Cybercriminals use Win32 / Brolux.A banking trojan to compromise users in Japan
Recently, our analysts discovered a malicious campaign in which the Win32 / Brolux.A banking Trojan was used. The campaign was targeted at Japanese Internet banking users, and its goal was to spread this malware. The attackers resorted to using exploits for two vulnerabilities. The first vulnerability relates to the Flash Player software, an exploit for which was in the leaked data of the Hacking Team, and so on. unicorn bug, which is a vulnerability in the Internet Explorer web browser, which was discovered at the end of 2014.

Both of these exploits are still distributed through an adult website and attempt to install a digitally signed executable malware file. The malware itself specializes in stealing the victim's personal data and online banking data. This distribution mechanism reminds us of another banking Trojan that was also targeted at Japanese banks and financial institutions. It was called Win32 / Aibatook .
')
When a user visits a maliciously crafted adult website, the system will execute an exploit for either a vulnerability in Internet Explorer (CVE-2014-6332) or a vulnerability in Flash Player (CVE-2015-5119). The experimental PoC code for the first vulnerability has been publicly available for some time. For use in their malicious campaign, attackers subjected it to modifications. A working exploit for the Flash Player vulnerability was made publicly available after a data leak from the Hacking Team cyber group.
Although the above vulnerabilities have already been included by the authors of exploit kits in their cybercrime creations, we do not have information that exploit kits were used in this malicious campaign. Unlike the exploits used in the kits, no obfuscation is provided for exploits from this campaign. As you can see in the screenshot below, a malicious adult website is trying to compromise visitors, while downloading videos from another, real site.
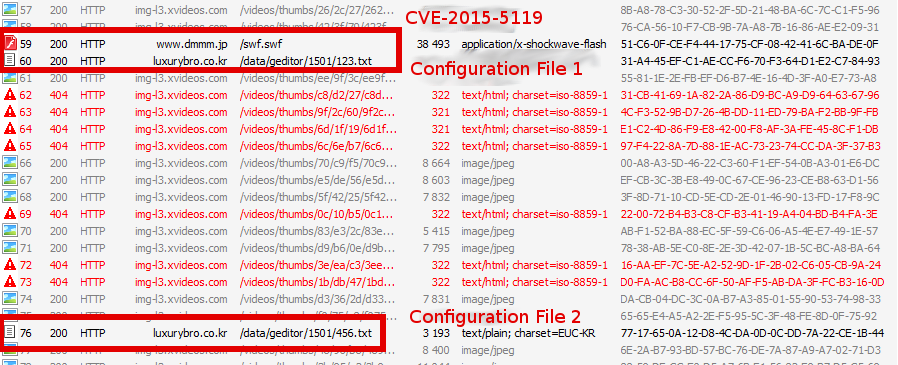
