Panda Adaptive Defense 360: Adapting IT Security to New Enterprise Needs
Malware Panorama
In recent years, the malware panorama has undergone major changes: firstly, the number of threats in circulation has rapidly increased, and secondly, they have become more difficult to detect. Nowadays, hundreds of thousands of new malware variants appear every day, while methods for overcoming protection systems and masking threats have become much more sophisticated, making corporate networks more vulnerable to targeted attacks and zero-day threats than ever earlier.
')
Protecting computers from attack is very difficult. Protection should include a wide range of modules, including traditional antivirus, personal firewall, web filtering and mail protection, device control. Plus, any defense should provide an additional barrier against difficult-to-find targeted attacks and zero-day attacks.
Traditional endpoint security solutions are effective in blocking known threats using detection techniques based on signature files and heuristic algorithms.

However, they are not able to protect against targeted attacks and zero-day threats that use the “window of opportunity” - the time between the emergence of a new virus and the release of the antidote by antivirus companies. The increasing gap is used by hackers to spread viruses, encryptors, Trojans and other types of threats in corporate networks.
In addition, lately we are increasingly hearing about the "constant threats of increased complexity" ( APT ). Such threats prefer to secretly penetrate into the IT system of the enterprise and, being there for several months or even years, carry out their malicious actions: as a rule, it is theft of confidential information. An alarming situation arises when an enterprise, confident in the effectiveness and reliability of its defense, is not even aware of serious problems.
It should be noted that any enterprise can become a target: not only large, but also small ones. It is often easier for hackers to hit hundreds of small companies and to demand a corresponding ransom for confidential or personal information from each of them. Unfortunately, to save such information, many are forced to pay. It should be noted that backup systems in some cases are not a salvation, because hackers can blackmail an enterprise by publishing stolen information.
Protection needs of enterprises
It turns out that in most cases, enterprises are forced to acquire and maintain a number of products from different manufacturers to protect endpoints. In many cases, this may be unjustified: on the one hand, the cost of acquiring all the required security solutions increases, and on the other hand, the maintenance of such integrated systems becomes more complex (again, more expensive).
Obviously, businesses need a security system, but how powerful should it be?
In our opinion, enterprises should be able to prevent attacks, and if preventive measures fail, then the CIO should have automated means of responding to attacks and eliminating consequences. The complex itself should ensure the operation of the security system in the following areas:
- proactive attack detection;
- prompt collection of necessary information to effectively respond to security flaws;
- automatic application of recovery actions to minimize the effects and scale of attack / infection.

It is necessary to take into account the important fact that the security system should not interfere with the business processes of the enterprise. For any enterprise, the business itself is important. Everything else is secondary and should be aimed at increasing sales, profits, work efficiency, etc. Too strict security measures can interfere with the daily work of the company's employees. In other words, security should not be a brake, but should be an intermediary.
In addition, in the era of BYOD , distributed and remote offices, when using different cloud services, it is too difficult and costly to establish strict rules of control over information flows. Most likely, it is necessary to move from control to understanding and monitoring the flow of information: who, how and when got access to this or that information, where it was sent (inside or outside the company).
Thus, on the one hand, employees are asked not to interfere with their daily tasks, and on the other hand, IT administrators want to provide their enterprise with a higher level of security with less effort and expense.

What is Panda Adaptive Defense 360
For the past 5 years, Panda Security has been actively researching and developing a new cloud services family that will allow enterprises to get a comprehensive security solution to protect not only against traditional threats, but also targeted attacks, zero-day threats and other unknown threats of a new generation. In addition to a high level of protection, such a solution should be easy to implement, easy to use and manage, and inexpensive in terms of total cost of ownership.

In September, Panda Security introduced a new solution - Panda Adaptive Defense 360 . What it is?
According to the developers, Panda Adaptive Defense 360 is the first and only cloud solution, combining in a single solution the endpoint protection capabilities (EPP) , as well as attack detection and response (EDR) to protect against zero-day threats and targeted attacks, that take advantage of the “window of opportunity for malware”. Adaptive Defense 360 also allows you to automate the solution of various IT issues, reducing the burden on IT staff.
