How did Cisco Security Ninja teach 20,000 employees to secure programming?
When you hear the phrase “raising awareness of information security,” what comes first to your mind? Training users not to open letters from outsiders and not to click on phishing links? Learning how to recognize social engineering? Tracking so that no stranger comes into the office, as if he is with you? We also have such a program at Cisco, and we also regularly undergo appropriate training. But today I would like to talk about our other voluntary awareness-raising program, which was created in less than six months by a team of only four people with a budget of less than 50 thousand dollars. Pay attention again. A complete program! Created by four people! Less than six months! Only for 50 thousand dollars! And more than 20 thousand employees of Cisco - engineers and developers have passed training and successfully passed the exam in this program.
History of creation
The idea of creating this initiative came in May 2012, when Adobe presented Adobe's Security Program Training program at the Security Development conference. Then we got the idea why not to create such a program in Cisco. Moreover, the problem is long overdue. There was no developer training program as such. Many people knew the principles of secure programming ( Cisco Secure Development Lifecysle , CSDL), but not everyone understood how to use them in practice to reduce the number of errors and potential vulnerabilities. Moreover, the developers, by tradition, did not think much about how the world of security develops on the other side of the barricades, how attackers act, what they can and where their aspirations are directed?
The idea was an idea, but we didn’t want to go along the beaten track with the organization of another safety training. After all, what to hide, many educational programs, even corporate ones, even free ones, are considered by many employees as punishment and inevitable evil. With such an attitude, it was not worth waiting for a big effect. Therefore, we decided to practice our practice in secure programming and creating trusted systems, which we have been actively developing in recent years, to combine with the experience of our incident response unit in our own products ( Cisco Product Security Incident Response Team , PSIRT). And to impose on this combination a gaming component, engaging workers on their own will in an exciting game in which it would be possible to earn points, gain recognition from others and, incidentally and unobtrusively, obtain new knowledge and competencies. As you know, the information obtained in the form of a game is remembered for a much longer period than the usual theory, even clothed with beautiful presentations and videos.
')
No sooner said than done. The idea of teaching martial arts, with its combination of studying philosophy and techniques, teaching in the hall (the so-called dojo) and in life, passing through various degrees (belts), reflecting the specific achievements of the student, was taken as a basis. The participants of our program are called Cisco Security Ninja. Why ninja? Probably because for many decades or even centuries there were many legends around these Japanese warriors and their name was overgrown with many secrets. Attaching to the “secret” of CSDL is a distinctive sign of developers and engineers who have received appropriate training.
The motto of this initiative was a rehashed statement: “Security is the way, not the destination.”

Cisco Security Ninja Belts
In contrast to the traditional ten belts in martial arts, we decided to limit ourselves to five — white, green, blue, brown and black, “obtaining” of which should demonstrate the acquisition of certain knowledge and skills, as well as passing the corresponding exam.

