Quantum communications: from research to technology business
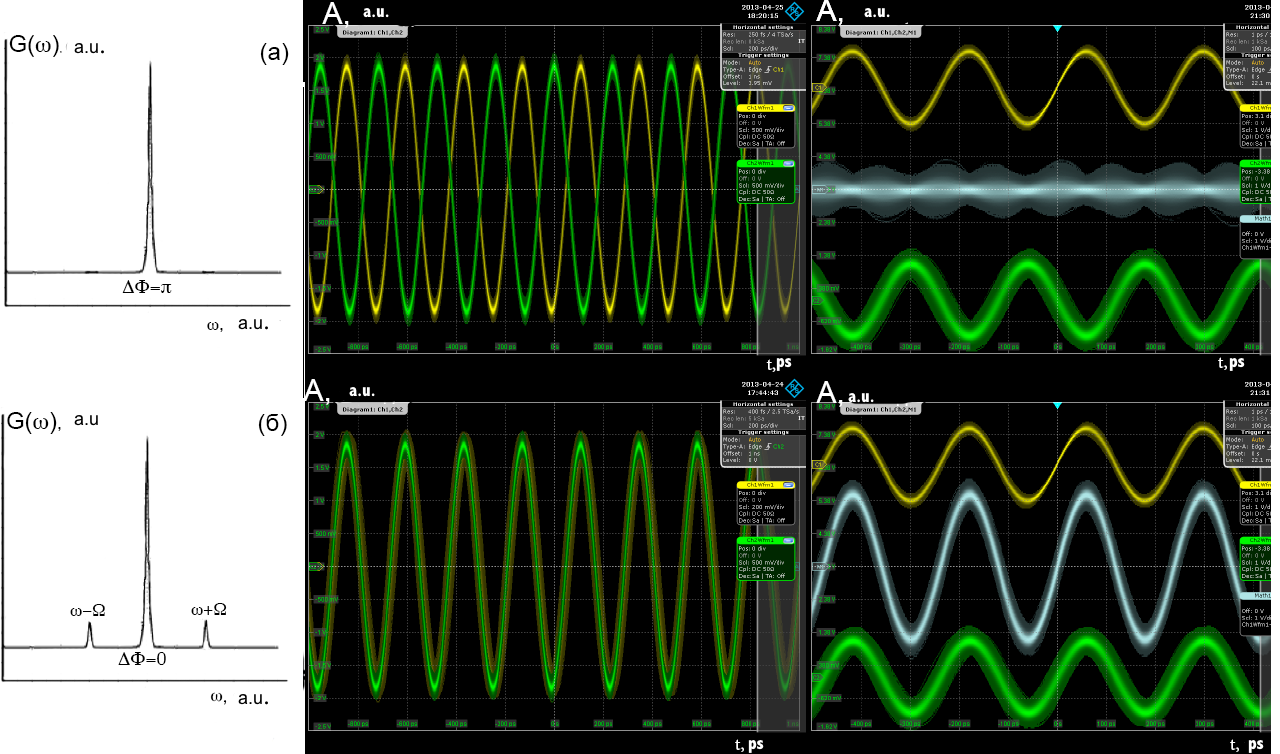
Image Link
The problem associated with the protection of personal information transmitted via public telecommunications channels is of great interest today. The possibilities of high-speed computers and quantum computers that have been intensively developed lately have greatly simplified the process of decrypting information. For example, the Pentium 4 processor managed to crack the 1024-bit RSA encryption in just over 104 hours.
Regardless of the specific implementation, the security of information today is ensured by exceeding the average decryption time over the data relevance time. This problem can be solved with the help of an “ absolutely strong cipher ” developed by C. Shannon. However, in this case, the user will face the task of exchanging unique keys before each communication session, which increases the risk of their interception and subsequent data compromise.
')
Now imagine such a line of communication, which is impossible to listen to in any way, because it is contrary to the laws of physics. Whatever the attacker tries to do, he will not be able to intercept the transmitted information. Such data transmission devices using the principles of quantum cryptography are created at Quantum Communications, LLC, a small innovative enterprise at the ITMO University .
We have achieved significant success in developing a quantum communication system for optical fibers - it has parameters that are close to and even surpass the record results obtained in laboratory systems. If we compare it with the quantum communication systems on the market, we have learned how to transmit quantum signals and, as a result, implement secure data transmission at speeds 10 times higher than the best world analogues. As for the range, we can transmit a signal 3 times farther.