Panda Adaptive Defense 360 is a complete integration (within a single management console and a single interface) of two Panda cloud solutions, which, if necessary, can be purchased separately. The functions of the EPP solution are provided by one of the best-in-class Panda Endpoint Protection Plus solutions, which offers simple and centralized profile-based protection, recovery system, real-time reporting and monitoring, centralized device monitoring and web monitoring with URL filtering. This solution is designed to protect systems running Windows, Linux and Android.
To combat targeted attacks and zero-day threats, the capabilities of the Panda Adaptive Defense solution are used, which is a cloud-based EDR service that can correctly classify each application running on enterprise computers, allowing only legitimate programs to run.
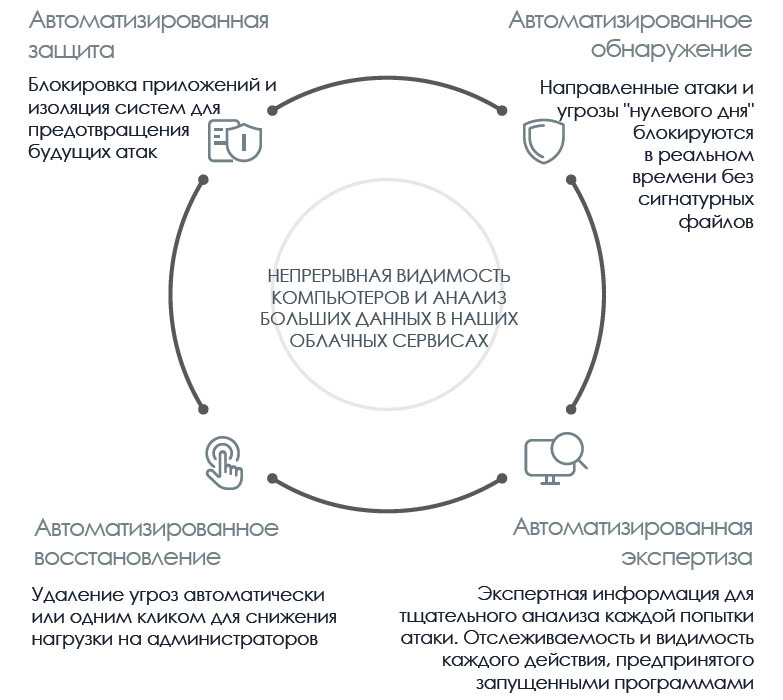
EDR’s Panda Adaptive Defense 360 capabilities are based on a security model based on three principles: continuous monitoring of applications on the company's computers and servers, automatic classification using machine learning on our Big Data platform, and our technical experts analyzing those applications cannot be classified automatically. All this allows you to accurately determine the behavior of all programs running in corporate systems.
Thus, these capabilities are now combined with Panda's best EPP solution, closing the cycle of adaptive threat protection, which now includes automated protection, detection, examination and recovery.
Key Features of Panda Adaptive Defense 360
Being a cloud service, the entire infrastructure of this solution is located in the cloud - in Microsoft data centers on the Windows Azure platform, with the highest level of physical and information security. Therefore, to work with this solution, you only need a regular web browser and registration data for secure access to the web management console.
The solution contains the following elements:
• A web-based console , accessible anytime from anywhere, for remote and centralized security management of endpoints;
• Local agents , centrally and remotely installed from the web console in automatic mode. Local agents contain local protection technologies (signatures, heuristics, behavioral analysis) with the possibility of two-way automated “communication” with the central cloud knowledge base in real time;
• The cloud knowledge base Collective Intelligence , containing dynamic information about malware (malware) and non-malicious (goodware) applications, objects, files and codes. This knowledge base allows you to “advise” local agents in real-time when detecting suspicious files and codes: in the case of malware, provide a micro vaccine for treatment or place it in centralized quarantine for subsequent analysis; in the case of goodware, give a “hang up” to local agents and reduce the level of false positives.
