How does the radio interface work in GSM networks

I think many have ever thought about how cellular networks work. After all, we use mobile phones almost every day. The number of subscribers is increasing every day, as well as the area of network coverage ... The new standards are coming to replace the new ones, and the “appetites” of mobile Internet users are growing. If you are interested in how it all works, welcome to the cut! Since the cellular network infrastructure is quite large, and its description can take up a whole book, in this article we will focus on the Um interface, through which our phones interact with the operator’s equipment, as well as other subscribers.
Beware,
Foreword
Cellular communication appeared quite a long time ago. Back in the 40s of the twentieth century, research began with the goal of creating a mobile communications network. In 1956, the Mobile System A (MTA) car telephone network was launched in several cities in Sweden. In 1957, our compatriot L.I. Kupriyanovich publicly demonstrates the mobile phone he developed and the base station for him. Then, in the USSR, the development of the Altai civilian cellular communication system will begin, which in a few years will cover more than 30, and then completely 114 Soviet cities. By the way, in some cities of the post-Soviet space Altai is still working, for example, in Novosibirsk (numbering +7 (383) 349-8XXX)! In the 80s, Motorola launches its famous DynaTAC 8000X worth $ 3995. And only in 1992, following the NMT-450, AMPS, ETACS, D-AMPS and NMT-900 in Germany, cellular communications are launched based on the GSM standard.
')
Today, after more than twenty years, we use new generation networks, such as 3G and 4G, but GSM networks have not disappeared anywhere - they are still used by ATMs, terminals, alarm systems, and even modern phones to save electricity and maintain backward compatibility. In addition, new items, like UMTS (or W-CDMA) and LTE, have much in common with GSM. Unlike, for example, TCP / IP, cellular networks are less accessible for study and research. There are a lot of reasons: starting from rather high prices for equipment, ending with the ban of the majority of countries on the use of GSM-band frequencies without a license. In my opinion, an understanding of the principles of cellular networks is very important for specialists in the field of information security, and not only. That is why I decided to write this publication.
Content:
- Introduction to cellular networks
1.1 Cellular Service Providers
1.2 Principles of network coverage
1.3 Cellular network infrastructure
1.4 Interoperability - Um-interface (GSM Air Interface)
2.1 Frequency ranges
2.2 Physical channels, multiple access separation
2.3 Logical channels
2.4 What is a burst?
2.5 Types of burst
2.6 Frequency Hopping
2.7 Basic principles of interaction between MS and BTS
2.8 Handover
2.9 Speech coding - Security and Privacy
3.1 Basic attack vectors
3.2 Subscriber Identification
3.3 Authentication
3.4 Traffic Encryption
1. Introduction to cellular networks
1.1 Cellular Service Providers
By analogy with Internet providers, cellular services are provided by certain companies, most often called "operators". Each of them offers its own range of services, and also sets its own tariff plans. Most often, operators use their own equipment to build the basic network infrastructure; some use the existing one, for example, in Russia, the Yota operator operates on the basis of the equipment of the Megafon operator.
From the point of view of an ordinary subscriber of mobile networks, the individuality of the operator lies in the quality of communication services provided, a certain range of numbers, its own brand SIM-cards, as well as tariff plans. From the operators themselves, as well as other telecommunication areas, each of them is identified by the country code (MCC - Mobile Country Code) and the unique network code within the country (MNC - Mobile Network Code). In addition, subscriber identification is carried out not by the usual telephone number, but by the international subscriber ID — IMSI (International Mobile Subscriber Identity), which is recorded in the subscriber’s SIM card, as well as in the operator’s database. Phone numbers are simply “tied” to a specific IMSI, so that the subscriber can change the operator by saving his phone number.
1.2 Principles of network coverage
Coverage of a certain area by cellular communication is provided by distributing transceiver devices over its area. I am sure many have seen them on advertising pieces, various buildings, and even on individual masts. Most often they are a few white directional antennas, as well as a small building where the wires are pulled. So, in GSM terminology, such complexes are called base stations (BTS) and can consist of several transceiver devices - transceivers (TRX - Transmitter / Receiver).

A key feature of cellular communication is that the total coverage area is divided into cells (cells), determined by the coverage areas of individual base stations (BS). By the way, the name “cellular communication” originated from here. Each base station covers one or more sectors, and also has one or more transceivers in each sector, each of which emits a signal at its own frequency. Simply put, a cell is one of the coverage cells that has its unique identifier, called CI (Cell ID). Honeycombs can be classified according to the scale of the covered territory: macro cell (up to 35 km, sometimes up to 70 km), ordinary cell (up to 5 km), microcell (up to 1 km), pico cell (up to 300 meters) and femto cell (most commonly found indoors, covered tens of meters).