At the first level, which serves as the basis for further growth, we introduce beginner ninja with the basic concepts of information security, terminology, the basics of secure programming, and CSDL. This training consists of 16 modules - introduction, terminology, basics of information security, conformity assessment, hackers and attacks, typical security myths, CSDL, input validation, resource overflow, authentication, authorization, secure configuration, information leaks, cryptography , security at the hardware level , PSIRT.
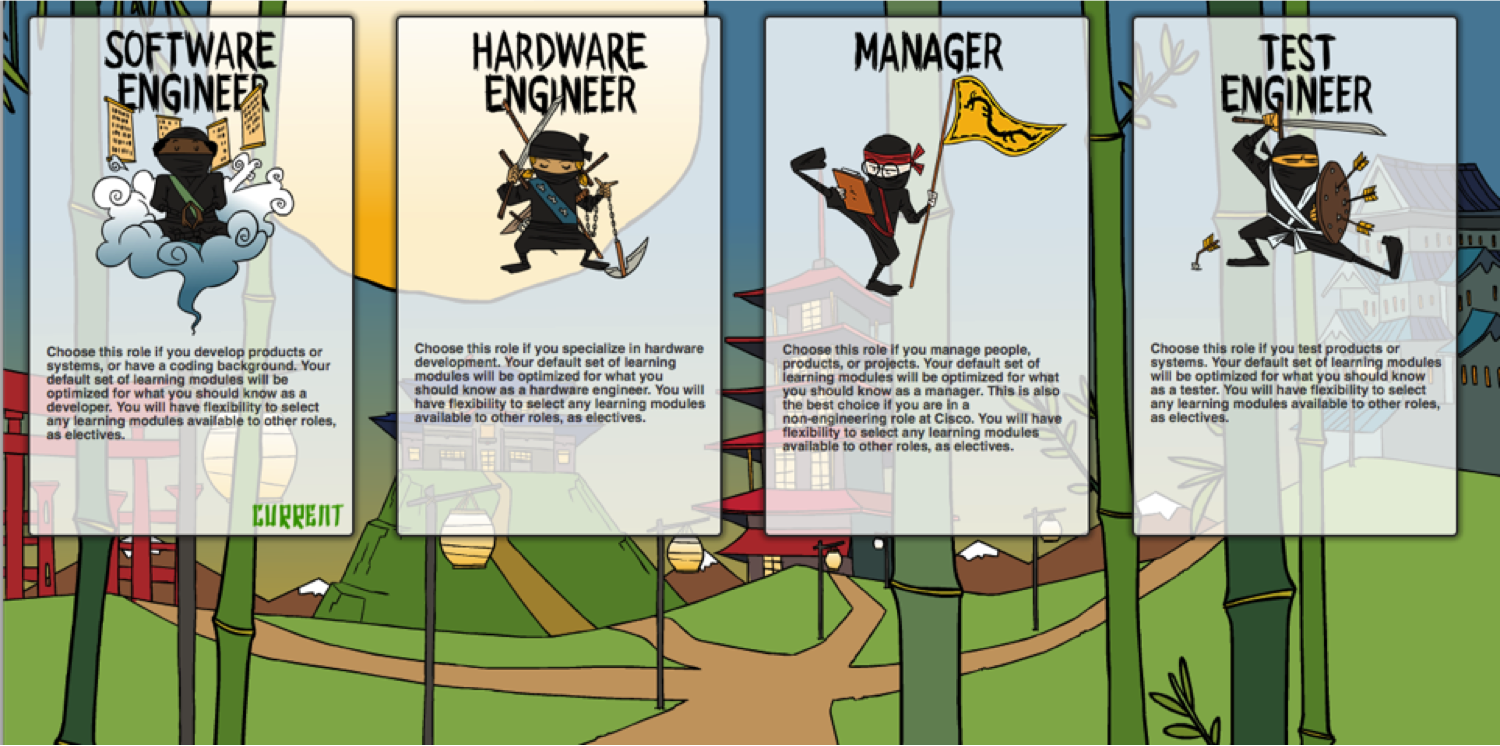
The green belt meant gaining advanced knowledge of various security concepts, as well as the practical application of safety principles and practices depending on the role of the learner. We identified six of them - product manager, program manager, manager, design engineer, development engineer, testing engineer. To get a green belt, it was necessary to go through about 50 modules - starting from studying various attacks (XSS, CSRF, SQL Injection, social engineering, hardware-level attacks) and CSDL (threat modeling, vulnerability search, code analysis, typical programming errors by C) to the basics of protecting Linux, learning Secure Boot, SSL, supply chain management and “managerial” topics.
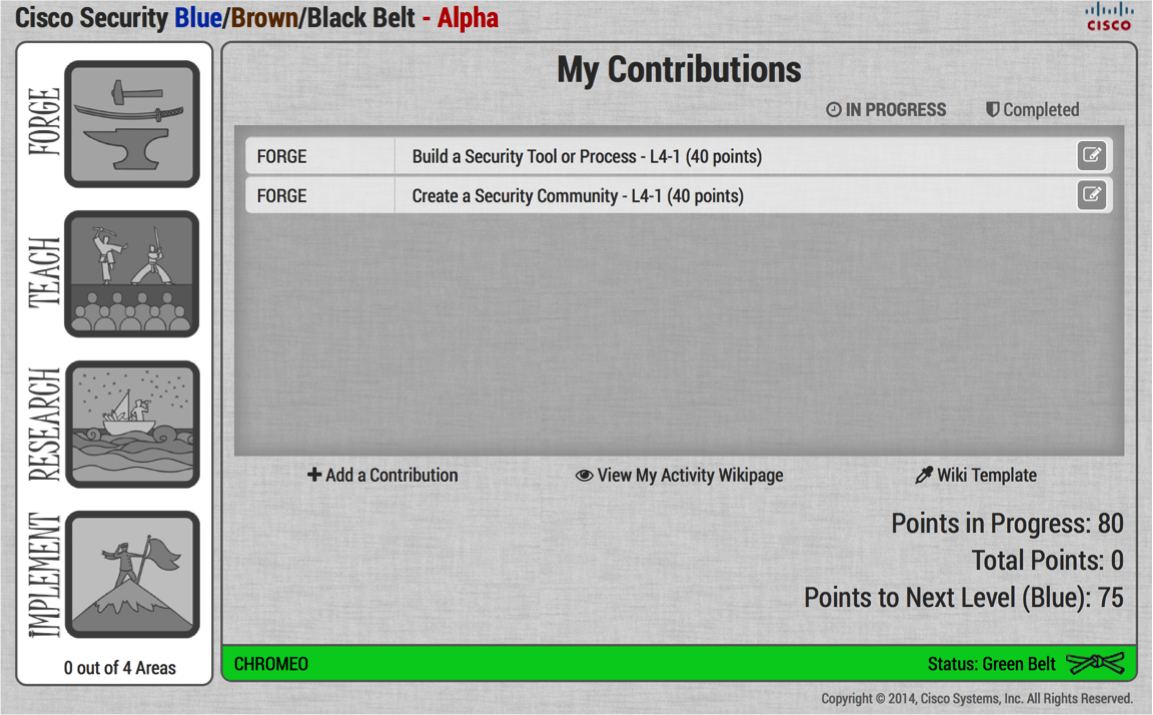
The following three belts meant no longer studying any theoretical or practical topics, but promoting the introduction of secure programming practices in Cisco activities. And the higher the belt, the more such actions need to be implemented. To eliminate uncertainty in the process of conquering the “higher” belts, all the activities that candidates for the blue / brown / black belt had to do were divided into 4 groups - an invention (for example, creating a useful tool or process or leading a community), training ( mentoring, conducting or developing courses, speeches), research (analysis of a problem, participation in an internal working group or committee, development of a security function) and implementation (test, feature, CSDL process, etc.).
