HackerSIM: Debriefing

Recently, many articles ( 1 , 2 , 3 , 4 , 5 , 6 , 7 ) have appeared on Habré and Hiktaimes about a SIM card endowed with unprecedented and unheard of possibilities, which has caused concern and interest in various circles. There was a lot of skepticism and controversy, and then various theories, sometimes amazing for its fantastic. Let's try to open the veil of secrecy from the technical side. Naturally, these tests would not have been possible without this SIM card, which MagisterLudi kindly provided us.
For those who do not want to read many letters, I summarize: there is no forced encryption, there is no protection against interception complexes, there is no connection to the second level of the BS signal, there is a number substitution, there is a voice substitution, there is no billing, there is no IMSI hiding .
')
Let's start in order.
First disappointment
There is no Anonymus logo on the SIM card, which was depicted in the very first article . Here’s what HackerSIM actually looks like:

Here we decided not to continue the study - after all, the logo was the main feature.

Whose is she?
The ICCID of the SIM card (printed on it) tells us the following:
We insert the SIM card into the phone, and the first thing we see is that we are roaming, connected to the MTS, and the third line, which is impossible not to pay attention: AY Security - it immediately says whose SIM it really is : www.aysecurity.co.uk/ru/aysim.html

Interestingly, but in a modern phone completely different information is displayed (it remains a mystery, which means “GT”)

The site claimed the following "unique" features:
- caller ID replacement,
- force encryption
- protection from interception systems,
- voice substitution
- cost optimization
- hiding the real IMSI,
- hide real location
- virtual number.
The first and fourth points have already been actively discussed at Habré, so we will not touch them, but try to understand the rest, much more "muddy."
Force encryption
“This function prohibits your SIM card from reducing the level of encryption and forces you to ignore commands from operators or interception complexes to disable the encryption key generation algorithm (A8) stored in the SIM module. Thus, all your conversations are encrypted using the A5.1 algorithm. ”