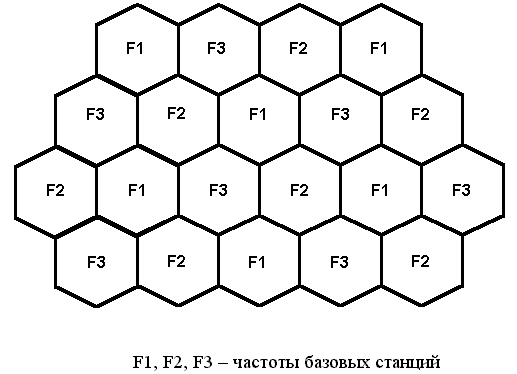
The base stations located nearby operate in different frequency bands, due to which the cells of different operators can partially or almost completely overlap each other. A collection of base stations working together is called a Location Area Code (LAC). All base stations necessarily broadcast their identification data, such as MCC, MNC, Cell ID, and LAC, so that mobile phones are connected only to their operator’s BTS. In addition, mobile phones with a certain interval notify the network of their current location, i.e. LAC. This procedure is called Location Update, but more on that later.
1.3 Cellular network infrastructure
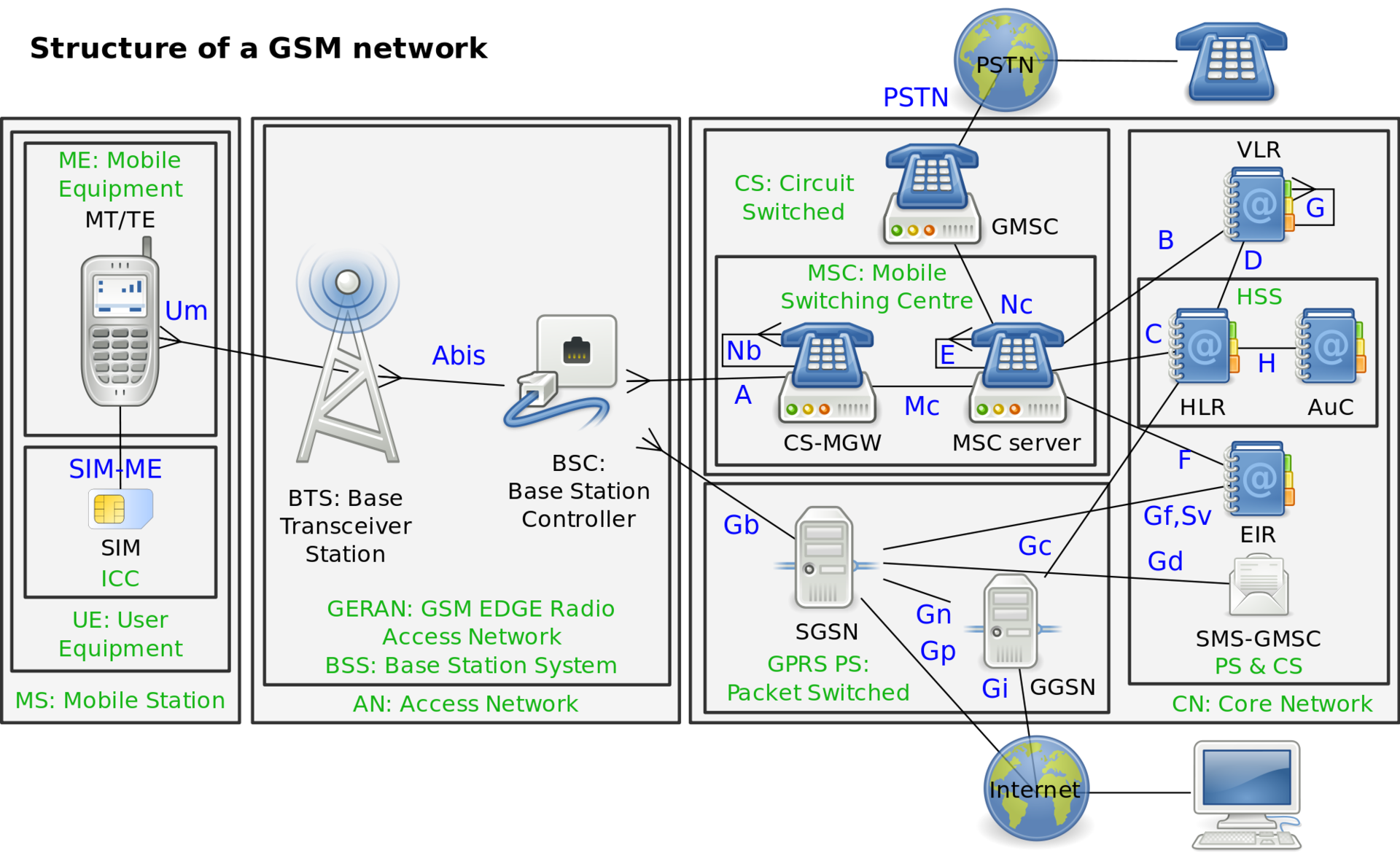
Base stations cannot exist by themselves, therefore, being in a certain LAC, they are connected to a base station controller - BSC (Base Station Controller). The controllers, in turn, perform load balancing, as well as actively participate in the exchange of traffic between the network and their "slaves". The interaction of BTS and BSC is carried out via the A-bis interface . Within the network, most operators, most often, have several base station controllers that, through the A-interface and Gb-interface to the switching nodes of the network (MSC - Mobile Switching Center, SGSN - Serving GPRS Support Node).