For each action, there are certain points, the number of which depends on time-consuming (1 point = 1 hour) and the scale of activity (only within the team, inter-team activity, external, etc.). Then these points are summed up and, depending on the final amount, one or another degree is assigned. For example, to get a blue belt, it is enough to “earn” only 75 points, while for black you need at least 400 points out of all four of the above described activity groups. The black belt is the highest level not only in martial arts, but also in the Cisco Security Ninja program. It means recognition both inside and outside of Cisco.
Cisco Security Ninja program in numbers
We launched the program in December 2012, asking some colleagues to “try”. Having received positive feedback, in February 2013, Cisco Security Ninja officially started. In December 2013, an expanded program (on the green belt) was added to the initial training program for the “white” belt, and after a few more months, we added training by roles. December 2014 was marked by the launch of the remaining three programs to get the blue, brown and black belts.
In 2014, the program received support at the level of the company's management, which began to persistently recommend to all interested parties to get at least a white belt. It is worth noting that, until today, this program is not mandatory for employees who voluntarily join it. In March 2015, we reached the border of 20,000 employees who received their belt, of which 47 received a black belt, 22 — brown, 72 — blue, 2640 — green (among them I).
Dojo for training and exams
Dojo is a place where training, competitions and certification in oriental martial arts take place. There is a dojo (Cisco Security Dojo) and we. This is a specially designed platform that includes various activities and tools with which you can get training in various forms and pass the appropriate exams and get a well-deserved belt. Also, using this platform, all ninja security can track their status and colleagues, record their activities to achieve higher degrees and perform a number of other tasks.