In fact, initially the entire transfer is carried out without the use of encryption, and the inclusion of encryption is carried out on command from the operator Ciphering Mode Command. Here is an example from a real network (using HackerSIM):
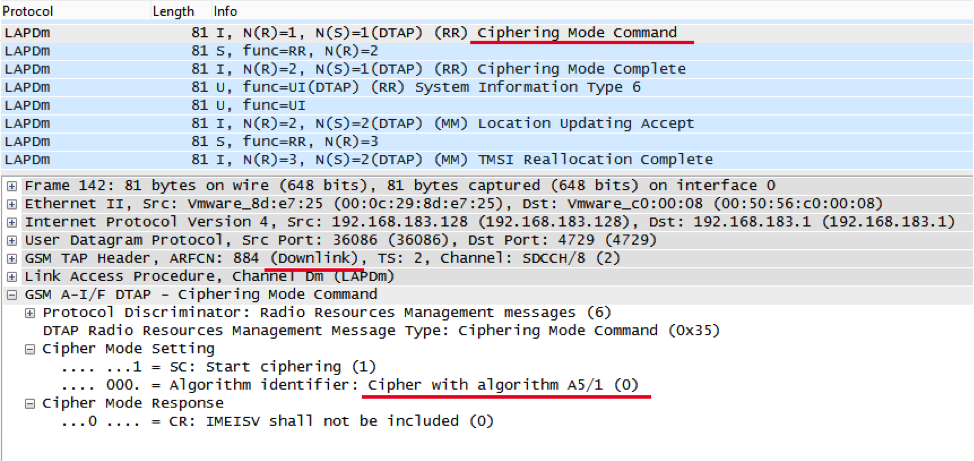
However, this also works on all other SIMs, since encryption is usually used in all Russian networks. To check the "ban" of work without encryption, connect to OpenBTS and try to call:
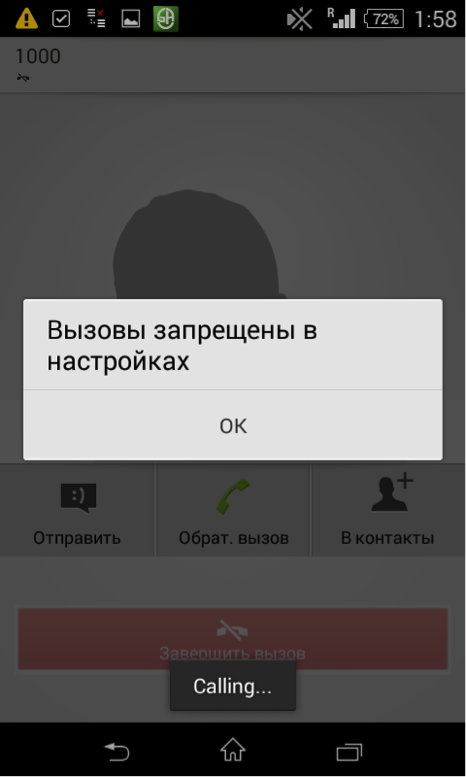
At first, it really seems that the SIM card somehow proclaimed that there is no encryption, and blocked the call. (But in reality, everything is not so, about this below, and pay attention to the “Calling ...” window at the bottom of the screen.) However, if you try to call several times in a row (in our case three times), the call passes:
Incoming calls go without problems and the conversation also happens without problems:

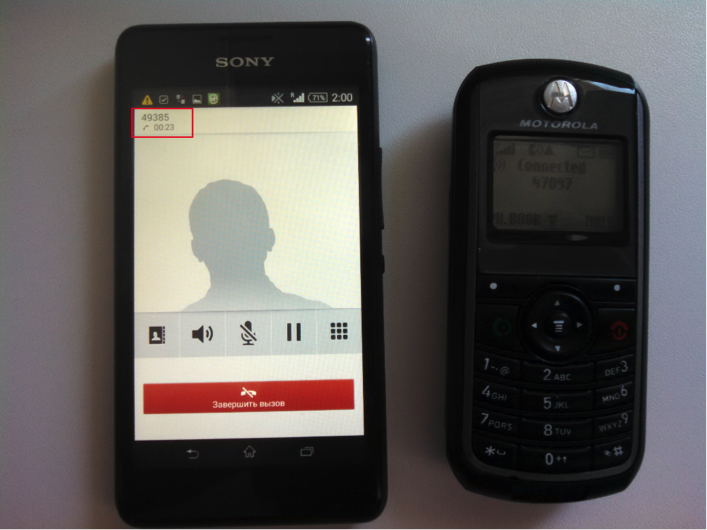
It is worth noting: the manufacturer claims that it is for the voice that there is a ban on the lack of encryption; in a fake network without encryption, both incoming and outgoing SMS are transmitted without problems.
Protection against interception complexes
This function allows the subscriber to become invisible for mobile interception complexes. The principle of the interception complex is based on the substitution of a real base station, thus, becoming, in fact, a priority for all phones within its radius of action. A phone with our software package ignores the bases with the highest signal level.
Generally speaking, the phone chooses not by the signal level, but by the C2 parameter, which depends on the current signal level, on the minimum acceptable signal for this BS and on the BS priority. Therefore, the very idea that it saves from a fake BS is a delusion. For example, OpenBTS, deployed on SDR, has a power of about 100 mW, which is less than the phone itself can (up to 1 W), and much less than a standard base station. Thus, interception is achieved not by a high power level, but by a high priority. And the fact that the phone uses a less powerful BS means only that its priority is higher.
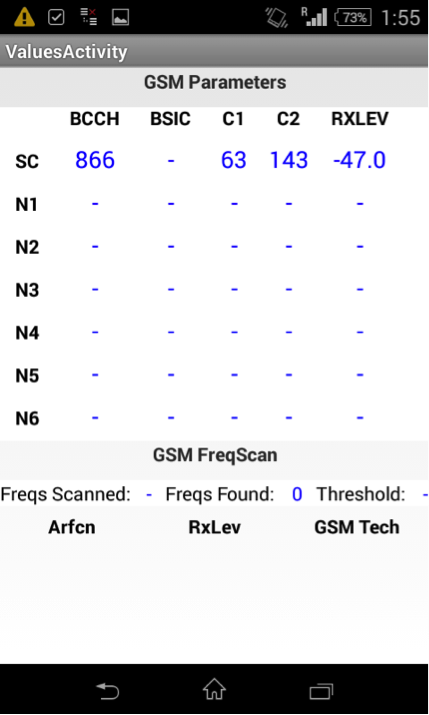
To measure power, parameters C1 and C2, we used the Greenhead app.