MSC forms the core of the network infrastructure (Core Network), which includes the following main elements:
- HLR (Home Location Register) - a database containing personal data of each subscriber, including a phone number, a tariff plan, a list of connected services, as well as information about the SIM card used by the subscriber.
- VLR (Visitor Location Register) is a temporary database of subscribers that are located within the range of a certain mobile switching center. Each base station in the network is assigned to a specific VLR, so the subscriber cannot be present in several VLRs at the same time.
- AuC (Authentication Center) is a subscriber authentication center that authenticates each SIM card that connects to the network.
- SMSC (SMS Center) is a short text messaging center dedicated to storing and routing them.
- GMSC (Gateway MSC) is a gateway that provides access to wired landline networks. It is thanks to this element that calls between subscribers of cellular and local telephone networks are possible.
- SGSN (Serving GPRS Support Node) is a GPRS subscriber service node that acts as a connection point between the base station system (BSS) and the core network (Core Network). SGSN can be called analogue of the GSM network MSC switch. SGSN monitors the delivery of data packets, monitors online users, converts GSM frames to formats used by the TCP / IP protocols of the global computer network of the Internet, registers or “attachments” subscribers, newly “appeared” in the network coverage area, encryption data, processing incoming billing information, and also provides interaction with the register of own subscribers of the HLR network. Unlike the above elements, the SGSN connects directly to the BSC.
In addition, there is a billing system inside the network infrastructure, where our “balance” is stored, fees for using services are written off, and various payment transactions are processed. The operator can attach other subsystems to the core of the network at its discretion.
1.4 Interoperability
Networks of different operators interact with each other, so, for example, Alice, being a subscriber of operator A, can call Bob, who is a subscriber of operator B. This network is called SS-7 or SS7, it works either on the basis of special wired / wireless communication networks, or over the Internet (yes, yes, network over network). SS7 provides a set of protocols for the interaction of various operators. Roaming also works thanks to this network.
2. Um-interface (GSM Air Interface)
2.1 Frequency ranges
Any equipment in cellular networks interacts through certain interfaces. As already mentioned, the data exchange between the base station and the subscriber is carried out through the Um-interface , which is primarily a radio interface, hence the data exchange takes place in the process of receiving / transmitting radio waves. Radio waves are the same electromagnetic radiation as heat or light. Ultraviolet, X-ray and ionizing radiation are also types of electromagnetic radiation with certain frequency ranges and specific wavelengths. Remember this picture?

