Yandex and ZeroNights: a month of searching for vulnerabilities in Yandex Browser
Today, Yandex, together with the organizers of the ZeroNights conference, is launching a vulnerability search contest in Yandex Browser . Its participants will be able not only to help millions of users, but also to compete for quite material prizes.
Publishing a post on Habrahabr just for the sake of announcing the contest would be too boring, so I will combine the useful with the useful and tell you why our team introduces additional protection technologies into the browser (for example, proxying open wi-fi traffic), and is not limited to closing vulnerabilities. It would be interesting to discuss with you our vision.
')
Competition
I am sure Habr's readers will agree that security is not the end result, but a process of constantly searching and fixing problems. Whatever protection you have developed, sooner or later someone will break through it. And the more users have your product, the more often the protection will be tested for durability.
In this situation, it would be wrong to ignore the experience and knowledge of third-party specialists. The contest, which will be discussed later, is the first attempt of our Browser team to organize such a joint work, so we will be grateful for your feedback and assistance. And if everything works out, and the browser becomes safer as a result, we will continue this practice, and in the future we will include Yandex.Browser in the constant program “The Hunt for Errors”.
From October 26 to November 20, any researcher can try to find a vulnerability in the Yandex Browser and inform us about it through a special form . Three winners will be selected among all the contestants, who will send the most critical and unexpected vulnerabilities. As awards, they will receive 500, 300 and 150 thousand rubles, depending on the prize. Winners will be announced at the ZeroNights hacker conference on November 26 in Moscow.
Vulnerabilities need to be looked for in a stable version of Yandex. The browser is not lower than 15.10 (beta versions do not participate) for Windows and OS X operating systems.
More rules are described here .
What to look for:
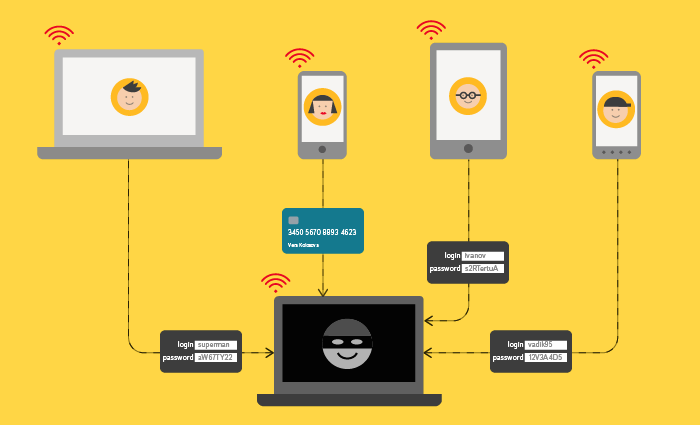
- Ability to bypass protection in public Wi-Fi networks, namely, creating an unprotected connection in an open Wi-Fi network or intercepting / modifying HTTP traffic.
- Ability to bypass password protection, namely to obtain a user password that matches the password from Yandex, to bypass the warning about entering a password from Yandex on another site. (Only protection bypass methods are accepted when entering passwords through standard HTML web forms of the form
Publishing a post on Habrahabr just for the sake of announcing the contest would be too boring, so I will combine the useful with the useful and tell you why our team introduces additional protection technologies into the browser (for example, proxying open wi-fi traffic), and is not limited to closing vulnerabilities. It would be interesting to discuss with you our vision.

')
Competition
I am sure Habr's readers will agree that security is not the end result, but a process of constantly searching and fixing problems. Whatever protection you have developed, sooner or later someone will break through it. And the more users have your product, the more often the protection will be tested for durability.
In this situation, it would be wrong to ignore the experience and knowledge of third-party specialists. The contest, which will be discussed later, is the first attempt of our Browser team to organize such a joint work, so we will be grateful for your feedback and assistance. And if everything works out, and the browser becomes safer as a result, we will continue this practice, and in the future we will include Yandex.Browser in the constant program “The Hunt for Errors”.
From October 26 to November 20, any researcher can try to find a vulnerability in the Yandex Browser and inform us about it through a special form . Three winners will be selected among all the contestants, who will send the most critical and unexpected vulnerabilities. As awards, they will receive 500, 300 and 150 thousand rubles, depending on the prize. Winners will be announced at the ZeroNights hacker conference on November 26 in Moscow.
Vulnerabilities need to be looked for in a stable version of Yandex. The browser is not lower than 15.10 (beta versions do not participate) for Windows and OS X operating systems.
More rules are described here .
What to look for:
- Ability to bypass protection in public Wi-Fi networks, namely, creating an unprotected connection in an open Wi-Fi network or intercepting / modifying HTTP traffic.
- Ability to bypass password protection, namely to obtain a user password that matches the password from Yandex, to bypass the warning about entering a password from Yandex on another site. (Only protection bypass methods are accepted when entering passwords through standard HTML web forms of the form
.)
- .
- (remote code execution) Use-After-Free, Integer Overflow, Stack/Heap Based Overflow, Memory Corruption ..
- Same Origin Policy (SOP), Universal XSS (UXSS), SOP Cache-Timing, Browser-API .
- Content Security Policy (CSP) CSP HTTP-.
- SSL\TLS, , SSL-Strip .
- (click-to-play bypass).
- (Remote DoS) JS HTML.
, , : wi-fi . , .
?
. . ( , ), ( , Liveinternet.ru). . Chromium (, , Chromium). , malware , , . .
, . ( 30% ). , , "" .. , . . , . , . . . , ..
( ) , . (, ), , , , , . ?
, . , , . . , . , , . .
Wi-Fi . - . Wi-Fi . HTTP-, .
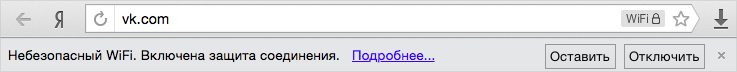
. - SafeBrowsing. - . - " " . . (, ) , . ( ). - .
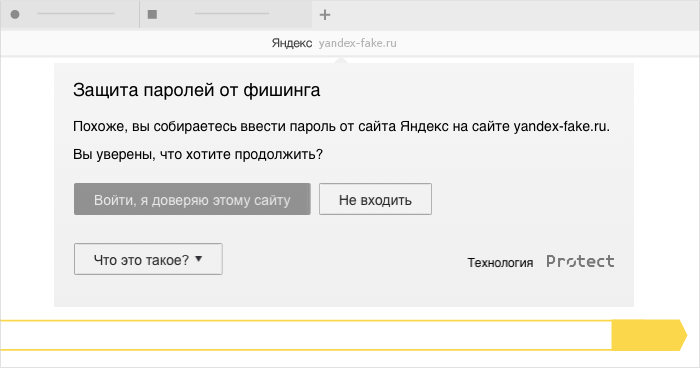
. , , !Source: https://habr.com/ru/post/269507/
All Articles