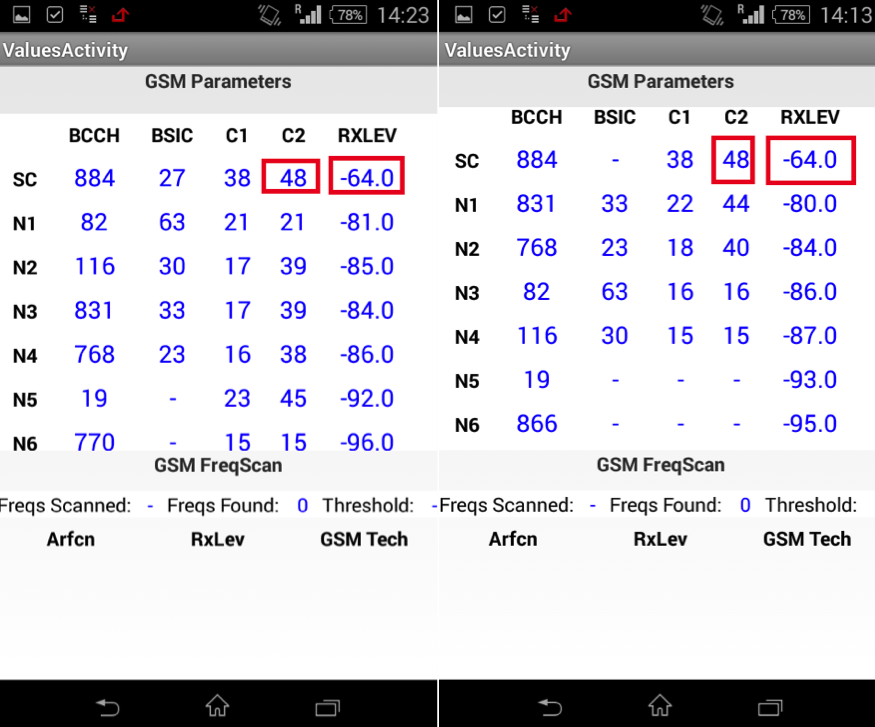
Well, some screenshots - a list of neighbor and serving channels (BCCH - arfcn, SC - serving cell, N1 - neigbour cell 1, etc.).
1. HackerSIM on the most powerful and highest priority BS
2. HackerSIM on not the most powerful, but the most priority BS
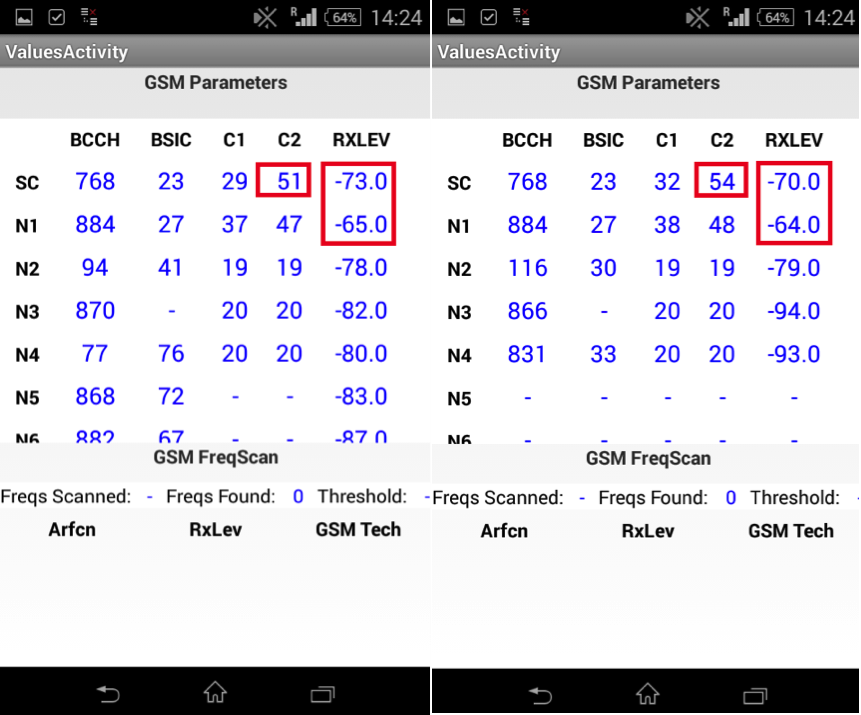
3. We turn on the "interception complex", and ... HackerSIM quietly connects to it, although, to be precise, this phone connects, since the SIM card does not control the cell selection, and HackerSIM is not an exception:
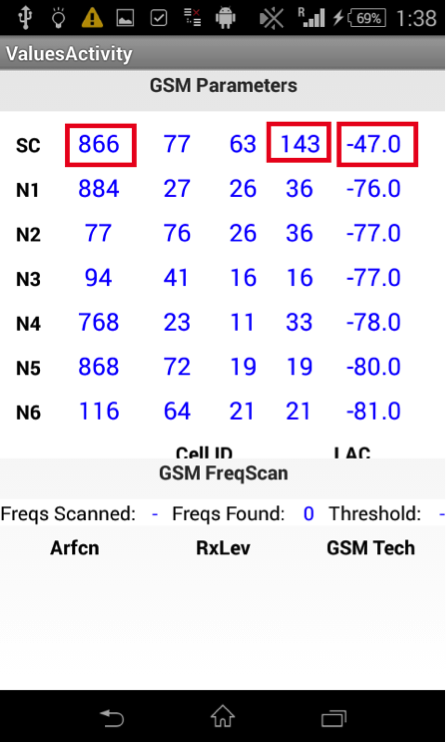
4. By capturing the phone, the fake network no longer reports its neighbors, so the phone has no choice but to be in the fake network as long as the attacker wishes, or until he leaves the area of its operation:
Cost optimization
This item sounds very original, taking into account the cost of both the SIM-card and its service.