So, the range of radio waves is also divided into subsidiary frequency bands, for example, the ranges of LF (30-300 kHz), MF (300-3000 kHz) and HF (3-30 MHz) are most often used for radio communications and broadcasting; TV broadcasts are in the VHF (30-300 MHz), UHF (300-3000 MHz) and SHF (3-30 GHz) bands; Wireless networks, such as WiFi, and satellite TV work in the same SHF. Most of all we are interested in the range of UHF, in which GSM networks operate. According to the 3GPP TS 45.005 standard, they have allocated as many as 14 children for the UHF band, and different bands are used in different countries. Consider the most common:
| Specifications | GSM-850 | P-GSM-900 | E-GSM-900 | DCS-1800 | PCS-1900 |
|---|---|---|---|---|---|
| Uplink, MHz | 824.2 - 849.2 | 890.0 - 915.0 | 880.0 - 915.0 | 1710.2 - 1784.8 | 1850.2 - 1909.8 |
| Downlink, MHz | 869.2 - 893.8 | 935.0 - 960.0 | 925.0 - 960.0 | 1805.2 - 1879.8 | 1930.2 - 1989.8 |
| ARFCN | 128 - 251 | 1 - 124 | 975-1023, 0-124 | 512 - 885 | 512 - 810 |
Any range allocated to the cellular network is divided into a number of segments (usually 200 KHz), some of which are called Downlink — here only base stations (BTS) transmit data, and Uplink, where only phones transmit (MS). Pairs of such segments, where one belongs to Downlink, and the other Uplink, form radio frequency channels, called ARFCN (Absolute radio-frequency channel number) . In other words, the phone cannot receive and transmit data at the same frequency, instead, when transmitting, it switches to Uplink frequencies, and when it is received to Downlink, and the switching process occurs very quickly.
2.2 Physical channels, multiple access separation
With ranges figured out. Now imagine a small closed room in which a lot of people. If at a certain point in time everyone starts talking, it will be difficult for the interlocutors to understand each other. Some will speak louder, which will only worsen the situation for others. So, in physics, this phenomenon is called interference . In other words, the interference can be called the imposition of waves. For GSM cellular networks, this is a parasitic phenomenon, so multi-access separation technologies come to the rescue.
The need for separation of multiple access has arisen for a long time and is used both in wired communications (I2C, USB, Ethernet) and in wireless. Cellular networks most often use FDMA (Frequency Division Multiple Access) , TDMA (Time Division Multiple Access) and CDMA (Code Division Multiple Access) technologies . The first two are used together in the networks of the second generation - GSM. CDMA is the basis of modern cellular networks that exceed GSM in terms of both security and maximum data transfer rates. What is this magic?
For radio systems, there are two main resources - frequency and time. The division of multiple access into frequencies, when a certain frequency is allocated to each receiver and transmitter, is called FDMA. The separation by time, when each pair of receiver-transmitter is allocated the whole range or most of it for a selected period of time, called TDMA. In CDMA, there are no restrictions on frequency and time. Instead, each transmitter modulates a signal using the individual numeric code currently assigned to each user, and the receiver calculates the desired part of the signal using a similar code. In addition, there are several other technologies: PAMA (Pulse-Address Multiple Access) , PDMA (Polarization Division Multiple Access) , SDMA (Space Division Multiple Access) , however, their description is beyond the scope of this article.
Fdma
The principle of this method is that the available frequency spectrum is divided between receivers and transmitters into equal or unequal frequency bands, some of which are allocated for Downlink (traffic from BTS to MS), part under Uplink (traffic from MS to BTS). We already spoke about it.
TDMA
Together with frequency division (FDMA), in GSM, the time division method (TDMA) is used. According to TDMA, the entire data stream is divided into frames, and the frames, in turn, are divided into several timeslots, which are distributed among the transmitting / receiving devices. Consequently, the phone can exchange information with the network only at certain intervals allocated to it.
Frames are combined into multi-frames, which are of two types:
Control Multiframe (contains 51 frame)
Traffic Multiframe (contains 26 frames)
Multiframes form superframes, and already superframes form hyperframes. More information about the structure of frames and their organization can be found here (source of images) and here .
As a result, the physical channel between the receiver and the transmitter is determined by the frequency allocated frames and numbers of timeslots in them. Typically, base stations use one or more ARFCN channels, one of which is used to identify the presence of BTS on the air. The first timeslot (index 0) of the frames of this channel is used as the base service channel (base-control channel or beacon-channel). The remaining part of the ARFCN is distributed by the operator for the CCH and TCH channels at its discretion.
2.3 Logical channels
On the basis of physical channels are formed logical. Um-interface involves the exchange of both user information and service. According to the GSM specification, each type of information corresponds to a special kind of logical channels realized by physical:

- traffic channels (TCH - Traffic Channel),
- service information channels (CCH - Control Channel).
Traffic channels are divided into two main types: TCH / F - Full rate channel with a maximum speed of up to 22.8 Kbps and TCH / H - Half rate channel with a maximum speed of up to 11.4 Kbps. These types of channels can be used for voice transmission (TCH / FS, TCH / HS) and user data (TCH / F9.6, TCH / F4.8, TCH / H4.8, TCH / F2.4, TCH / H2. 4), for example, SMS.
Service information channels are divided into:
- Broadcast (BCH - Broadcast Channels).
