Naked truth
Tedious technical details, without which it can not do, are highlighted with a paragraph sign: ¶. I hope you can skip them without losing the meaning of the presentation.
As it happens often, recently, new viruses come straight to the mail - quickly, conveniently and do not have to strain at all. The last virus sent itself in this letter:
At first, of course, he confuses why the topic of the letter is about P. Hilton, and inside - about A. Jolie, but ... let's get into the position of network villains! Their work is nervous, sometimes they make mistakes. It’s good that at all letters reach the addressees, they tried.
The attached file is called xjolie.scr.zip, and inside it contains a “like” screensaver xjolie.scr. The file is suspicious: there is little code, only three functions, almost no data either. The screensaver does not pull, and for the virus is not enough. Kaspersky’s online scanner designates a file as infected by the “Trojan.Win32.Pakes.cyu” virus.
By the way, Simantek, who was working at that moment, did not even utter a word, and stubbornly repeated “Clean”; so once again I am sure that it is not worth hoping for a heuristic analysis in the next twelve years.
The program extracts a data block from its body and decodes it. After that, it copies it in small parts (apparently, so as not to arouse suspicion) into a dynamically allocated memory area for this purpose.
This data block is actually also a full-fledged executable file, which we will call unpacked0 . This program is already a real dropper whose goal is to install malware on the victim's computer.
The structure of the dropper code is quite clear and simple, apparently written in "C". The file inside contains the line "d: \ programs \ siberia \ install \ objfre_wxp_x86 \ i386 \ Install.pdb". This is hardly an unfortunate omission. Maybe the author is trying in this way to inform the anti-virus companies, the manufacturer-recommended official name of the virus?
Check OS version. To be honest, this piece of code surprised me.
The program checks the current version of the OS, and finishes its work if it is not a Windows 2000, XP or 2003 server.
Base address . unpacked0 , as befits a proper paratrooper, finds out where he finally ended up. For this purpose, one of the simplest search methods is used, based on the fact that the beginning of the loaded image coincides with the beginning of the memory page. Its default size on our regular x86 computers is four kilobytes. The current place in the code is taken, from it we go to the beginning of the current page, we look for the MZ signature at the beginning, if not found, go to the previous page.
Import table . Since unpacked0 cannot rely on a fixed base address specified during compilation, the import table must also be updated. To do this, the program parses its own header (which is located at the very beginning of the downloaded image, and its address was found at the last step), parses the header of the kernel32 library in the same way, finds its export table, and finds two main functions by simple string matching: LoadLibraryA and GetProcAddress, using them, loads all other functions necessary for its black case.
Extract Driver . Yes, damn it, driver again. Viruses without a driver, it seems, already just suckers write. As some have already guessed, the driver body is contained in the resources at unpacked0 . By the way, the driver file contains the string "d: \ programs \ siberia \ protect \ objfre_wxp_x86 \ i386 \ protect.pdb". The trend however ...

The body of the driver is copied to the dynamically allocated memory area, after which its checksum is checked.
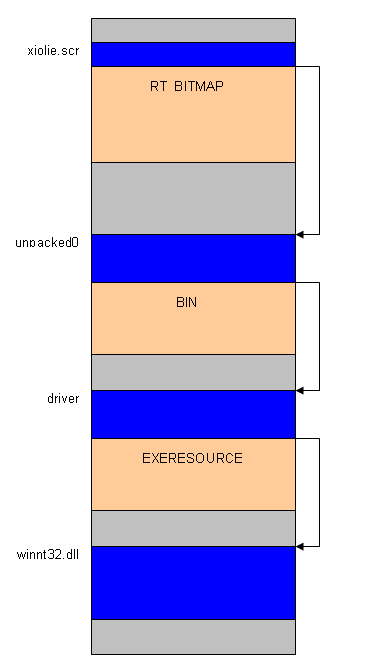
Extract winnt32.dll . And now, - attention, - feint ears. Another component is extracted from the newly extracted driver. From resources, but what about. Now the number of components of our virus is four: the initial xjolie file, the unzipped installer (unpacked0), the driver and the library with the modest name winnt32.dll.
The general unpacking scheme is shown in the figure (blue is the code, brown is the resources).
The name “winnt32.dll” is not randomly chosen from “scary”, even advanced users are unlikely to decide to delete such a file.
If for some reason it is impossible to create such a file, the dropper adds an underscore at the end of the name. This file with an underscore will be renamed to the desired one after a reboot - the MoveFileEx function with the MOVEFILE_DELAY_UNTIL_REBOOT flag is called for this. This will be done again under the system account and the probability of success is very high.
Setup winnt32.dll . Actually, using the library as the main Trojan file is an interesting move. Antiviruses and users practically do not pay attention to them, and in principle, reasonably: after all, not an executable file, which is there. Still, there are ways to force the system to load the library and transfer control to it. The method used by this trojan is rather original: it uses the winlogon process notification mechanism.