The following are the main characteristics of Panda Adaptive Defense 360, grouped by task type:
DETECTION AND RESPONSE
• Protecting intellectual assets from targeted attacks
• Expert report
• Protection of vulnerable systems
• Continuous monitoring and analysis of running applications
• Monitoring access and data transfer for applications
PROTECTION
• Antivirus protection against malware
• Personal and centrally managed firewall
• Device Control
• URL filtering
• Exchange mail traffic filtering (antivirus, antispam, content filter)
PERFORMANCE AND MANAGEMENT
• Simple and centralized management from a single web console (security profiles, user groups, quarantine, etc.)
• Easy implementation (own distribution utility and MSI installers for third-party utilities when deploying local protection agents on the local network, generating a URL for mailing for automatic deployment of local agents on remote and mobile computers and devices)
• Lightweight agent requiring minimal system resources (high performance even on plainly old machines)
• Complete transparency for end users (automation of processes, removal of resource-intensive processes to the cloud, if necessary, hidden mode of local agents, low resource consumption);
• Automatic generation of thematic reports (summary report for management, detailed reports for IT staff) with the required frequency and automatic sending to recipients;
• Optimized update of local agents in the local network of the enterprise: centralized updates and communication with the cloud through computers specified as repositories, the ability to automatically update within the network using peer-to-peer technologies (one computer updates 10 others, etc.).
Cloud Security Model Used
At the core of Panda Adaptive Defense 360 cloud solution is a three-stage cloud model for detecting and responding to attacks. This model is implemented on the Big Data platform using machine learning technologies.
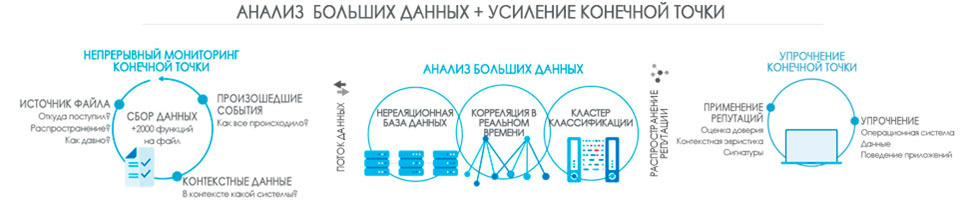
Stage 1. Endpoint Comprehensive Continuous Monitoring
Endpoint protection installed on each computer monitors all actions triggered by running processes. Each event is cataloged (based on more than 2000 characteristics) and sent to the cloud *:
• file downloads
• Software installation
• Driver Creation
• Communication processes
• DLL loading
• Service creation
• Creating and deleting files or folders
• Creating and deleting registry branches
• Local data access (over 200 formats)
Stage 2. Big Data Analysis
At this stage, the Big Data cloud platform accepts static and contextual information from local agents, as well as external third-party information for further correlation, and performs continuous classification of executable files. At the same time, automatic analysis of new applications is carried out for a maximum of 24 hours, although in practice, as a rule, no more than 4-6 hours, depending on a number of application characteristics. And only in isolated cases is it necessary to connect experts of the PandaLabs anti-virus laboratory for manual analysis.
The classification cluster allows you to classify each executable file to make a verdict: is it malicious or not. Classification is carried out on the basis of a reliability assessment — a parameter that determines whether the process can be trusted or not. If you can not trust, then the application may be prohibited to run. The assessment of the reliability of each process is recalculated based on the dynamic behavior of the process when new information is received (retrospective analysis).
Stage 3. End point hardening
At this stage, the Panda Adaptive Defense 360 solution receives from the cloud specific “instructions” for each executable file. The extended protection system can operate in three modes (for each security profile, you can configure your own individual mode of operation):
Audit
In this mode, the solution only collects and analyzes information about all executable processes, without blocking anything. This mode of operation, in fact, allows you to audit the information security of the enterprise.
