Security Week 41: censorship research, hacking Outlook Web Access, data loss at the joints
 Today is a special corporate issue of our digest, in which we will talk about such things as ROI, EBITDA, TCO, RAS, CRM, SLA, NDA, GAAP, etc. However, no, let's talk, as usual, about the most significant security news for the week. It turned out that all three somehow relate to corporate security: they show how companies break open, how data leaks, and how a business reacts to it. What is the main difference between "user" security and corporate? First, if relatively simple defensive solutions or methods are available to users, then there are no simple solutions for a business, if only because the infrastructure is much more complicated. Secondly, to effectively protect a company, we need not only complex technologies, but also certain organizational solutions.
Today is a special corporate issue of our digest, in which we will talk about such things as ROI, EBITDA, TCO, RAS, CRM, SLA, NDA, GAAP, etc. However, no, let's talk, as usual, about the most significant security news for the week. It turned out that all three somehow relate to corporate security: they show how companies break open, how data leaks, and how a business reacts to it. What is the main difference between "user" security and corporate? First, if relatively simple defensive solutions or methods are available to users, then there are no simple solutions for a business, if only because the infrastructure is much more complicated. Secondly, to effectively protect a company, we need not only complex technologies, but also certain organizational solutions.And what about the security of a business? Let's just say not very well. For example, Gartner believes that after three years, up to 30% of the IT budget will be spent on security, and that the “keep and not let go” companies' common approach is outdated. In a sense, now a typical company employs 90% of its efforts on perimeter defense, and only 10% on detection and response. If the attacker managed to break through the defense, then he finds himself in an environment that is favorable enough for him, with unpleasant consequences for the victim. Gartner's recommendation to change this ratio to 60/40 looks quite reasonable. For example, from our study of Carbanak , attacks on banking organizations, it is clear that in this very "zone of 10%" the attackers were very long.
Previous news digests can be found here .
Outlook Web App as an entry point to corporate infrastructure
News Cybereason research. Microsoft reaction .
')
If you hack one of the company's computers, install a bug on it and organize data transfer, what will it be to steal? From an employee’s laptop, the employee’s materials, and possibly other information from the file servers to which he has access. The case will go "more efficiently" if it is a computer of a manager, or an administrator with broad access rights. Access to the mail server theoretically could jeopardize the huge amount of data that somehow passes through the mail. A study by Cybereason shows that it may not be limited to mail alone.
As is often the case, there was no specific vulnerability in Outlook Web App (also known as Web Access, Exchange Web Connect, and Outlook on the web — over the 20 years of the product’s existence, Microsoft renamed it four times). They stole (most likely phishing) the login and password of the administrator, implemented a malicious DLL (and not signed) on the server. As a result, they got access not only to mail, but also to Active Directory. Burglars could send a letter on behalf of any employee of the company. Moreover, another tab was introduced into the IIS server to monitor connections to the web-mail, and judging by the results of the investigation, who and when (and from where) comes in the mail was monitored very closely. The researchers' main claim to OWA is that it was possible to launch an unsigned binary on the server without any problems, but Microsoft says that the correct configuration makes such an attack impossible.
Maybe so, but these are details. If we ignore them, we have:
- Service, by definition, has access to the Internet and to the internal network.
- Failure of IT security technician (stolen username and password, and obviously not the user).
- Incorrect server configuration, which allowed installing a backdoor without any problems.
- Inability to detect hacking for a long time.

But only the patch wanted to roll ...
That is, a whole set of problems, each of which must be solved separately. Interestingly, the value of data in Active Directory is usually not in doubt, and this service is securely protected (although there are examples of such an attack vector). However, there can always be a less obvious way to access valuable information through the weakest link.
T-Mobile stole data of 15 million subscribers through a contractor
News Disclosure from Experian, victim of the attack. Appeal to T-Mobile customers .
Let's start with a small lyrical digression. In the USA, the majority of mobile subscribers sign a long-term contract with the operator, the price of which may include communication services and a mobile phone, smartphone or tablet. On the one hand, this is convenient - you get a new device or even for free, or at a discount, on the other hand, you just won't be able to switch to another operator until the end of the contract. The scheme of work assumes that you, as a potential client, will be checked for solvency, something like when you make a loan at a bank. For this, a request is made to the local credit bureau. In the case of T-Mobile, the bureau was Experian, which was hacked.
According to information from the affected company, unauthorized access to one of its servers was one-time and short-lived, but a large amount of data about 15 million subscribers of the cellular operator was allegedly leaked over a two-year period. It must be admitted that both companies behaved very openly in this difficult situation. The sites were posted detailed descriptions of what happened. Victims are offered a free service for tracking suspicious transactions using their personal data. This is significant progress compared to, for example, Target, which, after leaking data on 40 million credit cards, limited itself to a brief message in the “we have fixed everything” style. In the case of T-Mobile, the credit card information did not suffer, but everything else was yes, including names, addresses, driver's licenses, and so on. Moreover, in a letter to the CEO of T-Mobile, it is noted that the data was partially encrypted, but apparently not well enough.

"And they are: we have all the data encrypted!"
This story is also related to privacy: a priori, credit organizations need to know a lot about their customers, and they receive information from various sources. Moreover, they sell this data to other companies for money, and not always their clients are respectable international companies. Previously, the same Experian lit up in another scandal. Then nobody broke, just one Vietnamese citizen paid Experian services on behalf of a Singaporean company and resold the data of 200 million Americans to groups of criminals specializing in identity theft. If you contact, for example, in Amazon with a request to change your forgotten password, you may be asked for the address, date of birth and social security number, and it is these data in the range that an organization like Experian owns.
