Web application vulnerabilities: the situation is not improving
In recent years, large organizations are increasingly using a variety of web applications - the official websites of companies and enterprise resource management systems (ERP), electronic trading platforms, remote banking services, and public services portals. Corporate applications based on specialized client software are increasingly being replaced by web versions and cloud services. Therefore, it is not surprising that the vulnerabilities of web applications are becoming one of the main vectors of attacks on corporate information systems. This article provides statistics on the most common vulnerabilities collected by Positive Technologies experts in the course of their work on analyzing the security of web applications in 2014.
Sources and methods
In total for the year, our experts analyzed about 300 web applications. Of these, 40 systems were identified, for which an in-depth analysis was conducted with the most comprehensive coverage of the checks. The statistics includes only data on external web applications accessible from the global Internet. The security assessment was carried out using the black, gray and white box methods using automated auxiliary means. Detected vulnerabilities were classified according to the corresponding threats by WASC TC v. 2, the risk of vulnerabilities was assessed by CVSS v. 2. The statistics included only vulnerabilities associated with errors in the code and configuration of web applications.
')
The studied web applications belonged to companies representing various industries: e-commerce (30%), finance and banks (22%), industry (17%), information technology (15%) and telecommunications (13%); The study also included one government agency.
Most of the web applications in the sample are based on PHP (58%) and ASP.NET (25%). The most common web server in this year’s study was Nginx (37% of web applications), followed by Apache (26%) and Microsoft IIS (24%). Most of the resources were productive systems (85%), however, test sites that are in the process of development or commissioning were also explored.
Overall results
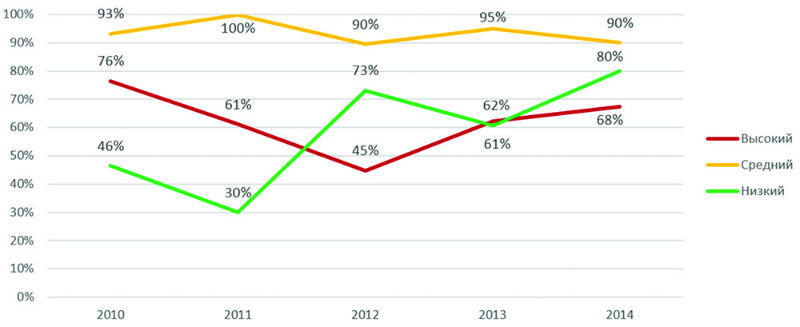
All 40 studied web applications contain certain vulnerabilities, a total of 1194. At the same time, 68% of systems contain high-risk vulnerabilities. This figure is higher than last year (62%). In addition, in 2013, on average, each web application accounted for 15.6 vulnerabilities, and in 2014 this number almost doubled to 29.9. Most of the identified vulnerabilities (89%) are caused by bugs in the program code, and only 11% of the flaws are due to incorrect configuration of web applications.
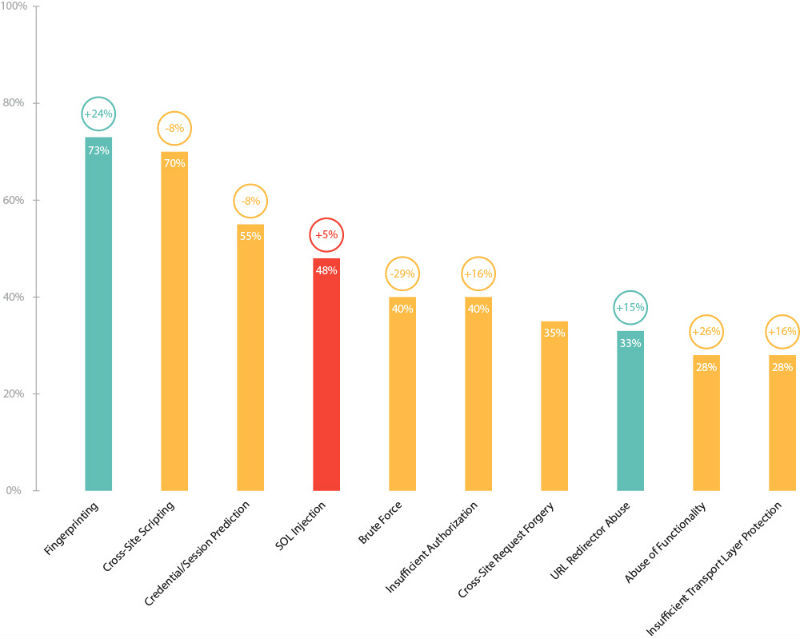
Shares of vulnerable sites depending on the degree of risk of vulnerabilities
In 2014, the most prevalent (73% of systems) was the low-risk software identification (Fingerprinting) vulnerability. The second place (70%) is the most common in 2013 Cross-Site Scripting (XSS) vulnerability. As a result of the operation of this error in the code, an attacker can organize an attack on users of the web application, for example, in order to gain access to the personal account.