Standard mode
In this mode, the service classifies all executable files with an accuracy of 99.9991%. Every process that is classified as malware is blocked immediately. The service also protects browsers and applications (Java, Adobe, Microsoft Office and others) from security holes using rules based on context and behavior. In addition, by providing data protection, the solution controls that only reliable applications can access the data and critical areas of the operating system.
Advanced mode
Advanced mode complements the standard mode of operation by blocking all unclassified applications. Those. all unclassified processes cannot be started until they have been assigned the highest level of trust (MCL) in the system. In other words, everything that is not allowed is prohibited.
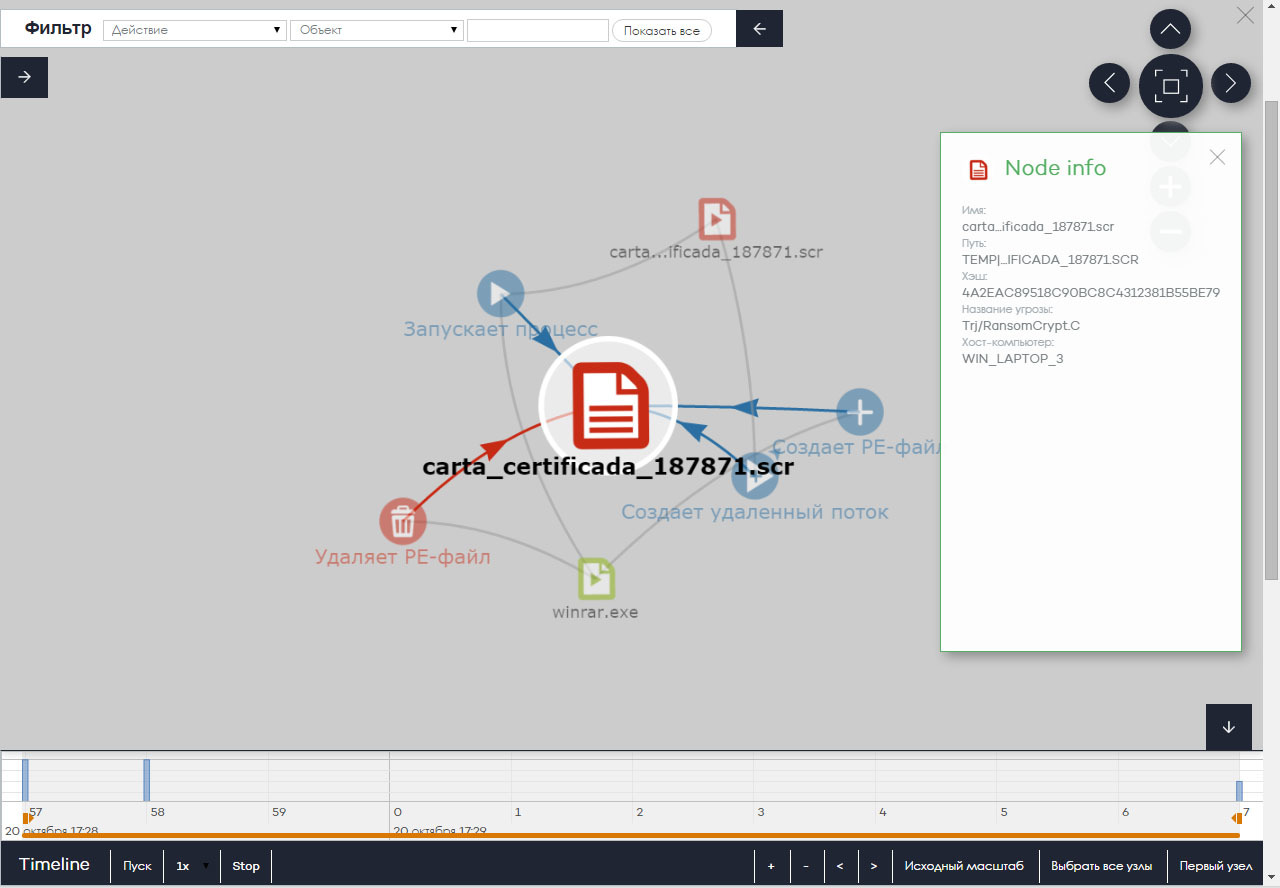
Thus, Panda Adaptive Defense 360 allows you to see the entire life cycle of any threat on the endpoints (below is the Panda Adaptive Defense 360 interface screen with data on the cryptographer):
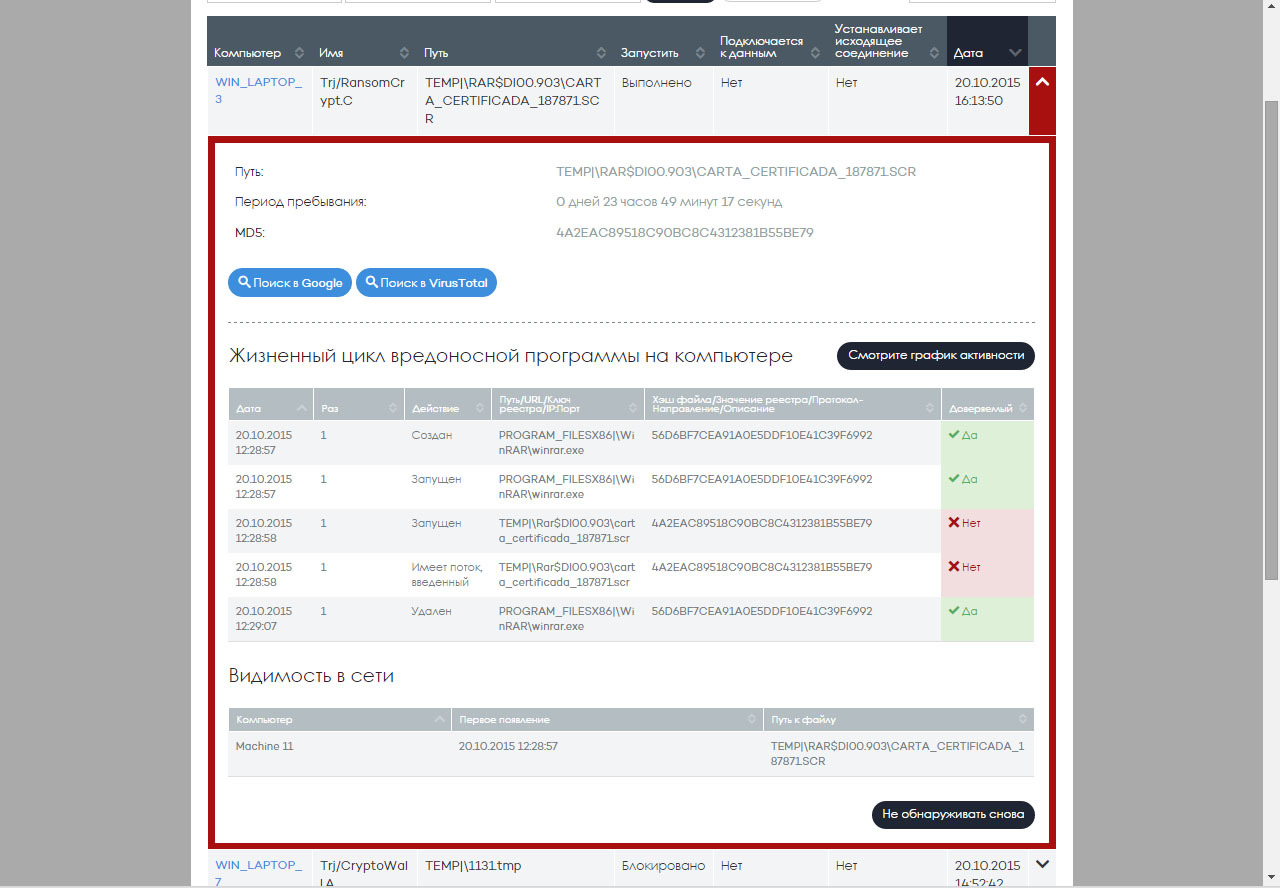