- FCCH - Frequency Correction Channel (channel correction frequency). Provides information needed by a mobile phone for frequency correction.
- SCH - Synchronization Channel. It provides the mobile phone with the information necessary for TDMA synchronization with the base station (BTS), as well as its BSIC identification data.
- BCCH - Broadcast Control Channel (broadcast service information channel). Transmits basic information about the base station, such as the method of organizing overhead channels, the number of blocks reserved for access grant messages, and the number of multiframes (51 TDMA frames) between the paging requests.
- General Purpose Channels (CCCH - Common Control Channels)
- PCH - Paging Channel. Looking ahead, I’ll tell you that Paging is a kind of mobile phone ping that allows you to determine its availability in a specific coverage area. This channel is designed specifically for this.
- RACH - Random Access Channel (random access channel). Used by mobile phones to request their own SDCCH service channel. Exclusively Uplink channel.
- AGCH - Access Grant Channel. On this channel, base stations respond to RACH requests from mobile phones, allocating SDCCH, or TCH immediately.
- Own channels (DCCH - Dedicated Control Channels)
Own channels, as well as TCH, are allocated to certain mobile phones. There are several subspecies:- SDCCH - Stand-alone Dedicated Control Channel. This channel is used for mobile phone authentication, encryption key exchange, location update procedure, as well as voice calls and SMS messaging.
- SACCH - Slow Associated Control Channel. Used during a call, or when the SDCCH channel is already involved. With its help, BTS transmits periodic instructions to the phone to change the timings and signal strength. In the opposite direction are data on the level of the received signal (RSSI), quality TCH, as well as the signal level of the nearest base stations (BTS Measurements).
- FACCH - Fast Associated Control Channel. This channel is provided with TCH and allows you to send urgent messages, for example, during the transition from one base station to another ( Handover ).
2.4 What is a burst?
Data in the air is transmitted in the form of sequences of bits, most often called "burst", within timeslots. The term “burst”, the most suitable analogue of which is the word “splash”, should be familiar to many radio amateurs, and appeared most likely when drawing up graphic models for analyzing radio broadcasting, where any activity is similar to waterfalls and water bursts. More information about them can be found in this wonderful article (source of images), we will focus on the most important. A schematic representation of the burst might look like this:

Guard Period
In order to avoid the occurrence of interference (i.e., the overlay of two busrt on each other), the duration of the burst is always shorter than the duration of the timeslot by a certain value (0.577 - 0.546 = 0.031 ms), called “Guard Period”. This period represents a kind of time margin to compensate for possible time delays during signal transmission.
Tail bits
These markers define the beginning and end of the burst.
Info
Payload burst, for example, subscriber data, or service traffic. Consists of two parts.
Stealing flags
These two bits are set when both pieces of TCH burst data are transmitted on the FACCH. One transmitted bit instead of two means that only one part of the burst is transmitted on the FACCH.
Training sequence
This part of the burst is used by the receiver to determine the physical characteristics of the channel between the telephone and the base station.
2.5 Types of burst
Each logical channel corresponds to certain types of burst:
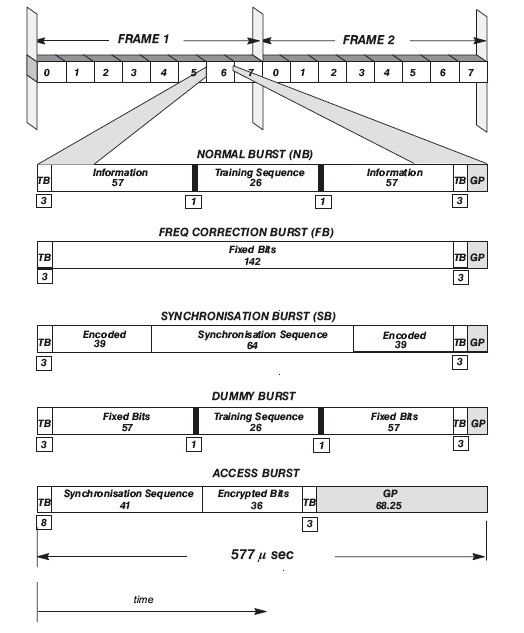
Normal burst
Sequences of this type implement traffic channels (TCH) between the network and subscribers, as well as all types of control channels (CCH): CCCH, BCCH and DCCH.
Frequency Correction Burst
The name speaks for itself. It implements a one-way downlink channel FCCH, allowing mobile phones to more accurately tune to the BTS frequency.
