DIY MAB Library for Microsoft NPS
Recently, more and more companies are starting to take network security seriously. Particular attention is paid to including control of access to the local network within the organization. It is not uncommon that the security policy requires that absolutely all devices connected to the wired and wireless networks be authenticated (we do not consider equipment that is physically isolated in the server rooms).
As a network engineer, I was just tasked with implementing all this. Immediately, I note that we have more than ten offices of different sizes in our company, whose networks have from one to thirty Cisco Catalyst access level switches. Historically, in virtually every office, the Microsoft Network Policy Server (NPS) has already been raised as a RADIUS server for authenticating wireless clients.
All these NPS needed to be used to accomplish the task, as the option with a centralized RADIUS server such as Cisco ISE / ACS dropped due to the unreliability of WAN channels, and there were no funds to buy other products.
')
Consider the problem in more detail.
1) It is necessary to authenticate:
2) It is necessary to dynamically assign vlan for each authenticated device, since some of them can “travel” to different floors (for example, video conferencing devices). At the same time, the phones should fall into the tagged voice vlan, and the rest of the devices in the data-vlan.
The workstations were decided to authenticate using the installed certificate using 802.1x. It is easily implemented in NPS. Create a Network Policy, select Authentication Type = EAP as a condition (in fact, this is EAP-TLS, where a secure channel between the supplicant and the authentication server is created using their certificates), NAS Port Type = Ethernet (for wired connections) or Wireless (for wireless ).
It is possible for fidelity to add a computer belonging to any domain group. Standard RADIUS atribuses are used to assign vlan, although you can also use Vendor Specific Attributes, which will be discussed later.
As for other devices, they need to use MAB (MAC-address Authentication Bypass), due to the lack of 802.1x support. With MAB, the switch acts as a supplicant and sends information about the mac-address of the connected device to the RADIUS server. Cisco Catalyst switches support MAB as the fallback method for 802.1x (when the switch did not receive an EAPoL response from the client).
It so happened that in NPS you can implement MAB only with reference to ActiveDirectory. Those. for each device, an object must be added to AD, which we absolutely did not like. It was decided to "finish" the NPS to normal support for MAB. Fortunately, Microsoft provides the ability to connect extension libraries to the NPS , which I used.
Gathering together Microsoft’s mean technical documentation, a description of the RFC standard for RADIUS, and a few examples found in the Internet, and adding to them my limited programming knowledge, I received a positive result ... two months later.
The library runs along with NPS and implements the RadiusExtensionProcess2 method, called with each new request. My algorithm checks the request to the RADIUS server and compares the Calling-Station-ID (client mac-address) and Username attributes, since they coincide with MAB. Of course, it was possible to identify MAB by other attributes, but I chose this method.
After we have determined that this request is a MAB, it is necessary to verify the client's address with the database of mac-addresses. All addresses are associated with different profiles (data, voice, printer, ...), each of which is assigned its own format of a RADIUS response.
Since I dealt with Cisco equipment, I decided to add Vendor Specific Attribute (VSA) - AV-Pair to the RADIUS response. With it, you can force the switch to place the client in some data / voice vlan (to be honest, I did not use standard RADIUS attributes here because I simply could not get the program to work correctly).
Example 1: put the client in vlan 2:
tunnel-type = VLAN
tunnel-medium-type = ALL_802
tunnel-private-group-id = 2
Example 2: put the client in a voice vlan configured on this port:
device-traffic-class = voice
If the client needs to be placed in data vlan, which is configured on the switch port, then there is no need to add VSA. Just send ResponseCode = AccessAccept.
Accessing the library is made after the NPS has checked all its policies (Network Policies) to match their conditions with the client's parameters, so the existing old policies for Wireless work fine even after the implementation of MAB.
I completely forgot to say that the NPS contains two groups of policies: Connection Request Policies and Network Policies. Earlier, I mentioned only the second. In the first one, it is enough to create one rule, under which all requests to the RADIUS server will fall. For example, as a condition, set the time from 00:00 to 24:00. Well, or if it does not suit you, you can specify all possible addresses of network devices in the NAS IPv4 Address parameter using the regex syntax.
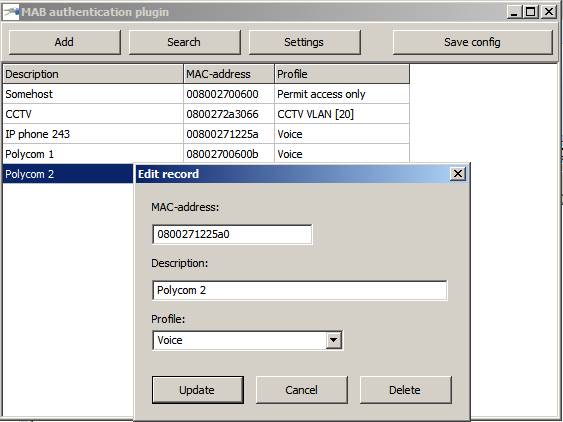
Let's go back to my library. To manage the database of mac-addresses, I wrote a simple GUI program that allows you to create profiles for different types of devices and link them with mac-addresses from the database. It looks like this:
Much has been written about setting up switches for 802.1x and MAB, but I will give an example anyway:
aaa new-model
aaa authentication dot1x default group radius
aaa authorization network default group radius
dot1x system-auth-control
radius-server host <server address> key <key> (or the same through the server group in the new IOS)
interface range <your access ports>
switchport mode access
switchport voice vlan (if needed)
authentication port-control auto
authentication host-mode multi-domain
dot1x pae authenticator
mab
A test version of the library and the management program can be downloaded here .
