This is not paranoia: sources of threats in the GSM system and protection from them.
Despite the impressive prophecies about the imminent disappearance of GSM, it continues to exist and develop.
The high level of mobile penetration, the tremendous pace of development of mobile devices, the high marginality of services for operators, convenience and reliability for subscribers have made mobile communication an integral part of our life, including business. Millions of minutes of corporate calls go through GSM networks every day. Most often, everything goes well, but do not forget about the existing sources of threats in cellular networks.
That was the beginning of our future post about the threats that arise in the GSM network. But recently, a post about a story with duplicates was published on Habré. In the comments, there was a vigorous discussion of security issues at the SIM level and even a proposal to create a business by selling “numbers that cannot be stolen” At Tottoli GSM, we immediately decided to slightly change the publication and tell in detail not only about the threats, but also about the simple protection method that has already been invented and successfully used.
')

It is worth starting with the fact that complete security within the framework of GSM-communication is a myth. Those who try to say the opposite, at the very least, are misleading people, and sometimes they are just scammers. Modern technologies can quite successfully cope with existing encryption algorithms protection mechanisms in the GSM network.
Tottoli GSM is not a theoretical expert who models sources of threats and searches for ideal solutions “in a vacuum”. Tottli GSM is a company with practical experience in developing solutions for SIM-cards and this article is the dry residue of many years of practical experience. There are quite a lot of materials related to the demonstration of the interception of the GSM signal, the remote hacking of SIM cards and the like. But here it must be borne in mind that all of these stories took place in either a specific laboratory environment, or super-expensive equipment was used. We proceed from the everyday practice of communicating subscribers, and protecting their privacy from unauthorized intrusion, assuming that no one can give 100% protection. At the same time, our technologies allow us to make communication secure at a high level. Our task is to talk about the threats and the possible method of protection, the safety of your communication is your decision.
SORM - a system of technical means to ensure the functions of operational search activities. Speaking openly, this is a forced evil, prescribed by law, which obliges telecoms operators to implement the system. Otherwise, the mobile operator may be deprived of the license. For the sake of justice, it is worth noting that the laws of the Russian Federation, and by-laws and regulations, as well as the very logic of the SORM system, protects cellular subscribers from abuse by authorized persons.
From an engineering point of view, SORM is a control panel (PU) that allows you to send commands to the network and receive answers and data to requests. With the development of mobile and convergent communications, as well as the provision of text, voice and Internet services in GSM networks, SORM experienced an upgrade and turned into a serious hardware-software complex, without losing its original logic. In addition to the usual components, special mediators are now included in the delivery, which are designed to process and transmit heterogeneous information to a single PU SORM. In fact, PU SORM has become a highly loaded distributed information center - after all, its task is to process enormous amounts of information coming through multi-service traffic channels (voice, mail, Internet, media, etc.), you should not even talk about the heterogeneity of traffic in the new generation NGN networks.
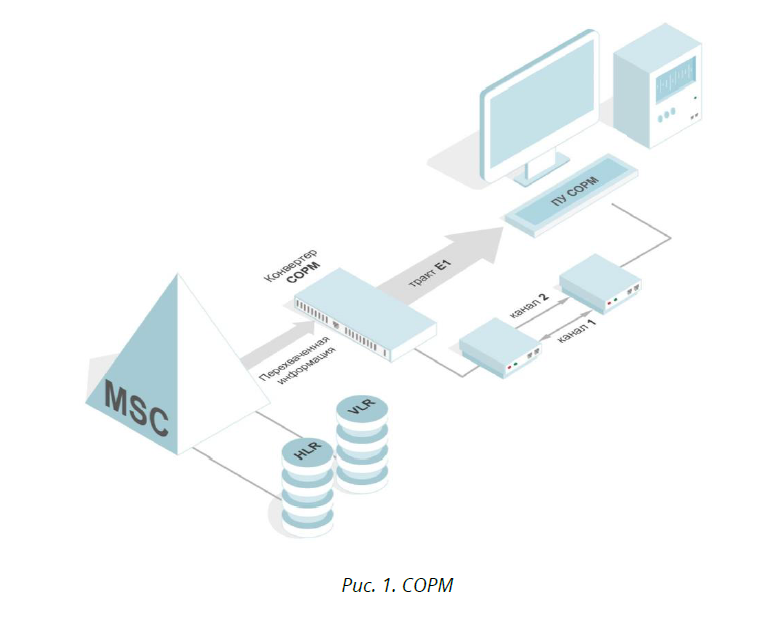
Practical implementation of lawful interception also does not constitute anything extraordinary and is provided through interaction with the operator’s network components — you can see this in the diagram. The interception control function solves the problem of ensuring the formation of network intercept points and the problem of supporting the acquisition of interception information. Further information using specific protocols is transmitted to the SORM control panel to the interested agent.