Gamification
One of the most important elements of the program, which allowed, to involve more than 20 thousand people, is gamification, which was achieved through various elements:
In general, gamification is a very interesting way of conveying information security topics. We often use it in the company. There are information security stands, flash games, games for smartphones, CTF, and much more.
Confession
One of the important elements of our program was the recognition of specialists who were trained and successfully received one or another belt. We use different options - certificates, logos that can be used in your profile on the corporate portal or in the signature in e-mail messages, appropriate straps for wearing a corporate badge, financial incentives.

Key success factors
Over the past almost three years, we were able to formulate 10 criteria for the success of our program:
As a conclusion
The Cisco Security Ninja program we implemented solved several problems at once, including not only involving 20 thousand employees in the process of ensuring information security of our products, but also increasing the level of security of our solutions. Is it possible to repeat this program in another organization? In the same form hardly. Still, the culture, levels of maturity, and the companies themselves can be very different from each other. But the key success factors will be the same for everyone. The main thing is not to sit still!
And remember: safety is movement, not a destination!
History of creation
The idea of creating this initiative came in May 2012, when Adobe presented Adobe's Security Program Training program at the Security Development conference. Then we got the idea why not to create such a program in Cisco. Moreover, the problem is long overdue. There was no developer training program as such. Many people knew the principles of secure programming ( Cisco Secure Development Lifecysle , CSDL), but not everyone understood how to use them in practice to reduce the number of errors and potential vulnerabilities. Moreover, the developers, by tradition, did not think much about how the world of security develops on the other side of the barricades, how attackers act, what they can and where their aspirations are directed?
The idea was an idea, but we didn’t want to go along the beaten track with the organization of another safety training. After all, what to hide, many educational programs, even corporate ones, even free ones, are considered by many employees as punishment and inevitable evil. With such an attitude, it was not worth waiting for a big effect. Therefore, we decided to practice our practice in secure programming and creating trusted systems, which we have been actively developing in recent years, to combine with the experience of our incident response unit in our own products ( Cisco Product Security Incident Response Team , PSIRT). And to impose on this combination a gaming component, engaging workers on their own will in an exciting game in which it would be possible to earn points, gain recognition from others and, incidentally and unobtrusively, obtain new knowledge and competencies. As you know, the information obtained in the form of a game is remembered for a much longer period than the usual theory, even clothed with beautiful presentations and videos.
')
No sooner said than done. The idea of teaching martial arts, with its combination of studying philosophy and techniques, teaching in the hall (the so-called dojo) and in life, passing through various degrees (belts), reflecting the specific achievements of the student, was taken as a basis. The participants of our program are called Cisco Security Ninja. Why ninja? Probably because for many decades or even centuries there were many legends around these Japanese warriors and their name was overgrown with many secrets. Attaching to the “secret” of CSDL is a distinctive sign of developers and engineers who have received appropriate training.
The motto of this initiative was a rehashed statement: “Security is the way, not the destination.”

Cisco Security Ninja Belts
In contrast to the traditional ten belts in martial arts, we decided to limit ourselves to five — white, green, blue, brown and black, “obtaining” of which should demonstrate the acquisition of certain knowledge and skills, as well as passing the corresponding exam.

At the first level, which serves as the basis for further growth, we introduce beginner ninja with the basic concepts of information security, terminology, the basics of secure programming, and CSDL. This training consists of 16 modules - introduction, terminology, basics of information security, conformity assessment, hackers and attacks, typical security myths, CSDL, input validation, resource overflow, authentication, authorization, secure configuration, information leaks, cryptography , security at the hardware level , PSIRT.
The green belt meant gaining advanced knowledge of various security concepts, as well as the practical application of safety principles and practices depending on the role of the learner. We identified six of them - product manager, program manager, manager, design engineer, development engineer, testing engineer. To get a green belt, it was necessary to go through about 50 modules - starting from studying various attacks (XSS, CSRF, SQL Injection, social engineering, hardware-level attacks) and CSDL (threat modeling, vulnerability search, code analysis, typical programming errors by C) to the basics of protecting Linux, learning Secure Boot, SSL, supply chain management and “managerial” topics.

The following three belts meant no longer studying any theoretical or practical topics, but promoting the introduction of secure programming practices in Cisco activities. And the higher the belt, the more such actions need to be implemented. To eliminate uncertainty in the process of conquering the “higher” belts, all the activities that candidates for the blue / brown / black belt had to do were divided into 4 groups - an invention (for example, creating a useful tool or process or leading a community), training ( mentoring, conducting or developing courses, speeches), research (analysis of a problem, participation in an internal working group or committee, development of a security function) and implementation (test, feature, CSDL process, etc.).
For each action, there are certain points, the number of which depends on time-consuming (1 point = 1 hour) and the scale of activity (only within the team, inter-team activity, external, etc.). Then these points are summed up and, depending on the final amount, one or another degree is assigned. For example, to get a blue belt, it is enough to “earn” only 75 points, while for black you need at least 400 points out of all four of the above described activity groups. The black belt is the highest level not only in martial arts, but also in the Cisco Security Ninja program. It means recognition both inside and outside of Cisco.

