Email Security Overview
We are starting a series of email protection and hacking articles. There will be three articles in total. In the first article we will look at modern algorithms, tools and methods for protecting email. In the second, email hacking methods will be discussed, and in the third article we will tell you about a new email protection tool - CyberSafe Mail Encryption, which is currently under development.

Below, we will consider the various means of protecting e-mail and the advantages and disadvantages of each of them.
Let's start with the classics of the genre. I think everyone is familiar with PGP - even if someone has not used it, he knows about its existence. If someone is familiar with PGP, then we recommend the excellent article “Introduction to Public Key Encryption and PGP” . It describes both the basics of public key cryptography and what PGP is.
')
We'd better focus on the advantages and disadvantages of PGP, and, to be extremely precise, the PGP Desktop programs from Symantec. If we discard all other features of PGP Desktop, and only focus on email protection, there will be not so many advantages (compared to other solutions) - the presence of a keyserver.pgp.com key server, which users can use to exchange keys. There is no longer a need to publish your public keys on the site or transfer them personally to each addressee.
A feature of the program is its email protection method, namely interception of the mail client at the driver level. The program detects the traffic of the mail client and encrypts the sent messages and automatically decrypts incoming messages. It would seem that this method of protection is very convenient. After all, it is not necessary to separately configure the mail client, and the interception method works with any mail client. You do not need to know the specifics of setting each client if you want, for example, to switch from Outlook to The Bat!
You do not need to configure the clients themselves, but you need to configure the PGP Desktop program for each mailbox you use - you need to set e-mail, SMTP / POP / IMAP server addresses, etc. Understandably, you also need to configure encryption keys. All this is not very easy for a novice user. If you have never worked with PGP Desktop, you can assess the complexity of setting up the program in the following video: http://www.itprotect.ru/support/video/pgp-desktop-email/
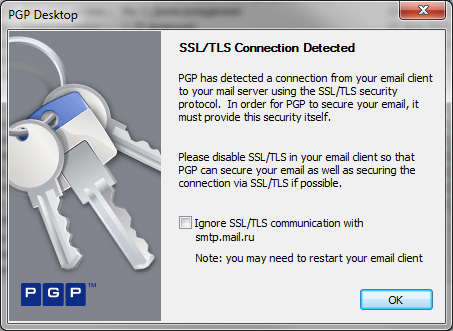
Fig. 1. PGP Desktop has detected an outgoing message.
But after all, the main drawback of the program also follows from this - already decrypted letters remain unprotected on the client. That is, by launching an email client that is not protected by anything, you can read the correspondence. If the attacker intercepts the traffic, he will not be able to read your messages, but if he takes possession of your hard disk, everything will be open, in full view. It is clear that the program also supports the creation of virtual containers, and encryption of physical disks. You can store the mail client's message base in a virtual container or on an encrypted disk, then the attacker will fail. But now it’s all about e-mail protection without any aids.
There is one more, no less significant drawback. If the PGP Desktop application has not been launched, and the sweat client has already received messages, they will remain undeciphered. And re-decipher them ... it's unclear how ... Of course, Symantec could not foresee this and developed a special plug-in for the Outlook email client, called Outlook Addin. But there are two things: the “glitches” of this plug-in didn’t really say anything lazy and what should those users who, instead of Outlook, say, Thunderbird, do?
S / MIME (Secure / Multipurpose Internet Mail Extensions) is a standard for encrypting and signing email with a public key. The principle of email security is as follows. The user generates a key pair (public / private key), configures his email client and provides the public key to everyone. They encrypt it with the public key of the letter, which can only be decrypted with the private key. In other words, using S / MIME, you can implement a classic asymmetric encryption scheme with all its advantages and disadvantages.
The advantages of this method include the following:
Of course, there are drawbacks:
However, not all flaws are such flaws. If you use special programs to create and manage user certificates, for example, CyberSafe Top Secret , then the first two drawbacks are irrelevant - you can create and publish your key on the key server. The program also allows you to search for keys published by other users.
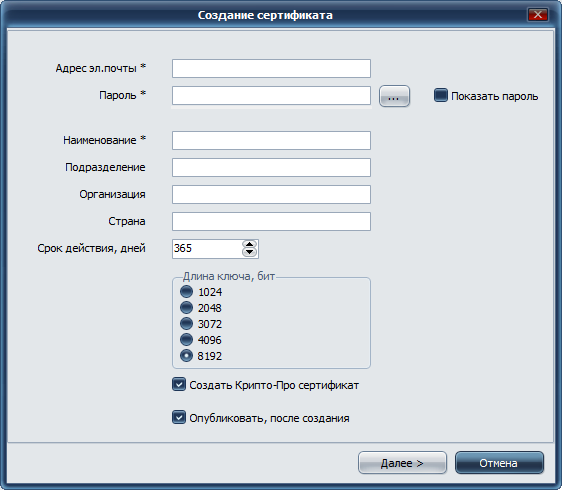
Fig. 2. Creating a certificate program CyberSafe Top Secret
In fact, the only noticeable flaw in S / MIME is the need to configure each email client manually. At the enterprise, you can configure your Outlook Address Book and everything will be much simpler (provided that you use Outlook). If you are an end user and use encryption for personal use, you will have to configure certificates in each mail client you use. In our other article it was shown how to configure encryption in Outlook .