Hiding the real IMSI. Hiding the real location. Lack of billing. Virtual number
No billing is declared, and that is why it is supposedly impossible to track this subscriber. However, if there is no billing, who issues this information?
Location tracking is carried out through the SS7 network using the attacks described by us [http://www.ptsecurity.ru/download/PT_SS7_security_2014_rus.pdf]. It’s enough to know the subscriber’s IMSI. Usually they recognize him by phone number; we do not know the phone number of our HackerSIM, and according to the instructions from the site, it for some reason is not shown to us (there must be another DID by which we can call):
We cannot verify the “virtuality” of this number, because we do not know it. But IMSI can be learned from the radio, for example, when you connect your phone to the network:
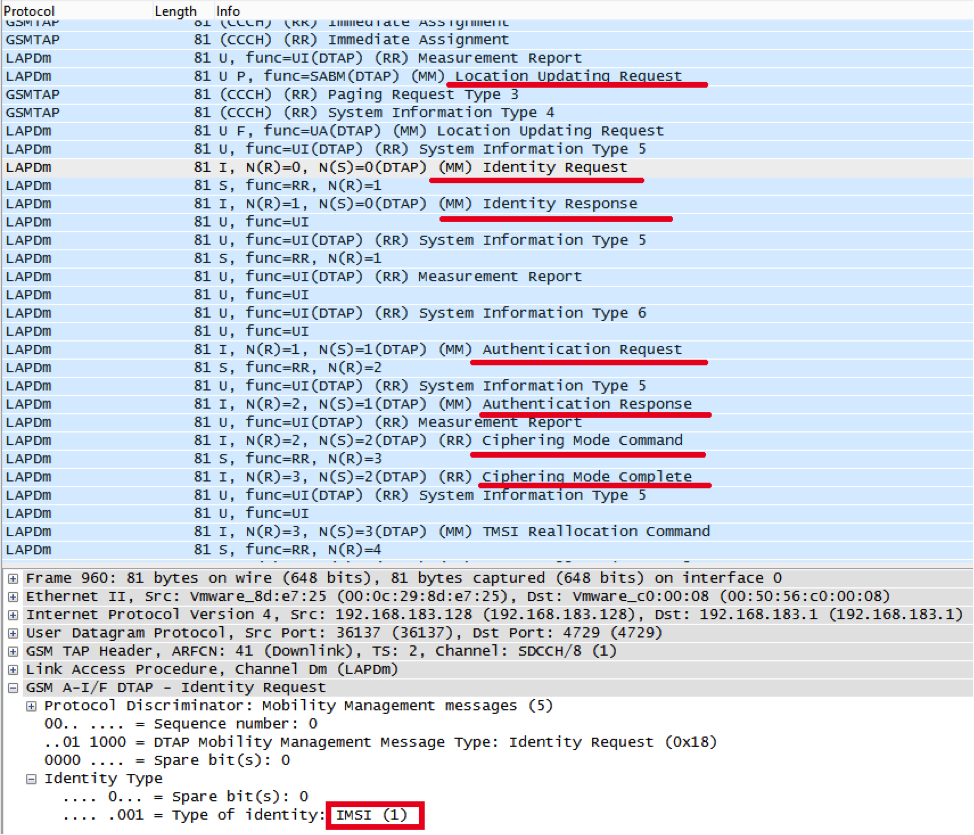
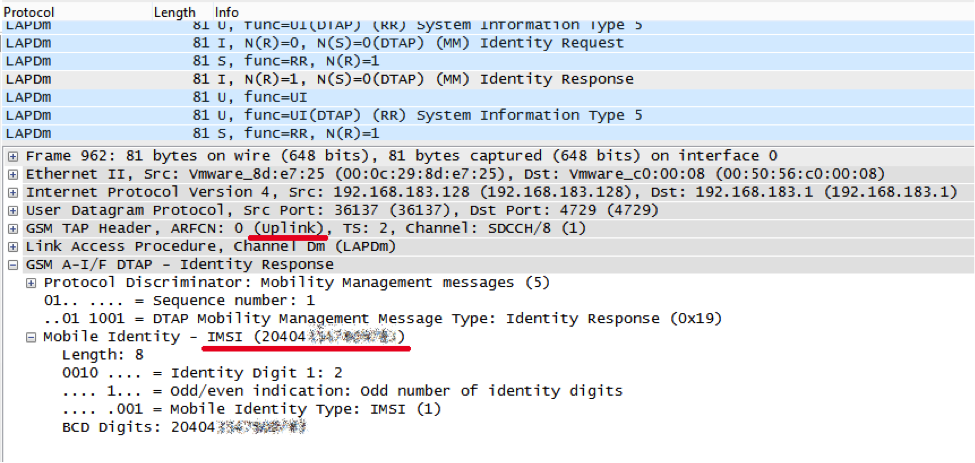
The phone sends the Location Update Request, the network requests the IMSI (Identity Request), the phone speaks its IMSI (Identity Response), then the session keys (Authentication Request and Authentication Response) are generated, and then the encryption command is received. In other words, IMSI can be intercepted in the radio network, even without breaking the encryption, but it cannot be otherwise: this is how the cellular network works.