The mobile operator accumulates the full information about subscribers. Moreover, it comes from two sources: from the subscriber's registration form (personal data) and is transferred to the billing when using the services. In the cellular network, the subscriber identification module is a SIM card, which has several parameters and, in conjunction with the special parameters of the mobile device, can tell everything about the subscriber. So, the profiles of calls (direction, number, duration), geo-targeting (determined by reference to the base station and cell), the volume and profile of traffic usage, SMS, MMS, etc. are loaded into the database of the billing system ... Of course, the operator takes unprecedented measures to protect this information, however leaks happen and the general public learns about many.
In addition to the threat of billing compromise, the danger can also come from carrier services. So an innocent parental control service, or any tracking service, can be perfectly used to track the movement of a subscriber.
Many of us have heard of spy scandals, software bookmarks and wiretaps that we get to ourselves as soon as we buy a cell phone. Indeed, today's devices are extremely flexible in setting up various tracking systems, and this is due to the fact that the devices have a lot of software component, full-fledged operating systems have appeared. It is unlikely that anyone will argue that it is much easier to write a program and implement it in the logic of the operating system than to look for ways to physically intercept data. An additional threat is created by the continuous connection of the device to the Internet and the transmission of geotargeting tags. And of course, it would not be superfluous to remember that a company’s director can be given a new-fashioned telephone in which special programs are simply installed that are ready to collect the necessary data.

Perhaps this is the most interesting source of danger in the style of techno-thriller. In the first generation cellular communication systems, the confidentiality of a conversation was difficult to solve — in view of the analog nature of the speech signal, interception could be accomplished with a fairly simple device. In modern systems to protect the conversation has become incomparably easier - thanks to digital coding. In digital coding, analogue speech is converted to a stream of binary data to be encrypted, scrambled, and so on ... However, there are an incredible number of ways to intercept traffic at the "physical" level. We will tell about several of them.
False base station (IMSI trap), which lowers the level of encryption installed on the network and greatly facilitates data interception. It works with a unique identifier registered in the SIM-card - IMSI (International Mobile Subscriber Identity). It is hard to believe, but this is really a small device, which is an imitation of a cell tower. The GSM communication standard provides for mandatory machine authentication in the network in the absence of such an obligation from the network itself. The trap disables encryption, collects data and transmits an already open signal to the base station (of course, the trap is not able to connect the subscriber).
Unprotected access to a Wi-Fi network or imitation of points are also a way to intercept traffic in a radio channel. Fraudsters use special sniffers (traffic analyzers), which receive information from the wireless network adapter and decode the data.
Today, devices with NFC, a short-range wireless high-frequency communication module operating at a distance of up to 20 cm, have become incredibly popular. The technology is widely used in access control systems and payment systems, built into many tablets and smartphones. This technology can be paired with a phone hacking in its immediate vicinity.
And of course, no one has canceled one of the most dangerous sources of threats in the GSM network - forgotten, lost and stolen phones. No matter how you password or encrypt them, there is always a program that can access the data. Tottoli GSM employees can only give one piece of advice - do not store important personal and commercial information in your phone and do not log in through it to critical cloud services, if you use any.
A subscriber in a GSM network is a combination of specific identifiers of a SIM card and a mobile device. The SIM card is the cornerstone of privacy protection in GSM networks. It is she who contains on her microcontroller individual user information, encryption programs, and keys.
For a mobile device, the main identifier is IMEI (International Mobile Equipment Identity). Roughly speaking, this is the factory number, which is unique for the device and is stored in it. With the help of IMEI, you can search for a stolen phone, check its original origin, prohibit equipment for security purposes. In addition, IMEI capabilities help to handle cases of fraud and prevent criminal access. This parameter is transmitted on the network.
For the subscriber, the identifier is IMSI (International Mobile Subscriber Identity - international mobile subscriber ID (individual subscriber number). This parameter is transmitted on the network. It is this identifier that is written in the SIM that turns the phone into a mobile terminal that identifies the subscriber, registers it in roaming and used for billing.
