Vulnerabilities in Plategka.com service including XSS
I am interested in payment services, banks, plastic cards, and in general I follow e-commerce. And I also like to find errors and vulnerabilities in the systems of Internet banking, payment terminals or in online transfer systems .
Not so long ago, one Ukrainian online payment service, Plategka.com , launched a function: creating a link with a unique address and a QR code for receiving a transfer to a card.
As soon as I wanted to check how the new service works, I saw the same mistake that Portmone made: the link indicates the full card number. Going through the links, you can collect card numbers. " Initially, we thought about hiding the card number, but this issue has its pros and cons, so at the first stage, so that Payer had the opportunity to verify the accuracy of the data already entered, we decided to leave it, " they write to the user .
')

But the fact of having a full card number is aggravated by the fact that, for the convenience of the payer, the name and surname of the recipient is indicated.
Total: you can collect full numbers + full names of cardholders ( I just indicated the first letters of the Latin alphabet ).
I immediately informed the company about this mistake, they corrected the display of the full card number fairly quickly and even thanked me with a sum of ... 200 hryvnia ($ 8.5). Well…
After a couple of days, finding free time, I went to the site again. And, since initially during the registration I indicated in the fields “last name” and “name” not quite correct data, this time I decided to see whether it is possible to indicate two words in these fields.
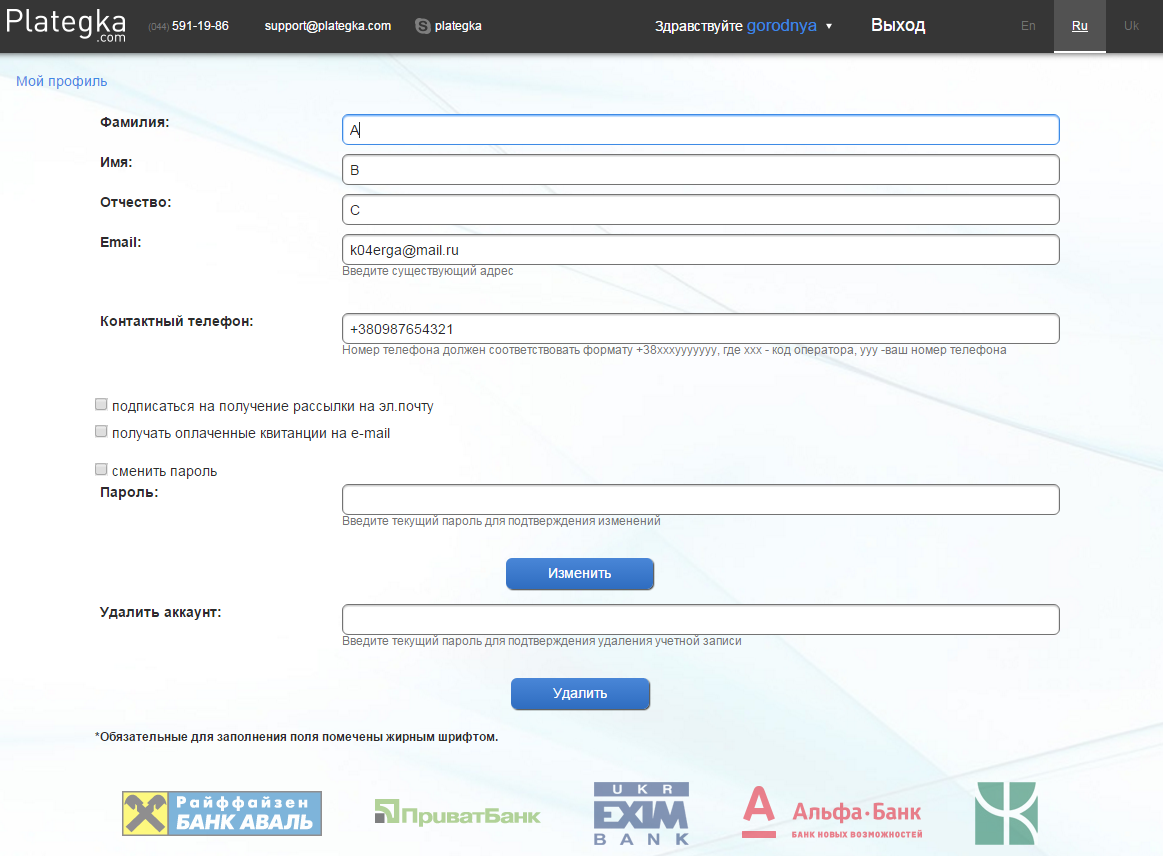
(the phone number is not mine)
Two words could be specified.
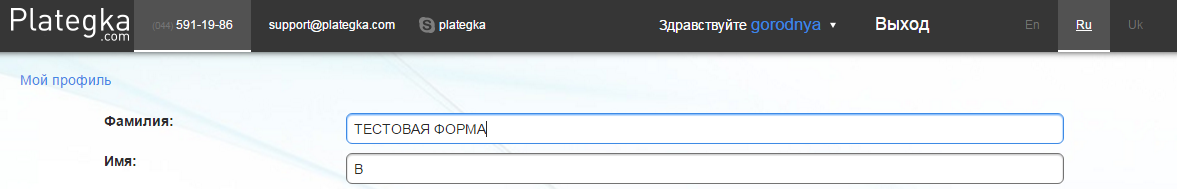
It was possible to specify and more.
It turned out the following:

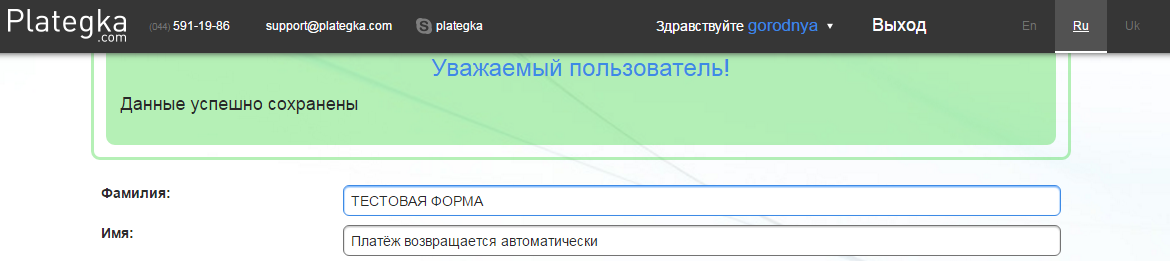
What if you add a line break
However, the developers also forgot to take this into account - the system accepted and “correctly” displayed both the line break and the font color change:

With this form, fraudsters can collect money for a long time from gullible users. Especially if you set the psychologically correct text. By the way, the service allows you to "book" the address of the link. Naturally, I tried and created links of the form:
other.
Well, I could not help trying to insert in any field.
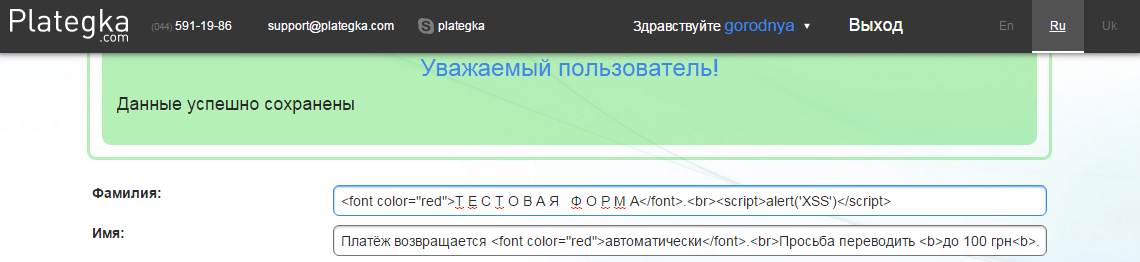
And, unfortunately, the service and my happiness, the code was executed:
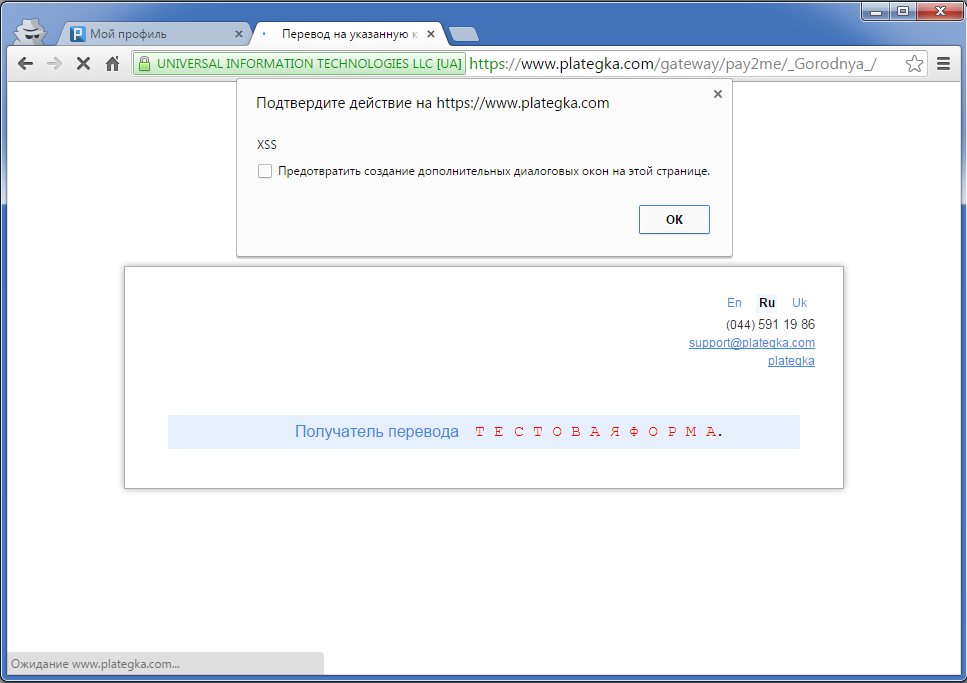
Well, business was not limited to HTML code, right there and XSS.
I sent a message to the company, indicating that these errors are more serious than previous ones. I was thanked and I received a reward. Reward, attention, in the amount of ... again 200 (!) Hryvnia!
I understand that not all companies allow payments for found vulnerabilities, but
eight and a half dollars for xss ?
Not so long ago, one Ukrainian online payment service, Plategka.com , launched a function: creating a link with a unique address and a QR code for receiving a transfer to a card.
As soon as I wanted to check how the new service works, I saw the same mistake that Portmone made: the link indicates the full card number. Going through the links, you can collect card numbers. " Initially, we thought about hiding the card number, but this issue has its pros and cons, so at the first stage, so that Payer had the opportunity to verify the accuracy of the data already entered, we decided to leave it, " they write to the user .
')

But the fact of having a full card number is aggravated by the fact that, for the convenience of the payer, the name and surname of the recipient is indicated.
Total: you can collect full numbers + full names of cardholders ( I just indicated the first letters of the Latin alphabet ).
I immediately informed the company about this mistake, they corrected the display of the full card number fairly quickly and even thanked me with a sum of ... 200 hryvnia ($ 8.5). Well…