Background of the project
The project began as a research project, which was conducted at the university and was purely fundamental in nature. In the course of the work, it was proposed to generate information carriers - single photons - not as a source of radiation, but as a result of phase modulation of classical pulses. Then the task was to find out: is it possible to transmit quantum signals over long distances via an optical cable in a similar way, is it possible physically?
During the tests, it was found that such modes are implemented and really allow to achieve the advantages described above in speed and range. After conducting a series of laboratory tests, a mock-up was created, which was sent to the exhibition in Lenexpo and tested by a potential audience. An experimental model has already been developed and the first mock-up of a quantum network section based on the use of subcarriers (side) frequencies connecting the university buildings has been created. This is the first in Russia experimental section of the “civil” quantum network.

Quantum cryptography systems based on subcarrier frequencies
In the quantum key distribution systems, single photons are used as carriers of the information signal, which in most cases are generated by the extreme attenuation of laser radiation. An alternative approach is proposed in quantum cryptography systems based on the use of side (subcarriers) frequencies as a result of phase-frequency modulation, quantum signals are transferred to adjacent frequency components (Figure 1).
In this case, the spectral interval between the carrier and side frequencies is determined by the parameters of the modulating signal and is of the order of 10-20 pm. Systems at the side frequencies are characterized by a higher key generation rate and a lower probability of errors. However, their main advantage is the ability to generate several side frequencies at once in the vicinity of one central one, which allows placing up to 10 independent quantum channels inside a single multiplexer window.
In combination with WDM, this technology allows you to increase the spectral efficiency of quantum cryptography systems in optical networks from today's 4% to 40% or more, implementing quantum networks with a data transfer rate of about 400 Mbps. All this makes the technology cost-effective - now the speed of the world's best quantum systems is only 1-2 Mbit / s (50 km), while the channel capacity on an Ethernet network is about 1 Gbit / s.

Fig. 1. Spectrum of the optical signal after modulation in the sender (a) and receiver unit in the case of constructive (b) and destructive (c) interference
Below (Fig. 2) is a simplified diagram of our system. A semiconductor laser generates radiation with a narrow spectrum at a wavelength of 1550 nm. After that, the radiation enters the phase modulator FM1, controlled by an electronic control unit (electronic control unit). As a result of phase modulation, two side frequencies appear in the radiation, differing from the carrier by the amount of a 4.4 GHz modulating radio signal.
The power of the side frequencies is controlled by changing the amplitude of the modulating signal. The modulated signal arrives at the attenuator AT, at the output of which the signal power at the side frequencies corresponds to the average number of photons per pulse (of the order of unity). Each bit of the transmitted signal is encoded using the phase shift ΦA added to the modulating signal. The phase shift is controlled by the electronic control unit and for each bit is randomly selected from four values: 0; π / 2; π and 3π / 2.
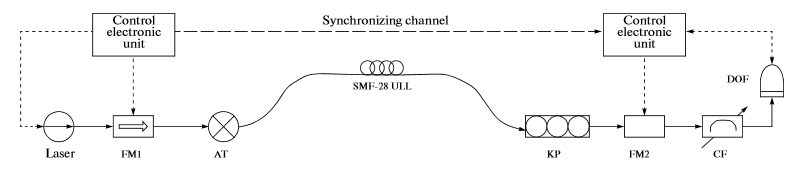
Figure 2 - Schematic diagram of a quantum cryptography system based on the use of subcarrier frequencies
The electronic control units in the transmitting and receiving modules are synchronized using a special-shaped signal: a sinusoid with a frequency of 10 MHz and a gating pulse with a duration of 10 ns. The starting strobe signal initiates the key generation, and the subsequent ones synchronize the writing of quantum samples to the buffer memory of the transmitting and receiving modules. The modulation generators of the transmitting and receiving modules synchronize the sinusoidal signal. The sync signals are transmitted via a separate optical fiber.