Synchronization Burst
Burst of this type, as well as Frequency Correction Burst, implements a downlink channel, only SCH, which is intended to identify the presence of base stations on the air. By analogy with beacon-packets in WiFi networks, each such burst is transmitted at full power, and also contains information about the BTS necessary for synchronization with it: frame rate, identification data ( BSIC ), and others.
Dummy burst
A dummy burst transmitted by the base station to fill in unused timeslots. The fact is that if there is no activity on the channel, the signal strength of the current ARFCN will be significantly less. In this case, the mobile phone may seem like it is far from the base station. To avoid this, BTS fills unused timeslots with meaningless traffic.
Access Burst
When establishing a connection with the BTS, the mobile phone sends a request for a dedicated SDCCH channel on the RACH channel. The base station, having received such a burst, assigns the subscriber its FDMA timings and responds on the AGCH channel, after which the mobile phone can receive and send Normal Bursts. It is worth noting the increased duration of Guard time, since initially the information on time delays is not known either to the telephone or to the base station. In case the RACH request did not hit the timeslot, the mobile phone sends it again after a pseudo-random period of time.
2.6 Frequency Hopping
Quote from wikipedia:
Pseudo-random tuning of the operating frequency (FHSS - frequency-hopping spread spectrum) is a method of transmitting information by radio, a feature of which is the frequent change of the carrier frequency. The frequency varies according to a pseudo-random number sequence known to both the sender and the receiver. The method increases the noise immunity of the communication channel.
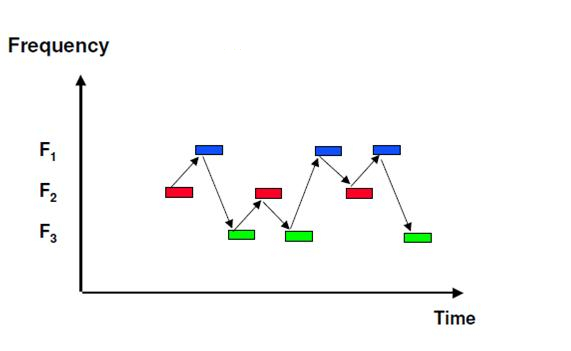
Frequency Hopping (FHSS) is one of the methods of spreading . In addition to GSM networks, a variation of this method is used in Bluetooth. What for?
- Reducing the effects of interference. Due to frequent frequency changes, interference can affect the signal only for a short time.
- Data protection from unauthorized access. Without knowing the algorithm by which the signal frequency changes, it is impossible to extract the necessary data from the noise-like stream.
- The complication of jamming. Frequency Hopping makes it difficult to “targeted” (i.e., jamming a particular device, or a combination of devices) to jam the signal. In this case, it is necessary to jam the entire occupied frequency range, which requires the use of more expensive and powerful equipment.
2.7 Basic principles of interaction between MS and BTS
Let's start with what happens when you turn on your mobile phone. Most often, even if the phone is turned off with the battery inserted, it continues to work. At this time, there is a small program called the “loader”. The loader waits for pressing the power key, starts the charging process when the charger is connected, and sometimes the alarm clock. It all depends on the specific phone model. As soon as the power key is pressed, the process of loading the operating system begins, which first checks for the presence of a SIM card and then starts scanning the air in search of the operator’s network. Even if there is no SIM card, the phone still connects to the nearest base station, providing an emergency call feature. If the SIM card is in place, a Location Update request is made, notifying the network of the current LAC of the subscriber. Then, the base station requests the IMEI of the phone and the IMSI SIM card to identify the subscriber (Identity Request). If the provided IMEI is different from the one with which the subscriber connected before, the operator can send Internet settings. By the way, you can even find a stolen phone. Then authorization is performed, after which the phone can be in one of two states:
- IDLE - “idle mode”. The phone does not transmit any network data while listening to the CCCH.
- DEDICATED - an active connection is established between the network and the phone, during which the phone periodically transmits information about the signal quality to the network and also exchanges user data.
Now let's take a closer look at the process of connecting to the network. Each base station necessarily has a broadcast channel CCCH, which is located on the zero timeslot of a certain ARFCN. In the process of scanning the air, the phone sequentially switches the frequency of the tuner, measuring the power of the received signal. As soon as the BTS with the strongest signal is found, the phone switches to its sync channel (SCH). Then, after receiving the first Synchronization Burst, the phone determines the sequence of timeslots, as well as the BSIC identification data, which consists of the NCC (Network Color Code) and BCC (Base station Color Code). The list of allowed and prohibited identifiers is stored on the SIM-card.