After a couple of days, finding free time, I went to the site again. And, since initially during the registration I indicated in the fields “last name” and “name” not quite correct data, this time I decided to see whether it is possible to indicate two words in these fields.

(the phone number is not mine)
Two words could be specified.
It was possible to specify and more.

It turned out the following:

What if you add a line break
However, the developers also forgot to take this into account - the system accepted and “correctly” displayed both the line break and the font color change:

With this form, fraudsters can collect money for a long time from gullible users. Especially if you set the psychologically correct text. By the way, the service allows you to "book" the address of the link. Naturally, I tried and created links of the form:
www.plategka.com/gateway/pay2me www.plategka.com/gateway/pay2me admin /www.plategka.com/gateway/pay2me www.plategka.com/gateway/pay2me login /www.plategka.com/gateway/pay2me www.plategka.com/gateway/pay2me test /other.
Spoiler
Now my links with the description “Link owner account is blocked” are inactive, but this is not due to the “Billing” actions, but because I deleted one account and created another during the checkout, and the system does not allow the new user to create a link with the released word . Those. The old link can not be deleted / changed, a new one can also be created.
Well, I could not help trying to insert in any field.

And, unfortunately, the service and my happiness, the code was executed:

Well, business was not limited to HTML code, right there and XSS.
I sent a message to the company, indicating that these errors are more serious than previous ones. I was thanked and I received a reward. Reward, attention, in the amount of ... again 200 (!) Hryvnia!
I understand that not all companies allow payments for found vulnerabilities, but
eight and a half dollars for xss ?
Source: https://habr.com/ru/post/269663/
All Articles