There is one more unsolved point mentioned on Habré. When registering a phone in a roaming network, a request is made to the home network, but then all calls must pass through the guest network. So how do all outgoing calls go through a PBX? The answer is original, but simple enough.
When we tried to call through the Motorola C118, the call was dropped, and no one returned the call. The same is true when using the mobile utility from the osmocom-bb package:
By the way, SMS is reset with an even more interesting reason:

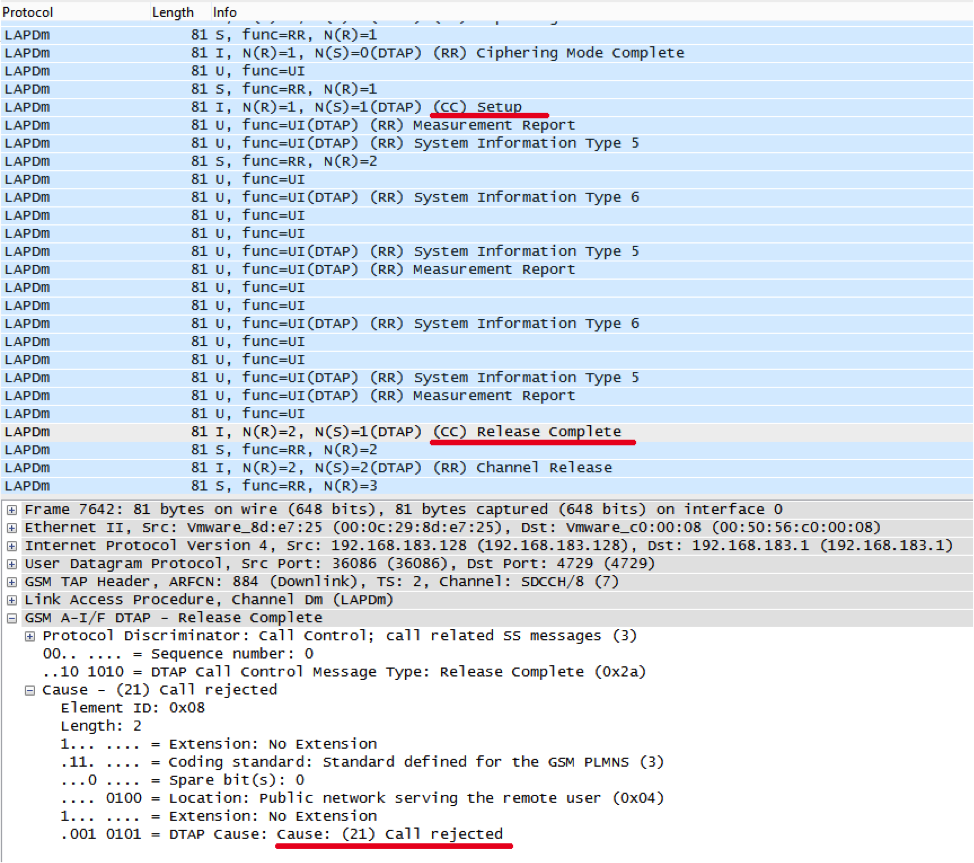
But let us return to the question of why in the old Motorola the outgoing call does not work, and in the modern phone it is dropped, and then the PBX calls back. Radio dump reveals the secret:
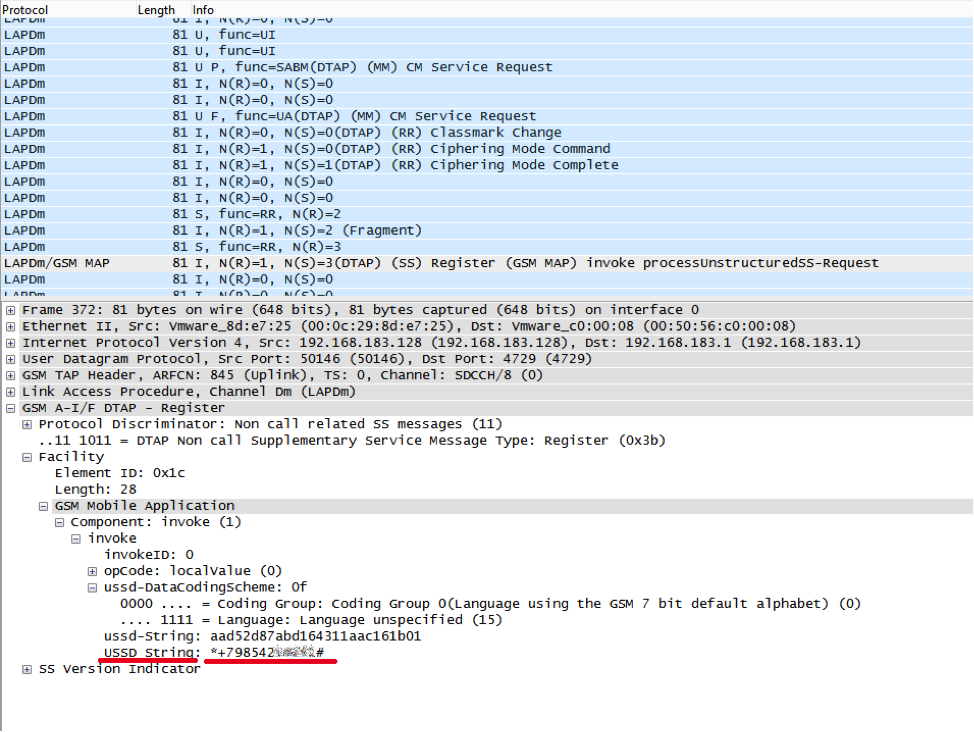