The same information is presented in the form of an activity graph, when you can see the life cycle of a threat over time and in a convenient visual form:
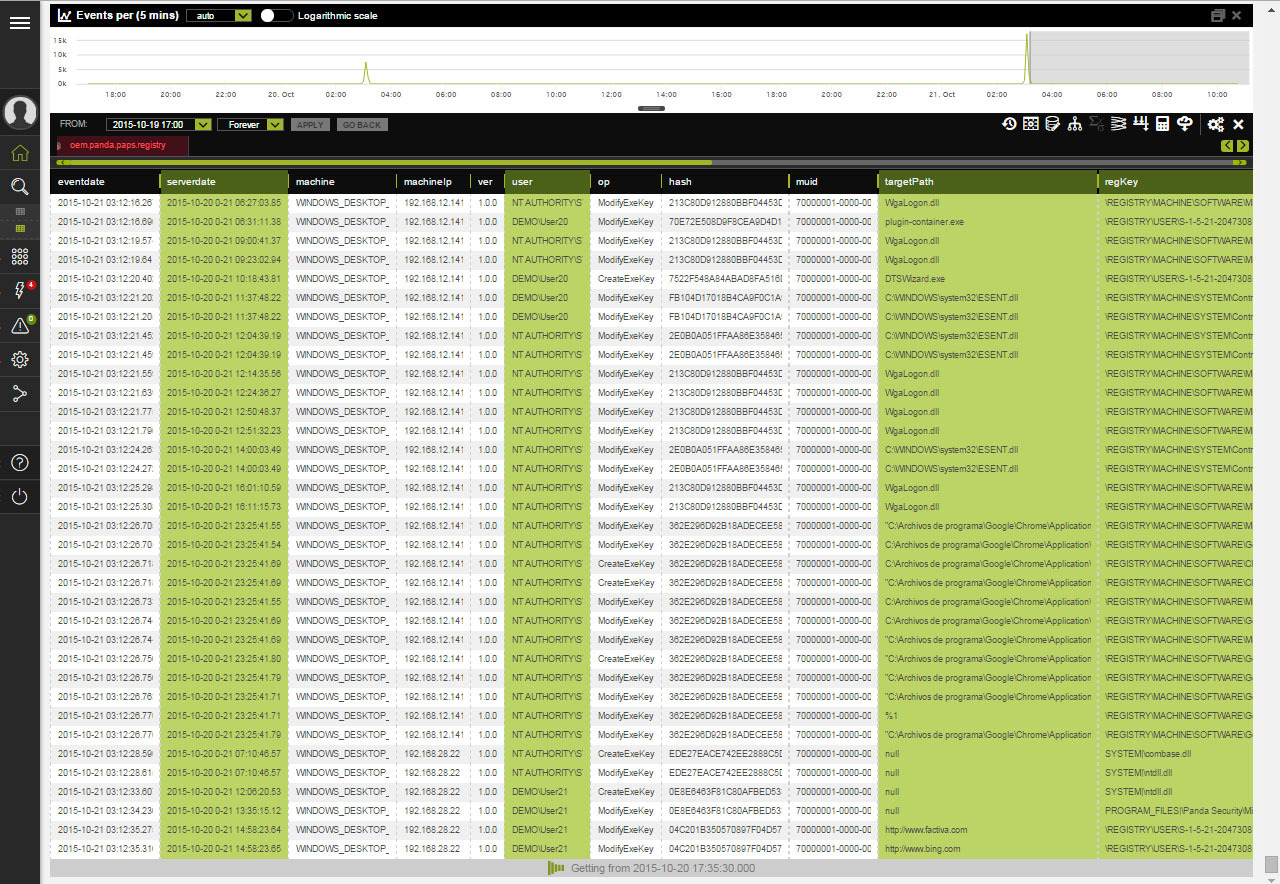
In addition, the additional external service LogTrust allows an enterprise to perform automated deep processing of all logs for obtaining expert information:
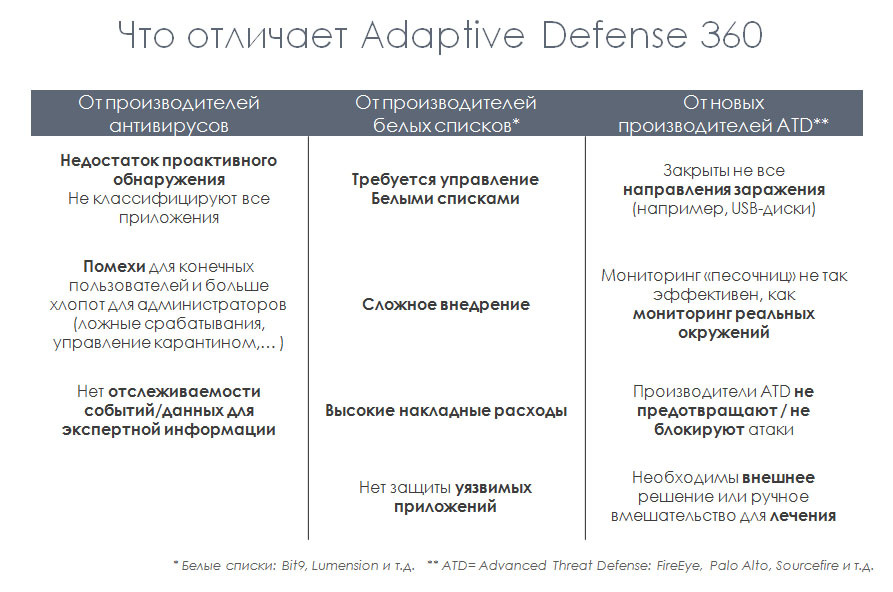
Distinctive features of Panda Adaptive Defense 360
Traditional corporate antivirus solutions to identify malware use signatures or behavioral analysis. This allows you to detect known malware, as well as identify potentially dangerous threats. Therefore, in the case of Panda Adaptive Defense 360, the main task is to protect against malicious programs that have gone unnoticed. This solution is able to detect them through continuous monitoring of all processes running on the endpoints. Due to this, the solution is able to detect APT, which for a long time can be at rest until it is activated.