As soon as the phone finds an allowed BCCH, a RACH request is sent, the base station allocates a specific physical channel, authenticates the subscriber, and also registers its arrival in the VLR and HLR. After that, the phone is in IDLE mode. When an incoming call or SMS message is received, all base stations of the current LAC begin to send Paging Requests to notify the subscriber of any event. If the phone “heard” it, it answers, the network sends an Immediate Assignment package describing the resources allocated to the subscriber (frequency, number of timeslot, etc.). Very similar to Ping on the Internet. From this point on, the phone is in DEDICATED mode until the connection is broken.
If the subscriber himself acts as the initiator of the connection, he must first send a CM Service Request request, and then wait for Immediate Assignment from the network.
2.8 Handover
Handover (American version - handoff) - in cellular communication the process of transferring a subscriber from one base station to another during a telephone conversation or data transfer session. This process occurs when the subscriber leaves the coverage area of one base station and enters the coverage area of another. Also, a handover can be performed if the current base station is overloaded, or its physical channels are too noisy.
Handover is of two types:
- handover («break-before-make»). BTS , . , . handover . :)
- handover («make-before-break»). , BTS, , BTS . , .
2.9
As already mentioned, the speech of subscribers is transmitted on the TCH channel, which can be of two types: Full Rate (FR) and Half Rate (HR). The following standards are used for encoding an audio stream in GSM mobile networks (and not only):
- GSM-FR (Full Rate, 13 Kbps) is the first digital standard for speech coding, which provides a rather low sound quality compared to modern standards. Despite the existence of more modern codecs, GSM-FR is still very widely used.
- GSM-HR (Half Rate, 5.6 Kbps) is the codec used by phones in power saving mode. It takes half the bandwidth of the full rate channel. Battery saving can be up to 30%.
- GSM-EFR (Enhanced Full Rate, 12,2 /) — , Nokia , GSM-FR. , 5% GSM-FR.
- AMR (Adaptive multi rate) — . GSM UMTS, . / .
3.
It's time to consider the basic algorithms for ensuring the privacy and security of subscriber data. Against the backdrop of loud scandals and disclosures in the field of information security, this topic is quite relevant. GSM, like any other complex system, has its own protection mechanisms, as well as vulnerabilities, which we will consider in this chapter. I will not go into the wilds, describing the low-level bit conversion processes during encryption, etc., otherwise the article will turn into a huge bellied book. Who cares, you can read these materials:
Wikipedia, GSM Security
Habrahabr, GSM Security: data encryption
A lot of presentations and articles on this topic in my GitHub repository
3.1 Basic attack vectors
Since the Um interface is a radio interface, all its traffic is “visible” to anyone who is within the range of the BTS. Moreover, it is possible to analyze the data transmitted through the air, even without leaving home, using special equipment (for example, an old mobile phone supported by the OsmocomBB project, or a small dongle RTL-SDR) and
There are two types of attacks: passive and active. In the first case, the attacker does not interact with the network, or with the attacked subscriber - only the reception and processing of information. It is not difficult to guess that it is almost impossible to detect such an attack, but it does not have as many prospects as an active one. An active attack involves the interaction of the attacker with the attacked subscriber and / or the cellular network.
It is possible to identify the most dangerous types of attacks to which subscribers of cellular networks are subject:
- Sniffing
- Leakage of personal data, SMS and voice calls
- Location data leak
- Spoofing (FakeBTS or IMSI Catcher)
- Remote SIM card capture, arbitrary code execution (RCE)
- Denial of Service (DoS)
3.2 Subscriber Identification
As mentioned at the beginning of the article, subscriber identification is performed by IMSI, which is recorded in the subscriber’s SIM card and the operator’s HLR. Mobile phone identification is performed by serial number - IMEI. However, after authentication, neither IMSI, nor IMEI in open form fly over the air. After the Location Update procedure, the subscriber is assigned a temporary identifier - TMSI (Temporary Mobile Subscriber Identity), and further interaction is carried out with his help.
Attack methods
Ideally, the subscriber’s TMSI is known only to the mobile phone and the cellular network. However, there are ways to circumvent this protection. If you ring the subscriber cyclically or send SMS messages (or better Silent SMS), watching the PCH channel and performing the correlation, you can select the attacked subscriber with a certain accuracy.
In addition, having access to the inter-operator SS7 network, by phone number you can find out the IMSI and LAC of its owner. The problem is that in the SS7 network all operators "trust" each other, thereby reducing the level of confidentiality of the data of their subscribers.