When an outgoing call instead of a call setup message (Setup), the phone sends USSD with the number of the called subscriber, who has been walking around the world for a long time, getting to the home of the Netherlands, then a USSD answer comes with a simple Calling start phrase, and then the incoming call is received with the usual sequence Setup, Call Confirmed, Assigned Command.
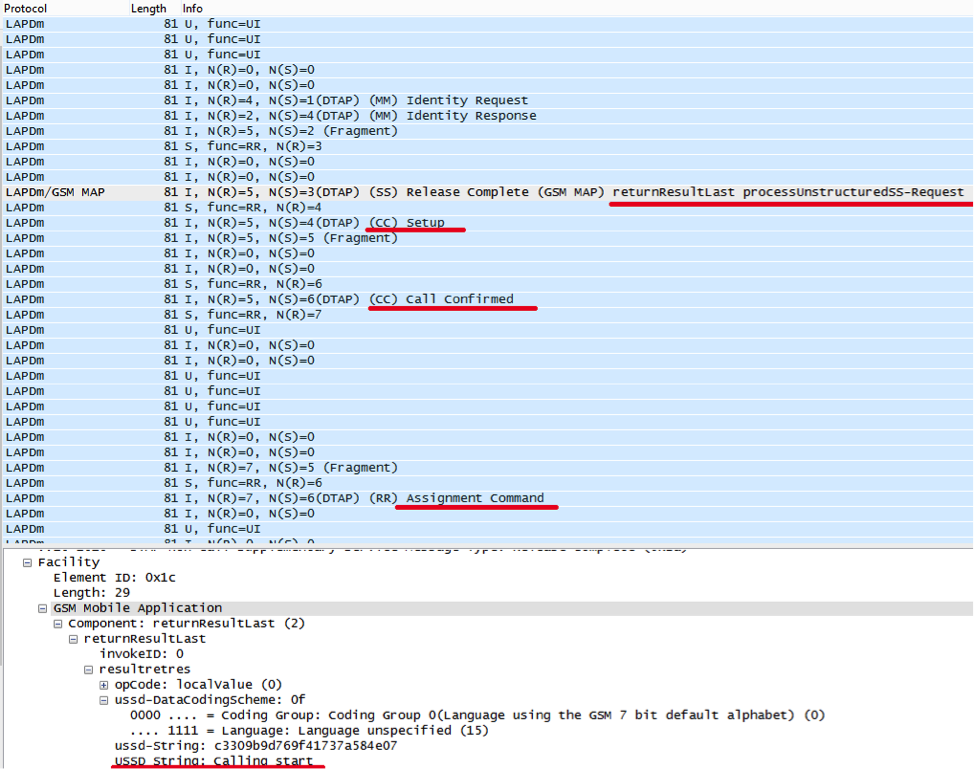
Thus, any outgoing activity, except for USSD, is prohibited for the SIM card and is prohibited by the home network. And the call itself is intercepted by the application on the SIM card and is replaced by a USSD with the called number, this goes into the home network, at this time the application ends the call, displays the message “Calling ...” on the screen and waits for a response to the USSD; it also checks the use of "encryption" on the network. If the USSD fails or the Calling start does not answer, it simply blocks the call (what we saw on the fake network).