Previously it was thought that it was enough to “get” a mailbox on a secure mail service like GMail.com and such security measures would be enough for the safety of email. However, in 2013, Google said it no longer guarantees data security . Such a statement plunged many users of this service into shock and forced them to look for either encryption tools or immediately protected services. The advantage of the latter is obvious - you do not need to configure anything. Just get yourself a "safe" mailbox and use it as usual.
One such service is HushMail. On their website everything is very beautifully painted, if you do not believe us, you can verify this yourself:
https://www.hushmail.com/about/technology/security/
Even a threat matrix is provided, allowing you to determine what HushMail can protect against and what not against it. The site says that the service will help from intercepting your Internet connection, from data leakage, from unauthorized content analysis, as well as from government monitoring programs. I especially want to stay at the last opportunity. However, we all know that earlier, HushMail sent the decrypted messages of some of its users to the police during the trial of a drug smuggling case. The point is not even in the fact of data transfer (of course, no one wants to hide the criminals), but in the fact of data decryption.

Fig. 3. HushMail Threat Matrix
HushMail was once famous for being the only cryptographic service where all cryptographic operations were performed on the client side in a special Java applet. In the same applet, key pairs were generated, and only encrypted messages were stored on the server, which excluded access to the user's private keys. This applet was even checked for bookmarks. They were not found. But the fact of the transfer of decrypted messages was not argue with that.
Then HushMail turned into a regular mail service with SSL support, albeit with OpenPGP support, however, all cryptographic operations are performed on the server. That is why we do not recommend using such services - you never know what is happening “on the other side”.