More than half of the websites contain vulnerabilities associated with the use of predictable values for user IDs and sessions (Credential / Session Prediction). Critically dangerous vulnerability "The introduction of SQL statements" (SQL Injection) has risen from 6th place to 4th, now it is detected in almost half of web applications (48%). Exploiting this vulnerability could lead to unauthorized access to important information stored in application databases; in addition, it is often possible to develop an attack until gaining complete control over the server.
Development Vulnerabilities
Like last year, PHP applications turned out to be the most vulnerable: 81% of systems written in this language contain critically dangerous vulnerabilities (76% last year). But for resources based on ASP.NET, this figure decreased from 55 to 44%. Each PHP web application averages 11 critical vulnerabilities. For ASP.NET, this figure was 8.4, but in this case, the statistics were strongly influenced by one system, which contained 60 high-risk vulnerabilities: in other ASP.NET-based applications, the average number of vulnerabilities was only 2.
It can also be noted that the proportion of resources on PHP that are affected by the “Cross-site scripting” vulnerability is significantly higher (95%) than the corresponding share of resources on ASP.NET (44%). This may be due to the fact that in ASP.NET there are built-in basic mechanisms of protection against attacks of this type (Request Validation).
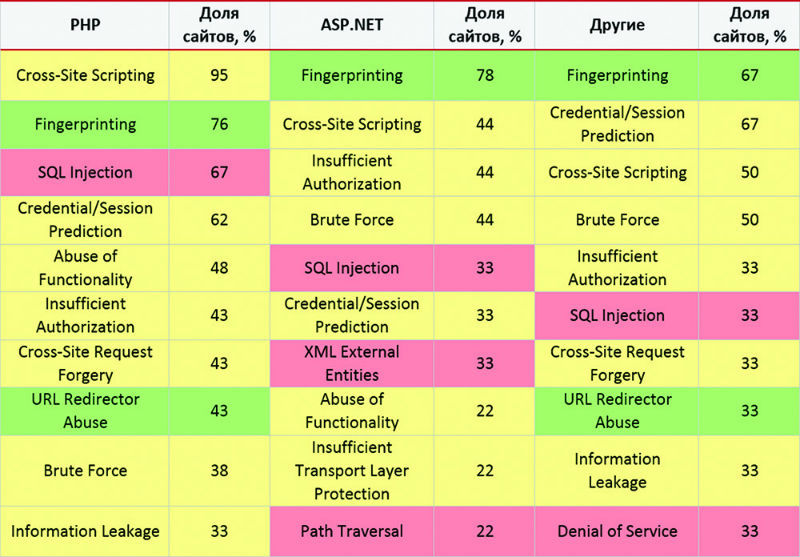
The most common vulnerabilities (by development tools)
Server Vulnerabilities
86% of the studied web applications running on the Nginx server contain high-risk vulnerabilities. The share of vulnerable resources based on Microsoft IIS has decreased significantly compared with 2013 and amounted to 44% instead of 71%. The number of vulnerable sites under Apache increased by 10% and amounted to 70%.
The most common web server administration error is “Software Identification” (Fingerprinting). In particular, this vulnerability is found on 8 out of 10 web resources running Apache. This is due to the fact that the standard configuration of the studied servers implies disclosure of version information of the web server in error messages (for example, when accessing a non-existent resource).
Vulnerabilities by industry
The leader in the number of systems with high-risk vulnerabilities was the banking industry (89%). This may be due to the fact that most of the resources studied were not RBS systems or other systems where financial transaction data is processed, so banks paid less attention to ensuring the protection of application data. Also, a high percentage of web applications exposed to critical vulnerabilities are noted for the telecommunications industry (80%). This is followed by industry (71%) and information technology (67%). In e-commerce, the share of systems with high-risk vulnerabilities is also quite high - 42%.
According to the average number of vulnerabilities per system, the sites of industrial enterprises were the least protected, with 18 critical vulnerabilities per application. It is worth noting that the previously mentioned application, in which 60 critically dangerous vulnerabilities were identified, belonged to the industrial sector. Without taking it into account, the corresponding indicator for this sector of the economy is 13.1 vulnerability of a high degree of risk to the system, which coincides with the indicator for the banking industry.
In 2014, high-risk vulnerabilities, “Implementing SQL Statements”, “Implementing XML Entities” and “Going beyond the designated directory” were more common than other shortcomings. As in 2013, the critically dangerous vulnerability "The introduction of SQL statements" was discovered in the web applications of all studied sectors of the economy.