However, apparently, the performance of the SIM card does not allow to intercept all calls, and having filled it with calls, they start to leave directly.
We tried to repeat this in a real network in order to make a call bypassing the PBX, but there all the calls are “fought off” by the network, because, as already mentioned, all outgoing activities are prohibited for HackerSIM.
The most attentive ones could have noticed the Identity Request request in the previous screenshot before the USSD response. This message is used by the network to receive an IMSI or IMEI from the phone.
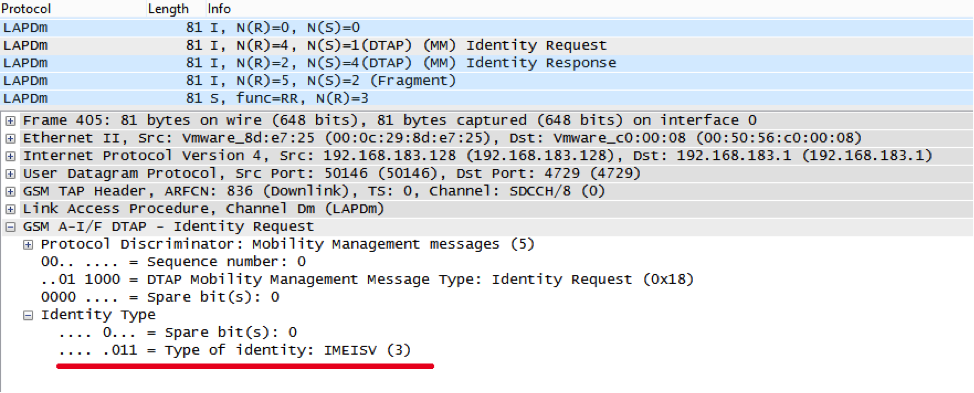
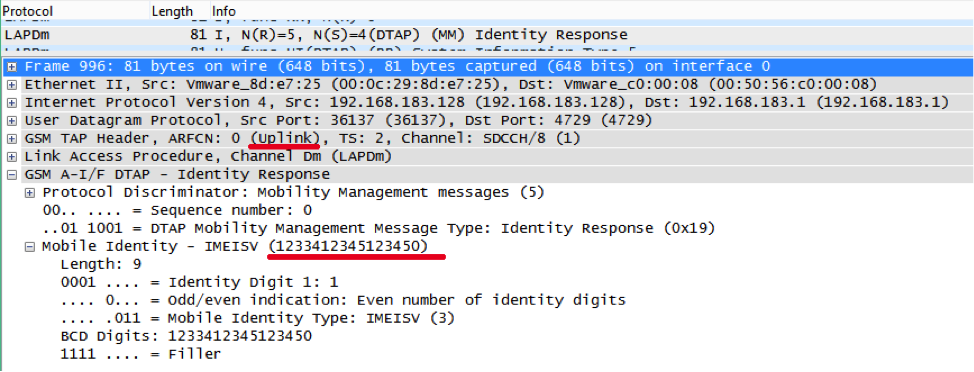
Recall that IMEI is generally an optional identifier in the cellular network and may never be requested. So someone collects them and not by chance. There is no anonymity when using HackerSIM: they know who, where, when, and where.
Now, knowing the secret of outgoing calls, we can call both from the old Motorola and from the mobile utility of the osmocom-bb package.

Multi IMSI / Ki
For the IMSI / Ki shift pair, you must use the SIM card menu:
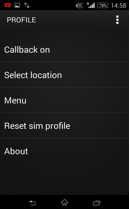
Callback on / off - turns on (off) the SIM card application, replacing outgoing calls to USSD.
Menu - there is nothing there except Exit.
Reset sim profile - resets TMSI and Kc (session key).
About -
Select Location — select IMSI / Ki.
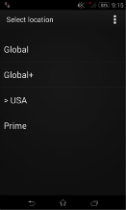
Global - IMSI 22201xxxxxxxxxxxx, owned by the Italian operator TIM.
Global + - IMSI 20404xxxxxxxxxx, owned by the Dutch operator Vodafone Libertel.
USA - IMSI 310630xxxxxxxxx, not owned by a specific operator, used in various Global SIM.
Prime - IMSI 23418xxxxxxxxxx, owned by the British Cloud9 / wire9 Tel.
