Operator famous banker Trojan Citadel sentenced to prison
In the US, a sentence was passed on a person from Russia who was found guilty of participating in a cybercrime group specializing in the use of the well-known banking Trojan Citadel. Dmitry Belorossov (Dimitry Belorossov) aka Rainerfox was sentenced to imprisonment for 4 years and 6 months as the operator of a large botnet based on Citadel, which included 7 thousand bots.

Cybercriminal began its activities in 2012 and specialized in distributing banking Trojan using various methods, including phishing e-mail and advertising links on websites. The malicious program supplied the operator with the online banking information of the compromised user, which was used by him for the subsequent withdrawal of funds.
')
Malicious software Citadel saw the light after leaking Zeus source texts on which it was based. Its first versions were discovered in 2011. Citadel offered users a substantially improved cybercrime scheme for using malware and creating a botnet based on it. For clients offered something like those. support that could advise them on the functions of the banker Trojan. They could also request the addition of new functions there or report on the defects found. Citadel could be distributed by subscription as a cybercrime service.
Cybercriminal Rainerfox ordered to pay more than $ 300 thousand compensation for the damage.
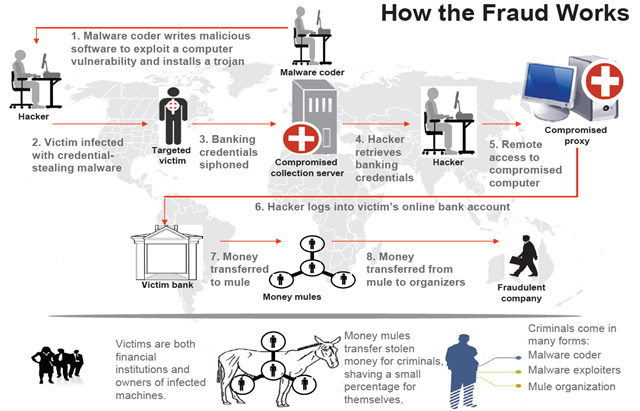
Fig. A typical pattern of cybercriminals who use bank malware, including Citadel.

Cybercriminal began its activities in 2012 and specialized in distributing banking Trojan using various methods, including phishing e-mail and advertising links on websites. The malicious program supplied the operator with the online banking information of the compromised user, which was used by him for the subsequent withdrawal of funds.
')
In 2012, Belorossov downloaded a version of Citadel, which he then used to operate a Citadel botnet primarily from Russia. The system is remotely controlled over. He also received information on the victim computers, including online banking credentials.
Malicious software Citadel saw the light after leaking Zeus source texts on which it was based. Its first versions were discovered in 2011. Citadel offered users a substantially improved cybercrime scheme for using malware and creating a botnet based on it. For clients offered something like those. support that could advise them on the functions of the banker Trojan. They could also request the addition of new functions there or report on the defects found. Citadel could be distributed by subscription as a cybercrime service.
Cybercriminal Rainerfox ordered to pay more than $ 300 thousand compensation for the damage.

Fig. A typical pattern of cybercriminals who use bank malware, including Citadel.
- The author of the Trojan is developing the necessary functionality of the bot.
- The operator (hacker) is responsible for distributing the compiled executable files of the Trojan program. He can use the services of spammers to organize spam mailings, “iframes” to redirect legitimate users of hacked sites to a Trojan or other methods known in the cybercrime world.
- The user is infected with a banking trojan, after which he uses a browser (in the process of which the malicious code is located) to work with online banking. The confidential data specified when working with the online banking system is sent to the attacker's server.
- The operator (hacker) receives the data sent by the bot in the previous step.
- The operator may use another compromised computer (proxy) to conduct fraudulent operations with the victim’s account, thus hiding the source of the attack.
- Using the proxy specified in the previous paragraph, the operator logs in to the user's online banking account using the login / password pairs stolen in step 4.
- Funds from the victim’s account are transferred to several dummy bank accounts in small portions, and then cashed at ATMs by various persons participating in the criminal scheme (mules).
- The organizer (coordinator) of the entire criminal scheme receives funds from the “mules”, and each of them “mules” receives its share.
Source: https://habr.com/ru/post/267977/
All Articles