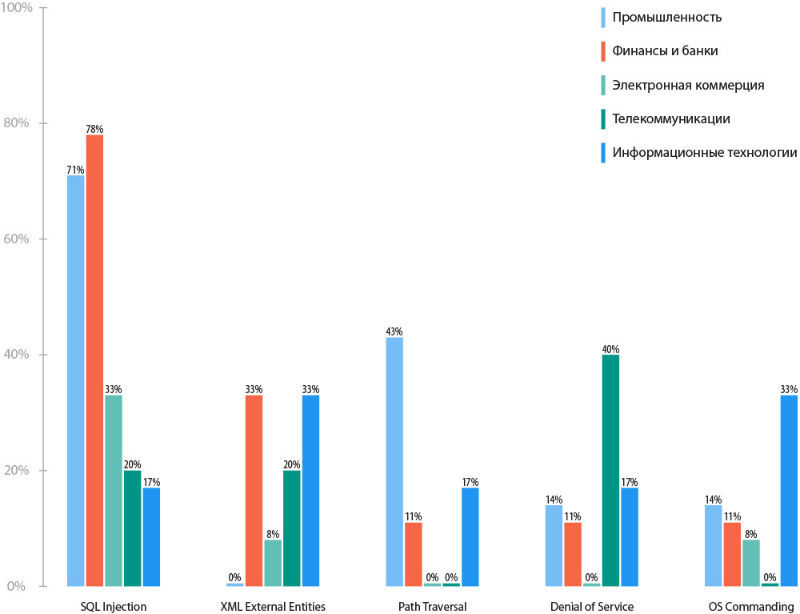
Shares of vulnerable sites from different industries
Vulnerabilities in production and test sites
Critical vulnerabilities were detected in 71% of productive web resources, for test sites this figure is 50%. The average number of high-risk vulnerabilities identified in test systems (12.8) is almost two times higher than the productive ones, with an average of 7 critically dangerous vulnerabilities identified. However, in productive systems, on average, more medium-risk vulnerabilities were found (20.6 vs. 14.3 for test ones).
A similar situation with the security of systems already in use clearly demonstrates the need to implement security processes at all stages of the application life cycle (SSDLC).
Comparison of testing methods
In the course of security research, Positive Technologies specialists compared the white box test results (using internal system data, including source code analysis) with the black and gray box test results (when the analysis is performed with privileges identical to those of a potential attacker). The share of sites containing high and medium risk vulnerabilities was about the same for these testing methods. It can be concluded that the attacker's lack of access to the source code does not make the web application secure.
On the other hand, source code analysis, in addition to black and gray box analysis, reveals more vulnerabilities for each application. In particular, white-box testing on average finds 3.5 times more medium-risk vulnerabilities compared to the black and gray box methods. Another vivid example: in each resource investigated by the black and gray box methods, on average, 4 vulnerabilities of the “Cross-site scripting” type were found - but the white box method revealed an average of 29 vulnerabilities of this type.
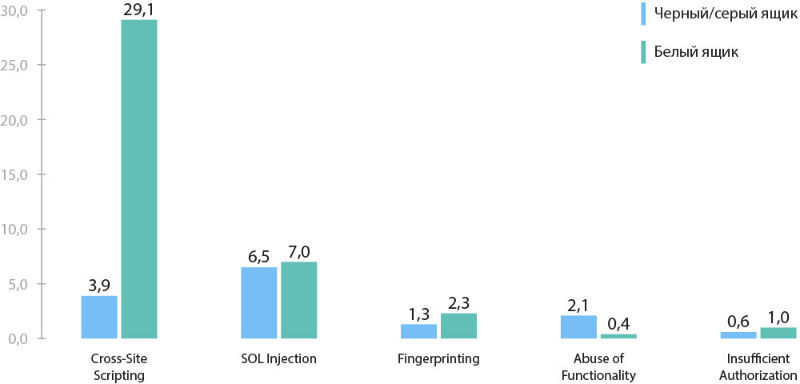
The average number of identified vulnerabilities of a certain type per system (by testing method)
In general, today the level of web application security remains extremely low - and even worse than last year. Despite this, intrusion detection and prevention systems ( web application firewalls ) are almost never used: such a mechanism was used to protect only one of all the sites reviewed in this study.
A full version of this study, as well as a compilation of Positive Research '2015 with all the studies of last year’s vulnerabilities (SCADA, RBS, telecoms, etc.), can be found at www.ptsecurity.ru/lab/analytics
And if you are interested in modern methods of web application security research, we invite you to listen to the free webinar of Vladimir Kochetkov, head of the development department of source code analyzers Positive Technologies.
The webinar will be held on November 12 at 2:00 pm, pre-registration here: www.ptsecurity.ru/lab/webinars/#42235
Source: https://habr.com/ru/post/268779/
All Articles