By the way, HushMail has two interface options - new and “original” (original). The latter is depicted in Fig. 4. It is in this version of the interface that there is a menu item Hushtools, which calls the window of the same name, which provides a means of managing keys. In the “new” version of the interface, it is generally not clear how to manage keys and encryption. In it, HushMail is similar to a regular email service like Gmail.com.
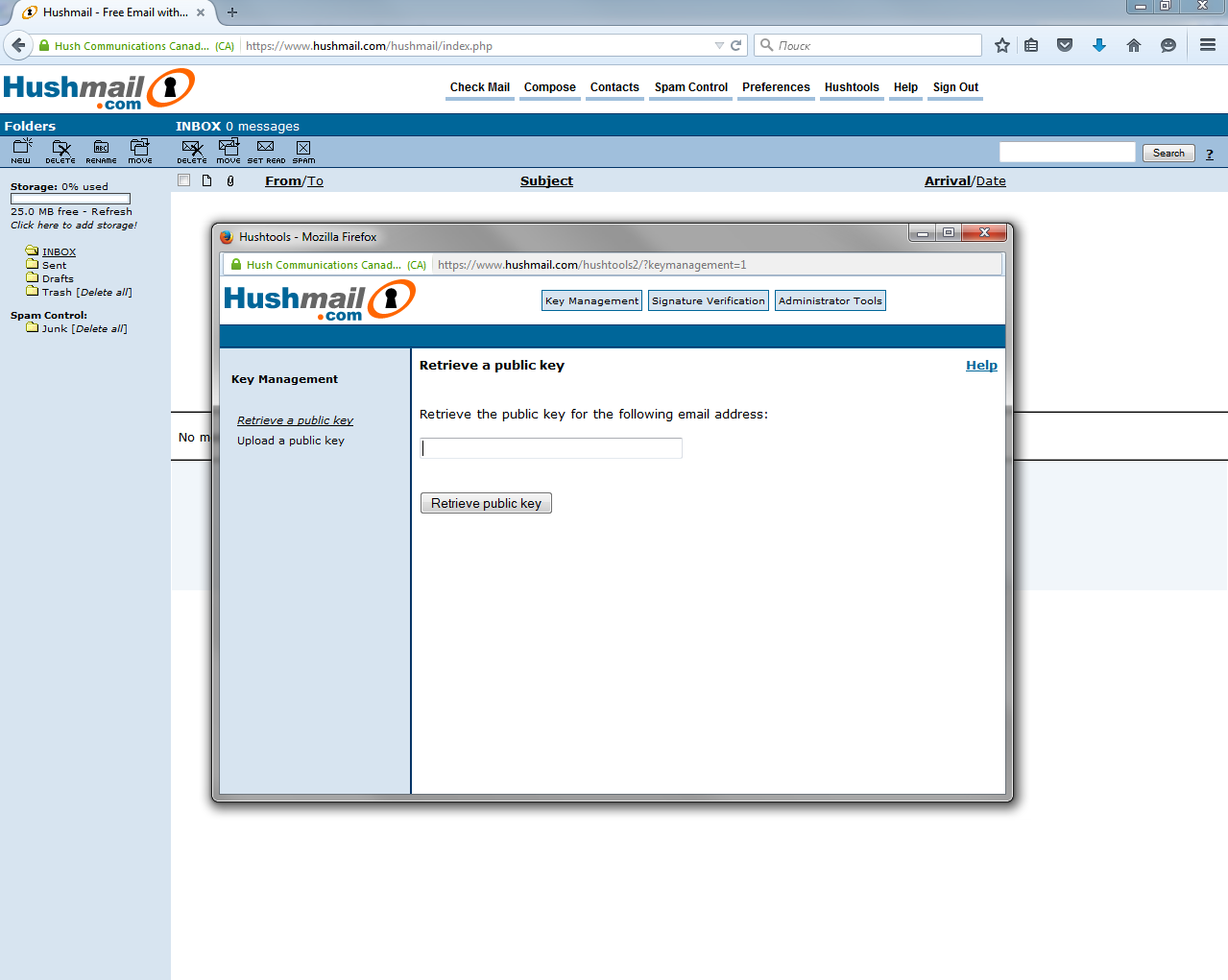
Fig. 4. Original HushMail Interface
Allows the use of asymmetric encryption (i.e. public / private key encryption) on the client side. About the capabilities of this plugin can be found on the official site . It is necessary to mention only four of its features:
The fact that encryption is performed on the client side is the only advantage of this plugin. But the recommendation to use TOR can complicate the familiarity with this plugin for inexperienced users. But for these users, this plugin is created, as more experienced use PGP or S / MIME.
Yes, and dependence on the browser - the same is not good. And what if the user uses Edge? But this browser, in spite of the popularity of Chrome and Firefox, is quite popular just because it is the “court” browser of Microsoft.
Unlike PGP Mail, the SecureGmail plugin offers symmetric encryption, that is, each secret message is encrypted with a password that both the sender and the recipient need to know. Such an encryption system can be used with full trust between all its participants. Moreover, with an increase in the number of participants will have to increase the number of keys. For example, you correspond with Ivanov, Petrov and Sidirov. You can, of course, encrypt all messages with one password, which all three recipients will know. But this is not correct. It is more correct to create separate keys (passwords) for each of the recipients. When there are three of them, this will not make any special problems. But when you need to exchange email with hundreds of recipients, how to remember all the keys? Consequently, such an encryption system is convenient when exchanging e-mail with a small group of recipients.
The SecureGmail plugin works in tandem with the Chrome browser, it does not support other browsers.
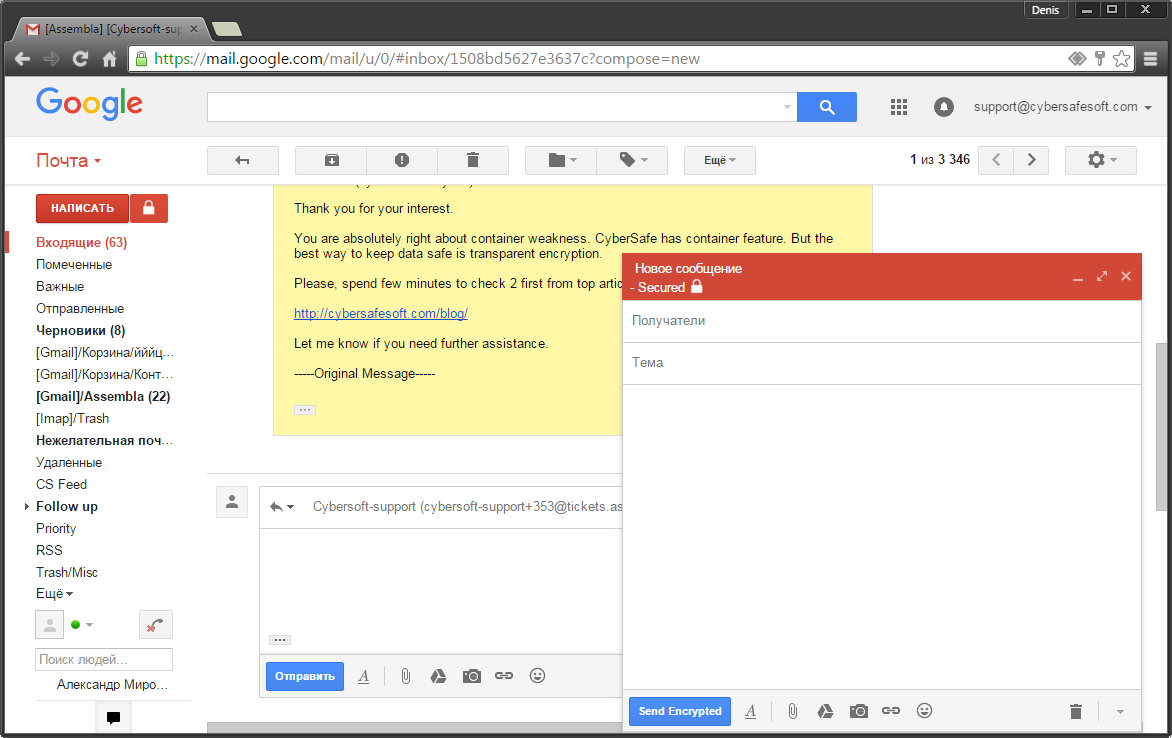
Fig. 5. SecureGmail plugin
The Encrypted Communication plug- in is similar in its functionality to SecureGmail, but it only works in the Firefox browser, other browsers are not supported.