In order to enable this mechanism, the dropper adds the following values to the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon \ Notify registry key
(A list of possible parameters with a description is given here: msdn.microsoft.com/en-us/library/aa379402.aspx )
This briefly means that Winlogon, when logging in to the user, is obliged to load winnt32.dll, call the WLEventStartShell function in it, synchronously, without using impersonalization — under the same account under which winlogon itself, that is, SYSTEM, works. For the user who will log in, it means Scary Things.
At this point, the installation of winnt32.dll is complete, and the dropper returns to the driver.
Driver installation . First of all, the dropper tries to connect to the already installed driver using the device name "" \\. \ Prot2 ". If it fails to connect, it saves the driver's body to a file with a random name like% SystemRoot% \ System32 \ drivers \ Wwwdd.sys where W is capitalized, w - lowercase letters, d - numbers.
After this, the driver is registered and started by the CreateService-StartService API functions. Also, the dropper adds the necessary registry lines to the sections.
That is, when you return to the last successful configuration or boot in safe mode, the driver will still load. Very mean.
Then it calls cmd.exe with the command line / c del FILENAME >> NULL , deleting itself from the user's computer.
Under the guise of a naked diva hides not just a trojan. This is a whole program complex of three programs - an installer, a rootkit driver, and a dynamic user mode library. The techniques used to introduce malicious code are simple, effective and not without originality. But, as always, I will note that with a banned entry in% SYSTEMROOT% \ system32, the installer breaks off in full.
In the second part, we will look at the malicious functionality of the dropped-down library winnt32.dll and its dark defender driver.
Part one. Landing
As it happens often, recently, new viruses come straight to the mail - quickly, conveniently and do not have to strain at all. The last virus sent itself in this letter:
From: "Shauna Hoover" <olwen.davie@mairie-paris.fr>
To: <xxx@xxx.xx>
Subject: Paris Hilton
Good afternoon, buddy.
')
I found nude Angelina Jolie!
See in attachment!
Bye.
At first, of course, he confuses why the topic of the letter is about P. Hilton, and inside - about A. Jolie, but ... let's get into the position of network villains! Their work is nervous, sometimes they make mistakes. It’s good that at all letters reach the addressees, they tried.
The attached file is called xjolie.scr.zip, and inside it contains a “like” screensaver xjolie.scr. The file is suspicious: there is little code, only three functions, almost no data either. The screensaver does not pull, and for the virus is not enough. Kaspersky’s online scanner designates a file as infected by the “Trojan.Win32.Pakes.cyu” virus.
¶ At the very beginning of execution, we come across a surprise: the program calls the NtDeleteValueKey function (using KiFastCallEntry, which is essentially a sysenter instruction), and passes to it as arguments uninitialized local variables in which any garbage lies. Therefore, NtDeleteValueKey in 99.9 percent of cases should return STATUS_INVALID_HANDLE. This value (0xC0000008) is used as a starting value, from which by long calculations (numerous “garbage” arithmetic operations), the program gets some address it needs. The task of the system call here, apparently, is to trick automatic analyzers and other antiviruses.
By the way, Simantek, who was working at that moment, did not even utter a word, and stubbornly repeated “Clean”; so once again I am sure that it is not worth hoping for a heuristic analysis in the next twelve years.
The program extracts a data block from its body and decodes it. After that, it copies it in small parts (apparently, so as not to arouse suspicion) into a dynamically allocated memory area for this purpose.
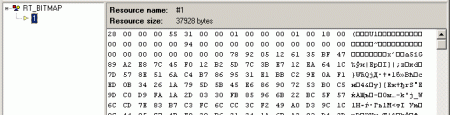
¶ The address on which the encrypted data is located initially leads, seemingly, to where it is not clear where. But in fact it turns out - in the application resources:
After the program has deciphered itself, we do a dump:.writemem unpacked0.dmp 00402088 L00009400, writing the decrypted file to disk.
This data block is actually also a full-fledged executable file, which we will call unpacked0 . This program is already a real dropper whose goal is to install malware on the victim's computer.
The structure of the dropper code is quite clear and simple, apparently written in "C". The file inside contains the line "d: \ programs \ siberia \ install \ objfre_wxp_x86 \ i386 \ Install.pdb". This is hardly an unfortunate omission. Maybe the author is trying in this way to inform the anti-virus companies, the manufacturer-recommended official name of the virus?

Installation
Check OS version. To be honest, this piece of code surprised me.
In pseudocode, it looks like this:if Version.Major = 5
if Version.Minor = 0
is_win2k = 1
else
is_win2k = 0
else
is_win2k = 0
is_win2k_temp = is_win2k
After that, there are three more blocks one-on-one: for XP and 2003 server. Why so many variables and how many comparisons? In short, I did not understand these dances with a tambourine.
