick up a password using the “spear” method (aka the Cauchy method). Of course, under ideal conditions, she will succeed sooner or later. But almost all services will block the mailbox after 3-5 failed attempts. Therefore, it is unlikely that you will be able to use the “brute force method”. If you still want to try, then you can try using the Brutus utility, the use of which is discussed on hackerthreads .
There is one more quite popular utility - THC-Hydrathat allows you to hack a variety of services: Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, S7-300, SAP / R3, SIP, SMB, SMTP, Enum SMTP, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak ( TS2), Telnet, VMware-Auth, VNC and XMPP.
Efficiency: low
Difficulty: Medium
Cost: low
Method 10: Turn to professionals
On the Internet, it will not be difficult to find contacts of a “professional” engaged in mail hacking. This is the easiest way. Its effectiveness depends on the correctness of the choice of a specialist. The advantage is that practically everything described in this article will be done for you (maybe a little more, maybe a little less) and you yourself will not have to do anything. The disadvantage is that a “hacker” may turn out to be an elementary scam. As a result, no hacked mailbox, no money. There are even special forums on the Internet where you can easily find a “specialist” (fig. 25). We deliberately erased the address of the forum in order not to make any extra advertising. However, if you wish and have the ability to use a search engine, you can easily find not only this forum, but also hundreds of others like it.

Fig.25. Forum with announcements of mail hacking offers
Efficiency: average
Difficulty: low
Cost: High
Next week, CyberSoft plans to release its plug-in and portable-version of mail encryption, which will take into account all possible hacking methods described in the two previous articles.
Source: https://habr.com/ru/post/269829/
All Articles