We have already talked about the disadvantages of a symmetric encryption system, so we will not repeat. If you write secret information with one or two users, such plug-ins still justify their existence. Otherwise, it is better to use an asymmetric system.
Fig. 6. Encrypted Communication Plugin
The advantage of such plugins is ease of use. No need to understand asymmetric encryption (after all, the concept of a public / private key may seem complicated to beginners), no need to fool your head with keys, backing them up. You just need to remember the password and it is advisable to tell it to your friends so that the attacker could not intercept it.
Similar to browsers, encryption plug-ins also exist for email clients. One of them is Enigmail . It is an OpenPGP plugin for Thunderbird and Postbox.
This solution has no particular advantages, since you still have to install and configure additional software — the GnuPG program. When everything is set up, we can say that the plugin is easy to use.
The disadvantage is that you still need to delve into the asymmetric encryption system and figure out what the public and private keys are and what each of them is used for. However, this is a lack of all methods that use asymmetric cryptography. Here is either security and knowledge, or ignorance and symmetric cryptography.
Next, we will look at the threat matrix (Table 2), but first we suggest that you familiarize yourself with the general table of advantages and disadvantages of each email protection tool.
Table 1. Comparative table of mail protection tools
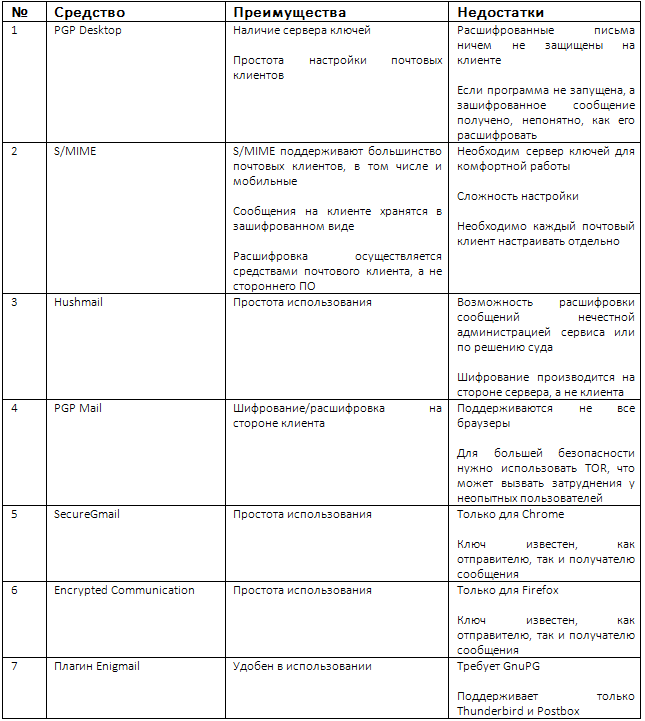
When building Table 2, we took the HushMail project’s threat matrix as a basis, supplemented it and can use it to compare the email protection tools described in the table. The number of the means in this table corresponds to the number of the means in table 1. The value “Yes” means that you are protected from the threat. The value "Yes / No" means that there are any restrictions, which we describe.
Table 2. Comparison of email protection tools by threat matrix
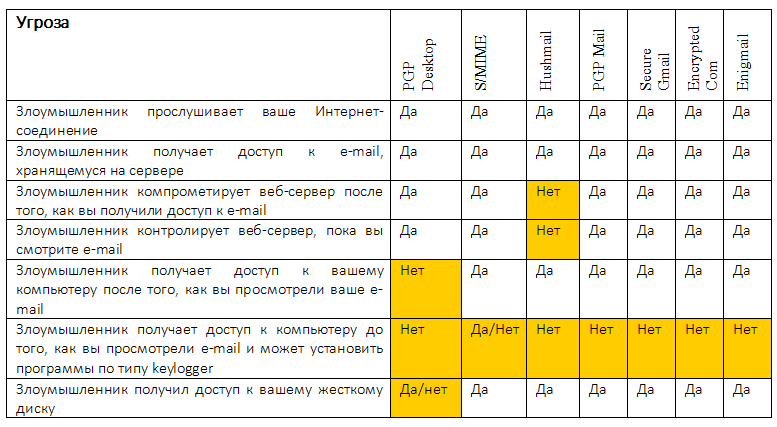
Let us comment on this table on the example of PGP Desktop and Huhsmail protection tools (columns 1 and 3).