All IMSI, except Global + , are not registered in Russia for one of these two reasons:
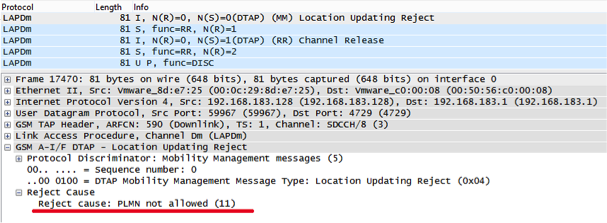
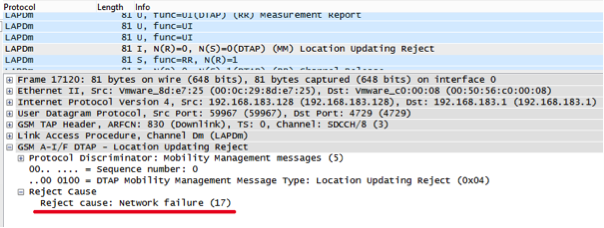
In Global + mode, too, not everything is smooth.
The list of preferred networks (where exactly it will work):
List of preferred PLMNs: MCC |MNC -------+------- 234 |15 (Guernsey, Vodafone) 262 |02 (Germany, Vodafone) 208 |10 (France, SFR) 222 |10 (Italy, Vodafone) 214 |01 (Spain, Vodafone) 505 |03 (Australia, Vodafone) 228 |01 (Switzerland, Swisscom) 206 |01 (Belgium, Proximus) 404 |20 (India, Vodafone IN) 404 |11 (India, Vodafone IN) 404 |27 (India, Vodafone IN) 404 |05 (India, Vodafone IN) 404 |46 (India, 46) 272 |01 (Ireland, Vodafone) 202 |05 (Greece, Vodafone) 232 |01 (Austria, A1) 655 |01 (South Africa, Vodacom) 286 |02 (Turkey, Vodafone) 238 |01 (Denmark, TDC) 268 |01 (Portugal, Vodafone) 260 |01 (Poland, Plus) 230 |03 (Czech Republic, Vodafone) 250 |01 (Russian Federation, MTS) 216 |70 (Hungary, Vodafone) 226 |01 (Romania, Vodafone) 244 |05 (Finland, Elisa) 602 |02 (Egypt, Vodafone) 219 |10 (Croatia, VIPnet) 620 |02 (Ghana, Ghana Telecom Mobile / Vodafone) 255 |01 (Ukraine, MTS) There are no prohibited networks, but when you try to register with Beeline and TELE2, a failure comes from your home network, MegaFon is working, MTS is preferable (in the SIM card)
Here is what happens when you try to connect to Beeline:
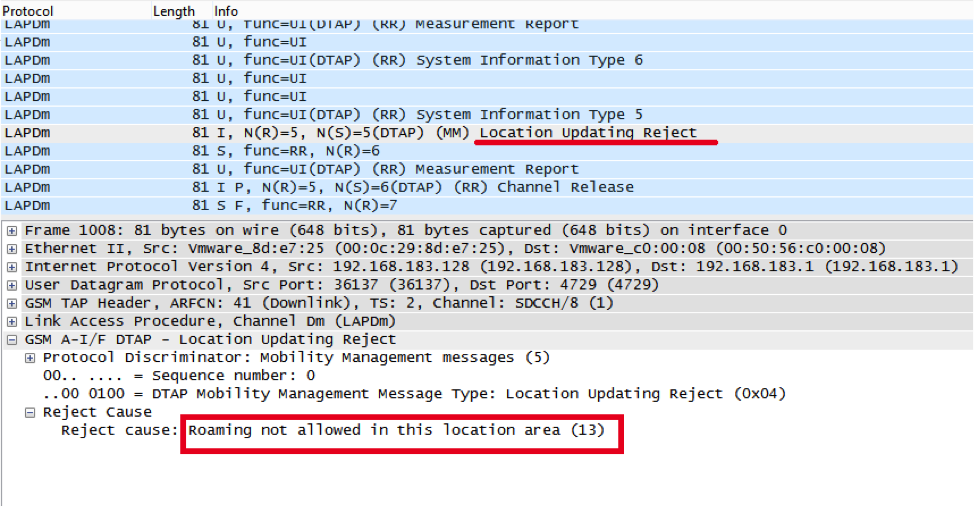
So, if this SIM works in any country of the world, it definitely does not work in any network of the world.
findings
The outgoing call scheme used may cause problems in the search for the call initiator, but only if the PBX is located abroad and does not contact the special services, and telecom operators do not know and do not want to know about the existence of such specific SIM cards. However, if you want to track the activity of all those who use such SIM-cards, it is easy: the only difference is that you will need to look for a slightly different information than usual.
There are no fantastic and hacker properties of the SIM card itself.
Source: https://habr.com/ru/post/269525/
All Articles