The program checks the current version of the OS, and finishes its work if it is not a Windows 2000, XP or 2003 server.
Base address . unpacked0 , as befits a proper paratrooper, finds out where he finally ended up. For this purpose, one of the simplest search methods is used, based on the fact that the beginning of the loaded image coincides with the beginning of the memory page. Its default size on our regular x86 computers is four kilobytes. The current place in the code is taken, from it we go to the beginning of the current page, we look for the MZ signature at the beginning, if not found, go to the previous page.
Import table . Since unpacked0 cannot rely on a fixed base address specified during compilation, the import table must also be updated. To do this, the program parses its own header (which is located at the very beginning of the downloaded image, and its address was found at the last step), parses the header of the kernel32 library in the same way, finds its export table, and finds two main functions by simple string matching: LoadLibraryA and GetProcAddress, using them, loads all other functions necessary for its black case.
Extract Driver . Yes, damn it, driver again. Viruses without a driver, it seems, already just suckers write. As some have already guessed, the driver body is contained in the resources at unpacked0 . By the way, the driver file contains the string "d: \ programs \ siberia \ protect \ objfre_wxp_x86 \ i386 \ protect.pdb". The trend however ...

The body of the driver is copied to the dynamically allocated memory area, after which its checksum is checked.
Extract winnt32.dll . And now, - attention, - feint ears. Another component is extracted from the newly extracted driver. From resources, but what about. Now the number of components of our virus is four: the initial xjolie file, the unzipped installer (unpacked0), the driver and the library with the modest name winnt32.dll.
The general unpacking scheme is shown in the figure (blue is the code, brown is the resources).

The name “winnt32.dll” is not randomly chosen from “scary”, even advanced users are unlikely to decide to delete such a file.
¶kernel32! CreateFileA: 7c801a24 8bff mov edi, edi 0: 000> da poi (esp + 4) 0012feac "C: \ WINDOWS \ System32 \ WinNt32.dll"
If for some reason it is impossible to create such a file, the dropper adds an underscore at the end of the name. This file with an underscore will be renamed to the desired one after a reboot - the MoveFileEx function with the MOVEFILE_DELAY_UNTIL_REBOOT flag is called for this. This will be done again under the system account and the probability of success is very high.
Setup winnt32.dll . Actually, using the library as the main Trojan file is an interesting move. Antiviruses and users practically do not pay attention to them, and in principle, reasonably: after all, not an executable file, which is there. Still, there are ways to force the system to load the library and transfer control to it. The method used by this trojan is rather original: it uses the winlogon process notification mechanism.
In order to enable this mechanism, the dropper adds the following values to the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon \ Notify registry key
DLLName: winnt32.dll
StartShell: WLEventStartShell
Impersonate: 0
Asynchronous: 0
(A list of possible parameters with a description is given here: msdn.microsoft.com/en-us/library/aa379402.aspx )
This briefly means that Winlogon, when logging in to the user, is obliged to load winnt32.dll, call the WLEventStartShell function in it, synchronously, without using impersonalization — under the same account under which winlogon itself, that is, SYSTEM, works. For the user who will log in, it means Scary Things.
At this point, the installation of winnt32.dll is complete, and the dropper returns to the driver.
Driver installation . First of all, the dropper tries to connect to the already installed driver using the device name "" \\. \ Prot2 ". If it fails to connect, it saves the driver's body to a file with a random name like% SystemRoot% \ System32 \ drivers \ Wwwdd.sys where W is capitalized, w - lowercase letters, d - numbers.
kernel32!CreateFileA:
7c801a24 8bff mov edi,edi
0:000> da poi(esp+4)
0012fc94 "C:\WINDOWS\System32\drivers\Hwo84.sys"After this, the driver is registered and started by the CreateService-StartService API functions. Also, the dropper adds the necessary registry lines to the sections.
SYSTEM \ CurrentControlSet \ Control \ SafeBoot \ Network \
SYSTEM \ CurrentControlSet \ Control \ SafeBoot \ Minimal \
SYSTEM \ ControlSet002 \ Services \
SYSTEM \ ControlSet001 \ Services \
That is, when you return to the last successful configuration or boot in safe mode, the driver will still load. Very mean.
Then it calls cmd.exe with the command line / c del FILENAME >> NULL , deleting itself from the user's computer.
Conclusion
Under the guise of a naked diva hides not just a trojan. This is a whole program complex of three programs - an installer, a rootkit driver, and a dynamic user mode library. The techniques used to introduce malicious code are simple, effective and not without originality. But, as always, I will note that with a banned entry in% SYSTEMROOT% \ system32, the installer breaks off in full.
In the second part, we will look at the malicious functionality of the dropped-down library winnt32.dll and its dark defender driver.
Source: https://habr.com/ru/post/26847/
All Articles