Public parameter MSISDN - (Mobile Subscriber Integrated Services Digital Number) - the mobile subscriber number of the digital network with the integration of services for communication in GSM, UMTS standards, etc. It is this that is dialed when you call. This parameter is not transmitted on the network, but is comparable to the IMSI.
These parameters are sufficient to obtain the necessary operational information and use this data for analytical conclusions. Having these identifiers by means of SORM, interception complexes and other activities, you can get the following information on the subscriber:
It is time to return to the discussion of special SIM-cards that can protect the subscriber from potential threats, which is especially valuable for the corporate network.
Above were listed threat models. Now I would like to describe our technologies to minimize these threats.
Consider a few specific examples of the implementation of protection against threats in the technology Tottoli-GSM.
A subscriber of a usual SIM card after dialing a number presses a call key. At this point, the phone, via the high-speed control channel FACCH, sends an ALERT signal through the BSS (base station subsystem) to the BCS (base station controller), informing it of the connection request. BCS sends the received message to the MCS switching center, adding to it the id of the cell in which the mobile device is located. After that, the switch sends the AddressComplete message to the initiating subscriber who hears the beeps, and his opponent sends an incoming call signal (the telephone rings). Knowing the mobile number of one of the subscribers (MSIDIN) you can get all the details of the call and the session itself from the operator’s billing or intercept the session using certain technical means.
When the call key is pressed, the subscriber Tottoli GSM resets the call. At the same time, a command is transmitted to the server PBX (automatic telephone exchange) Tottoli GSM Security via an encrypted signal channel. The Tottoli GSM PBX via SSN7 (SS7) requests the VLR (visiting register) in order to allocate a temporary MSRN (Mobile Station Roaming Number) for this SIM card and for this call. The MSRN is a temporary identifier and routes the call from the MSC of the gateway to the MSC / VLR where the subscriber is located. As soon as the operator has allocated to our SIM card MSRN, the PBX Tottoli GSM starts the procedure for calling this MSRN. At this moment there is a call on Tottoli GSM. After the subscriber Tottoli GSM picked up the phone, the first shoulder opens. Next, the PBX Tottoli GSM starts the procedure for dialing the second subscriber. After the second subscriber picks up the phone, the second shoulder opens (Call Back technology).
With this logic of making a call, it is impossible to obtain information from the operator’s billing, since it is not known which operator has Tottoli GSM at the moment and there is no public MSISDN identifier that could be used to obtain IMSI, Ki and IMEI parameters. Even if the called subscriber is in control, it is impossible to establish the caller, since the session consists of two shoulders, in the gap of which the server PBX Tottoli GSM is located. The subscriber’s communication circle remains unknown to interested parties.
A call to a regular SIM card is carried out in accordance with standard procedures. After completing the call procedure and assigning a TMSI (temporary mobile subscriber identifier allocated to a user on the network), the VLR coverage area, which initiates the identification procedure of the mobile station and determines the set of services available to the subscriber, causes the traffic to land and the session is considered to be established. In this case, the operator’s billing records from which device the call is initiated, the location of the receiving device at the time of the session (location), the duration of the call, the parameters for applying additional services, etc.
A call to Tottoli GSM is performed as follows: Tottoli GSM is assigned a virtual DID number, which takes the call from the network, converts it using the SIP protocol and routes it to the PBX Tottoli GSM. In essence, a DID is a fixed telephone number in different geographic zones, which is programmed to be redirected to a VoIP device, a computer, or to a PSTN number or GSM telephone network. In turn, the Tottoli GSM PBX determines the specific subscriber to whom this DID is assigned, and starts the call procedure described above. Obviously, with such a call logic, it is impossible to determine the location of Tottoli GSM, since this does not allow making Tottoli GSM PBXs.
Taking into account the fact that operators are actively introducing subscriber search mechanisms into their networks by phonetic features (voice imprint), Tottoli GSM makes it possible to distort the acoustic characteristics for incoming and outgoing calls. This mechanism is especially useful if a call from Tottoli GSM is made to a regular SIM.
Perhaps each of us has information that we would like to protect. When it comes to the private sphere, the dissemination of this information entails a variety of risks that are rarely serious for the owner. If we are talking about corporate information, the risk of its compromise or loss can be extremely expensive. If you have something to lose, you should think about how to save it, including using Tottoli GSM. Hunters for valuable information are not asleep.