Cisco Security Ninja program in numbers
We launched the program in December 2012, asking some colleagues to “try”. Having received positive feedback, in February 2013, Cisco Security Ninja officially started. In December 2013, an expanded program (on the green belt) was added to the initial training program for the “white” belt, and after a few more months, we added training by roles. December 2014 was marked by the launch of the remaining three programs to get the blue, brown and black belts.
In 2014, the program received support at the level of the company's management, which began to persistently recommend to all interested parties to get at least a white belt. It is worth noting that, until today, this program is not mandatory for employees who voluntarily join it. In March 2015, we reached the border of 20,000 employees who received their belt, of which 47 received a black belt, 22 — brown, 72 — blue, 2640 — green (among them I).
Dojo for training and exams
Dojo is a place where training, competitions and certification in oriental martial arts take place. There is a dojo (Cisco Security Dojo) and we. This is a specially designed platform that includes various activities and tools with which you can get training in various forms and pass the appropriate exams and get a well-deserved belt. Also, using this platform, all ninja security can track their status and colleagues, record their activities to achieve higher degrees and perform a number of other tasks.

Gamification
One of the most important elements of the program, which allowed, to involve more than 20 thousand people, is gamification, which was achieved through various elements:
- Metaphors of information security, with the help of which key concepts and principles of security and safe programming were illustrated in a funny and humorous form.
- Comics "Little Ninja", consisting of 3 illustrations explaining certain provisions of the course.

- Funny clips “We are all security ninja”, in which our employees in ninja costumes chase the daily activities (in a cafe, in the gym, on vacation, on a phone call, etc.).

- “Pop Idol” - people known inside or outside the company who have spoken on certain IS issues

In general, gamification is a very interesting way of conveying information security topics. We often use it in the company. There are information security stands, flash games, games for smartphones, CTF, and much more.
Confession
One of the important elements of our program was the recognition of specialists who were trained and successfully received one or another belt. We use different options - certificates, logos that can be used in your profile on the corporate portal or in the signature in e-mail messages, appropriate straps for wearing a corporate badge, financial incentives.