The malware payload code uses two configuration files. The first one contains a list of 88 URLs of Japanese websites for working with online banking, which are targeted by the Trojan, and the second one contains the names of the corresponding web browser windows. Win32 / Brolux.A is a simple Trojan that tracks visits to users of online banking websites. It supports the compromise of web browsers such as Internet Explorer, Firefox, and Google Chrome.
When a user visits a website using Internet Explorer, the malware gets the current URL and compares it with a list from the configuration file. In the case of Chrome and Firefox, the malware's code will compare the web browser window title with the list from the second configuration file. In case of coincidence, the malware will create a new web browser process that will display a phishing web page. This web page contains a special form that asks the user for information to log in to the online banking account, as well as answers to secret questions to log in to the account. The attackers are trying to disguise the web page as a trusted agency in Japan. This institution is either a procurator (Public Prosecutors Office) or a Financial Services Agency. The URL uses the link to both of these institutions, and the content of the web page only on the FSA.
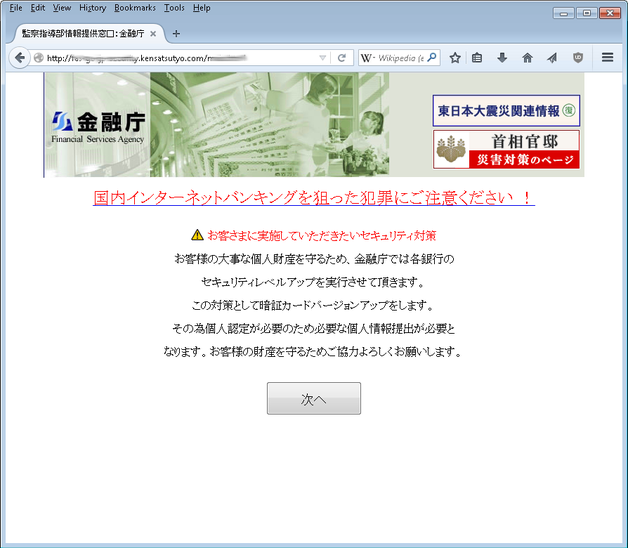
The above web page contains the following suggestions:
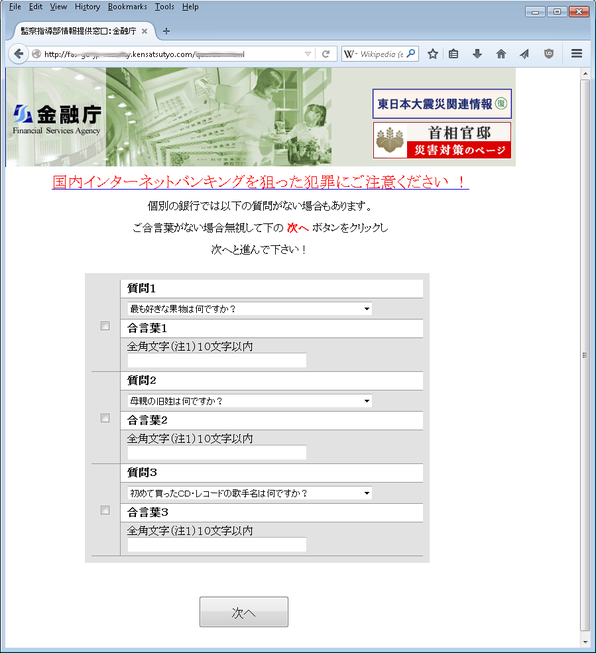
This web page contains the following sentences:
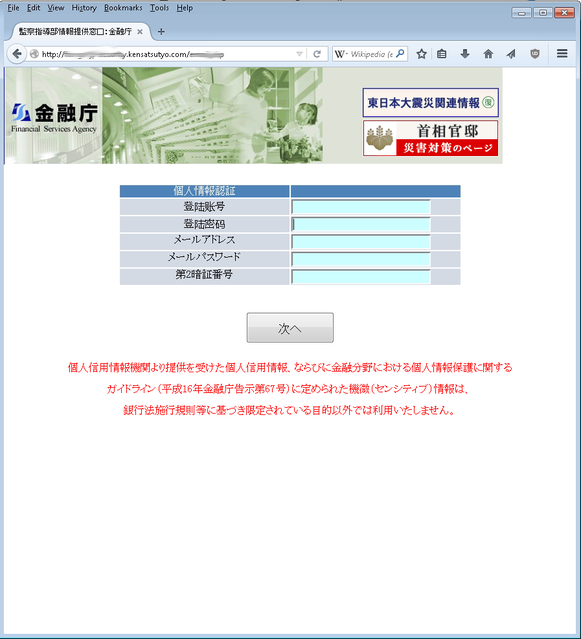
The user is required to enter the following information in the form fields:
It is interesting to note that both the Public Prosecutors Office and the FSA both published security notices about this type of fraud.
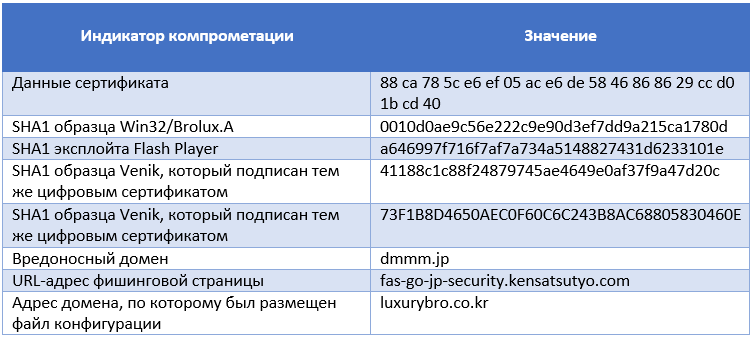
The Win32 / Brolux.A sample we analyzed creates a mutex with a Chinese name, it is also signed with the digital certificate indicated below. In addition, the phishing web page itself contains syntax errors and is not completely written in Japanese: two fields on the third web page (see the screenshot above) are written in Chinese.