The high level of mobile penetration, the tremendous pace of development of mobile devices, the high marginality of services for operators, convenience and reliability for subscribers have made mobile communication an integral part of our life, including business. Millions of minutes of corporate calls go through GSM networks every day. Most often, everything goes well, but do not forget about the existing sources of threats in cellular networks.
That was the beginning of our future post about the threats that arise in the GSM network. But recently, a post about a story with duplicates was published on Habré. In the comments, there was a vigorous discussion of security issues at the SIM level and even a proposal to create a business by selling “numbers that cannot be stolen” At Tottoli GSM, we immediately decided to slightly change the publication and tell in detail not only about the threats, but also about the simple protection method that has already been invented and successfully used.
')

It is worth starting with the fact that complete security within the framework of GSM-communication is a myth. Those who try to say the opposite, at the very least, are misleading people, and sometimes they are just scammers. Modern technologies can quite successfully cope with existing encryption algorithms protection mechanisms in the GSM network.
Tottoli GSM is not a theoretical expert who models sources of threats and searches for ideal solutions “in a vacuum”. Tottli GSM is a company with practical experience in developing solutions for SIM-cards and this article is the dry residue of many years of practical experience. There are quite a lot of materials related to the demonstration of the interception of the GSM signal, the remote hacking of SIM cards and the like. But here it must be borne in mind that all of these stories took place in either a specific laboratory environment, or super-expensive equipment was used. We proceed from the everyday practice of communicating subscribers, and protecting their privacy from unauthorized intrusion, assuming that no one can give 100% protection. At the same time, our technologies allow us to make communication secure at a high level. Our task is to talk about the threats and the possible method of protection, the safety of your communication is your decision.
Sources of threats. Source number 1. SORM
SORM - a system of technical means to ensure the functions of operational search activities. Speaking openly, this is a forced evil, prescribed by law, which obliges telecoms operators to implement the system. Otherwise, the mobile operator may be deprived of the license. For the sake of justice, it is worth noting that the laws of the Russian Federation, and by-laws and regulations, as well as the very logic of the SORM system, protects cellular subscribers from abuse by authorized persons.
From an engineering point of view, SORM is a control panel (PU) that allows you to send commands to the network and receive answers and data to requests. With the development of mobile and convergent communications, as well as the provision of text, voice and Internet services in GSM networks, SORM experienced an upgrade and turned into a serious hardware-software complex, without losing its original logic. In addition to the usual components, special mediators are now included in the delivery, which are designed to process and transmit heterogeneous information to a single PU SORM. In fact, PU SORM has become a highly loaded distributed information center - after all, its task is to process enormous amounts of information coming through multi-service traffic channels (voice, mail, Internet, media, etc.), you should not even talk about the heterogeneity of traffic in the new generation NGN networks.

Practical implementation of lawful interception also does not constitute anything extraordinary and is provided through interaction with the operator’s network components — you can see this in the diagram. The interception control function solves the problem of ensuring the formation of network intercept points and the problem of supporting the acquisition of interception information. Further information using specific protocols is transmitted to the SORM control panel to the interested agent.
Source number 2. Service Provider - Mobile Operator
The mobile operator accumulates the full information about subscribers. Moreover, it comes from two sources: from the subscriber's registration form (personal data) and is transferred to the billing when using the services. In the cellular network, the subscriber identification module is a SIM card, which has several parameters and, in conjunction with the special parameters of the mobile device, can tell everything about the subscriber. So, the profiles of calls (direction, number, duration), geo-targeting (determined by reference to the base station and cell), the volume and profile of traffic usage, SMS, MMS, etc. are loaded into the database of the billing system ... Of course, the operator takes unprecedented measures to protect this information, however leaks happen and the general public learns about many.

In addition to the threat of billing compromise, the danger can also come from carrier services. So an innocent parental control service, or any tracking service, can be perfectly used to track the movement of a subscriber.