Image Link
Figure 3 - Spectrum and oscillogram (a) attenuating and (b) amplifying interference
The cryptographic key is generated using the BB84 protocol with a strong reference pulse. The quantum signal in the receiving module occurs when the laser passes the polarization controller, phase modulator FM2 and spectral filter SF, connected in series.
The spectral filter extracts the sideband signal, which is monitored using a DOF photon detector (counter). At this stage, the signal is re-phase modulated. The FM2 phase modulator is controlled by the electronic control unit, and the bit sequence is encoded in the same way as in the transmitting module.
The phase change frequency is 100 MHz. The phase modulator introduces a phase shift ΦB into the modulating signal; each bit shift is chosen randomly from four possible values. The resulting subcarrier power depends on the phase shifts ΦA and ΦB. If ΦA = ΦB, then amplifying interference occurs (Fig. 3b), and the power of the optical signal turns out to be nonzero. If ΦA - ΦB = π, then attenuating interference appears (Fig. 3a), and the optical signal power is comparable to the noise of the dark current of the photon detector. States with phase difference π / 2 are discarded.
The exchange of information necessary for processing the measurement results is performed over an open channel. In this case, the "raw" key is generated simultaneously in the transmitting and receiving modules. After that, for the "raw" key, an error rate (QBER) is calculated, according to which legitimate users can determine whether an attempt was made to intercept. If there was no wiretapping, the errors are corrected, and a secret cryptographic key is generated in the sending and receiving modules.
Laboratory setup
We conducted a series of experiments in the laboratory (Fig. 4). System parameters such as key generation rate and quantum error rate (QBER) at distances up to 250 km in a corning SMF-28 ULL optical fiber were measured.
Another unique Russian development in the field of photonics was used as a radiation detector: a superconducting detector of single photons based on ultrathin film (SNSPD). This device was designed and developed in Moscow by SCONTEL .

Figure 4 - Experimental setup with superconducting single-photon detector based on ultrathin film (SNSPD)
The QBER value is defined as the ratio of the number of error bits to the total number of bits received:

where R sift (the length of the "sifted" key) equals the number of coincidences of the bases of Alice and Bob (receiver and transmitter), which in turn equals half the length of the "raw" key:
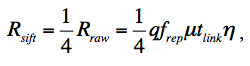
where f rep is the pulse repetition frequency, μ is the average number of photons per pulse, t link is the transfer coefficient, that is, the probability of the photon to reach the Bob detector, η is the probability of photon detection, that is, the quantum efficiency of the detector. The factor q <= 1 is introduced for systems with phase coding to account for non-interfering photons.
The results are collected in the table below and presented in the graphs.