Since encryption is performed on the client side, PGP Desktop protects your correspondence from listening to an Internet connection. As for HushMail, you only have to rely on SSL. But gmail also offers this protection, and if you are primarily interested in protection against the Internet connection “interception”, then you can not use any means of protection at all. However, the site HushMail indicated that the service protects against wiretapping, so the table says "Yes."
What happens if an attacker finds out your mailbox password? Since the letters are stored in encrypted form on the server, nothing terrible will happen - the maximum that he can read is spam (where it is without him) and other unimportant correspondence that you could not encrypt.
And what happens if an attacker compromises or controls the web server itself? PGP Desktop, like any tool where encryption occurs on the client, will protect you from this trouble. After all, the data from the user's computer is already sent in encrypted form. That can't be said about HushMail. Yes, the SSL protocol saves from wiretapping, and "inside it" the data is transmitted in the clear, until encryption takes place on the server itself. Therefore, the web server has full data access. This is the answer to the question of how the HushMail administration was able to provide access to the correspondence during the trial.
When using PGP Desktop after decryption, messages are stored in unencrypted form. Therefore, if someone gains access to your computer after reading your letters or takes possession of your hard drive, PGP Desktop will not help you much. Of course, if PGP Desktop was not running when the message arrived, therefore, there was no one to decrypt it, then maybe the information will still remain secret. Therefore, opposite PGP Desktop in Table 2 is Yes / No for the latest threat. As for HushMail, you don’t need to worry about these threats, because the message is encrypted on the server.
But both defenses are vulnerable when using keylogger. If an attacker intercepts your passwords (in particular, from certificates), then nothing will help you. Is that the transition to tokens instead of entering passwords.
All other security tools use encryption on the client side, so they are not afraid of either interception or access to your mailbox - the messages will be encrypted. The only thing that poses a threat to these defenses is the interception of keyboard input. An attacker can gain access not only to your passwords, but also to plain text that you enter in the message body before it is encrypted. By the way, you need to make an important remark about S / MIME, namely why, if used correctly, S / MIME, even a keylogger may not help. If the key is added to the repository as not exported (which, by the way, CyberSafe Top Secret does), then the attacker will fail. That is why at the moment S / MIME can be considered the most reliable way to protect email.
General information about email security is given in table 3.
Table 3. Summary of Email Security
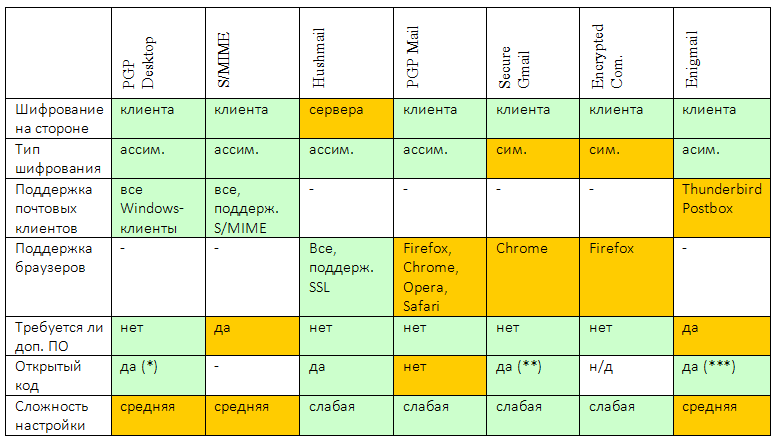
The easiest way to protect email is to use symmetric encryption. To implement it, you can use the SecureGmail browser and Encrypted Communication plug-ins or do without them, and use programs that allow you to create password-protected archives (for example, WinRAR, 7-Zip). The calculation is simple: you protect the file with an archive, put a message with possible attachments in it and send it to another person. He, knowing the password, opens the archive. The easiest to implement, but not very easy to use way. Creating an archive for each new post is pretty routine. SecureGmail and Encrypted Communication plugins make symmetric encryption more convenient, but it doesn’t make it safer.
More secure asymmetric encryption. It is implemented in many different ways. You can use the standard S / MIME (which allows the use of asymmetric cryptography even on mobile devices), you can use PGP and derivative products (OpenPGP, PGP Mail, GnuPG).
Ideally, we just recommend using the S / MIME standard as the most reliable and versatile.
Its reliability lies in the fact that in the mail client itself the messages are stored in encrypted form and are decrypted only as they are accessed (that is, if someone takes possession of your hard drive, he will not be able to decrypt your messages). When decrypting, a password is requested that only you know (as opposed to symmetric encryption, where at least two people know the password).