Source No. 3. Manufacturers of mobile devices and control systems (Operating System)
Many of us have heard of spy scandals, software bookmarks and wiretaps that we get to ourselves as soon as we buy a cell phone. Indeed, today's devices are extremely flexible in setting up various tracking systems, and this is due to the fact that the devices have a lot of software component, full-fledged operating systems have appeared. It is unlikely that anyone will argue that it is much easier to write a program and implement it in the logic of the operating system than to look for ways to physically intercept data. An additional threat is created by the continuous connection of the device to the Internet and the transmission of geotargeting tags. And of course, it would not be superfluous to remember that a company’s director can be given a new-fashioned telephone in which special programs are simply installed that are ready to collect the necessary data.

Source number 4. Interception of traffic in the radio channel (interception complexes: active, semi-active, passive, and other means of interception)
Perhaps this is the most interesting source of danger in the style of techno-thriller. In the first generation cellular communication systems, the confidentiality of a conversation was difficult to solve — in view of the analog nature of the speech signal, interception could be accomplished with a fairly simple device. In modern systems to protect the conversation has become incomparably easier - thanks to digital coding. In digital coding, analogue speech is converted to a stream of binary data to be encrypted, scrambled, and so on ... However, there are an incredible number of ways to intercept traffic at the "physical" level. We will tell about several of them.
False base station (IMSI trap), which lowers the level of encryption installed on the network and greatly facilitates data interception. It works with a unique identifier registered in the SIM-card - IMSI (International Mobile Subscriber Identity). It is hard to believe, but this is really a small device, which is an imitation of a cell tower. The GSM communication standard provides for mandatory machine authentication in the network in the absence of such an obligation from the network itself. The trap disables encryption, collects data and transmits an already open signal to the base station (of course, the trap is not able to connect the subscriber).
Unprotected access to a Wi-Fi network or imitation of points are also a way to intercept traffic in a radio channel. Fraudsters use special sniffers (traffic analyzers), which receive information from the wireless network adapter and decode the data.
Today, devices with NFC, a short-range wireless high-frequency communication module operating at a distance of up to 20 cm, have become incredibly popular. The technology is widely used in access control systems and payment systems, built into many tablets and smartphones. This technology can be paired with a phone hacking in its immediate vicinity.

And of course, no one has canceled one of the most dangerous sources of threats in the GSM network - forgotten, lost and stolen phones. No matter how you password or encrypt them, there is always a program that can access the data. Tottoli GSM employees can only give one piece of advice - do not store important personal and commercial information in your phone and do not log in through it to critical cloud services, if you use any.
Does the network know the subscriber in person?
A subscriber in a GSM network is a combination of specific identifiers of a SIM card and a mobile device. The SIM card is the cornerstone of privacy protection in GSM networks. It is she who contains on her microcontroller individual user information, encryption programs, and keys.
For a mobile device, the main identifier is IMEI (International Mobile Equipment Identity). Roughly speaking, this is the factory number, which is unique for the device and is stored in it. With the help of IMEI, you can search for a stolen phone, check its original origin, prohibit equipment for security purposes. In addition, IMEI capabilities help to handle cases of fraud and prevent criminal access. This parameter is transmitted on the network.
For the subscriber, the identifier is IMSI (International Mobile Subscriber Identity - international mobile subscriber ID (individual subscriber number). This parameter is transmitted on the network. It is this identifier that is written in the SIM that turns the phone into a mobile terminal that identifies the subscriber, registers it in roaming and used for billing.
Public parameter MSISDN - (Mobile Subscriber Integrated Services Digital Number) - the mobile subscriber number of the digital network with the integration of services for communication in GSM, UMTS standards, etc. It is this that is dialed when you call. This parameter is not transmitted on the network, but is comparable to the IMSI.
These parameters are sufficient to obtain the necessary operational information and use this data for analytical conclusions. Having these identifiers by means of SORM, interception complexes and other activities, you can get the following information on the subscriber:
- using IMEI, you can get all IMSI SIM cards that were used in this device and, as a result, all billing data on these SIM cards (location, social circle, SMS, MMS, voice, URLs, logins and passwords, etc.);
- using IMSI, you can get all IMEI devices and IMSI SIM cards that were used in these devices and as a result all the same billing data as in the previous case becomes available.
It is time to return to the discussion of special SIM-cards that can protect the subscriber from potential threats, which is especially valuable for the corporate network.
Methods of dealing with threats in the GSM network on the platform Tottoli GSM
Above were listed threat models. Now I would like to describe our technologies to minimize these threats.
- We use several profiles on the same SIM card, with the ability to rotate the profile by air (OTA). (For clarification: a profile is a set of identifiers (IMSI + KI)).