In addition to detection, the solution provides integrated threat treatment. Instant access to real-time information and a history of events provide complete visibility of malware activity over time, allowing you to more accurately and accurately respond to attacks.
Panda Adaptive Defense 360 allows you to detect and block encryptors, targeted attacks and other such threats, as well as to detect unknown variants of traditional threats much more effectively. Panda Security’s own research has shown that traditional antiviruses detect only 82% of new threats in the first 24 hours , and even after 3 months this figure is only 98%, while solutions similar to Panda Adaptive Defense 360 can work in advanced mode. in the first 24 hours, reveal about 99% of new threats .
Currently, Panda Adaptive Defense 360 has classified over 1.2 billion applications , with malware detected on ALL product implementations, regardless of the presence of security systems. Currently, over 100,000 computers and servers worldwide are protected by the Panda Adaptive Defense 360 solution.
It is also worth noting that, unlike traditional solutions, Panda Adaptive Defense 360 is characterized by a low total cost of ownership: no infrastructure (hardware and software) is required for the operation of a corporate security system, its maintenance and servicing, an intuitive interface that does not require specific IT knowledge.
Conclusion
Modern attacks can bypass our traditional security solutions and remain unnoticed in our IT systems for a long time. And such threats are quite real. Those. The integrity of the enterprise security system is broken, but nobody knows about it.
According to IDC estimates, the total damage from the actions of cyber-criminals worldwide reaches about 400 billion US dollars. And do not fool yourself: any company can make a "contribution" to this sad statistics.
Panda Adaptive Defense 360 is a new generation of cloud-based integrated security systems that are available for enterprises of any size with any structure. The solution provides a high level of security from all current threats and new IT calls with a low total cost of ownership.
Dear IT professionals, it is very important for us to know your opinion.
Source: https://habr.com/ru/post/269235/
All Articles