The versatility lies in the fact that once you have created your certificate, you can use it in any email clients (of course, with S / MIME support), as well as in any operating systems on which these email clients work. For example, you can generate a certificate with a Windows program, install it in Outlook and in the MailDroid mobile email client. There are no restrictions on the use of certificates. The main thing when using S / MIME is to choose a convenient program for creating certificates themselves. It is desirable that it allows you to publish certificates on the key server and manage them.
(*) PGP Desktop Source Code
(**) SecureGMail Source Code
(***) EnigMail Source Code
CyberSafe Top Secret Program
Configuring S / MIME in Outlook

Email Protection Tools
Below, we will consider the various means of protecting e-mail and the advantages and disadvantages of each of them.
PGP
Let's start with the classics of the genre. I think everyone is familiar with PGP - even if someone has not used it, he knows about its existence. If someone is familiar with PGP, then we recommend the excellent article “Introduction to Public Key Encryption and PGP” . It describes both the basics of public key cryptography and what PGP is.
')
We'd better focus on the advantages and disadvantages of PGP, and, to be extremely precise, the PGP Desktop programs from Symantec. If we discard all other features of PGP Desktop, and only focus on email protection, there will be not so many advantages (compared to other solutions) - the presence of a keyserver.pgp.com key server, which users can use to exchange keys. There is no longer a need to publish your public keys on the site or transfer them personally to each addressee.
A feature of the program is its email protection method, namely interception of the mail client at the driver level. The program detects the traffic of the mail client and encrypts the sent messages and automatically decrypts incoming messages. It would seem that this method of protection is very convenient. After all, it is not necessary to separately configure the mail client, and the interception method works with any mail client. You do not need to know the specifics of setting each client if you want, for example, to switch from Outlook to The Bat!
You do not need to configure the clients themselves, but you need to configure the PGP Desktop program for each mailbox you use - you need to set e-mail, SMTP / POP / IMAP server addresses, etc. Understandably, you also need to configure encryption keys. All this is not very easy for a novice user. If you have never worked with PGP Desktop, you can assess the complexity of setting up the program in the following video: http://www.itprotect.ru/support/video/pgp-desktop-email/

Fig. 1. PGP Desktop has detected an outgoing message.
But after all, the main drawback of the program also follows from this - already decrypted letters remain unprotected on the client. That is, by launching an email client that is not protected by anything, you can read the correspondence. If the attacker intercepts the traffic, he will not be able to read your messages, but if he takes possession of your hard disk, everything will be open, in full view. It is clear that the program also supports the creation of virtual containers, and encryption of physical disks. You can store the mail client's message base in a virtual container or on an encrypted disk, then the attacker will fail. But now it’s all about e-mail protection without any aids.
There is one more, no less significant drawback. If the PGP Desktop application has not been launched, and the sweat client has already received messages, they will remain undeciphered. And re-decipher them ... it's unclear how ... Of course, Symantec could not foresee this and developed a special plug-in for the Outlook email client, called Outlook Addin. But there are two things: the “glitches” of this plug-in didn’t really say anything lazy and what should those users who, instead of Outlook, say, Thunderbird, do?
S / MIME
S / MIME (Secure / Multipurpose Internet Mail Extensions) is a standard for encrypting and signing email with a public key. The principle of email security is as follows. The user generates a key pair (public / private key), configures his email client and provides the public key to everyone. They encrypt it with the public key of the letter, which can only be decrypted with the private key. In other words, using S / MIME, you can implement a classic asymmetric encryption scheme with all its advantages and disadvantages.
The advantages of this method include the following:
- S / MIME supports most email clients, including mobile clients (for example, MailDroid).
- Messages in the email client are encrypted until you decrypt them. To decrypt, you need to enter a password that is specified when creating a key pair.
- No problem decrypting messages as when using PGP Desktop. Since decryption takes place by means of an email client, and not by a third-party program, it is possible to decrypt the letter at any convenient time.
Of course, there are drawbacks:
- The main problem S / MIME - which program to generate a certificate?
- Each recipient must provide their public key. Of course, this can be smoothed a bit when using a key server, we'll talk about this a little later.
- The complexity of the settings. S / MIME requires a separate setting for each email client. For example, if you use Outlook in your office, The Bat! Houses, and MailDroid on your mobile phone, then you should know how to set up all these clients. And this requires user qualifications above average.
- Difficulties when changing the key, especially if users have a poor understanding of what they are doing.
However, not all flaws are such flaws. If you use special programs to create and manage user certificates, for example, CyberSafe Top Secret , then the first two drawbacks are irrelevant - you can create and publish your key on the key server. The program also allows you to search for keys published by other users.

Fig. 2. Creating a certificate program CyberSafe Top Secret
In fact, the only noticeable flaw in S / MIME is the need to configure each email client manually. At the enterprise, you can configure your Outlook Address Book and everything will be much simpler (provided that you use Outlook). If you are an end user and use encryption for personal use, you will have to configure certificates in each mail client you use. In our other article it was shown how to configure encryption in Outlook .