Key success factors
Over the past almost three years, we were able to formulate 10 criteria for the success of our program:
- No more than 20 minutes per module; and even better ten. Long modules look heavier than short ones. But making them harder. I often record videos for our corporate channel on YouTube and understand perfectly well what a difficult task it is to contain the necessary content in a limited time interval.
- A cohort of experts. They must create content, and possibly participate in its recordings.
- Confession. There are no universal recipes - it all depends on the specific organization. In our case, we were able to find inexpensive, but effective options, which allowed us to attract a little less than a third of the entire company into the ranks of security ninja.
- Viral marketing. It allows the employees themselves to be involved in the process of distributing information about the program, and they are happy to share with friends a “cool trick” and “touching the secret”.
- Course Designers. In English, these specialists are called insrtuctional designers and they are engaged in designing not only the course, but also, which is very important, tests and exams.
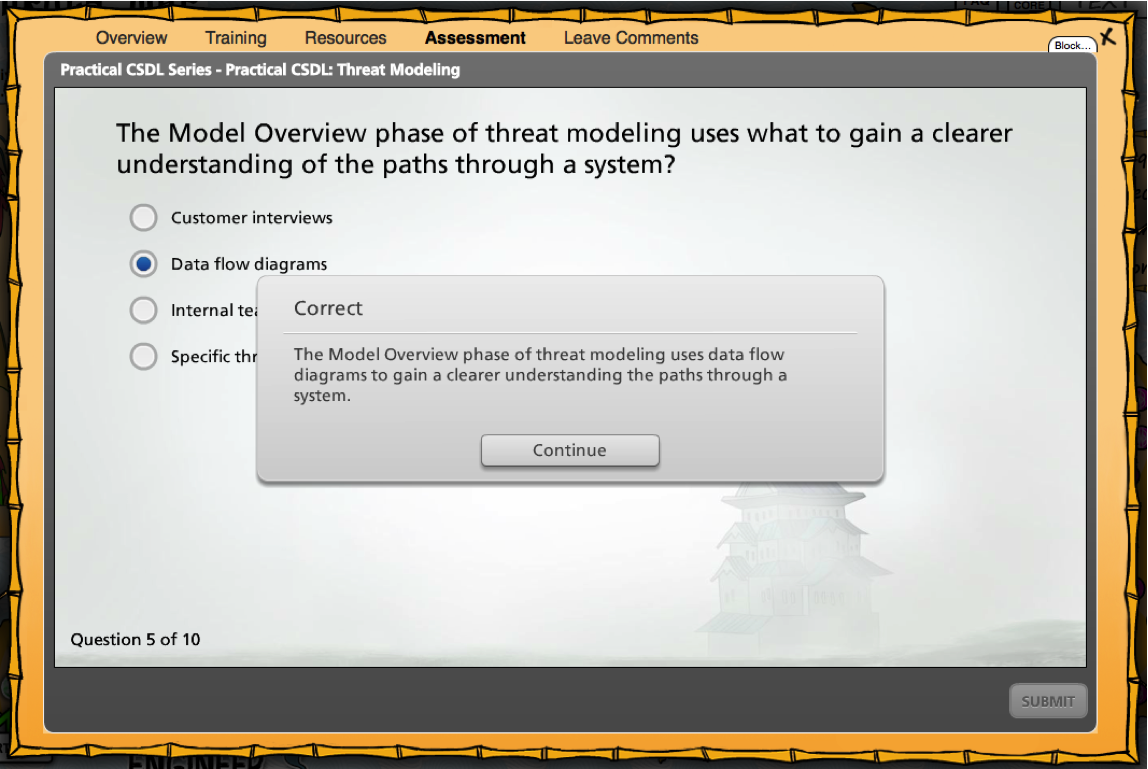
- Competition. Managers love to compete with each other - give them that opportunity by launching a website with statistics for their subordinates; they themselves will motivate their units to be better.
- Break the rules. When we launched the Cisco Security Ninja program, we did not know any rules for conducting classic training. We did what we thought was necessary and made it fun, with jokes and jokes. People feel this and are more easily involved in training with elements of the game.
- Creative people. Running such a program is not a “tick” task. It does not help people who do something out of a stick and people who are not interested in the result. Only a creative approach helped us to do what we did with a minimum of resources.
- Involving leadership. Well, there is no need for an extra explanation.
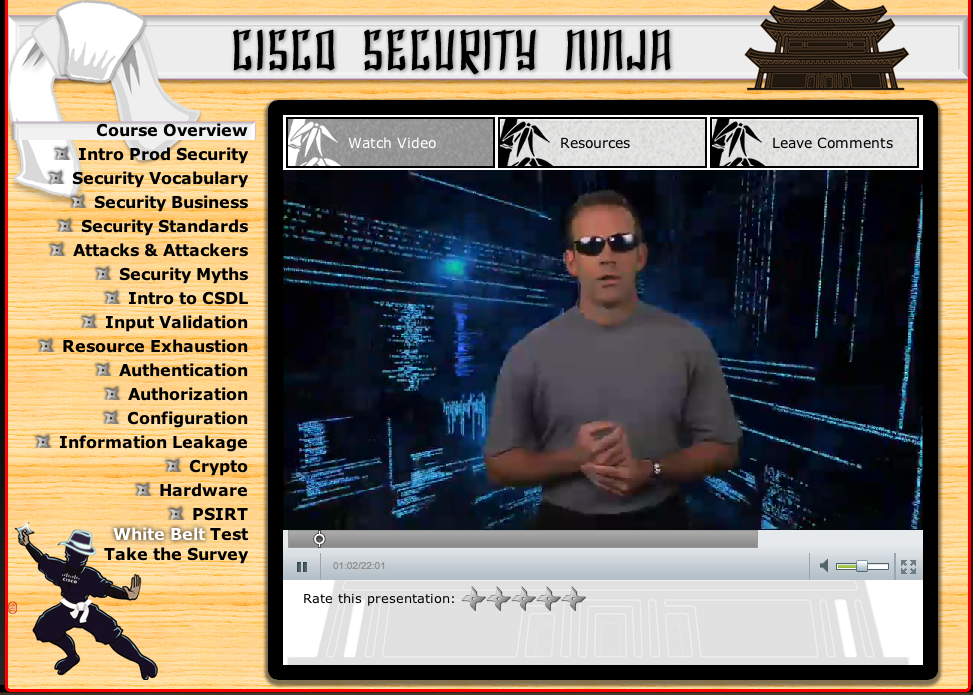
- Gamification We made an interface that showed movement, helped to achieve more, involved in the game. People liked to use the dojo created for them.
As a conclusion
The Cisco Security Ninja program we implemented solved several problems at once, including not only involving 20 thousand employees in the process of ensuring information security of our products, but also increasing the level of security of our solutions. Is it possible to repeat this program in another organization? In the same form hardly. Still, the culture, levels of maturity, and the companies themselves can be very different from each other. But the key success factors will be the same for everyone. The main thing is not to sit still!
And remember: safety is movement, not a destination!
Source: https://habr.com/ru/post/268999/
All Articles