- We do not use a public MSISDN identifier, we use DID numbers or FMC numbers within the network.
- The procedure for selecting a BTS (base station) does not allow the use of standard algorithms for cell selection. We use our algorithms as much as our capabilities allow. This mechanism is designed to avoid interception complexes. We use various unmasking factors inherent in the interception complexes, the SIM card applet and the interaction mechanism of the SIM card and our server for the necessary calculations. Based on the findings, we prohibit the operation of our SIM card with a tower, which is suspicious.
- Within the Tottoli GSM platform, there is no personalized billing with operators.
Consider a few specific examples of the implementation of protection against threats in the technology Tottoli-GSM.
Call
A subscriber of a usual SIM card after dialing a number presses a call key. At this point, the phone, via the high-speed control channel FACCH, sends an ALERT signal through the BSS (base station subsystem) to the BCS (base station controller), informing it of the connection request. BCS sends the received message to the MCS switching center, adding to it the id of the cell in which the mobile device is located. After that, the switch sends the AddressComplete message to the initiating subscriber who hears the beeps, and his opponent sends an incoming call signal (the telephone rings). Knowing the mobile number of one of the subscribers (MSIDIN) you can get all the details of the call and the session itself from the operator’s billing or intercept the session using certain technical means.
When the call key is pressed, the subscriber Tottoli GSM resets the call. At the same time, a command is transmitted to the server PBX (automatic telephone exchange) Tottoli GSM Security via an encrypted signal channel. The Tottoli GSM PBX via SSN7 (SS7) requests the VLR (visiting register) in order to allocate a temporary MSRN (Mobile Station Roaming Number) for this SIM card and for this call. The MSRN is a temporary identifier and routes the call from the MSC of the gateway to the MSC / VLR where the subscriber is located. As soon as the operator has allocated to our SIM card MSRN, the PBX Tottoli GSM starts the procedure for calling this MSRN. At this moment there is a call on Tottoli GSM. After the subscriber Tottoli GSM picked up the phone, the first shoulder opens. Next, the PBX Tottoli GSM starts the procedure for dialing the second subscriber. After the second subscriber picks up the phone, the second shoulder opens (Call Back technology).
With this logic of making a call, it is impossible to obtain information from the operator’s billing, since it is not known which operator has Tottoli GSM at the moment and there is no public MSISDN identifier that could be used to obtain IMSI, Ki and IMEI parameters. Even if the called subscriber is in control, it is impossible to establish the caller, since the session consists of two shoulders, in the gap of which the server PBX Tottoli GSM is located. The subscriber’s communication circle remains unknown to interested parties.
Receive a call
A call to a regular SIM card is carried out in accordance with standard procedures. After completing the call procedure and assigning a TMSI (temporary mobile subscriber identifier allocated to a user on the network), the VLR coverage area, which initiates the identification procedure of the mobile station and determines the set of services available to the subscriber, causes the traffic to land and the session is considered to be established. In this case, the operator’s billing records from which device the call is initiated, the location of the receiving device at the time of the session (location), the duration of the call, the parameters for applying additional services, etc.
A call to Tottoli GSM is performed as follows: Tottoli GSM is assigned a virtual DID number, which takes the call from the network, converts it using the SIP protocol and routes it to the PBX Tottoli GSM. In essence, a DID is a fixed telephone number in different geographic zones, which is programmed to be redirected to a VoIP device, a computer, or to a PSTN number or GSM telephone network. In turn, the Tottoli GSM PBX determines the specific subscriber to whom this DID is assigned, and starts the call procedure described above. Obviously, with such a call logic, it is impossible to determine the location of Tottoli GSM, since this does not allow making Tottoli GSM PBXs.
Phonetic control
Taking into account the fact that operators are actively introducing subscriber search mechanisms into their networks by phonetic features (voice imprint), Tottoli GSM makes it possible to distort the acoustic characteristics for incoming and outgoing calls. This mechanism is especially useful if a call from Tottoli GSM is made to a regular SIM.
Perhaps each of us has information that we would like to protect. When it comes to the private sphere, the dissemination of this information entails a variety of risks that are rarely serious for the owner. If we are talking about corporate information, the risk of its compromise or loss can be extremely expensive. If you have something to lose, you should think about how to save it, including using Tottoli GSM. Hunters for valuable information are not asleep.
Source: https://habr.com/ru/post/269407/
All Articles