Secure mail services. Hushmail
Previously it was thought that it was enough to “get” a mailbox on a secure mail service like GMail.com and such security measures would be enough for the safety of email. However, in 2013, Google said it no longer guarantees data security . Such a statement plunged many users of this service into shock and forced them to look for either encryption tools or immediately protected services. The advantage of the latter is obvious - you do not need to configure anything. Just get yourself a "safe" mailbox and use it as usual.
One such service is HushMail. On their website everything is very beautifully painted, if you do not believe us, you can verify this yourself:
https://www.hushmail.com/about/technology/security/
Even a threat matrix is provided, allowing you to determine what HushMail can protect against and what not against it. The site says that the service will help from intercepting your Internet connection, from data leakage, from unauthorized content analysis, as well as from government monitoring programs. I especially want to stay at the last opportunity. However, we all know that earlier, HushMail sent the decrypted messages of some of its users to the police during the trial of a drug smuggling case. The point is not even in the fact of data transfer (of course, no one wants to hide the criminals), but in the fact of data decryption.

Fig. 3. HushMail Threat Matrix
HushMail was once famous for being the only cryptographic service where all cryptographic operations were performed on the client side in a special Java applet. In the same applet, key pairs were generated, and only encrypted messages were stored on the server, which excluded access to the user's private keys. This applet was even checked for bookmarks. They were not found. But the fact of the transfer of decrypted messages was not argue with that.
Then HushMail turned into a regular mail service with SSL support, albeit with OpenPGP support, however, all cryptographic operations are performed on the server. That is why we do not recommend using such services - you never know what is happening “on the other side”.
By the way, HushMail has two interface options - new and “original” (original). The latter is depicted in Fig. 4. It is in this version of the interface that there is a menu item Hushtools, which calls the window of the same name, which provides a means of managing keys. In the “new” version of the interface, it is generally not clear how to manage keys and encryption. In it, HushMail is similar to a regular email service like Gmail.com.

Fig. 4. Original HushMail Interface
PGP Mail Browser Plugin
Allows the use of asymmetric encryption (i.e. public / private key encryption) on the client side. About the capabilities of this plugin can be found on the official site . It is necessary to mention only four of its features:
- Supported browsers: Firefox, Chrome, Opera, Safari
- It is recommended to use Firefox, since the encryption functions in Firefox are faster than in Chrome or Opera.
- It is recommended to use TOR
- Encryption is performed on the client side
The fact that encryption is performed on the client side is the only advantage of this plugin. But the recommendation to use TOR can complicate the familiarity with this plugin for inexperienced users. But for these users, this plugin is created, as more experienced use PGP or S / MIME.
Yes, and dependence on the browser - the same is not good. And what if the user uses Edge? But this browser, in spite of the popularity of Chrome and Firefox, is quite popular just because it is the “court” browser of Microsoft.
SecureGmail Browser Plugin
Unlike PGP Mail, the SecureGmail plugin offers symmetric encryption, that is, each secret message is encrypted with a password that both the sender and the recipient need to know. Such an encryption system can be used with full trust between all its participants. Moreover, with an increase in the number of participants will have to increase the number of keys. For example, you correspond with Ivanov, Petrov and Sidirov. You can, of course, encrypt all messages with one password, which all three recipients will know. But this is not correct. It is more correct to create separate keys (passwords) for each of the recipients. When there are three of them, this will not make any special problems. But when you need to exchange email with hundreds of recipients, how to remember all the keys? Consequently, such an encryption system is convenient when exchanging e-mail with a small group of recipients.
The SecureGmail plugin works in tandem with the Chrome browser, it does not support other browsers.

Fig. 5. SecureGmail plugin
Encrypted Communication Browser Plugin
The Encrypted Communication plug- in is similar in its functionality to SecureGmail, but it only works in the Firefox browser, other browsers are not supported.
We have already talked about the disadvantages of a symmetric encryption system, so we will not repeat. If you write secret information with one or two users, such plug-ins still justify their existence. Otherwise, it is better to use an asymmetric system.

Fig. 6. Encrypted Communication Plugin
The advantage of such plugins is ease of use. No need to understand asymmetric encryption (after all, the concept of a public / private key may seem complicated to beginners), no need to fool your head with keys, backing them up. You just need to remember the password and it is advisable to tell it to your friends so that the attacker could not intercept it.
Enigmail email client plugin
Similar to browsers, encryption plug-ins also exist for email clients. One of them is Enigmail . It is an OpenPGP plugin for Thunderbird and Postbox.
This solution has no particular advantages, since you still have to install and configure additional software — the GnuPG program. When everything is set up, we can say that the plugin is easy to use.
The disadvantage is that you still need to delve into the asymmetric encryption system and figure out what the public and private keys are and what each of them is used for. However, this is a lack of all methods that use asymmetric cryptography. Here is either security and knowledge, or ignorance and symmetric cryptography.