If the transmission distance is 200 m, then the generation rate of the “sifted” key will be 200 bit / s, with QBER equal to only 1%. Remarkably, such results were obtained at a clock frequency of 100 MHz, which greatly simplifies the electronic subsystem and leaves a reserve for further speed increase (in record systems with comparable parameters, the clock frequency is of the order of 1 GHz).
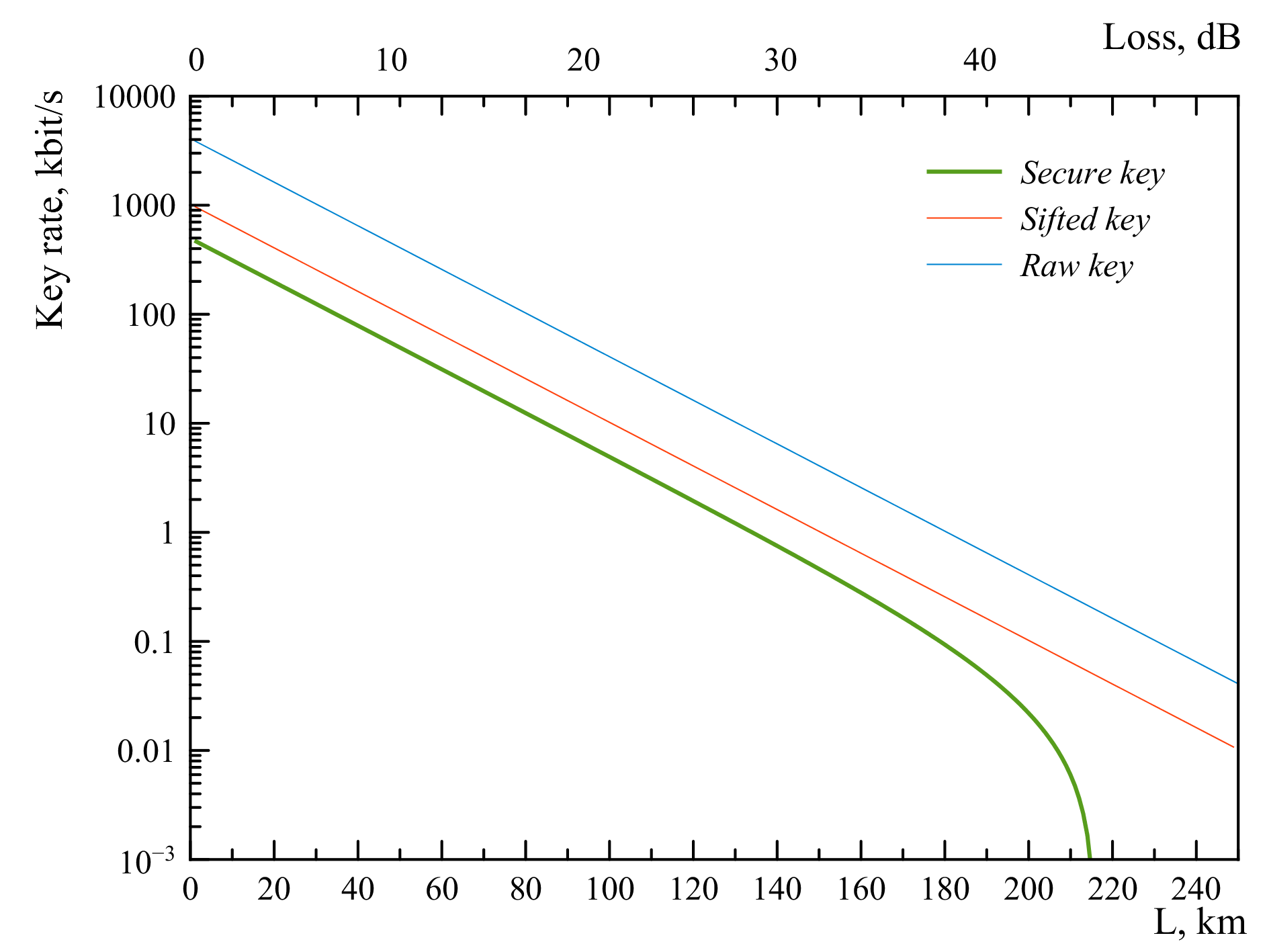
This was made possible by the engineering solutions of ITMO specialists, which made it possible to achieve a high visibility of the interference pattern (V> 98.9%) in the unidirectional channel due to precise control of the relative phase shifts and properties of the SNSPD detector (low dark count and high speed). For the maximum distance at which the experiment was carried out, the distribution rate of the "sifted" key was 28 bit / s, with a QBER of 9.3%, which still allows for the safe generation of keys.

The implementation of the system allows you to create networks of a new type, which give a new quality to a perfectly safe world: they can be embedded in the Internet of things, network concepts. This is a platform that can be used to develop integrated security and communications systems, as well as a basis for secure data transmission for other solutions. For example, to protect the control signals of unmanned aircraft.
If we approach the question from the user side, the system can be used in software that implements data exchange modes between clients. The ideology is comparable to the Android OS or iOS - the user has a platform, and with its help he solves his specific tasks. They do not have to be connected with space and military technologies - the system is suitable for solving issues as close as possible to the user. We will talk about these issues and other topics related to the prospects for using quantum networks in our next materials.
Source: https://habr.com/ru/post/269127/
All Articles