It is interesting to note that this certificate, which was issued to a Chinese company, was used in the past to sign various potentially unwanted applications (PUA). Analyzing various samples of malicious programs that have come hand in hand with us, we found that the principle of operation of another banking Trojan called Venik is very similar to Win32 / Brolux. Venik specializes in modifying the hosts file in the victim's OS to redirect users from legitimate online banking sites to phishing web pages.
Despite the fact that the Win32 / Brolux malware uses simple tricks in its work, it is another reminder for users that the necessary precautions should be taken when working with online banking. First, Win32 / Brolux uses outdated exploits for its distribution, so users should always be aware of the timely update of their operating system. Users should also track the appearance of additional or strange web forms on the online banking page.

Both of these exploits are still distributed through an adult website and attempt to install a digitally signed executable malware file. The malware itself specializes in stealing the victim's personal data and online banking data. This distribution mechanism reminds us of another banking Trojan that was also targeted at Japanese banks and financial institutions. It was called Win32 / Aibatook .
')
When a user visits a maliciously crafted adult website, the system will execute an exploit for either a vulnerability in Internet Explorer (CVE-2014-6332) or a vulnerability in Flash Player (CVE-2015-5119). The experimental PoC code for the first vulnerability has been publicly available for some time. For use in their malicious campaign, attackers subjected it to modifications. A working exploit for the Flash Player vulnerability was made publicly available after a data leak from the Hacking Team cyber group.
Although the above vulnerabilities have already been included by the authors of exploit kits in their cybercrime creations, we do not have information that exploit kits were used in this malicious campaign. Unlike the exploits used in the kits, no obfuscation is provided for exploits from this campaign. As you can see in the screenshot below, a malicious adult website is trying to compromise visitors, while downloading videos from another, real site.

The malware payload code uses two configuration files. The first one contains a list of 88 URLs of Japanese websites for working with online banking, which are targeted by the Trojan, and the second one contains the names of the corresponding web browser windows. Win32 / Brolux.A is a simple Trojan that tracks visits to users of online banking websites. It supports the compromise of web browsers such as Internet Explorer, Firefox, and Google Chrome.
When a user visits a website using Internet Explorer, the malware gets the current URL and compares it with a list from the configuration file. In the case of Chrome and Firefox, the malware's code will compare the web browser window title with the list from the second configuration file. In case of coincidence, the malware will create a new web browser process that will display a phishing web page. This web page contains a special form that asks the user for information to log in to the online banking account, as well as answers to secret questions to log in to the account. The attackers are trying to disguise the web page as a trusted agency in Japan. This institution is either a procurator (Public Prosecutors Office) or a Financial Services Agency. The URL uses the link to both of these institutions, and the content of the web page only on the FSA.

The above web page contains the following suggestions:
- Please note the possible fraud associated with online banking!
- The following security measures should be used by the client:
- To protect the important personal information of the client, the financial services agency specializes in providing services to the bank to enhance its protection.
- Each bank will be obliged to provide its customers with updated bank cards, as well as information necessary for customer identification.

This web page contains the following sentences:
- Please note the possible fraud associated with online banking!
- For every bank, there are those authentication cases where secret answers to questions are not required.
- If you are notified that you do not need to enter a secret phrase, simply click “Next” to go to the next field.

The user is required to enter the following information in the form fields:
- Personal information:
- Registration number
- Secret phrase
- E-mail address
- Email account password
- Second pin
- We do not use the personal information of the user's credit card or his other personal information, which is determined by the document on the protection of personal data, 2004 Financial Services Agency Notification No. 67, for those purposes that differ from those stated, as indicated by the Banking Act (Ordinance for Enforcement of the Banking Act).
It is interesting to note that both the Public Prosecutors Office and the FSA both published security notices about this type of fraud.
The Win32 / Brolux.A sample we analyzed creates a mutex with a Chinese name, it is also signed with the digital certificate indicated below. In addition, the phishing web page itself contains syntax errors and is not completely written in Japanese: two fields on the third web page (see the screenshot above) are written in Chinese.

It is interesting to note that this certificate, which was issued to a Chinese company, was used in the past to sign various potentially unwanted applications (PUA). Analyzing various samples of malicious programs that have come hand in hand with us, we found that the principle of operation of another banking Trojan called Venik is very similar to Win32 / Brolux. Venik specializes in modifying the hosts file in the victim's OS to redirect users from legitimate online banking sites to phishing web pages.
Despite the fact that the Win32 / Brolux malware uses simple tricks in its work, it is another reminder for users that the necessary precautions should be taken when working with online banking. First, Win32 / Brolux uses outdated exploits for its distribution, so users should always be aware of the timely update of their operating system. Users should also track the appearance of additional or strange web forms on the online banking page.

Source: https://habr.com/ru/post/268939/
All Articles