3.3 Authentication
To protect against spoofing, the network authenticates the subscriber before starting its service. In addition to IMSI, a randomly generated sequence, called Ki, is stored in the SIM card, which it returns only in a hashed form. Ki is also stored in the operator's HLR and is never transmitted in clear text. In general, the authentication process is based on the principle of a four-way handshake:
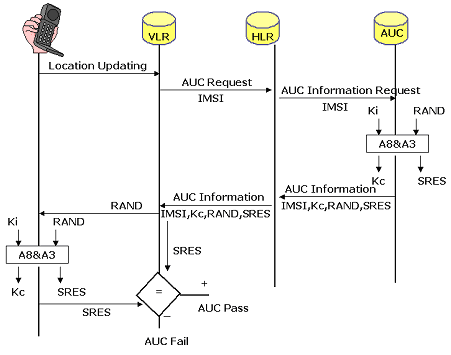
- The subscriber performs the Location Update Request, then provides the IMSI.
- The network sends a pseudo-random RAND value.
- The phone's SIM card hashes Ki and RAND using the A3 algorithm. A3 (RAND, Ki) = SRAND.
- The network also hashes Ki and RAND using the A3 algorithm.
- If the SRAND value on the subscriber side coincides with that calculated on the network side, then the subscriber has been authenticated.

Methods of attack
Busting Ki, having RAND and SRAND values, can take quite a long time. In addition, operators can use their own hashing algorithms. The network has quite a bit of information about brute force attempts. However, not all SIM cards are perfectly protected. Some researchers managed to get direct access to the file system of the SIM card, and then extract the Ki.
3.4 Traffic Encryption
According to the specification, there are three algorithms for encrypting user traffic:
- A5 / 0 is a formal designation for the lack of encryption, as well as OPEN in WiFi networks. I myself have never met networks without encryption, however, according to gsmmap.org , A5 / 0 is used in Syria and South Korea.
- A5/1 — . , , . 2 , Linux Kraken .
- A5/2 — . , .
- A5/3 — , 2002 . , . , 2G-. , .. . . , 3GPP-.
Attack Methods
As already mentioned, having sniffing equipment and a computer with 2 TB of memory and the Kraken program, you can quite quickly (a few seconds) find session encryption keys A5 / 1, and then decrypt anyone's traffic. German cryptologist Karsten Nohl in 2009 demonstrated the A5 / 1 hacking method. A few years later, Carsten and Sylvain Muno demonstrated the interception and method of decrypting a telephone conversation with the help of several old Motorola phones (OsmocomBB project).
Conclusion
My long story came to an end. In more detail and from the practical side, the principles of operation of cellular networks can be found in a series of articles on Introducing OsmocomBB as soon as I add the remaining parts. I hope I managed to tell you something new and interesting. Waiting for your feedback and comments!
References
en.wikipedia.org/wiki/Um_interface
en.wikipedia.org/wiki/GSM_frequency_bands
www.teletopix.org/gsm/what-is-burst-in-gsm-and-burst-types-in-gsm
en.wikipedia.org/wiki/Control_channel
www.etsi.org/deliver/etsi_gts/05/0502/03.08.00_60/gsmts_0502sv030800p.pdf
www.sharetechnote.com/html/FrameStructure_GSM.html
www.teletopix.org/gsm/how-26-and-51-multiframes-in-gsm
www.teletopix.org/gsm/bch-cbch-and-ccch-works-in-gsm
www.teletopix.org/gsm/dedicated-control-channel-dcch-in-gsm
en.wikipedia.org/wiki/Handover
www.teletopix.org/gsm/slow-and-fast-frequency-hopping-in-gsm
en.wikipedia.org/wiki/Um_interface
en.wikipedia.org/wiki/GSM_frequency_bands
www.teletopix.org/gsm/what-is-burst-in-gsm-and-burst-types-in-gsm
en.wikipedia.org/wiki/Control_channel
www.etsi.org/deliver/etsi_gts/05/0502/03.08.00_60/gsmts_0502sv030800p.pdf
www.sharetechnote.com/html/FrameStructure_GSM.html
www.teletopix.org/gsm/how-26-and-51-multiframes-in-gsm
www.teletopix.org/gsm/bch-cbch-and-ccch-works-in-gsm
www.teletopix.org/gsm/dedicated-control-channel-dcch-in-gsm
en.wikipedia.org/wiki/Handover
www.teletopix.org/gsm/slow-and-fast-frequency-hopping-in-gsm
Source: https://habr.com/ru/post/268127/
All Articles