Threats and Remedies
Next, we will look at the threat matrix (Table 2), but first we suggest that you familiarize yourself with the general table of advantages and disadvantages of each email protection tool.
Table 1. Comparative table of mail protection tools

When building Table 2, we took the HushMail project’s threat matrix as a basis, supplemented it and can use it to compare the email protection tools described in the table. The number of the means in this table corresponds to the number of the means in table 1. The value “Yes” means that you are protected from the threat. The value "Yes / No" means that there are any restrictions, which we describe.
Table 2. Comparison of email protection tools by threat matrix

Let us comment on this table on the example of PGP Desktop and Huhsmail protection tools (columns 1 and 3).
Since encryption is performed on the client side, PGP Desktop protects your correspondence from listening to an Internet connection. As for HushMail, you only have to rely on SSL. But gmail also offers this protection, and if you are primarily interested in protection against the Internet connection “interception”, then you can not use any means of protection at all. However, the site HushMail indicated that the service protects against wiretapping, so the table says "Yes."
What happens if an attacker finds out your mailbox password? Since the letters are stored in encrypted form on the server, nothing terrible will happen - the maximum that he can read is spam (where it is without him) and other unimportant correspondence that you could not encrypt.
And what happens if an attacker compromises or controls the web server itself? PGP Desktop, like any tool where encryption occurs on the client, will protect you from this trouble. After all, the data from the user's computer is already sent in encrypted form. That can't be said about HushMail. Yes, the SSL protocol saves from wiretapping, and "inside it" the data is transmitted in the clear, until encryption takes place on the server itself. Therefore, the web server has full data access. This is the answer to the question of how the HushMail administration was able to provide access to the correspondence during the trial.
When using PGP Desktop after decryption, messages are stored in unencrypted form. Therefore, if someone gains access to your computer after reading your letters or takes possession of your hard drive, PGP Desktop will not help you much. Of course, if PGP Desktop was not running when the message arrived, therefore, there was no one to decrypt it, then maybe the information will still remain secret. Therefore, opposite PGP Desktop in Table 2 is Yes / No for the latest threat. As for HushMail, you don’t need to worry about these threats, because the message is encrypted on the server.
But both defenses are vulnerable when using keylogger. If an attacker intercepts your passwords (in particular, from certificates), then nothing will help you. Is that the transition to tokens instead of entering passwords.
All other security tools use encryption on the client side, so they are not afraid of either interception or access to your mailbox - the messages will be encrypted. The only thing that poses a threat to these defenses is the interception of keyboard input. An attacker can gain access not only to your passwords, but also to plain text that you enter in the message body before it is encrypted. By the way, you need to make an important remark about S / MIME, namely why, if used correctly, S / MIME, even a keylogger may not help. If the key is added to the repository as not exported (which, by the way, CyberSafe Top Secret does), then the attacker will fail. That is why at the moment S / MIME can be considered the most reliable way to protect email.
General information about email security is given in table 3.
Table 3. Summary of Email Security

findings
The easiest way to protect email is to use symmetric encryption. To implement it, you can use the SecureGmail browser and Encrypted Communication plug-ins or do without them, and use programs that allow you to create password-protected archives (for example, WinRAR, 7-Zip). The calculation is simple: you protect the file with an archive, put a message with possible attachments in it and send it to another person. He, knowing the password, opens the archive. The easiest to implement, but not very easy to use way. Creating an archive for each new post is pretty routine. SecureGmail and Encrypted Communication plugins make symmetric encryption more convenient, but it doesn’t make it safer.
More secure asymmetric encryption. It is implemented in many different ways. You can use the standard S / MIME (which allows the use of asymmetric cryptography even on mobile devices), you can use PGP and derivative products (OpenPGP, PGP Mail, GnuPG).
Ideally, we just recommend using the S / MIME standard as the most reliable and versatile.
Its reliability lies in the fact that in the mail client itself the messages are stored in encrypted form and are decrypted only as they are accessed (that is, if someone takes possession of your hard drive, he will not be able to decrypt your messages). When decrypting, a password is requested that only you know (as opposed to symmetric encryption, where at least two people know the password).
The versatility lies in the fact that once you have created your certificate, you can use it in any email clients (of course, with S / MIME support), as well as in any operating systems on which these email clients work. For example, you can generate a certificate with a Windows program, install it in Outlook and in the MailDroid mobile email client. There are no restrictions on the use of certificates. The main thing when using S / MIME is to choose a convenient program for creating certificates themselves. It is desirable that it allows you to publish certificates on the key server and manage them.
Links
(*) PGP Desktop Source Code
(**) SecureGMail Source Code
(***) EnigMail Source Code
CyberSafe Top Secret Program
Configuring S / MIME in Outlook
Source: https://habr.com/ru/post/269513/
All Articles