And another thing: losing data is easiest at the time of transfer from one company to another. Just because the technology and approach to protection will necessarily be different.
The manufacturer of IP cameras blocked disclosure of information about vulnerabilities in his product, threatening to court
News Summary of the study.
Researcher of the Swiss company Ptrace Security Gianni Nyesa wanted to tell at the HITB GSEC conference in Singapore about some aspects of security of IP video cameras. But could not. His study contained examples of vulnerabilities in network surveillance cameras from three different manufacturers (we now don’t know which ones). Nothing foreshadowed such a turn of events: Gianni sent information about vulnerabilities to vendors, conducted routine correspondence with techies, and finally announced that he was preparing a speech, offered to agree on the content of his research. From this point on, the IT specialists of one of the companies disappeared somewhere, and instead of them, the lawyers entered into a dialogue, who recommended not to tell anything to anyone (otherwise it will be worse).
Not the first time this happens, and, alas, not the last. The reason is also clear: the line between the researcher and the cybercriminal is obvious from the point of view of the observer (the first tries not to harm), but from the point of view of the law is not clearly spelled out. A case in point is the Wassenaar Arrangement - an international agreement to restrict the export of dual-use technologies. In December 2013, the European Parliament added software to the list of such technologies for unauthorized access to computer systems. The idea of “hacking for good purposes” is generally extremely dubious, but at least they thought that the developers of such software (for example, the notorious Hacking Team) should choose customers more carefully.
But they formulated all this in such a way that anything can fall under the wording “intrusion software”. This will not interfere with cybercriminals, but it will complicate life for researchers (for example, pentesters). The result - in September, HP declined to participate in the Japanese hackathon PWN2OWN, because the company's travel team could be qualified as the “export of dual-use technologies”.
Oh. If everything is difficult for companies, then in matters of law in general a dark forest. The motivation of vendors who banned the publication of vulnerabilities is understandable - if there is a way to make your life easier, why not use it. But how does this affect security?
If companies didn’t spend their strength on litigation, but on closing vulnerabilities, the world would be much safer.
This is not to say that the “allow everything to everyone” scenario is much better than “deny everything” - in the end, irresponsible disclosure of information about vulnerable software and hardware can seriously harm users. The solution, as usual, is somewhere in the middle between two extremes.
What else happened:
With safety in nuclear power, everything is very , very bad. Post on the topic in the blog Eugene Kaspersky. The main conclusion: even if it seems to you that there is an Air Gap between your critical infrastructure and the Internet, think again. Maybe you just think.
 Gartner also predicts the future . Of the interesting: by 2018, we will have to create “machines controlling machines” - it will be impossible to administer millions of devices from the “Internet of things” (spending half the day off on “administering” four Raspberry Pi, I can't disagree). Moreover, even people are promised “robots-bosses”, and activity trackers will have to be worn not for counting steps, but for your employer to follow you. Brave new world! However, this is if you find work: in the fastest growing companies in three years there will be more cars than people.
Gartner also predicts the future . Of the interesting: by 2018, we will have to create “machines controlling machines” - it will be impossible to administer millions of devices from the “Internet of things” (spending half the day off on “administering” four Raspberry Pi, I can't disagree). Moreover, even people are promised “robots-bosses”, and activity trackers will have to be worn not for counting steps, but for your employer to follow you. Brave new world! However, this is if you find work: in the fastest growing companies in three years there will be more cars than people.Drones and other drones can be hacked (we had no doubt). Interestingly, each regular type of smart device is sick, like chickenpox, with all the children's security-sores. In this case: data transfer protocols that do not require authorization.
Antiquities:
Family "Hymn"
A family of very dangerous resident viruses. COM- and EXE-files are usually amazed when they are launched, closed, renamed or changed their attributes. If the number of the current month coincides with the number (January 1, February 2, etc.), destroy part of the system information of the C: boot sector of the disk :, then decrypt and display a picture:
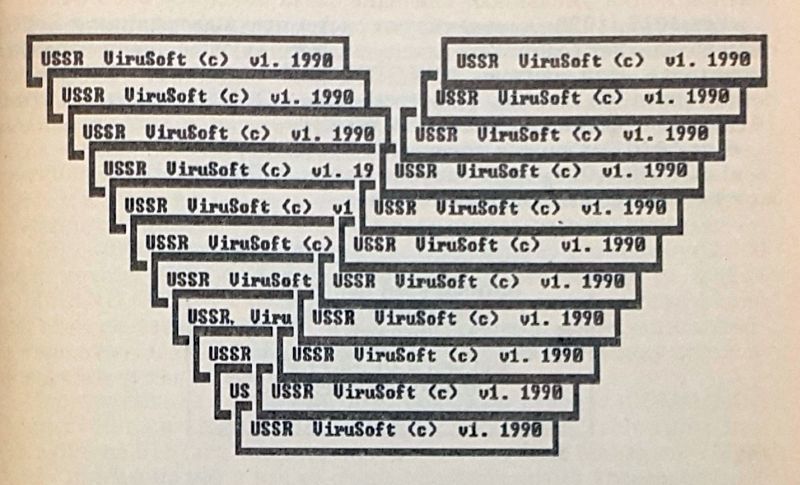
Then they play the National Anthem of the USSR. In this case, the virus clears bytes in the boot sector of the disk, which indicate the number of bytes per sector, sectors per cluster, the number of copies of FAT, etc. (only 9 bytes). If you make such changes in the boot sector of a computer running in MS-DOS environment, it will stop booting from both the hard drive and floppy disk. In order to recover information, you need to write your own mini-downloader or use special utilities. Hymn-1962 and Hymn-2144 encrypt their body.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 36.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/268493/
All Articles