Now I am actively testing it and at the same time I am developing a new, more serious version with central management via a web interface that combines several RADIUS servers from different offices and synchronizes data between them, and also can be friends with the main DBMS and automatically import the device MAC addresses from corporate inventory tools. I hope to tell about the new project in the following posts.
As a network engineer, I was just tasked with implementing all this. Immediately, I note that we have more than ten offices of different sizes in our company, whose networks have from one to thirty Cisco Catalyst access level switches. Historically, in virtually every office, the Microsoft Network Policy Server (NPS) has already been raised as a RADIUS server for authenticating wireless clients.
All these NPS needed to be used to accomplish the task, as the option with a centralized RADIUS server such as Cisco ISE / ACS dropped due to the unreliability of WAN channels, and there were no funds to buy other products.
')
Consider the problem in more detail.
1) It is necessary to authenticate:
- corporate workstations;
- IP phones and conference equipment;
- network printers;
- CCTV Cameras
- etc.
2) It is necessary to dynamically assign vlan for each authenticated device, since some of them can “travel” to different floors (for example, video conferencing devices). At the same time, the phones should fall into the tagged voice vlan, and the rest of the devices in the data-vlan.
The workstations were decided to authenticate using the installed certificate using 802.1x. It is easily implemented in NPS. Create a Network Policy, select Authentication Type = EAP as a condition (in fact, this is EAP-TLS, where a secure channel between the supplicant and the authentication server is created using their certificates), NAS Port Type = Ethernet (for wired connections) or Wireless (for wireless ).
It is possible for fidelity to add a computer belonging to any domain group. Standard RADIUS atribuses are used to assign vlan, although you can also use Vendor Specific Attributes, which will be discussed later.
As for other devices, they need to use MAB (MAC-address Authentication Bypass), due to the lack of 802.1x support. With MAB, the switch acts as a supplicant and sends information about the mac-address of the connected device to the RADIUS server. Cisco Catalyst switches support MAB as the fallback method for 802.1x (when the switch did not receive an EAPoL response from the client).
It so happened that in NPS you can implement MAB only with reference to ActiveDirectory. Those. for each device, an object must be added to AD, which we absolutely did not like. It was decided to "finish" the NPS to normal support for MAB. Fortunately, Microsoft provides the ability to connect extension libraries to the NPS , which I used.
Gathering together Microsoft’s mean technical documentation, a description of the RFC standard for RADIUS, and a few examples found in the Internet, and adding to them my limited programming knowledge, I received a positive result ... two months later.
The library runs along with NPS and implements the RadiusExtensionProcess2 method, called with each new request. My algorithm checks the request to the RADIUS server and compares the Calling-Station-ID (client mac-address) and Username attributes, since they coincide with MAB. Of course, it was possible to identify MAB by other attributes, but I chose this method.
After we have determined that this request is a MAB, it is necessary to verify the client's address with the database of mac-addresses. All addresses are associated with different profiles (data, voice, printer, ...), each of which is assigned its own format of a RADIUS response.
Since I dealt with Cisco equipment, I decided to add Vendor Specific Attribute (VSA) - AV-Pair to the RADIUS response. With it, you can force the switch to place the client in some data / voice vlan (to be honest, I did not use standard RADIUS attributes here because I simply could not get the program to work correctly).
Example 1: put the client in vlan 2:
tunnel-type = VLAN
tunnel-medium-type = ALL_802
tunnel-private-group-id = 2
Example 2: put the client in a voice vlan configured on this port:
device-traffic-class = voice
If the client needs to be placed in data vlan, which is configured on the switch port, then there is no need to add VSA. Just send ResponseCode = AccessAccept.
Accessing the library is made after the NPS has checked all its policies (Network Policies) to match their conditions with the client's parameters, so the existing old policies for Wireless work fine even after the implementation of MAB.
I completely forgot to say that the NPS contains two groups of policies: Connection Request Policies and Network Policies. Earlier, I mentioned only the second. In the first one, it is enough to create one rule, under which all requests to the RADIUS server will fall. For example, as a condition, set the time from 00:00 to 24:00. Well, or if it does not suit you, you can specify all possible addresses of network devices in the NAS IPv4 Address parameter using the regex syntax.
Let's go back to my library. To manage the database of mac-addresses, I wrote a simple GUI program that allows you to create profiles for different types of devices and link them with mac-addresses from the database. It looks like this:

Much has been written about setting up switches for 802.1x and MAB, but I will give an example anyway:
aaa new-model
aaa authentication dot1x default group radius
aaa authorization network default group radius
dot1x system-auth-control
radius-server host <server address> key <key> (or the same through the server group in the new IOS)
interface range <your access ports>
switchport mode access
switchport voice vlan (if needed)
authentication port-control auto
authentication host-mode multi-domain
dot1x pae authenticator
mab
A test version of the library and the management program can be downloaded here .
Now I am actively testing it and at the same time I am developing a new, more serious version with central management via a web interface that combines several RADIUS servers from different offices and synchronizes data between them, and also can be friends with the main DBMS and automatically import the device MAC addresses from corporate inventory tools. I hope to tell about the new project in the following posts.
Source: https://habr.com/ru/post/267599/
All Articles